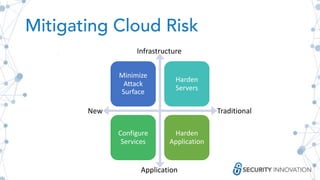
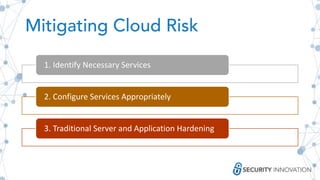
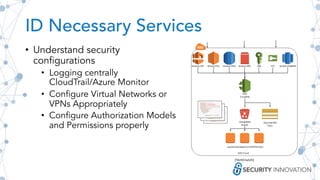
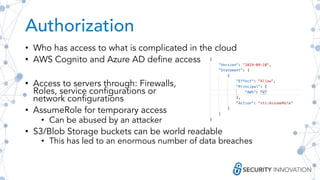
The document outlines best practices for securing cloud environments, emphasizing the need for careful service configuration, minimizing attack surfaces, and conducting regular security assessments. It highlights the importance of understanding authorization/authentication mechanisms and the shared responsibility of compliance and policy in the cloud. Additionally, it discusses the necessity of using infrastructure as code and implementing robust logging and monitoring to enhance overall security.