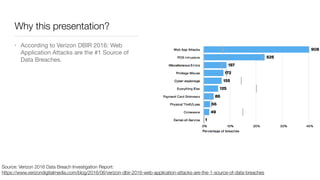
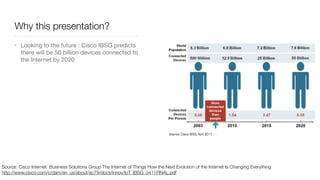
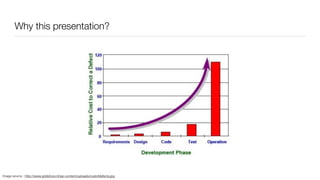
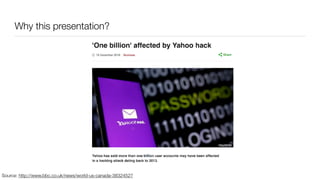
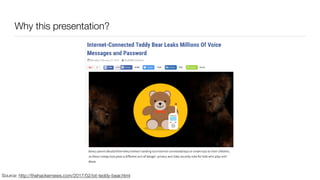
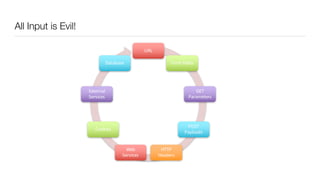
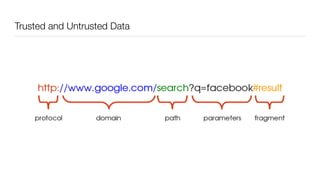
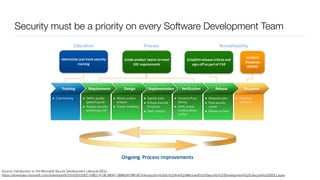
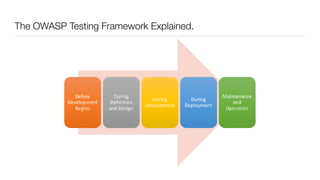
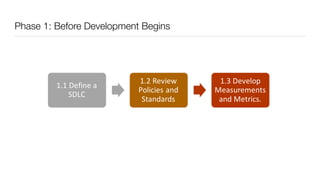
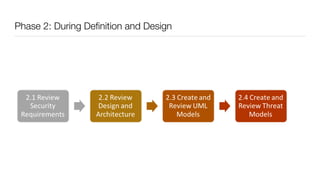
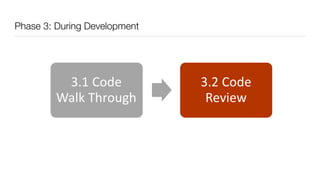
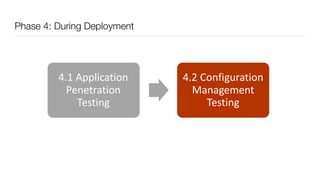
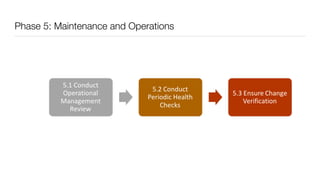
The document discusses the importance of application security testing, highlighting the need for software engineers to understand security principles given that web application attacks are a leading source of data breaches. It outlines the fundamental concepts of information security, the challenges of implementing security in software development, and the collaborative responsibility of all team members to prioritize security. It also emphasizes various phases of security testing and resources available for improving application security practices.