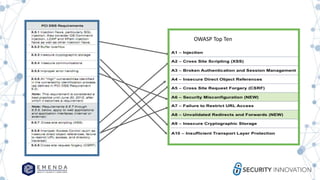
The document discusses the challenges and strategies in securing software development, emphasizing the importance of integrating security into every phase of the software development lifecycle (SDLC). It outlines risks associated with third-party software and the need for clear contractual agreements that define security expectations and training. Additionally, it highlights the necessity of ongoing assessment, threat modeling, and strong collaboration between development and security teams to mitigate vulnerabilities effectively.