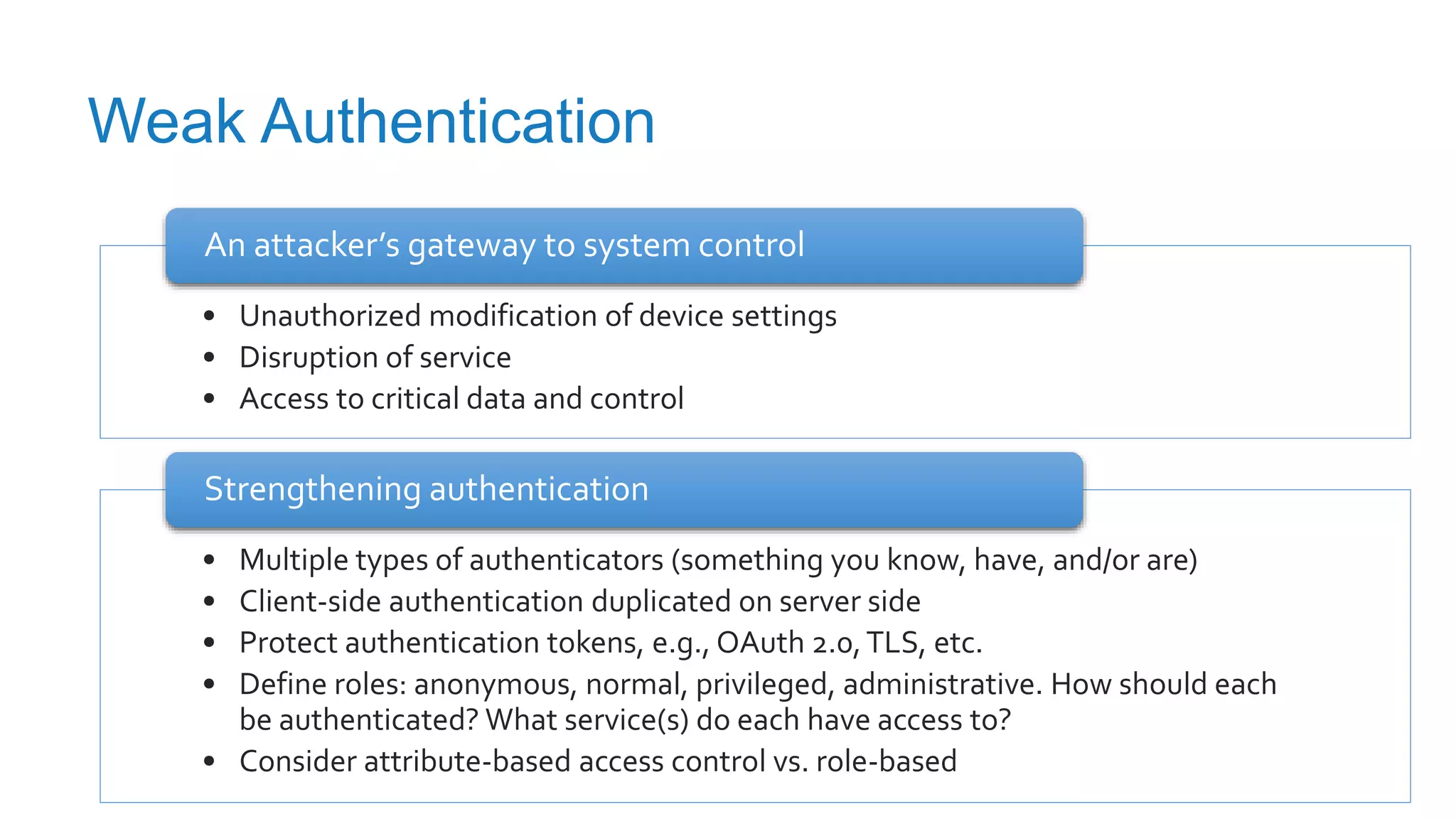
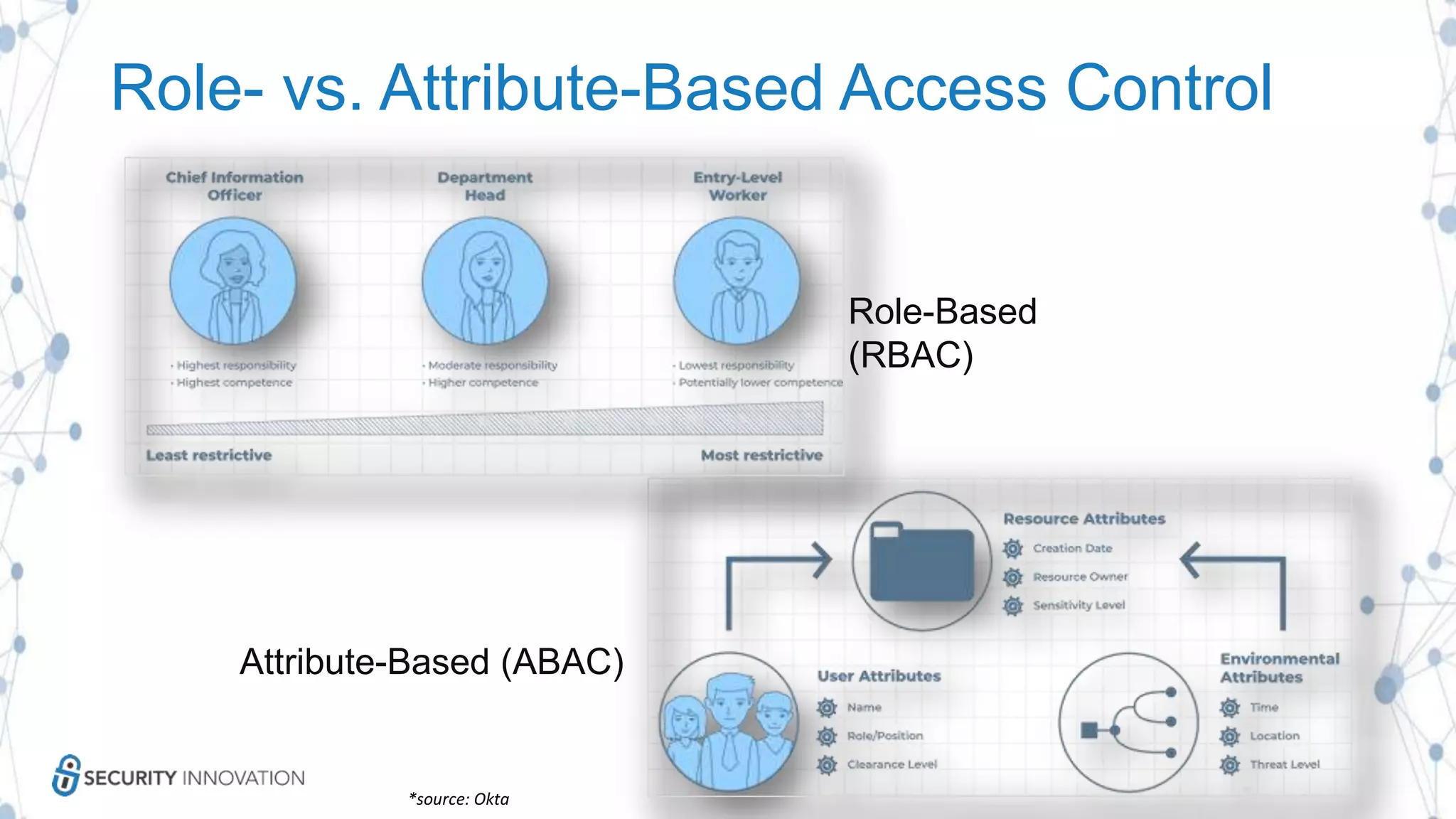
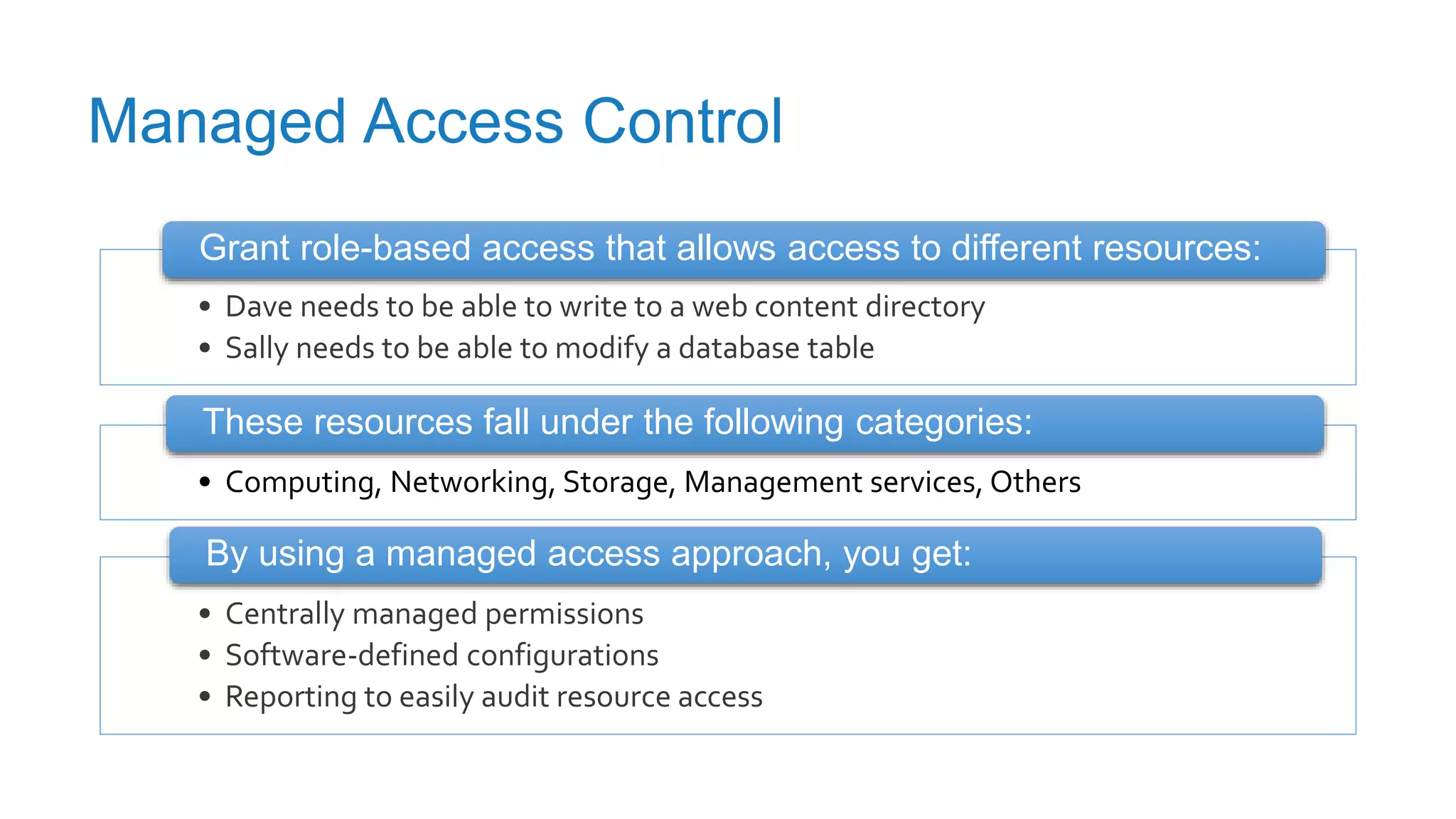
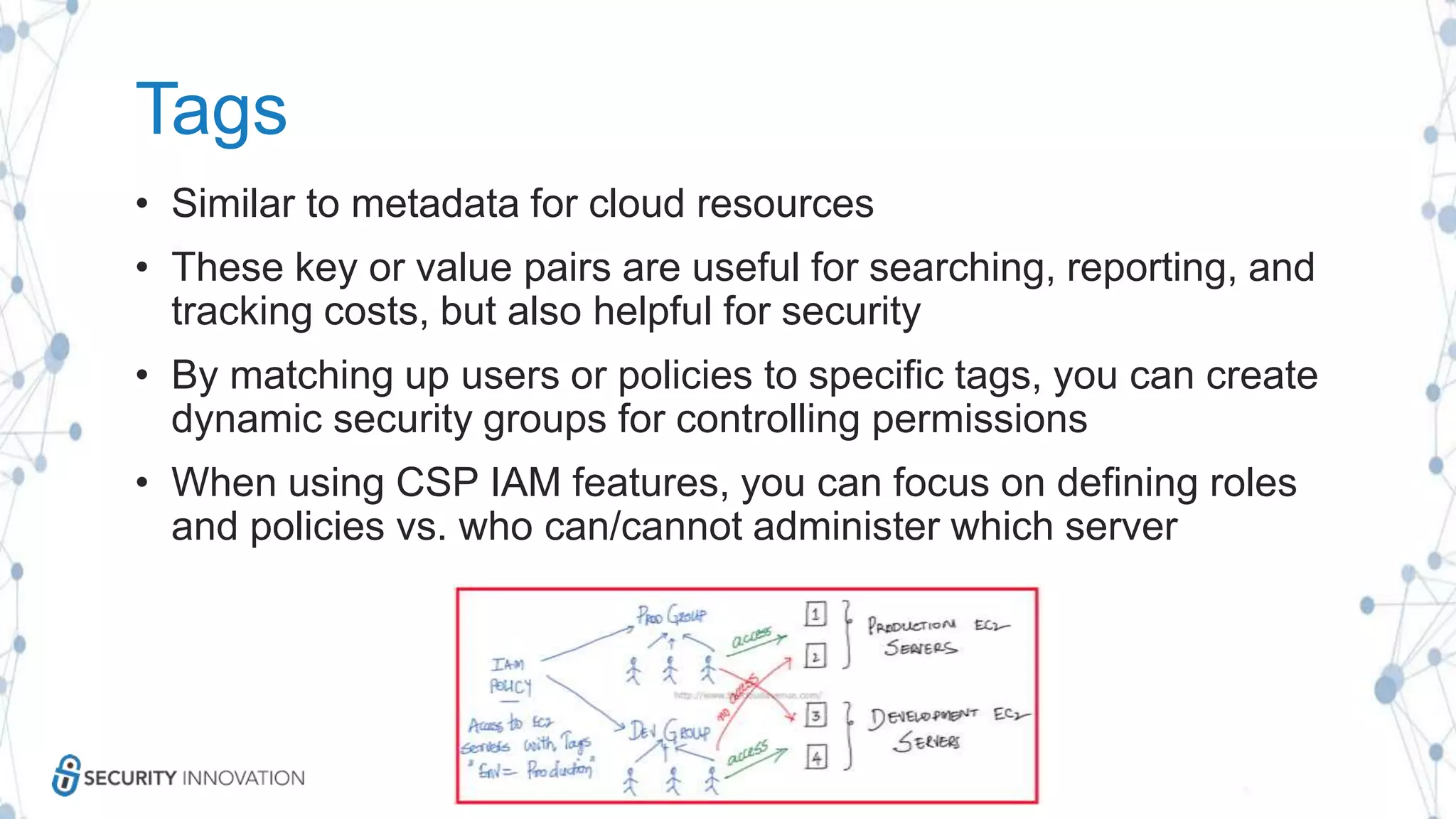
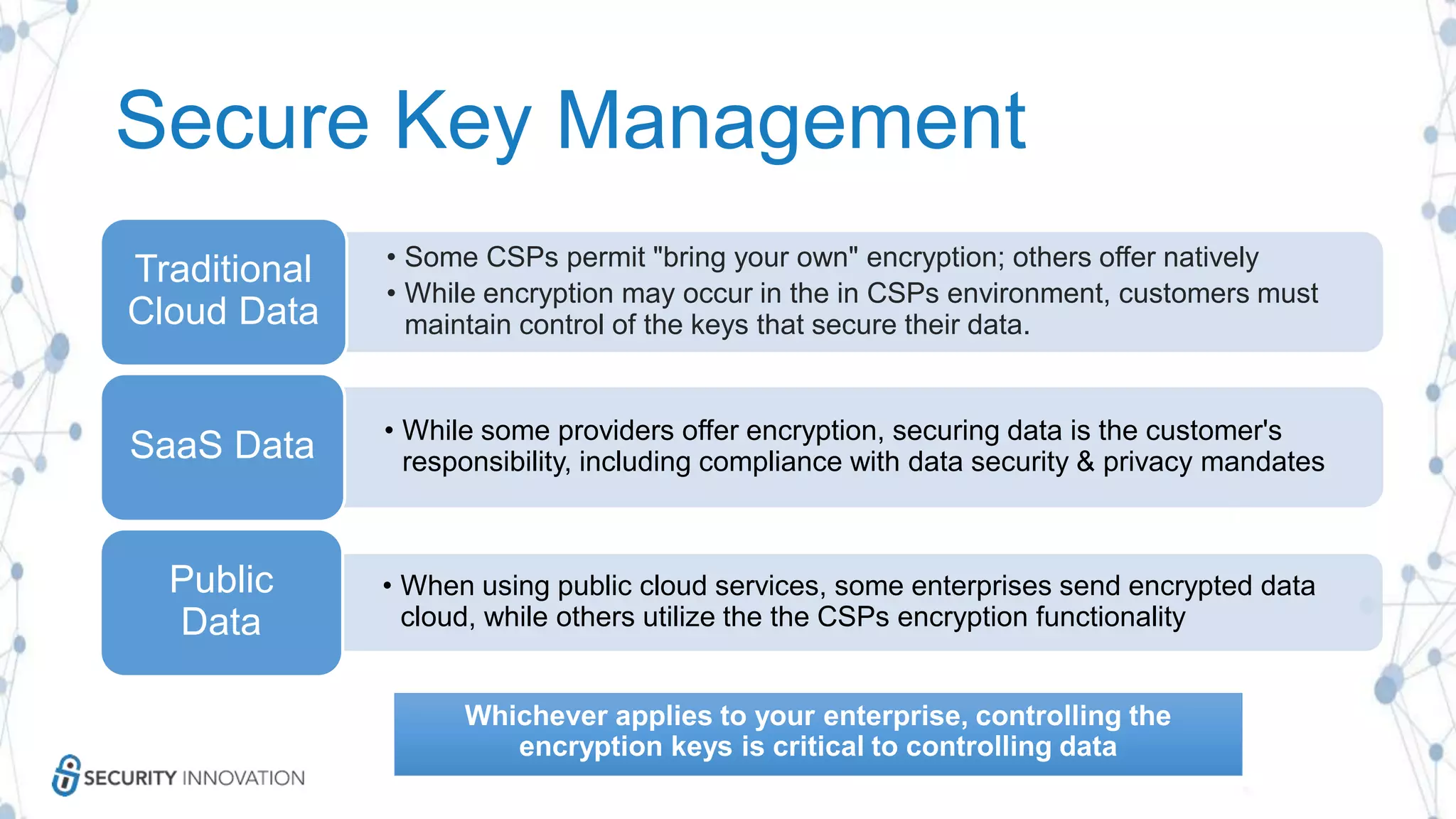
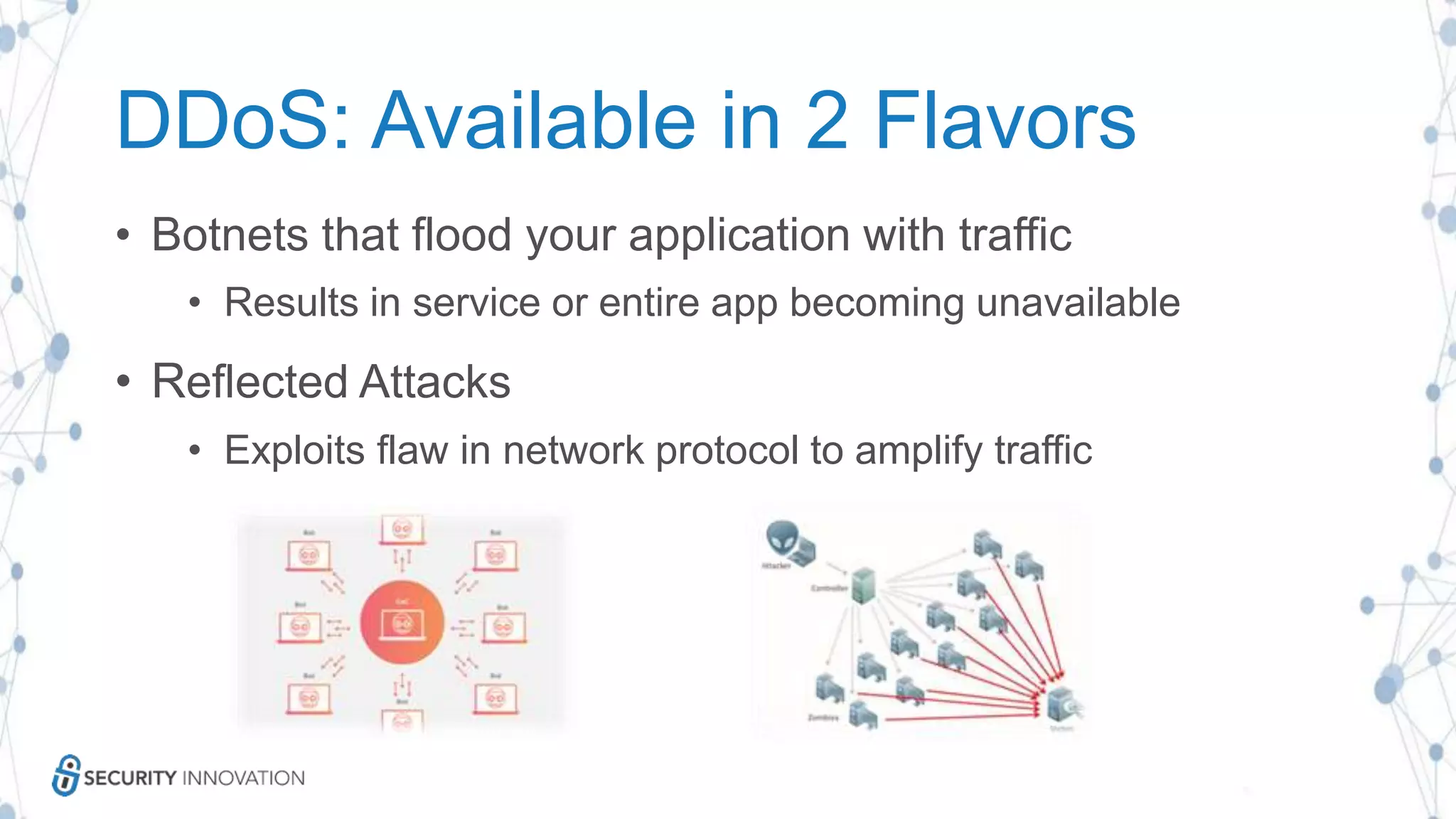
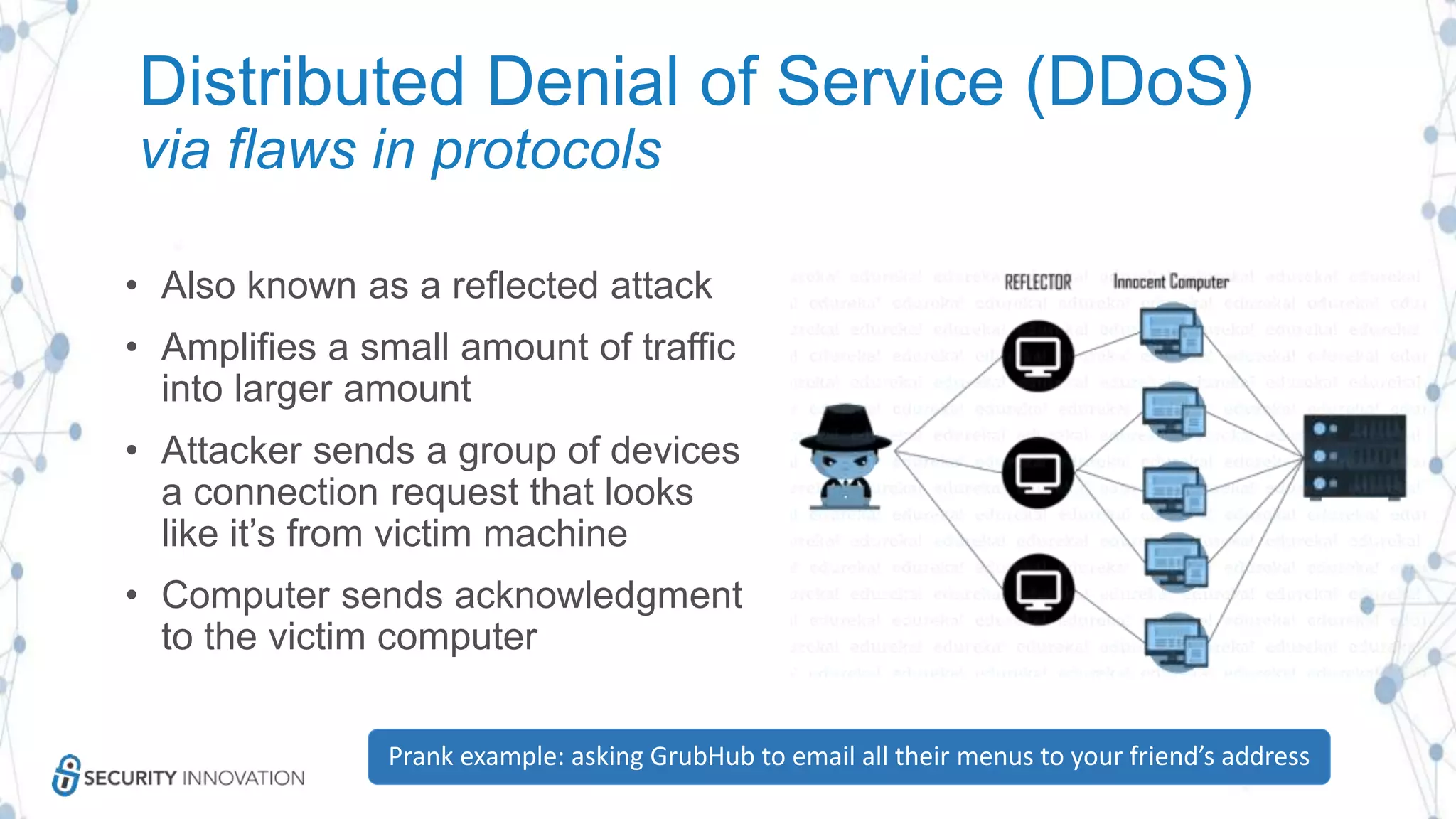
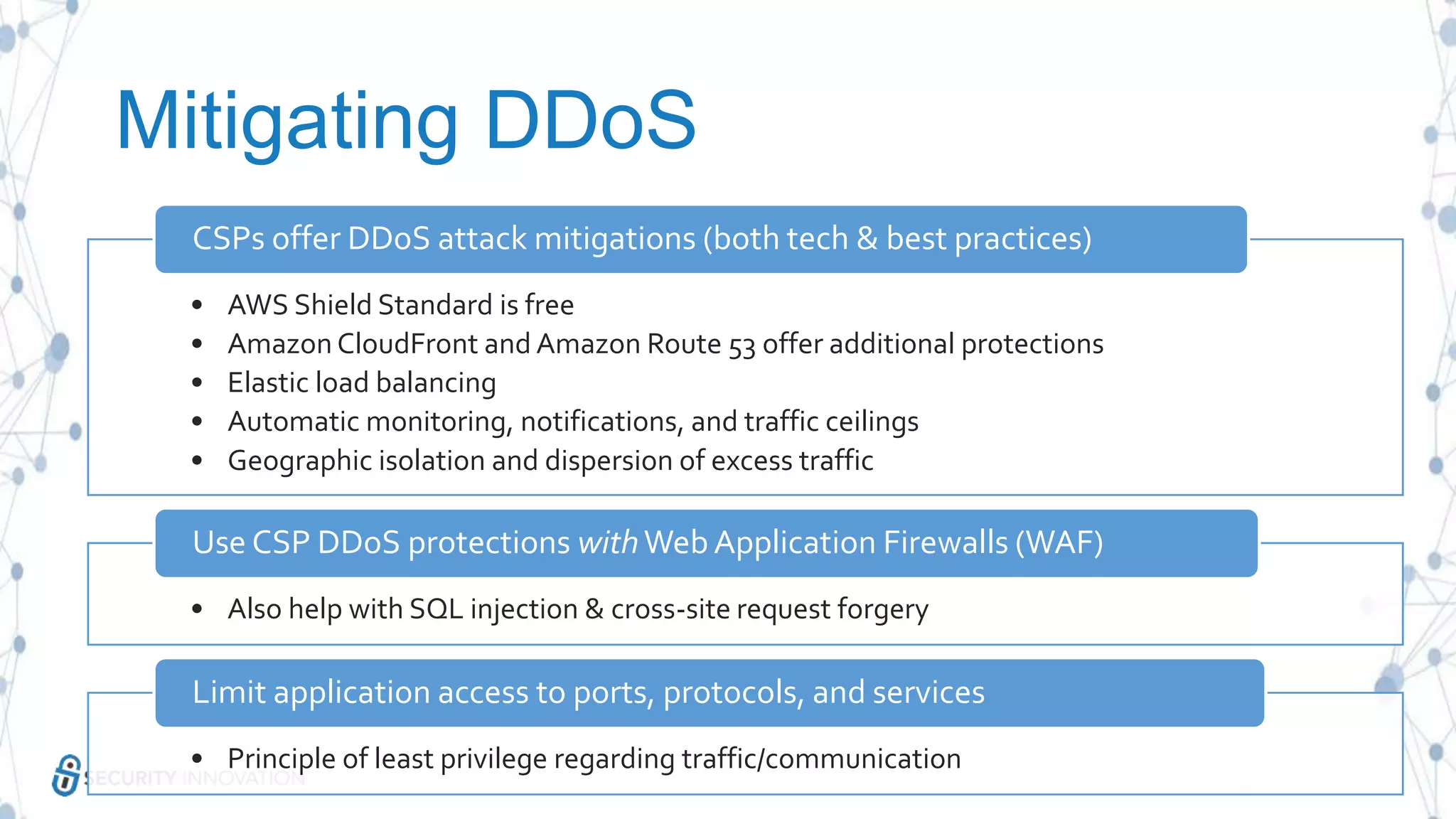
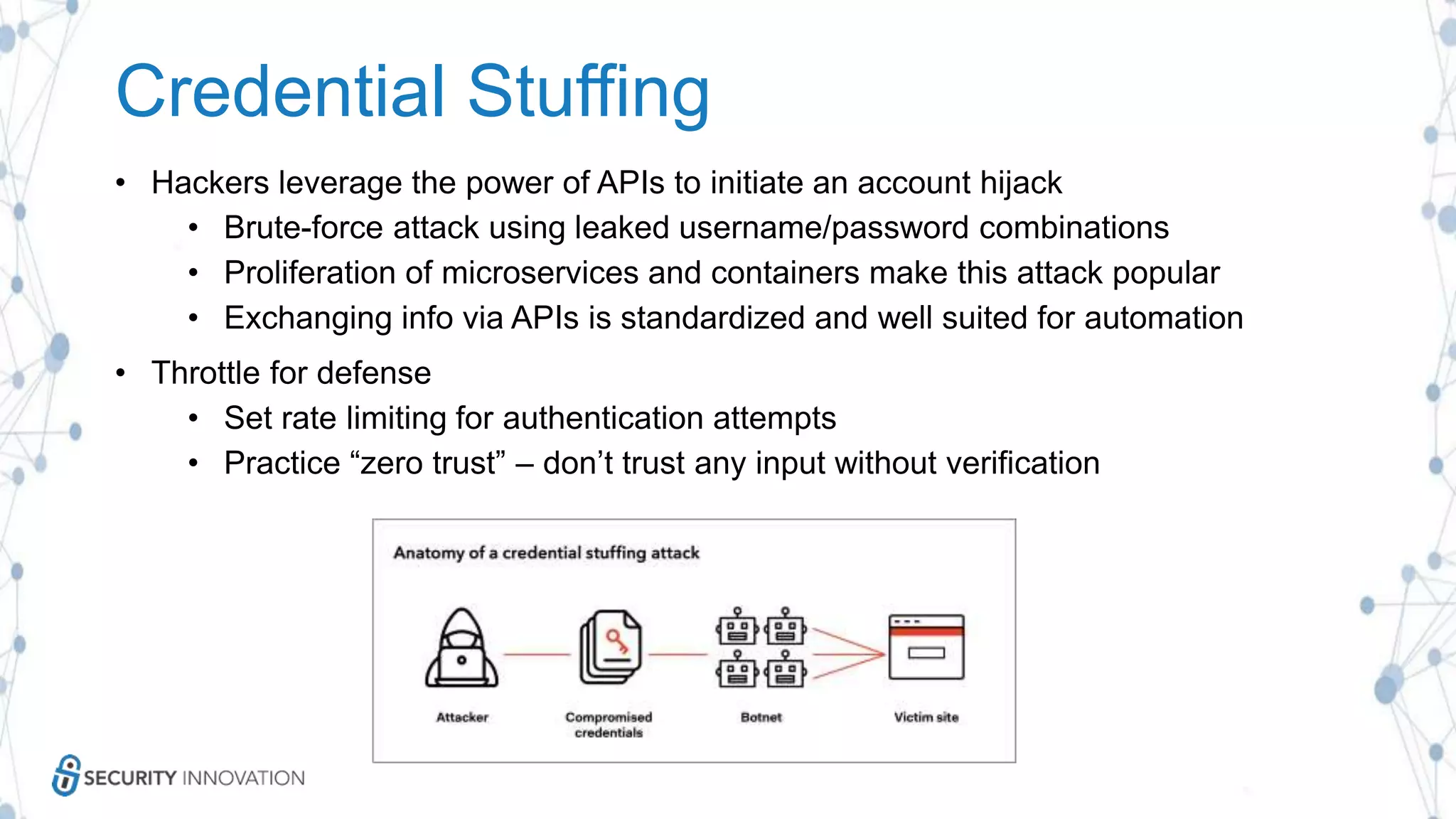
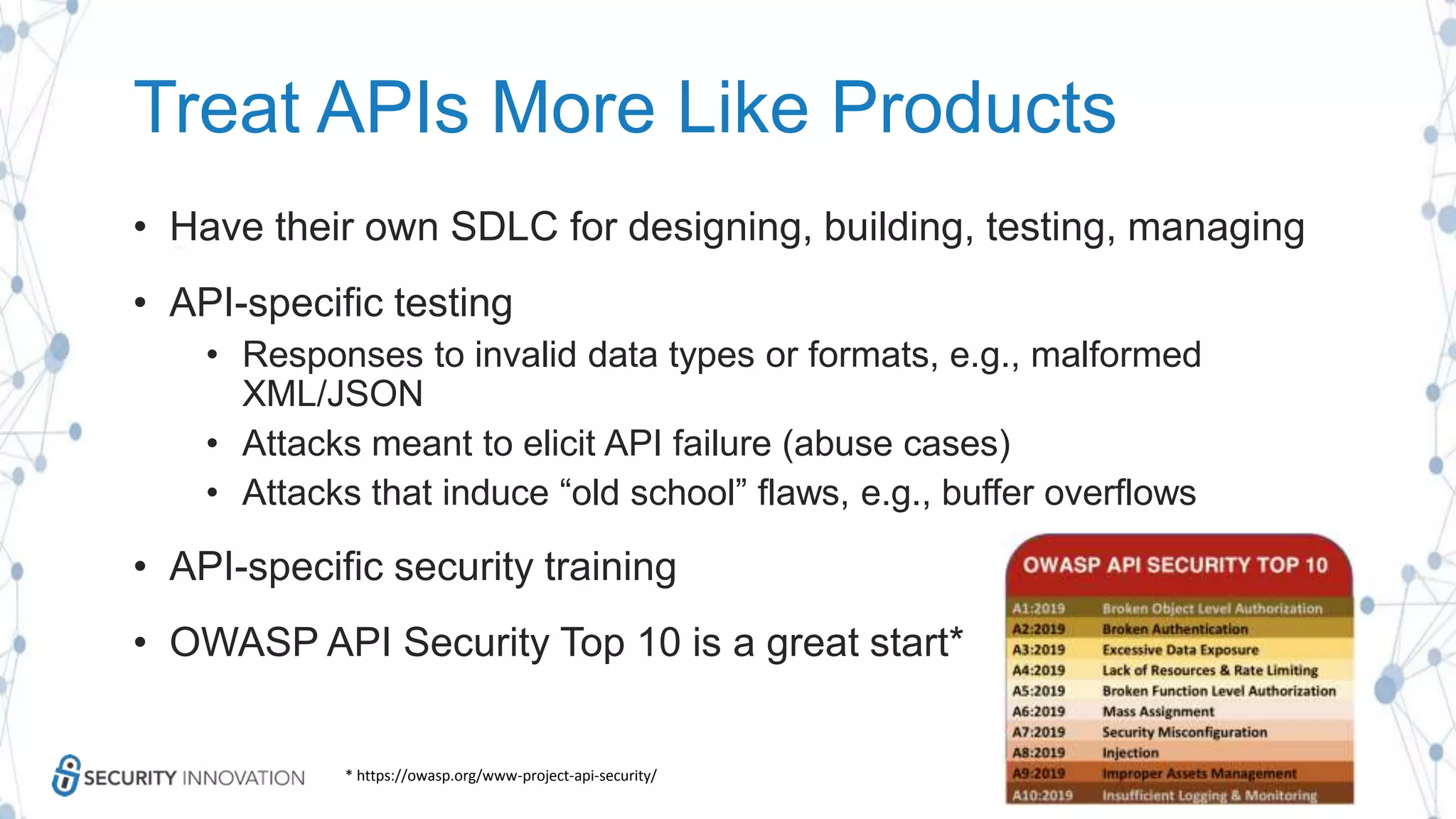
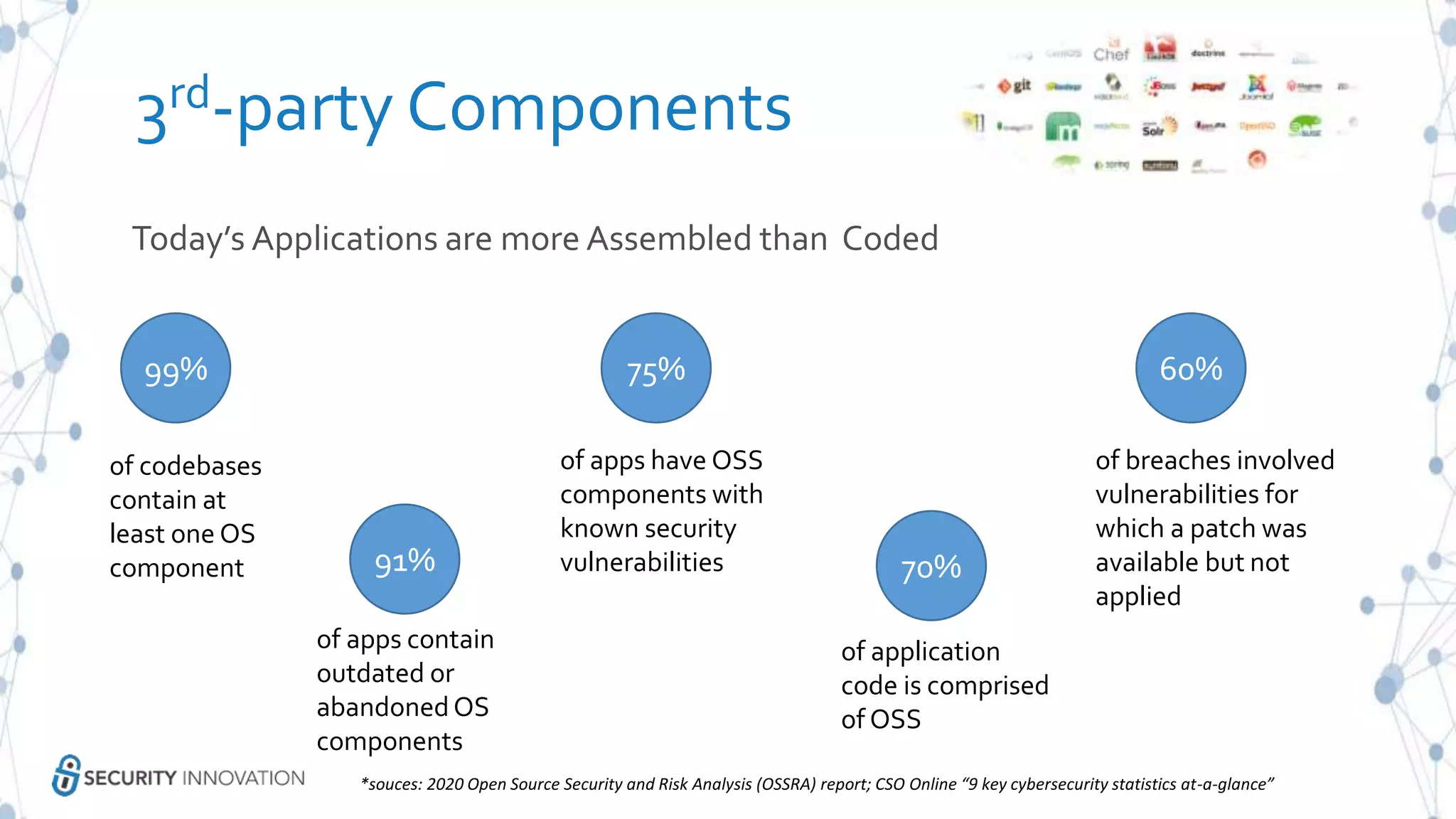
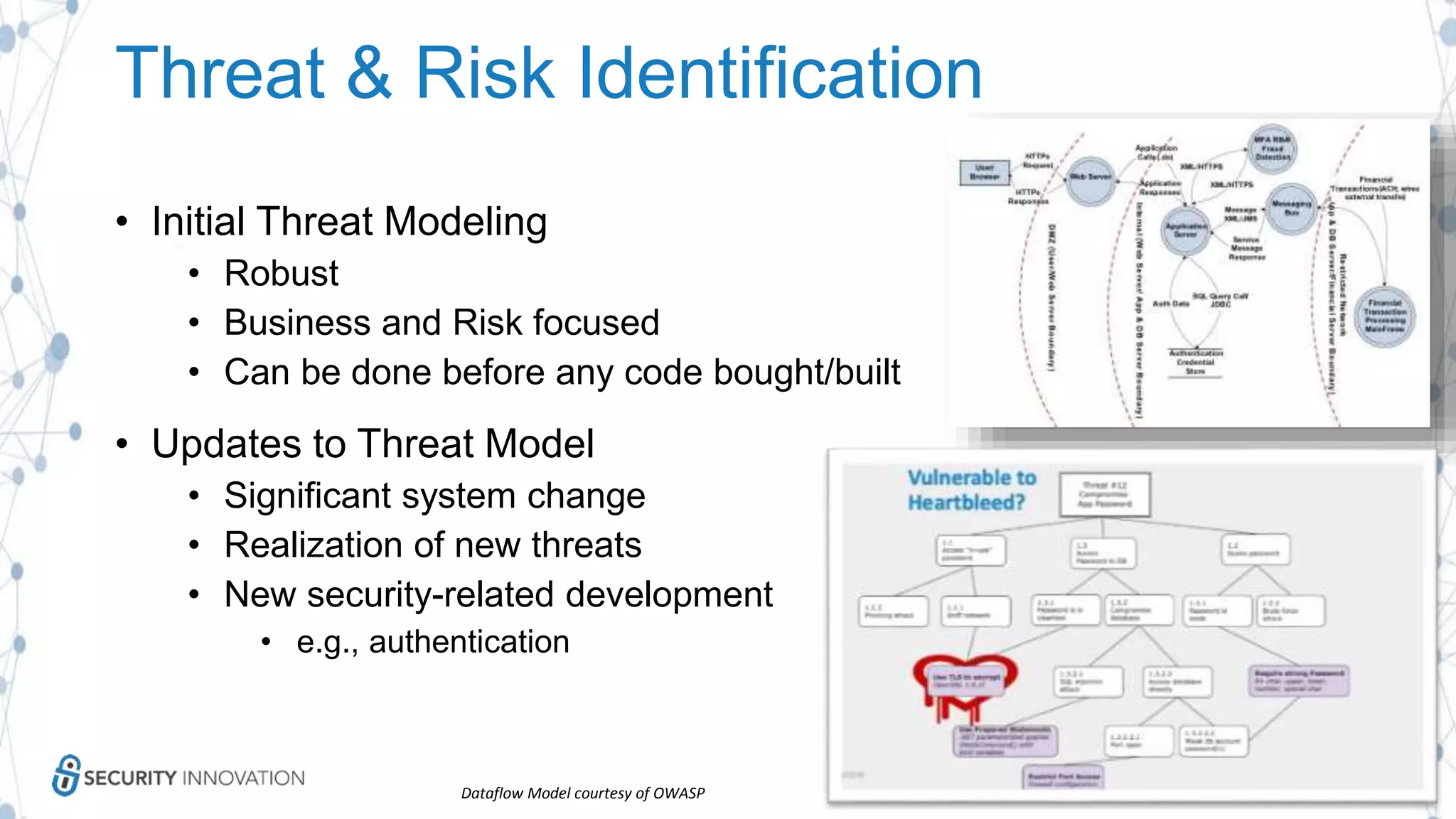
The document discusses securing applications in the cloud, highlighting key topics such as cloud threats and vulnerabilities, authorization and authentication challenges, and mitigation strategies against attacks like DDoS. It emphasizes the importance of proper identity and access management, secure key management, and the usage of third-party components while maintaining stringent security practices. Additionally, it outlines best practices, tools, and methods for improving security posture in cloud environments.