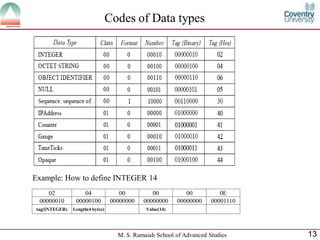
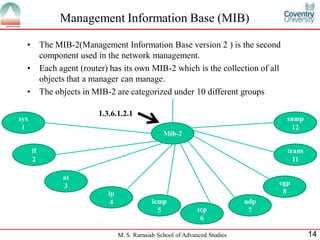
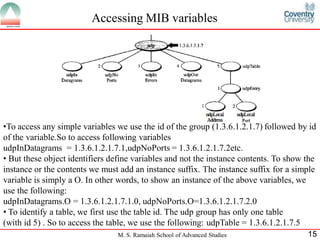
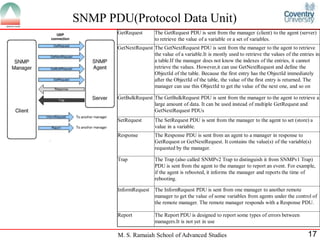
The document discusses SNMP (Simple Network Management Protocol). It provides a high-level overview of SNMP including its history, versions, components like SMI and MIB, and basic operations. SNMP allows network devices to be monitored and managed remotely. It uses a client/server model where a manager communicates with agents running on devices using SNMP messages to get/set variable values defined in MIBs.








![References
[1] Forouzan B. A. (2000) Data Communication and Networking,
2nd edition, Tata McGraw-Hill.
[2] Harrington,D.,Presuhn,R.,Wijnen,B.,(2002) An Architecture for
Describing Simple Network Management Protocol (SNMP)
Management Frameworks,RFC3411[Online]
Available
From: http://www.ietf.org/rfc/rfc3411.txt (Accessed:11 October
2012)
[3] Rahul,B.(2002) Internetworking Technologies- An Engineering
perspective, Prentice hall Of India
M. S. Ramaiah School of Advanced Studies 30](https://image.slidesharecdn.com/cjb0412001-cnp-spc2517-presentation-130105093521-phpapp01/85/SNMP-30-320.jpg)