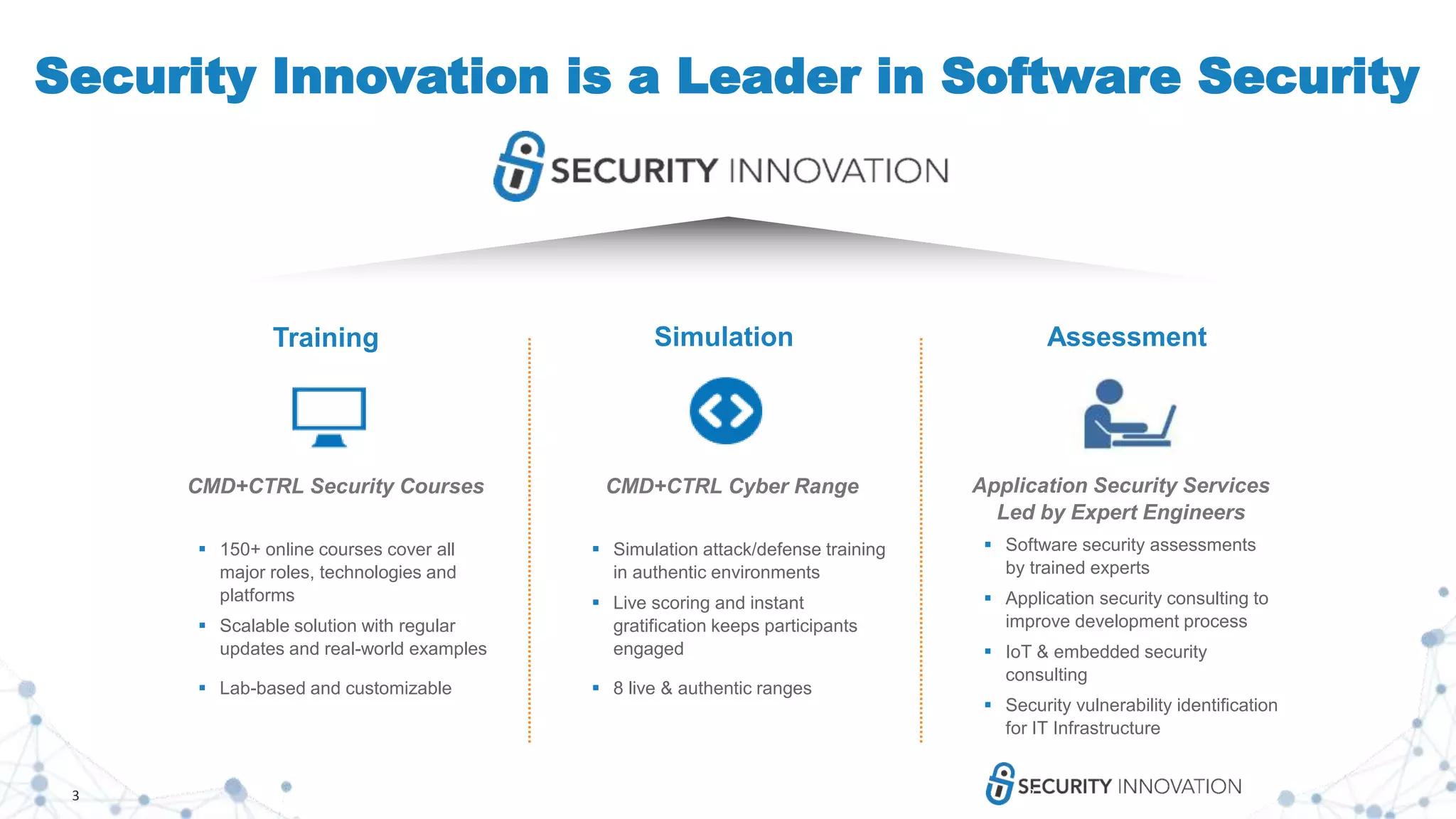
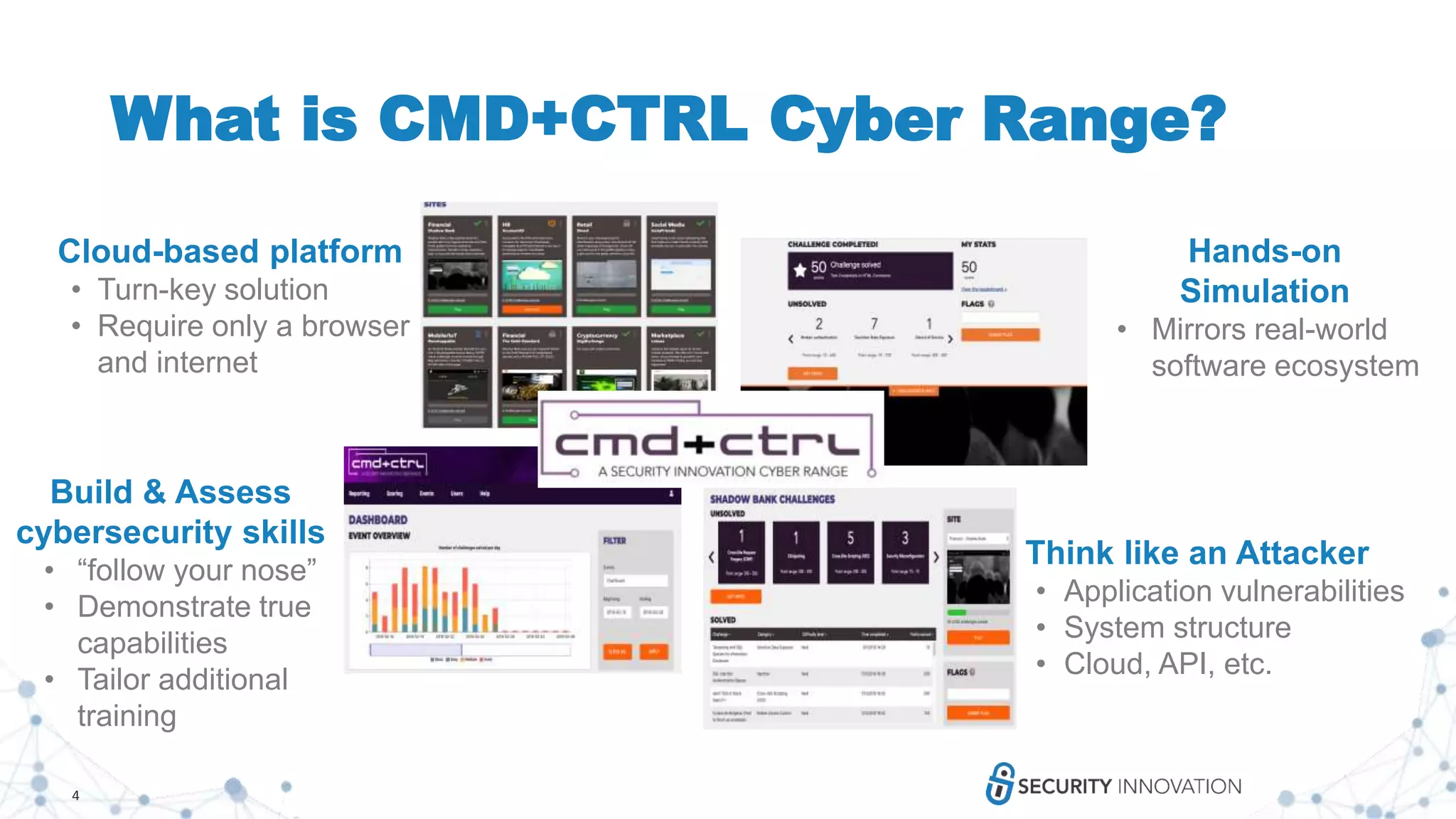
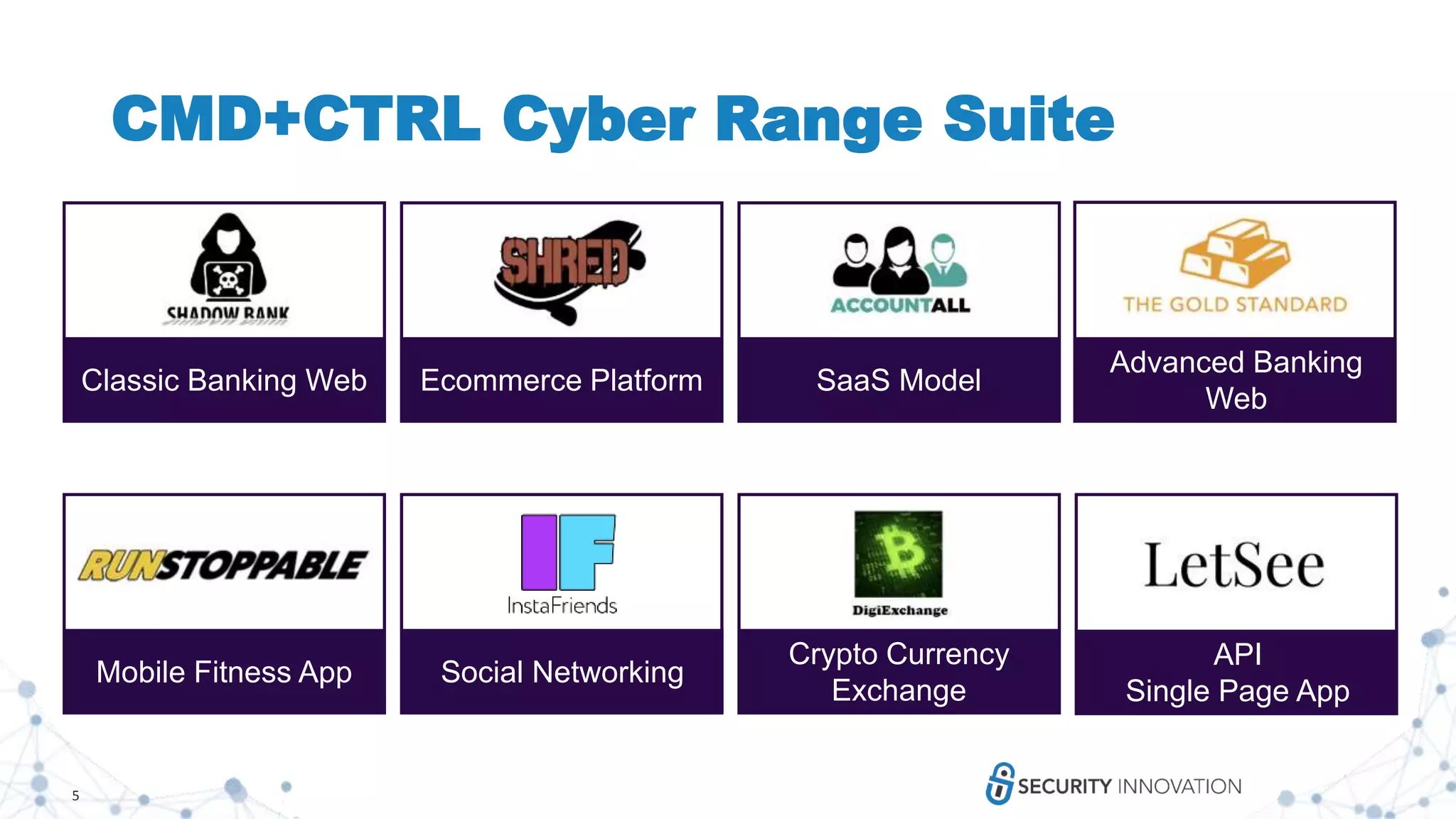
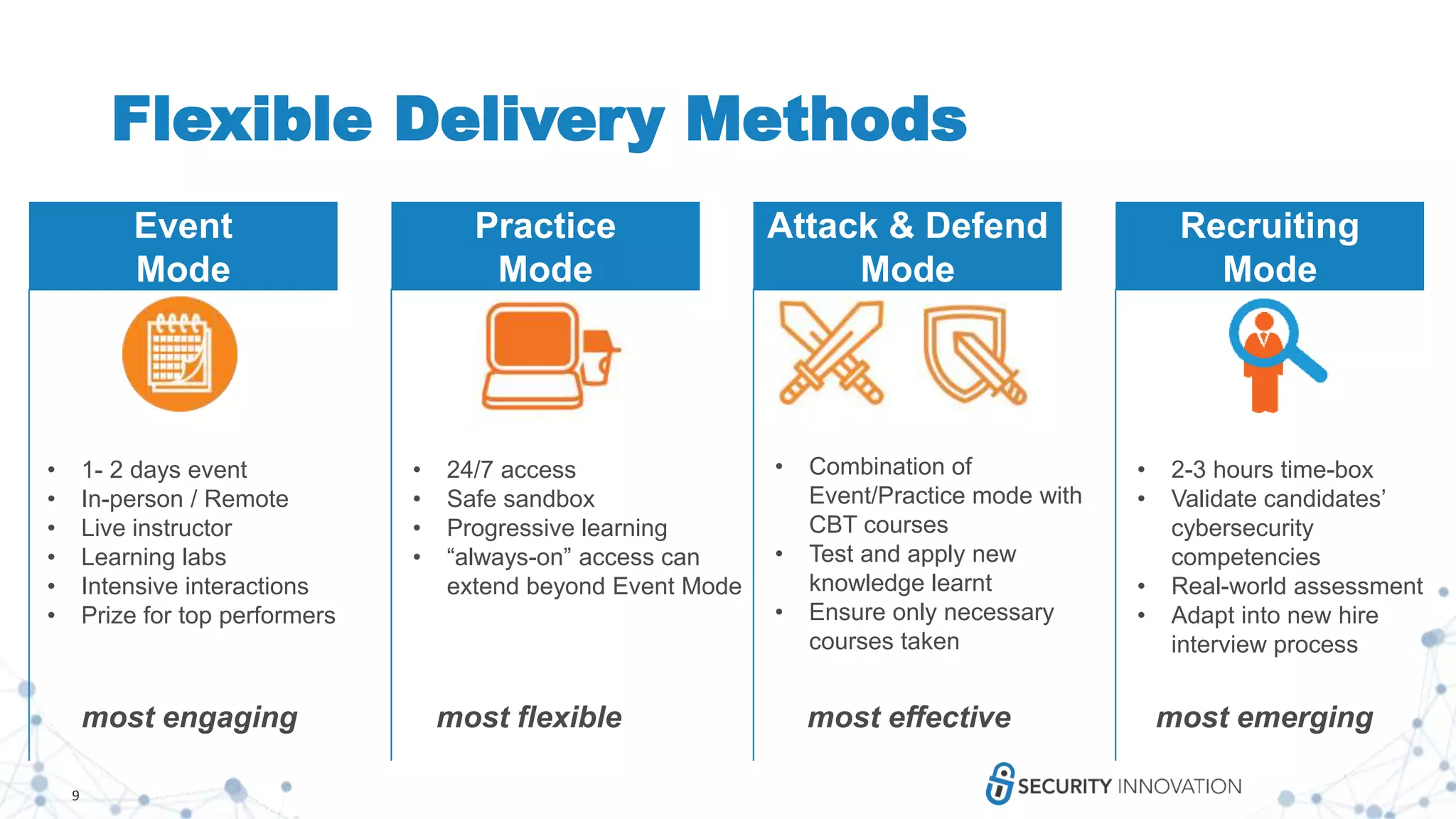
Security Innovation is a leader in software security that provides various security services and training solutions. Their CMD+CTRL Cyber Range is a cloud-based cybersecurity simulation and training platform that allows users to build and assess their skills through hands-on practice in simulated real-world software environments and scenarios. The platform aims to improve cybersecurity skills in a more engaging and effective manner compared to traditional cyber ranges.