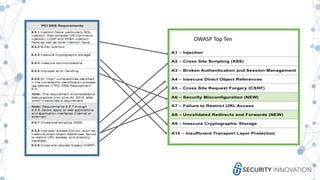
The webinar discusses strategies to mitigate risks associated with third-party developers by emphasizing the importance of security assessments, integrity checks, and establishing clear contractual obligations. It highlights the need for ongoing training, communication, and collaboration between internal teams and third-party suppliers to ensure security is embedded throughout the software development lifecycle. Key recommendations include threat modeling, vulnerability management, and proactive engagement to address potential risks before and after software delivery.