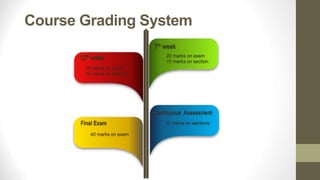
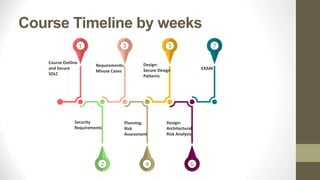
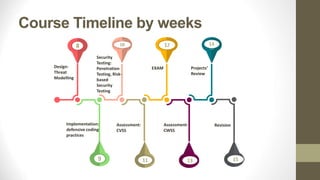
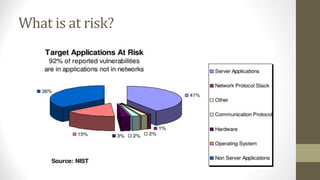
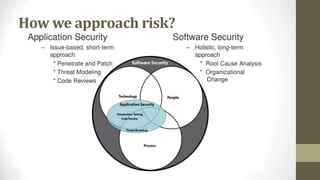
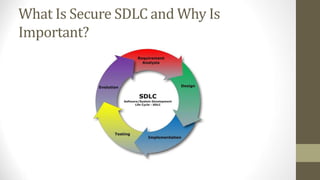
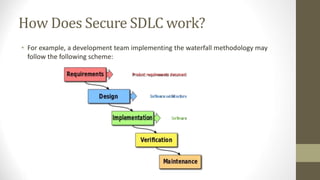
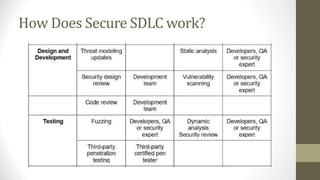
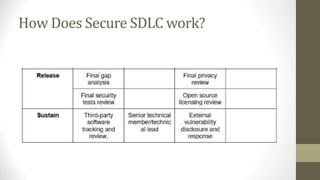
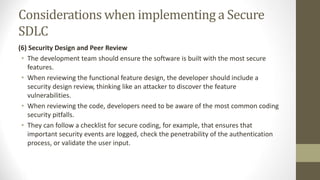
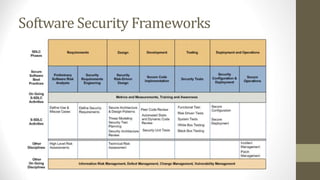
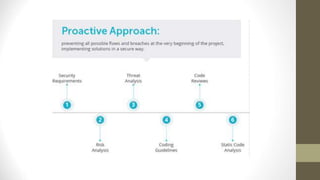
This document outlines a secure software development course. The course goals are to explain computer security needs and requirements, introduce security best practices, and present techniques for evaluating security solutions. It will be graded through exams, assignments, and a final exam. The course material will include a delivered textbook. The timeline shows the course content by week, covering topics like risk assessment, secure design patterns, threat modeling, and security testing. The document also provides the lecturer's contact information and defines key terms like information security risks and software security.