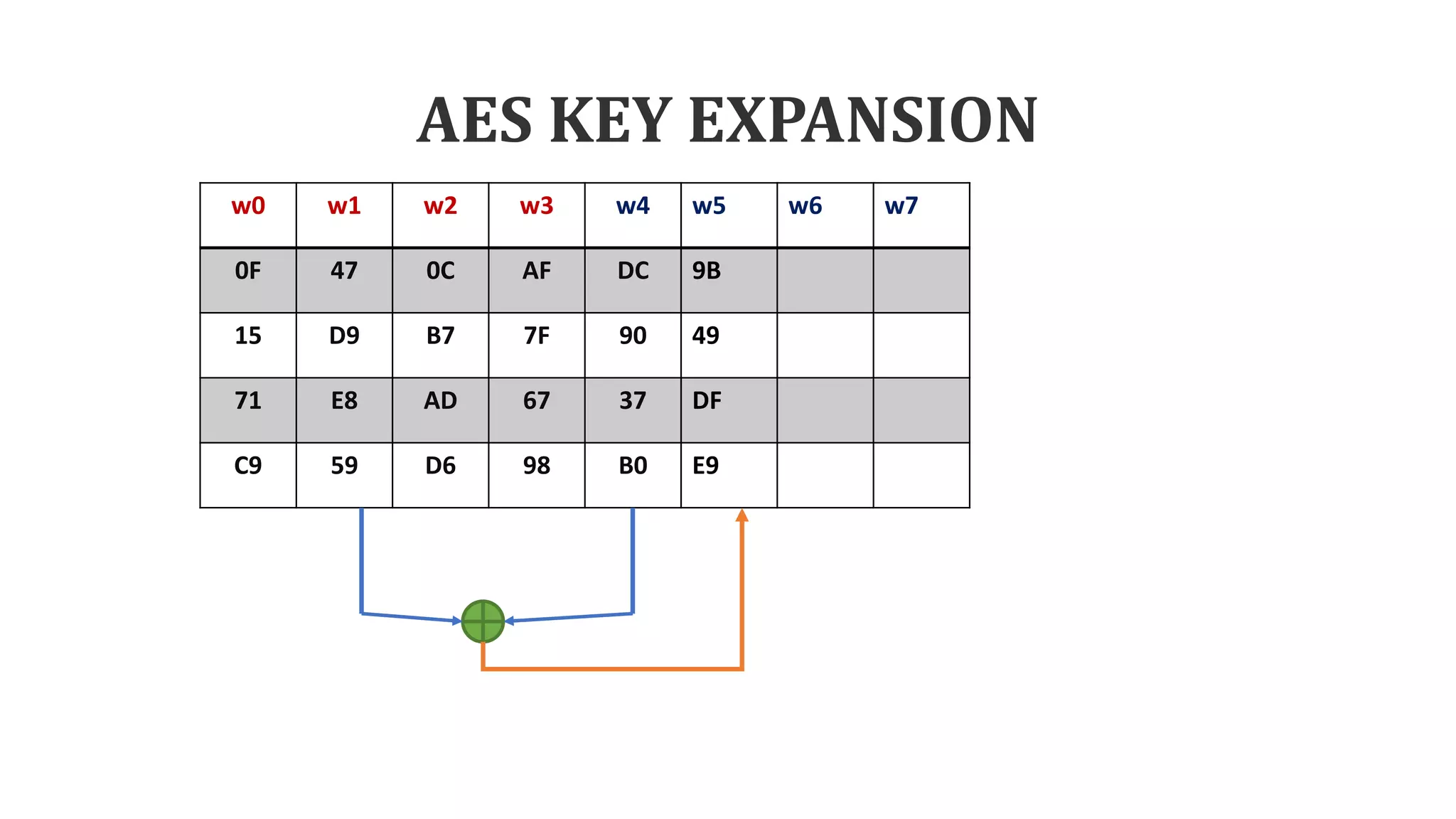
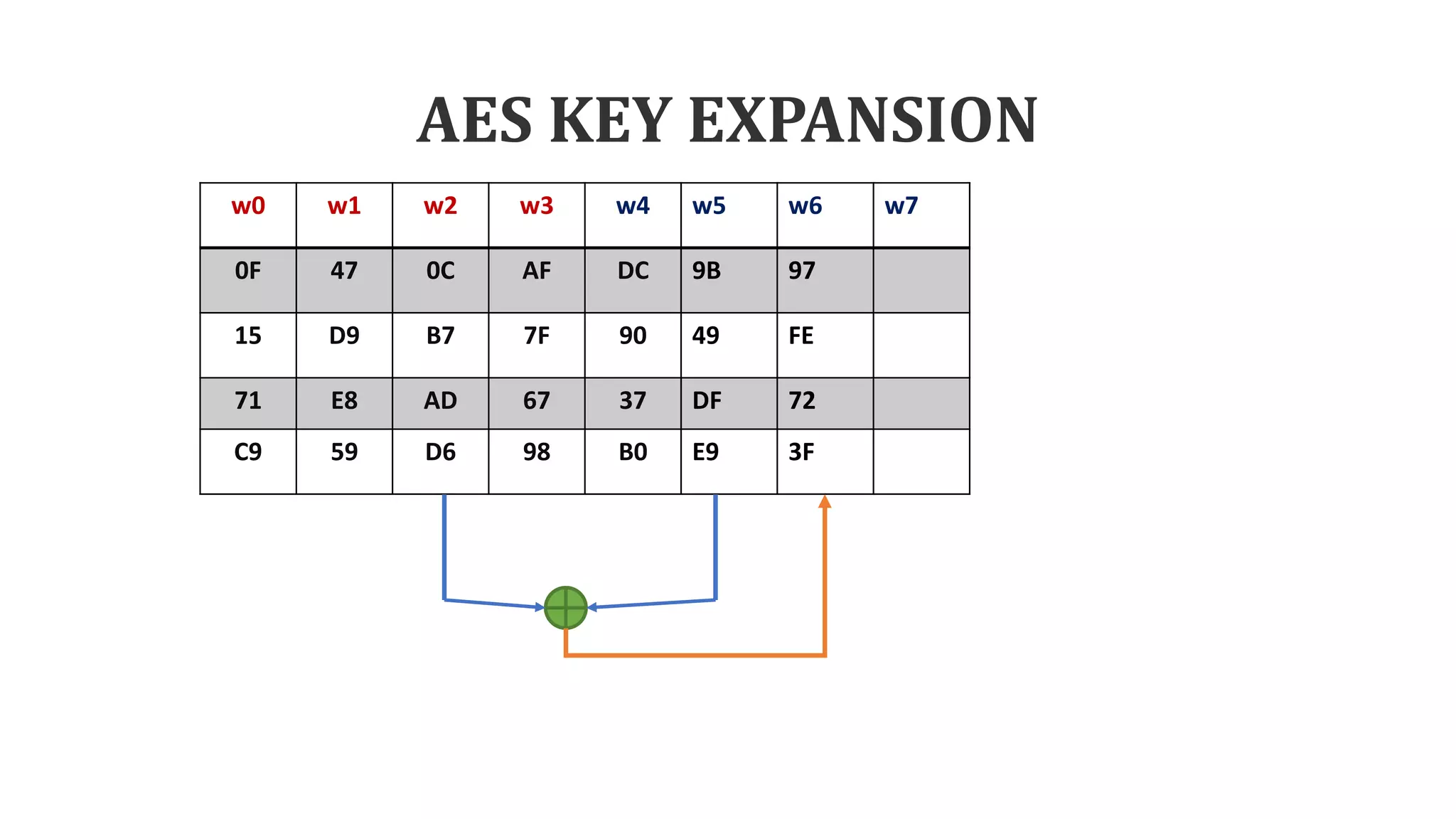
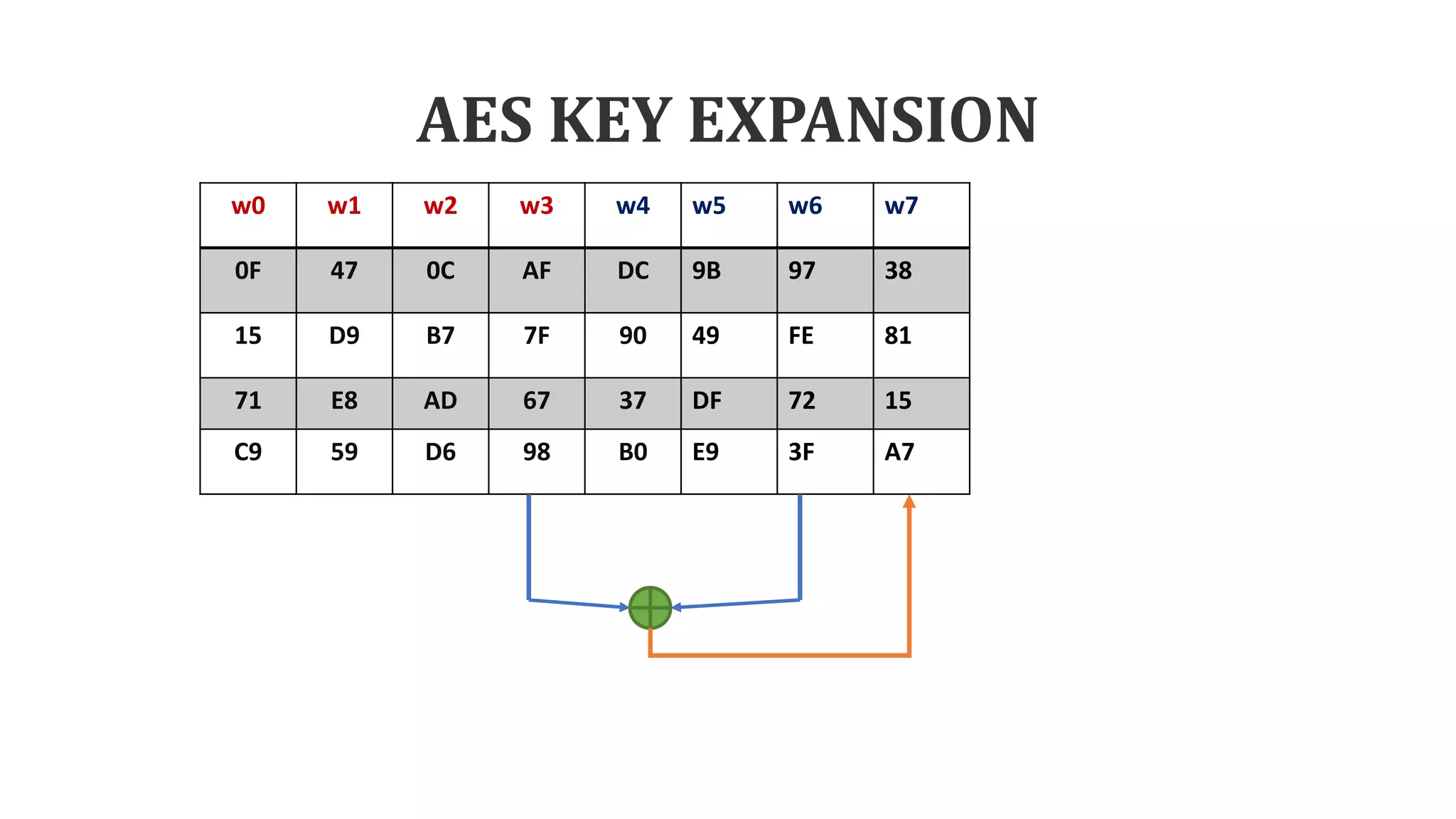
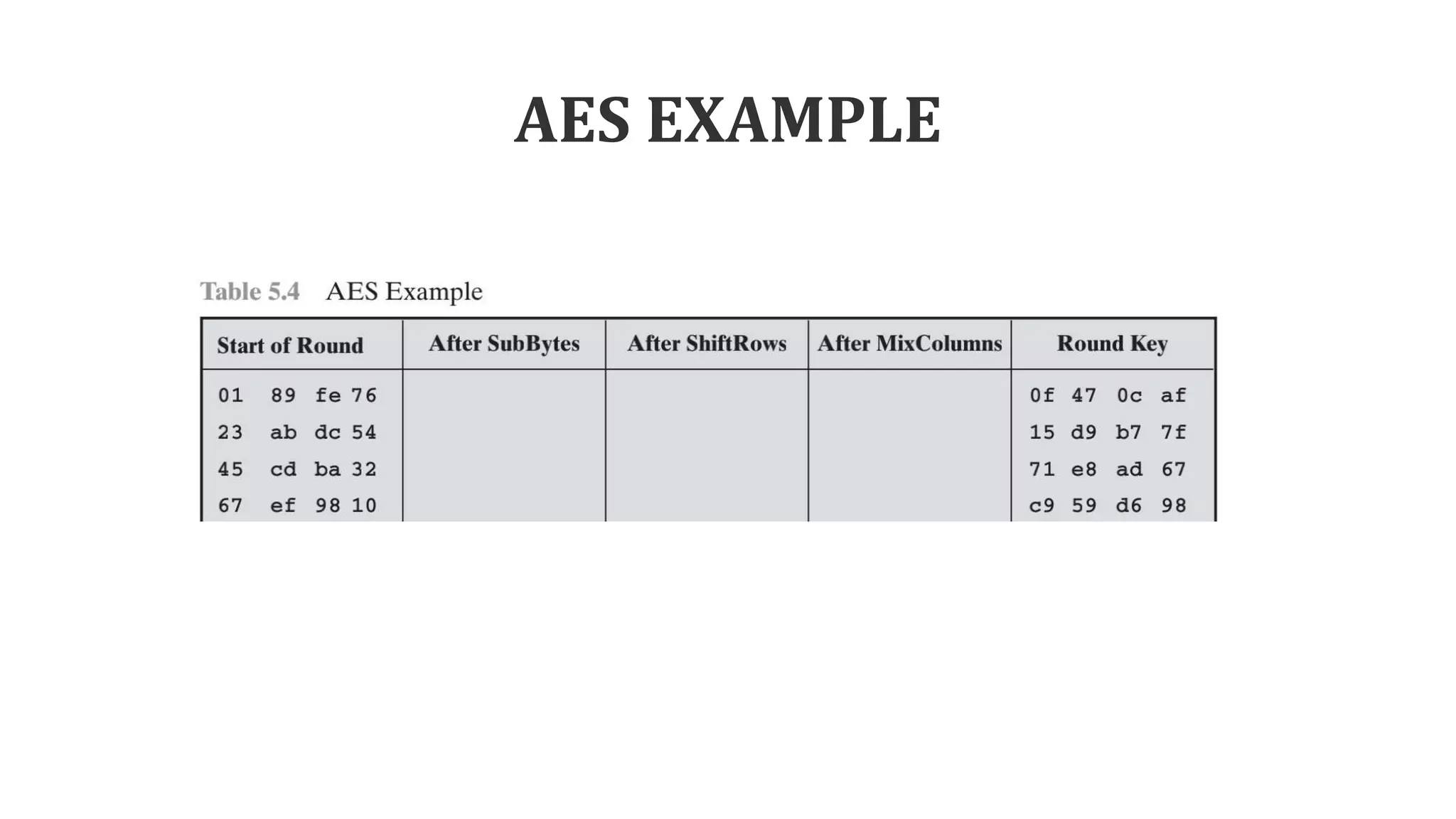
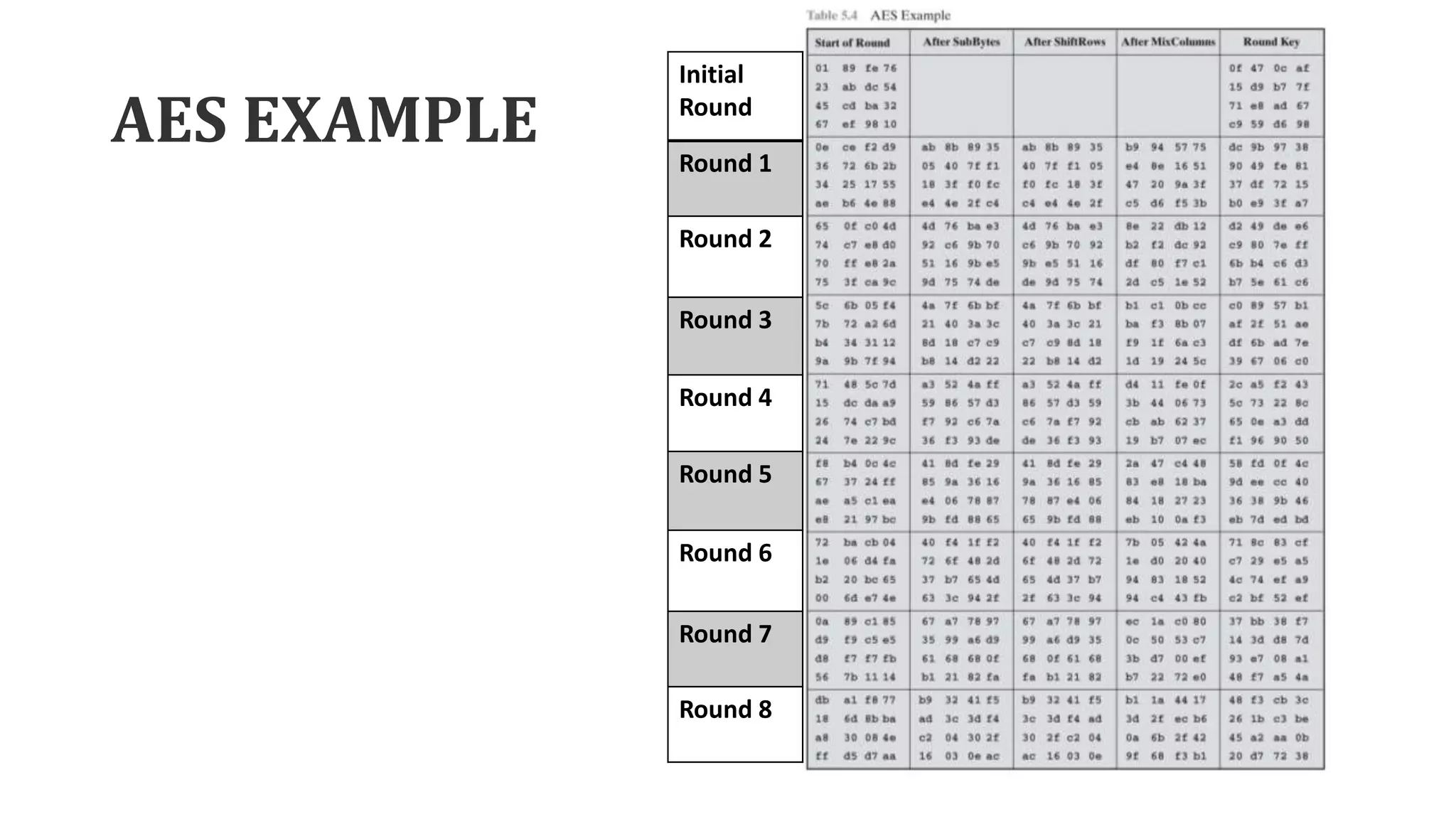
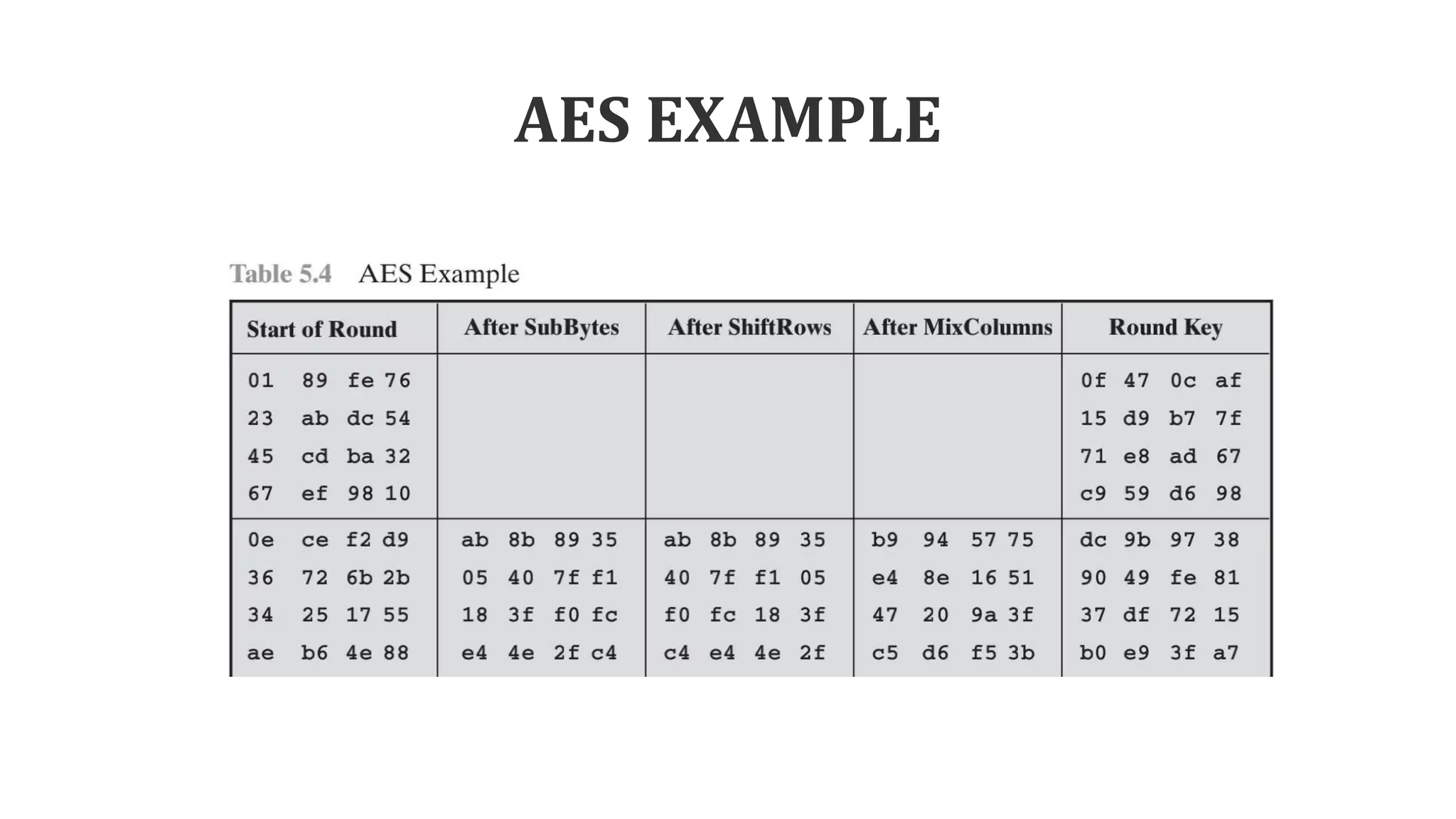
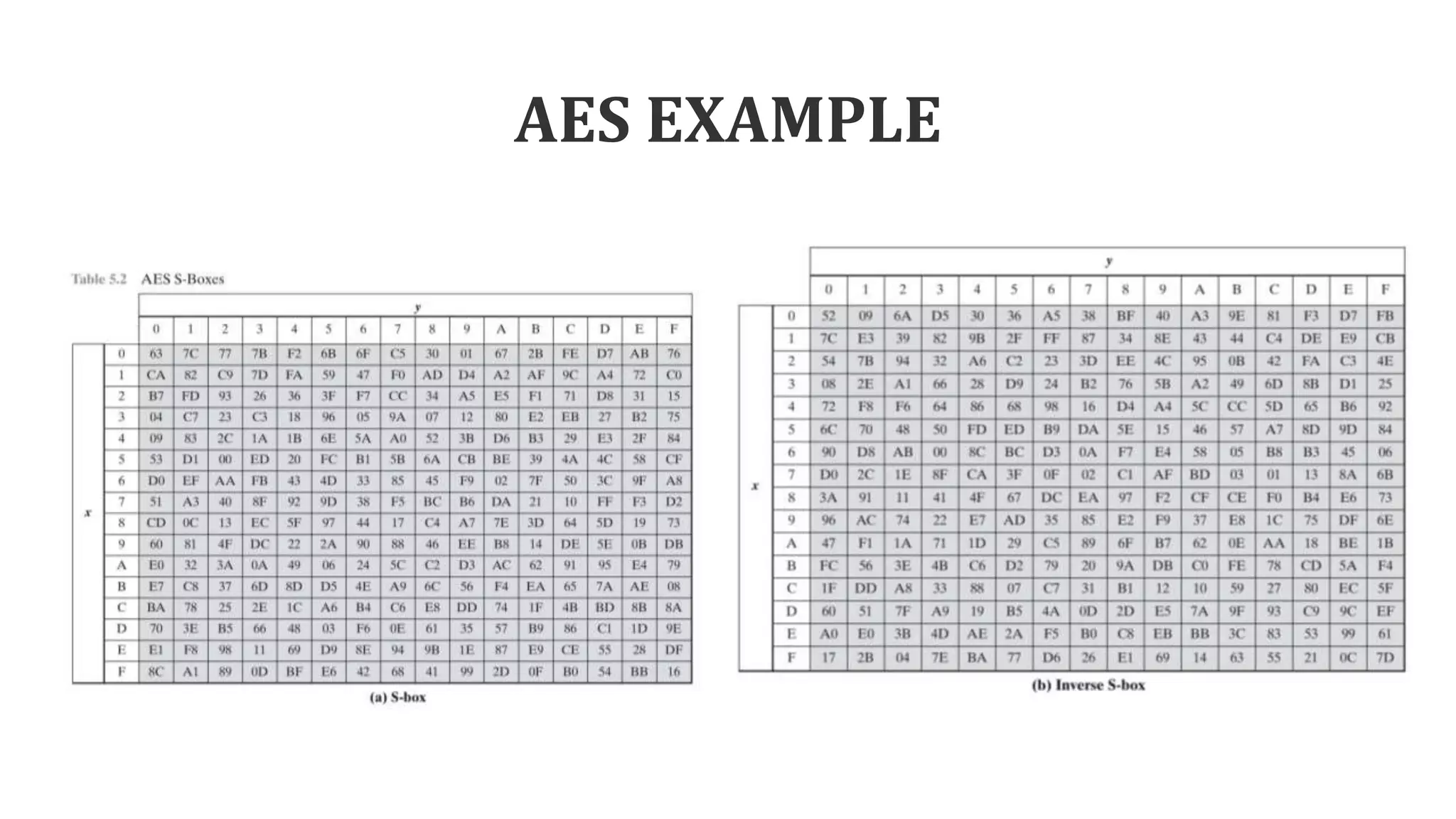
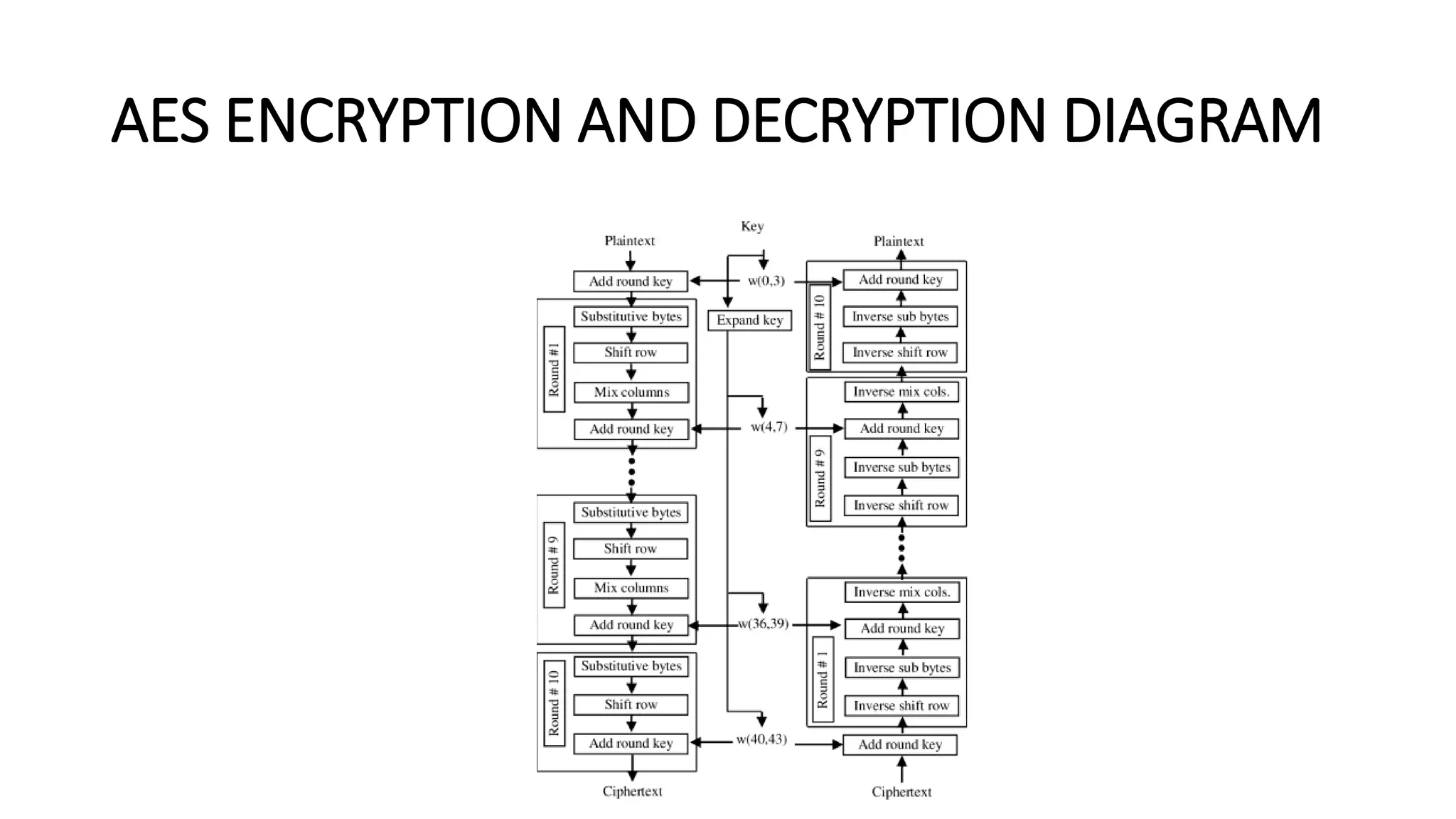
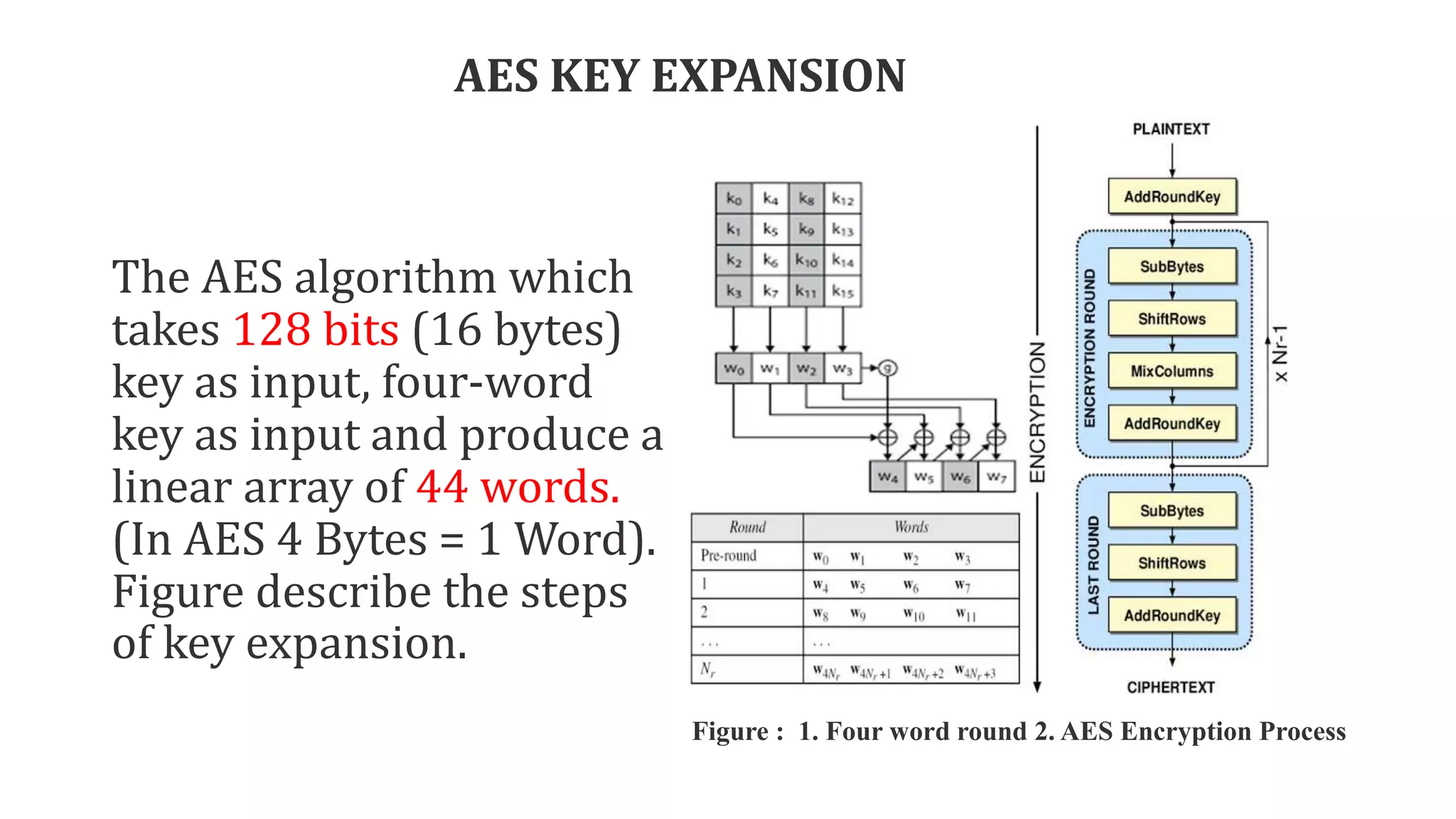
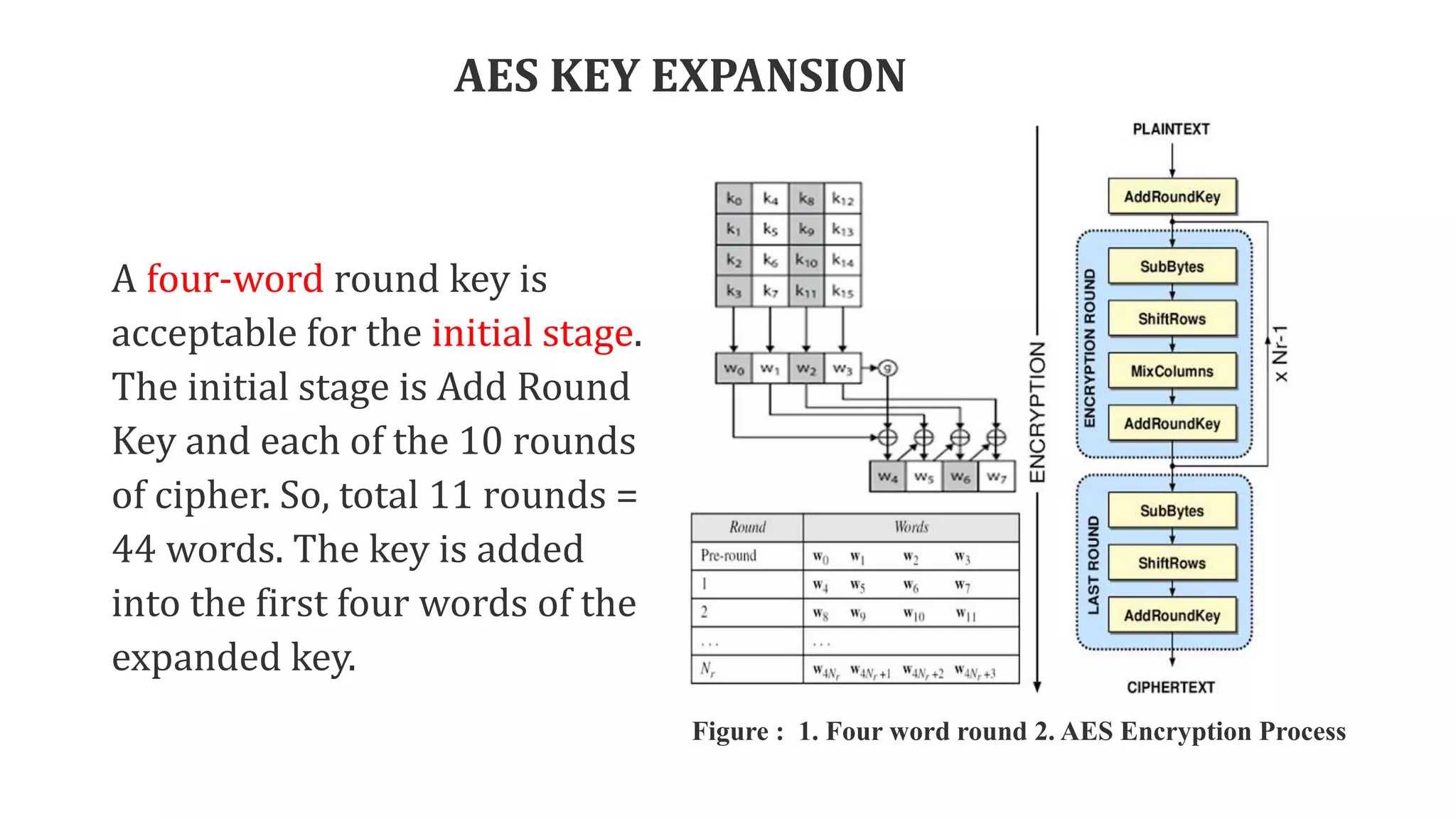
The document describes the AES key expansion process. The AES algorithm takes a 128-bit key as input and expands it into a linear array of 44 words using a key schedule. The key schedule applies the key expansion function g, which performs byte substitutions and XOR operations with round constants, to generate a key for each round. The initial key is added to the first four words of the expanded key schedule.

![AES KEY EXPANSION
• The function g defines the complex
and that function consist of some sub
function as follow:
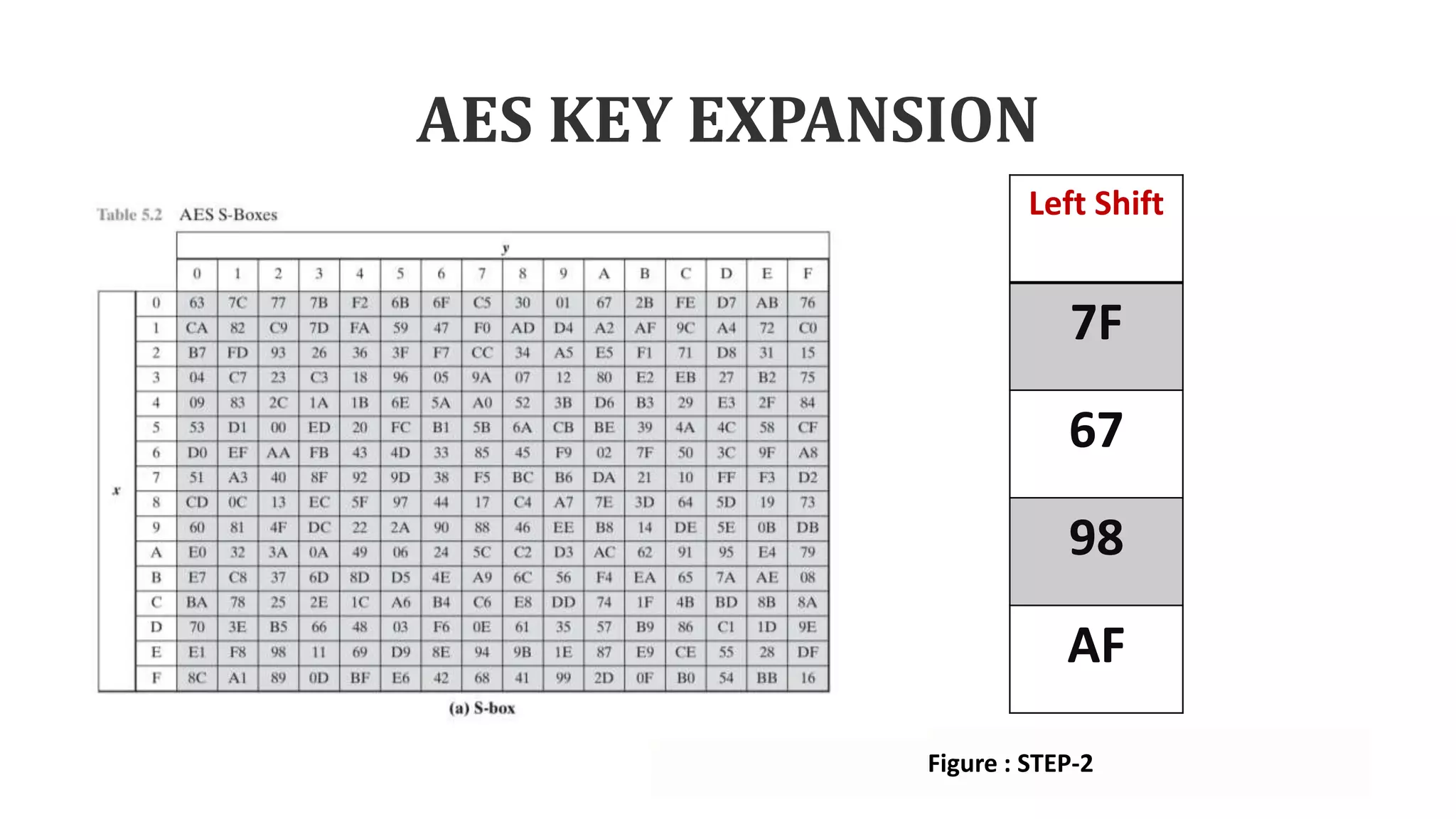
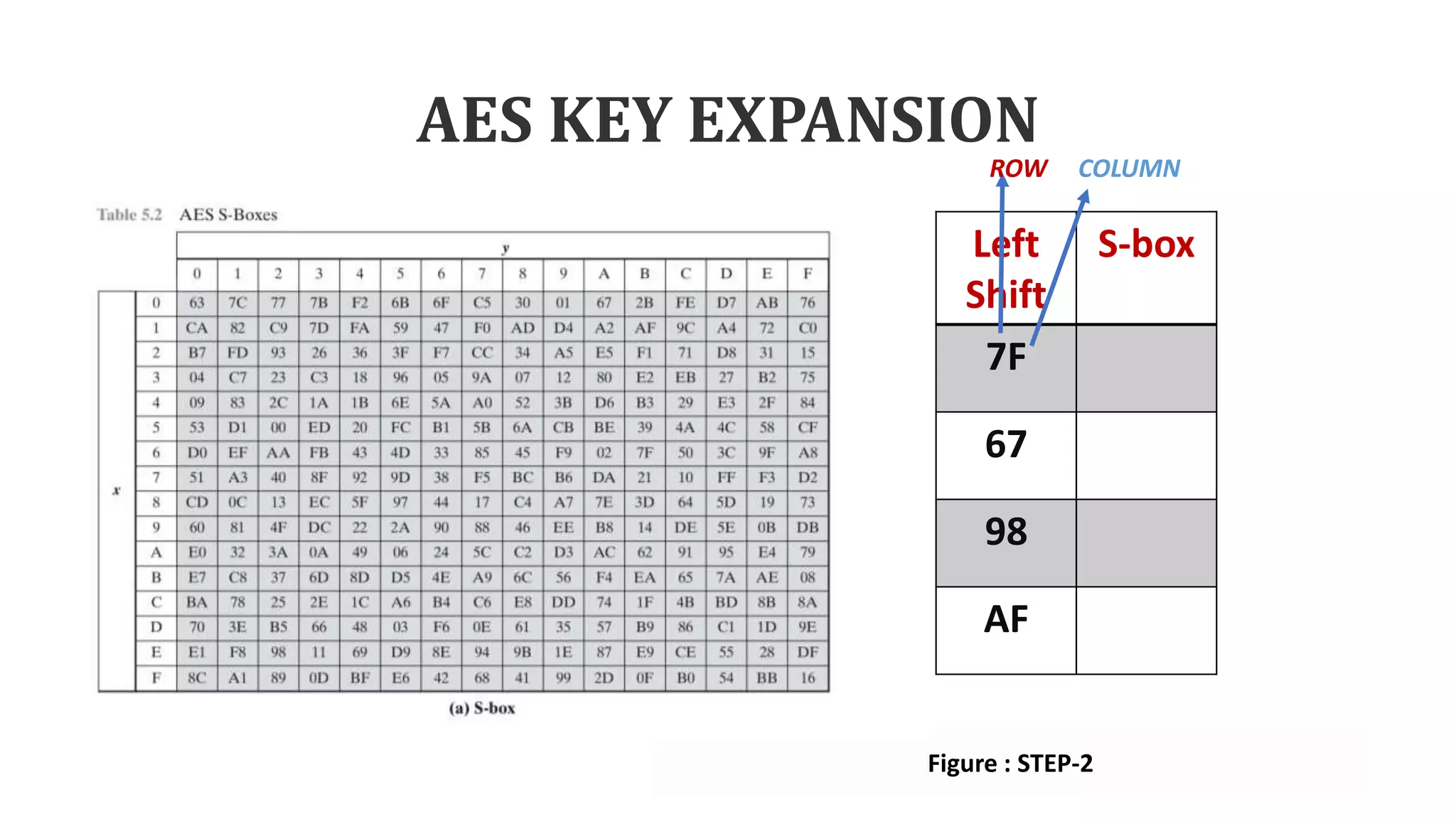
• Step-1: This function performs the
one-byte circular left shift.
• Step-2: Using S-box each sub word
performs a byte substitution.
• Step-3: Finally result of Rot word and
step 2 is XORed with the round
constant called as Rcon[Round].
Figure : Function g](https://image.slidesharecdn.com/aeskeyexpansion1-230201170256-e6881d6c/75/AES-KEY-EXPANSION-pptx-5-2048.jpg)
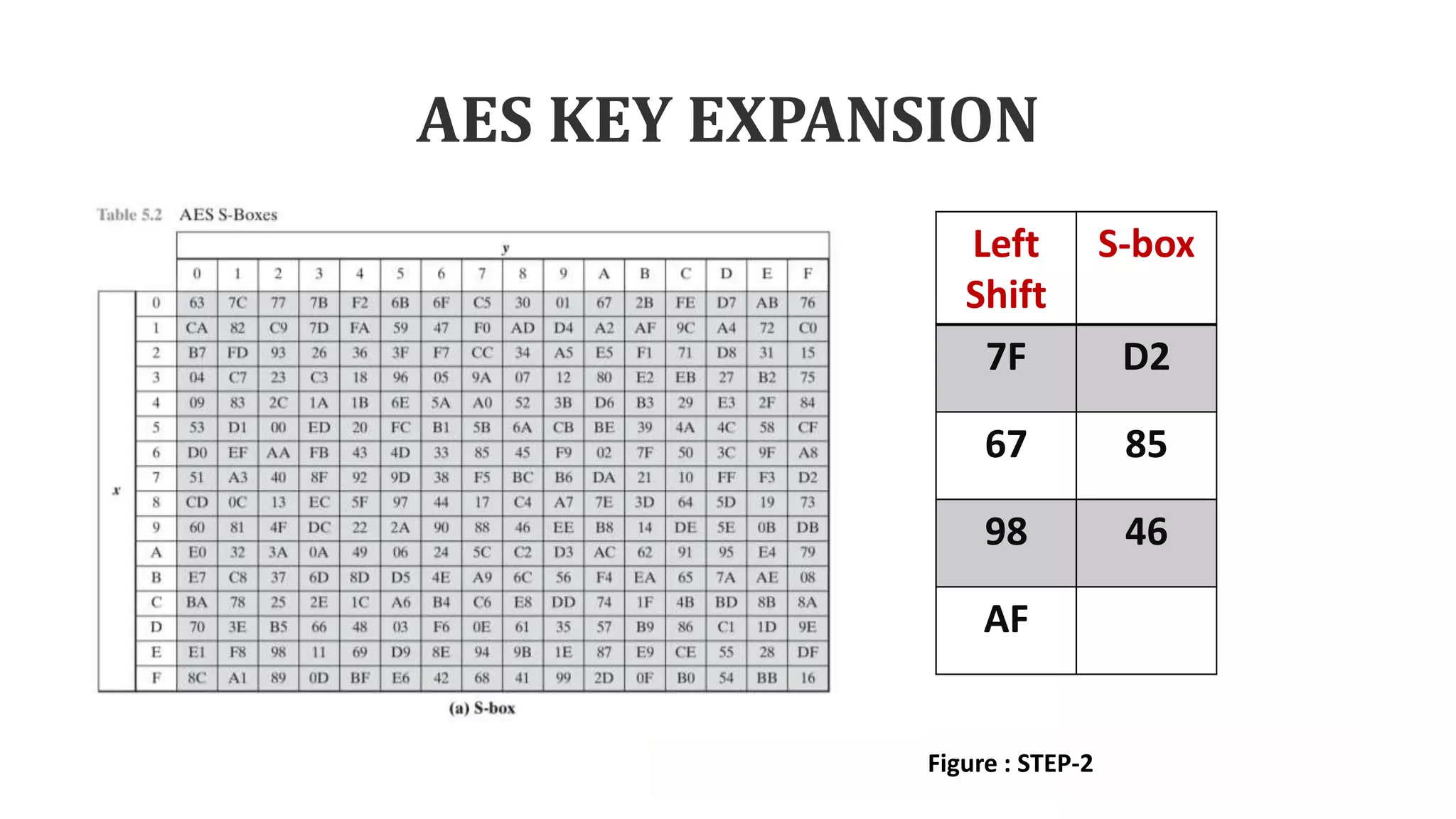
![AES KEY EXPANSION
• The function g defines the complex
and that function consist of some sub
function as follow:
• Step-1: This function performs the
one-byte circular left shift.
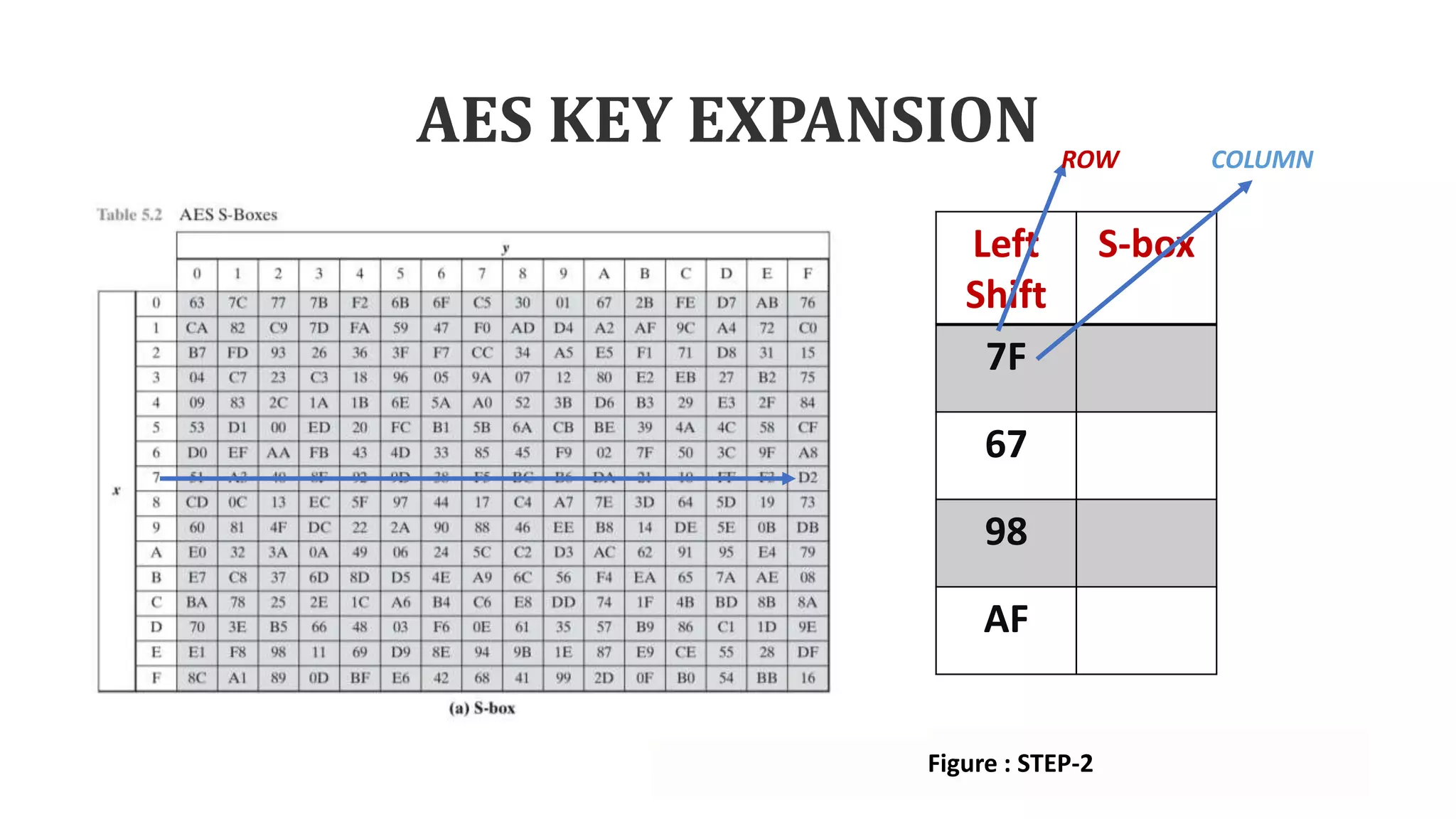
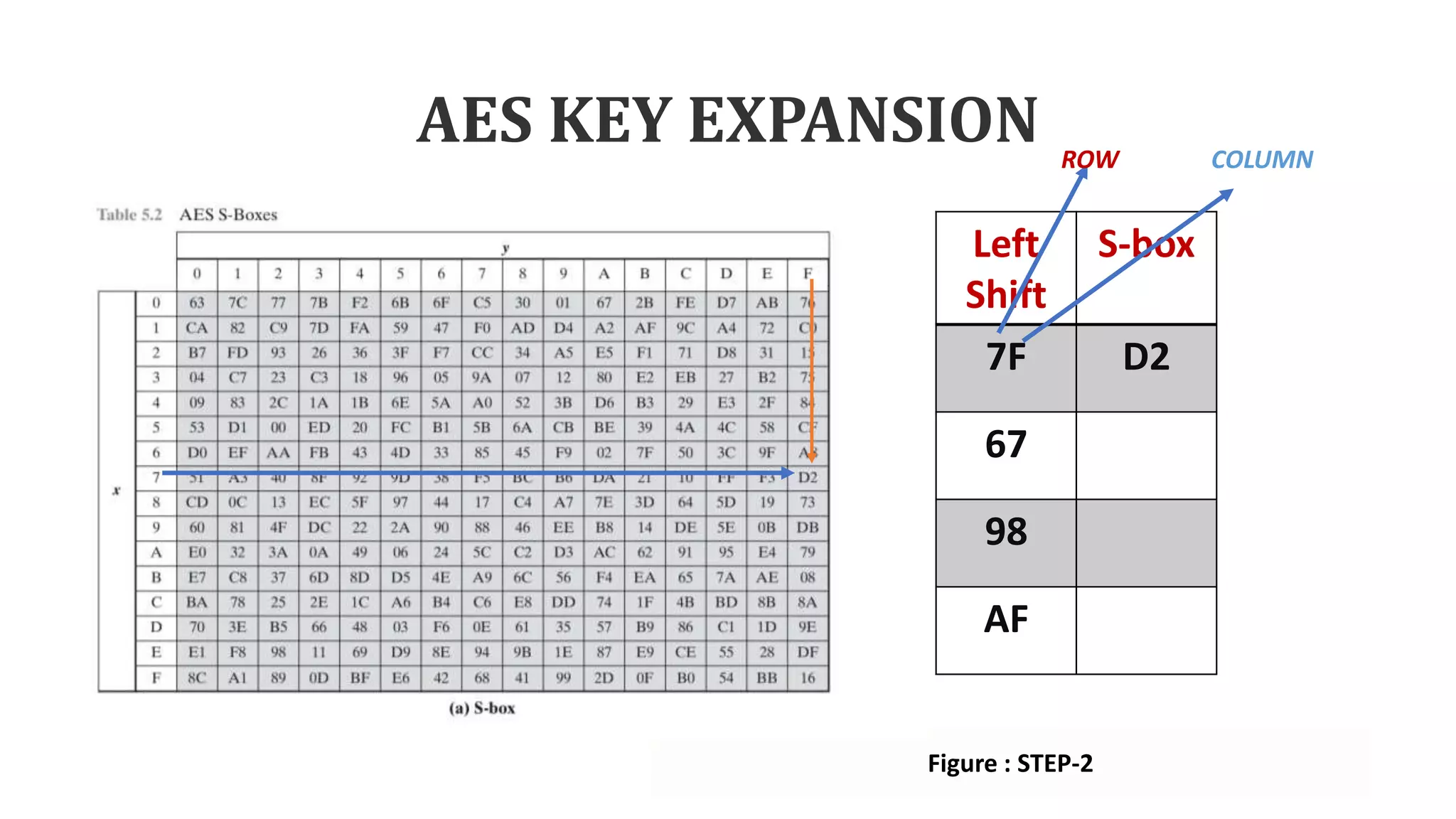
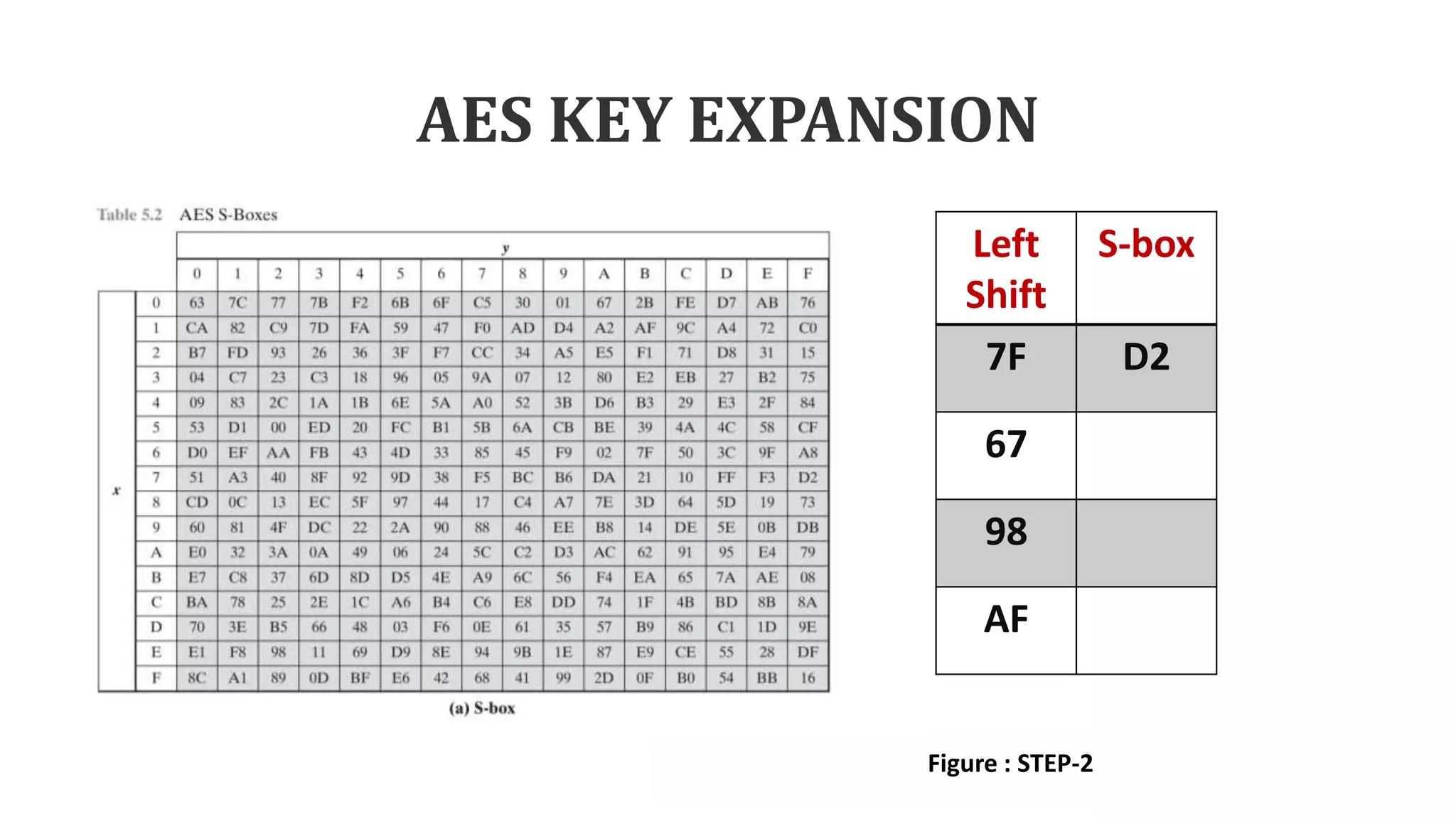
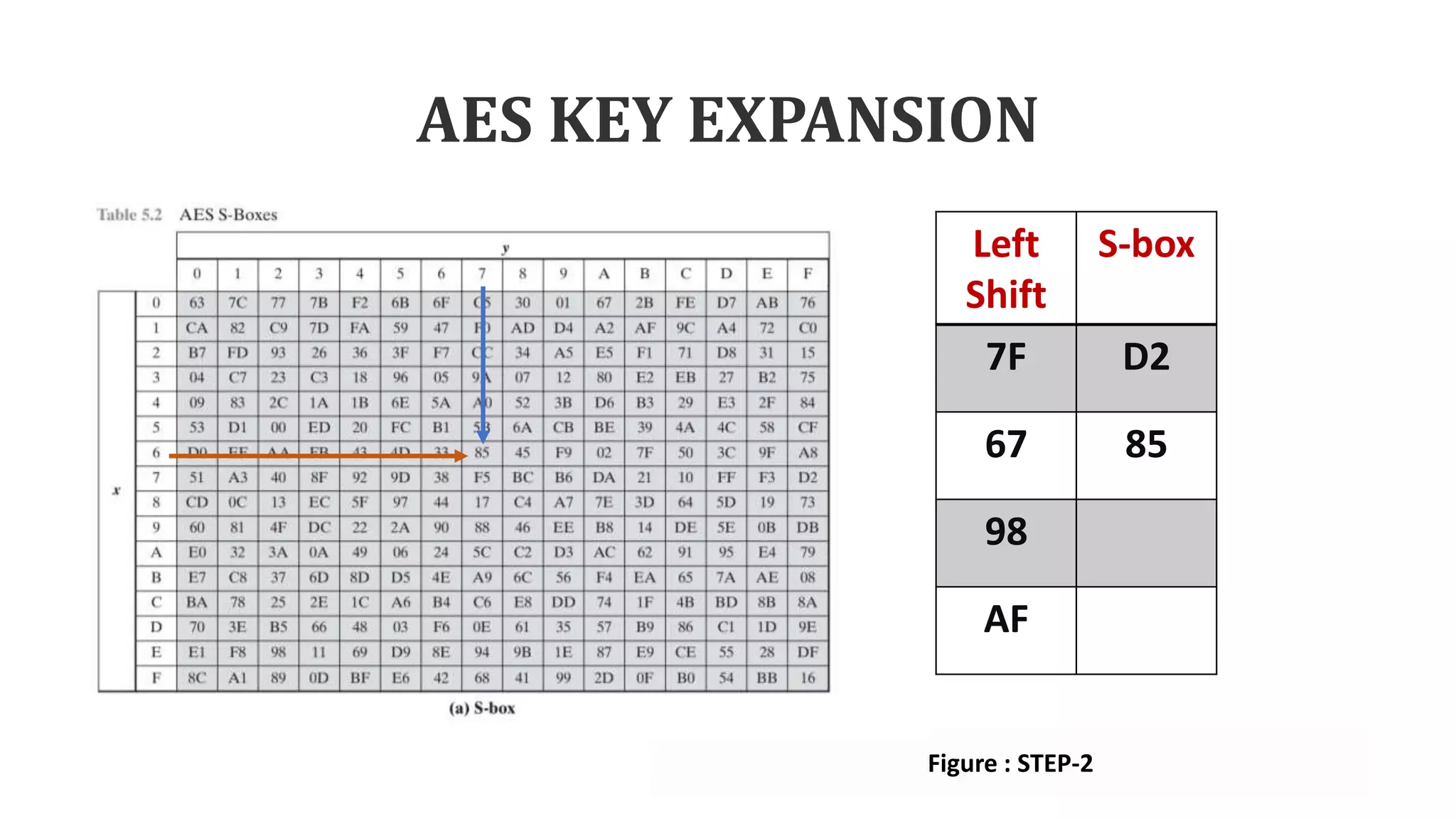
• Step-2: Using S-box each sub word
performs a byte substitution.
• Step-3: Finally result of Rot word and
step 2 is XORed with the round
constant called as Rconst[j].
Figure : STEP-1
W3 Left
Shift
AF 7F
7F 67
67 98
98 AF
W0 w1 w2 w3
0F 47 0C AF
15 D9 B7 7F
71 E8 AD 67
C9 59 D6 98](https://image.slidesharecdn.com/aeskeyexpansion1-230201170256-e6881d6c/75/AES-KEY-EXPANSION-pptx-6-2048.jpg)
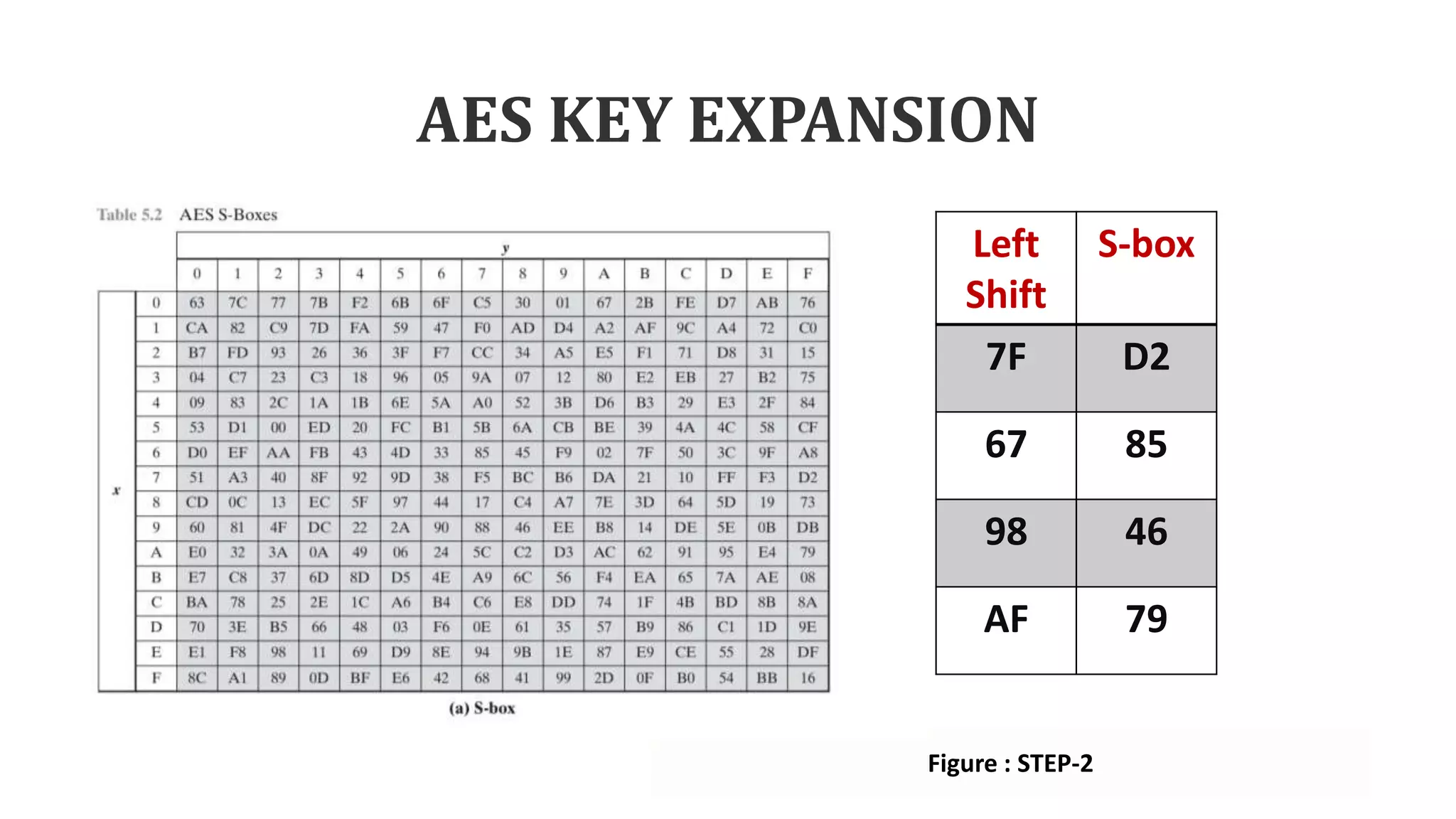
![AES KEY EXPANSION
• The function g defines the complex
and that function consist of some sub
function as follow:
• Step-1: This function performs the
one-byte circular left shift.
• Step-2: Using S-box each sub word
performs a byte substitution.
• Step-3: Finally result of Rot word and
step 2 is XORed with the round
constant called as Rcon[Round].](https://image.slidesharecdn.com/aeskeyexpansion1-230201170256-e6881d6c/75/AES-KEY-EXPANSION-pptx-15-2048.jpg)
![AES KEY EXPANSION
w0 w1 w2 w3
0F 47 0C AF
15 D9 B7 7F
71 E8 AD 67
C9 59 D6 98
Left Shift
(Step-1)
S-box
(Step-2)
7F D2
67 85
98 46
AF 79
S-box
(Step-2)
D2
85
46
79
Rcon(Round)
01
00
00
00
w0
0F
15
71
C9
W4
DC
90
37
B0
Step-3: Finally result of Rot word
and step 2 is XORed with the
round constant called as
Rcon[Round].](https://image.slidesharecdn.com/aeskeyexpansion1-230201170256-e6881d6c/75/AES-KEY-EXPANSION-pptx-16-2048.jpg)