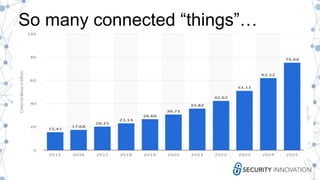
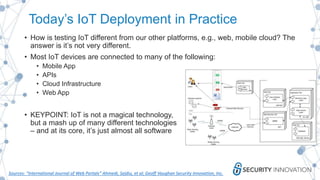
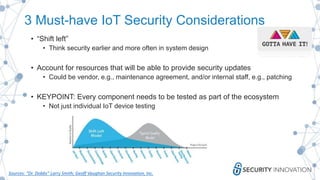
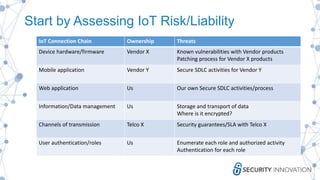
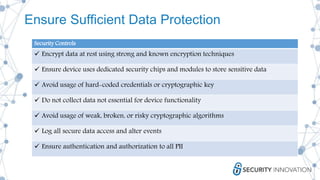
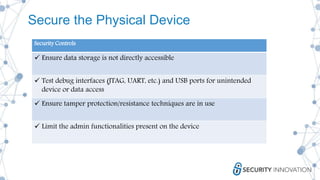
This document discusses the security risks associated with Internet of Things (IoT) devices, highlighting incidents like the Mirai botnet attack and vulnerabilities in consumer and medical devices. It emphasizes the importance of risk-based testing and security considerations in IoT deployments, urging manufacturers to build security into devices from the outset. Key recommendations include robust data protection, proper authentication, and ongoing monitoring of connected devices to mitigate risks.