This document discusses WiFi security and provides information on various topics related to securing wireless networks. It begins with an introduction to wireless networking and then covers security threats like eavesdropping and man-in-the-middle attacks. The document analyzes early security protocols like WEP that were flawed and discusses improved protocols like WPA and WPA2. It provides tips for securing a wireless network and examines potential health effects of WiFi radiation. The conclusion emphasizes that wireless security has improved greatly with new standards but work remains to be done.













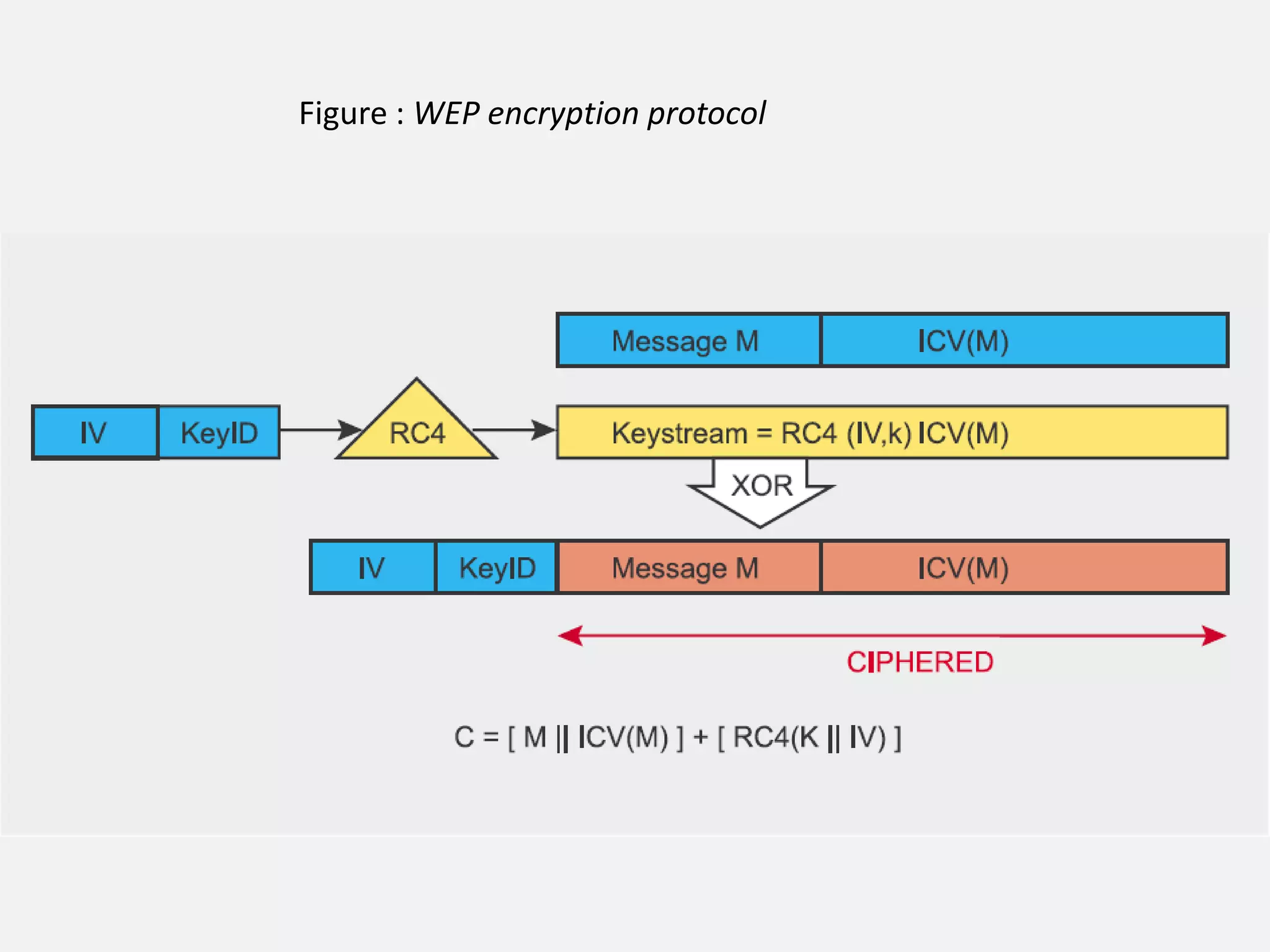
![WEP
(Wired Equivalent Privacy)
Default encryption protocol
Based on RC4 encryption algorithm
with a secret key of 40 bits or 104 bits being
combined with a 24-bit Initialisation Vector(IV) to
encrypt the plaintext message M and its checksumthe ICV (Integrity check value)
The encrypted message C was therefore determined
using the following formula:
C = [ M || ICV(M) ] + [ RC4(K || IV) ]](https://image.slidesharecdn.com/wi3-140222040001-phpapp02/75/Wifi-Security-14-2048.jpg)