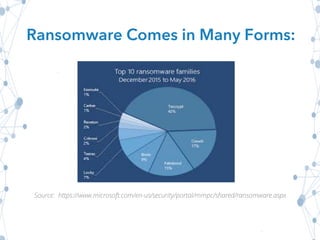
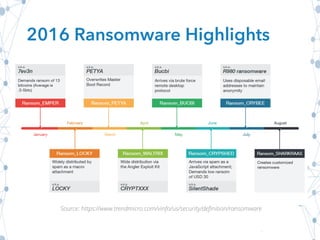
This document outlines ransomware, a malicious software that locks victims out of their computers and demands payment for access restoration, often citing real-world examples like hospital attacks. It provides guidance for potential victims on steps to take when infected, emphasizing not to pay the ransom, alongside general security best practices to prevent attacks. The document also highlights the importance of user education, regular backups, and maintaining up-to-date software to defend against ransomware threats.