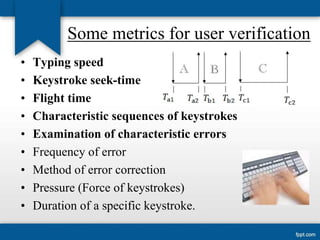
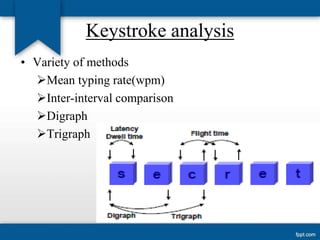
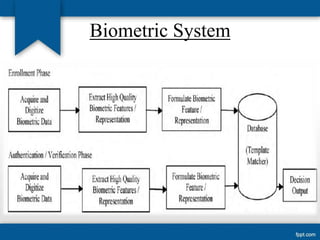
The seminar discusses keystroke dynamics as a biometric authentication method that analyzes typing patterns to verify user identity. It covers the types of biometric methods, their advantages and drawbacks, along with applications and ongoing research for more robust systems. Although promising and cost-effective, keystroke dynamics still faces challenges such as user variability and typing pattern changes.








![References
• [1] IEEE Keystroke dynamics as a biometric for
authentication, Fabian Monrose, Aviel D. Rubin, March 1999.
• [2] IEEE, Keystroke-Dynamics Authentication Against
Synthetic Forgeries Deian Stefan
• [3] Zeljka Zorz [Online] Avaliable: http://www.netsecurity.org/article.php?id=1610
• [4] wikipedia[Online] Avaliable :
http://en.wikipedia.org/wiki/Keystroke_dynamics](https://image.slidesharecdn.com/901-91-131110021922-phpapp01/85/Keystroke-dynamics-17-320.jpg)

