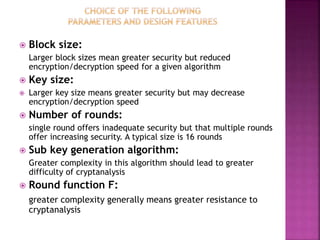
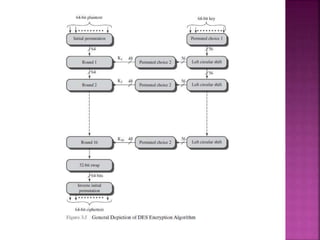
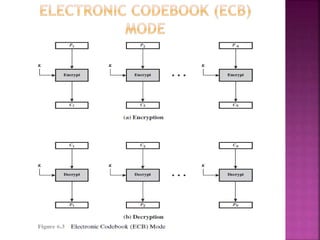
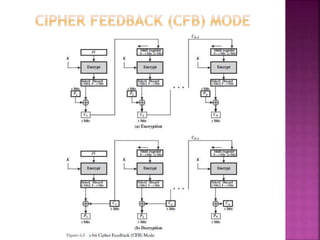
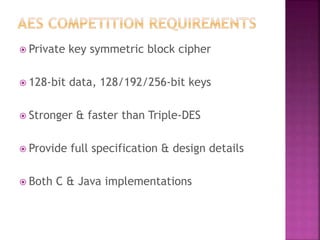
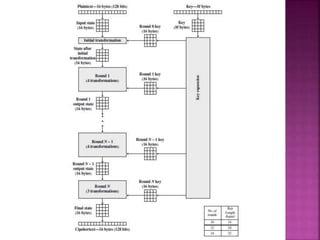
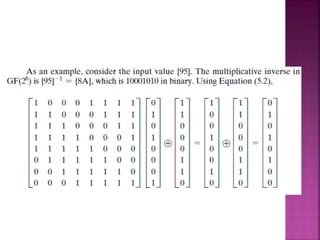
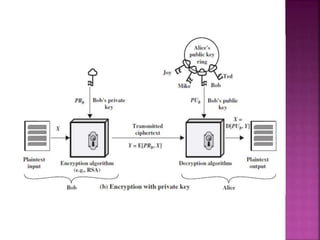
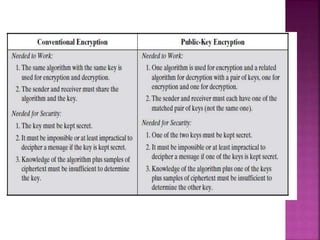
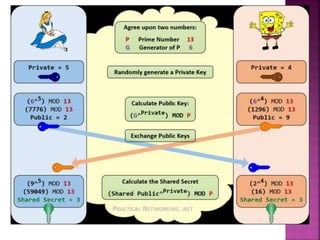
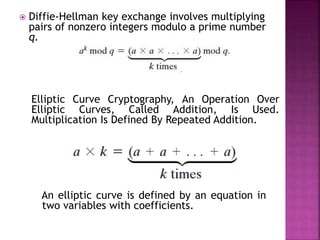
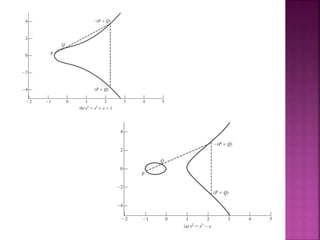
The document discusses stream ciphers and block ciphers. It explains that stream ciphers encrypt data bit-by-bit or byte-by-byte, requiring a randomly generated keystream, while block ciphers encrypt fixed-length blocks, allowing for broader applications. It then focuses on the Feistel cipher structure for block ciphers, proposed by Feistel to approximate an ideal block cipher for large block sizes. The Feistel structure uses a product cipher approach involving substitutions and permutations to provide diffusion and confusion and resist statistical cryptanalysis.