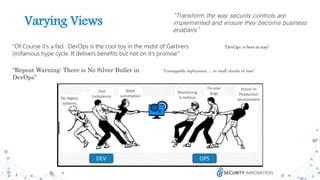
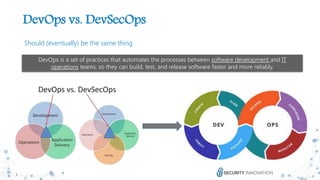
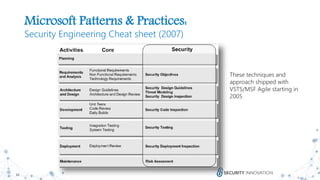
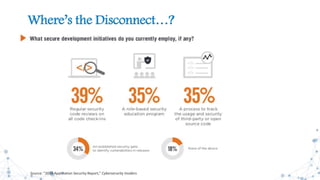
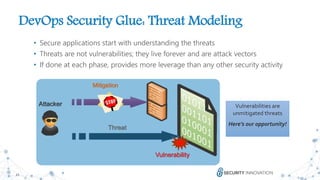
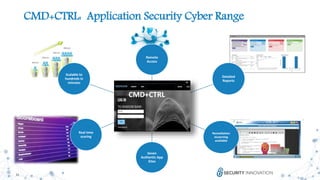
The document discusses the evolution and revolution of secure DevOps practices, emphasizing the importance of integrating security into the software development lifecycle. It highlights the need for cross-functional collaboration among development, operations, and security teams, as well as best practices for resilient software development. Additionally, it points out potential challenges such as over-automation and knowledge dilution, and stresses the necessity of automating processes while maintaining manual inspections for high-risk features.