This document summarizes a webinar on privacy secrets and how systems can reveal personal information. It discusses defining privacy, the seven types of privacy, and the differences between privacy and security. It also covers threats to privacy like big data, location tracking, and metadata analysis. The webinar examines data types like PII, PHI, and anonymous/pseudonymous data. It provides examples of data lifecycles and analyzing how data flows through systems and to third parties. The goal is to help organizations understand privacy risks and comply with regulations like GDPR.








![13
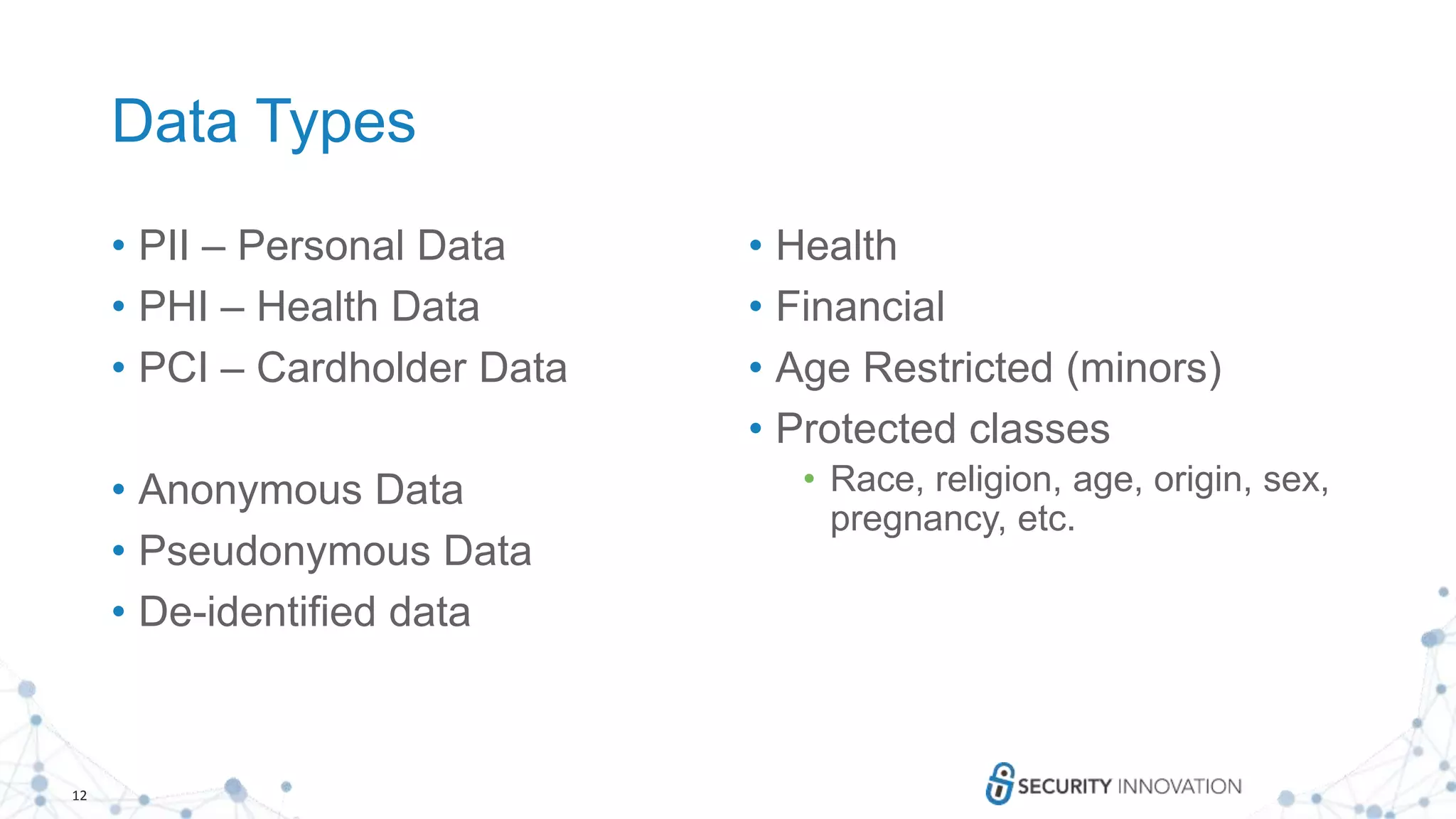
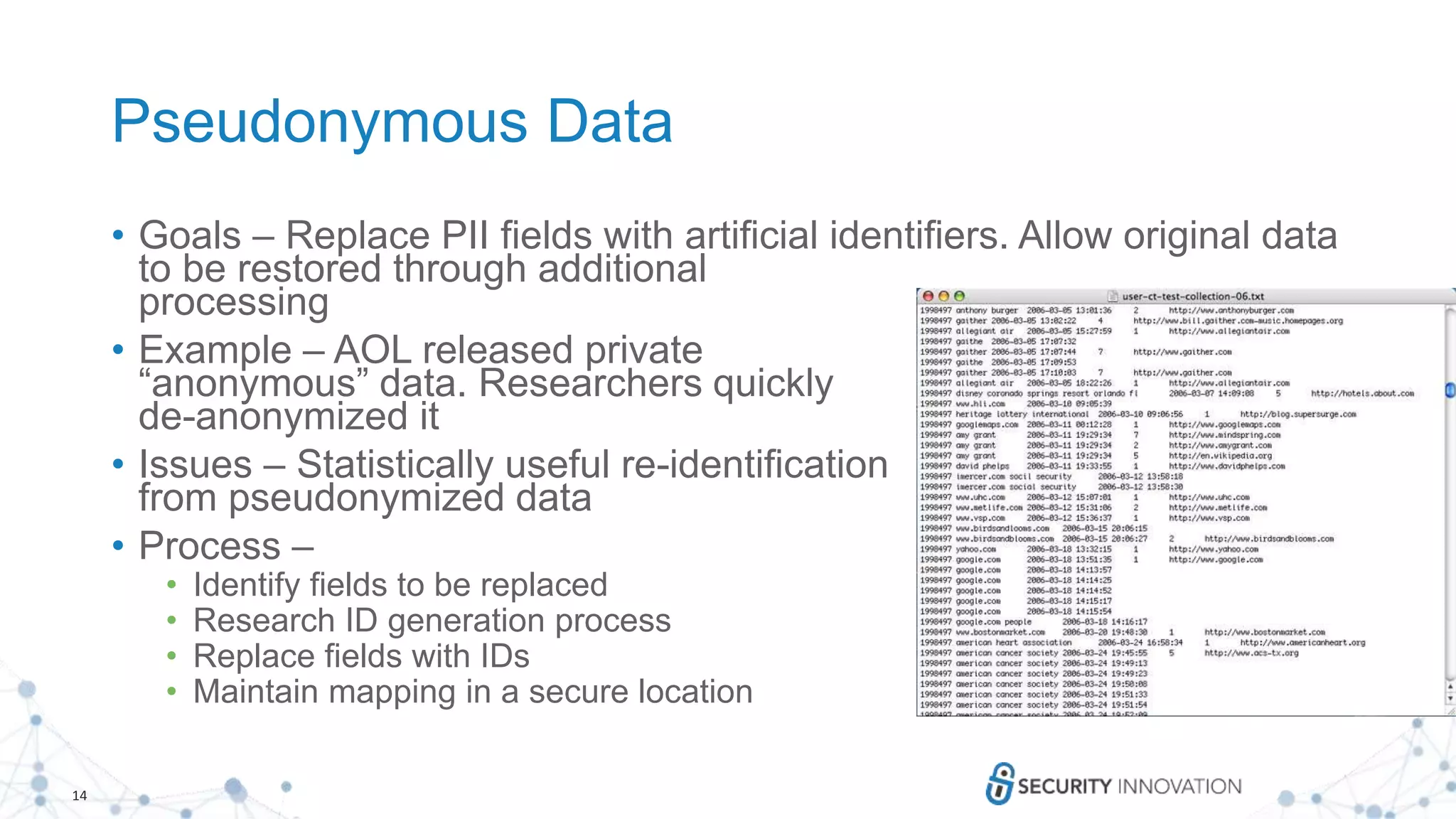
Anonymous Data
• Goal – keep only data that does not allow the original source to
be identified from the information. Irreversible.
• Example – Identifying individuals from
cellphone location data
• Issues
• De-anonymization
• Process: Remove [name, address, post code,
etc.]
• Additionally remove any data that could be used together with other
information that could be used to identify the origin](https://image.slidesharecdn.com/updatedprivacysecretsyoursystemsmaybetelling-190130155844/75/Privacy-Secrets-Your-Systems-May-Be-Telling-13-2048.jpg)
![15
De-identified Data
• Goals – Remove identifiers, but keep core data
• Example – Remove names and SSNs from Health Records to
analyze rate of infection without naming individuals
• Issues – re-identification
• Process –
• Delete or mask personal identifiers [name, SSN, etc.]
• Suppress or generalize quasi-identifiers [date of birth, zip code]](https://image.slidesharecdn.com/updatedprivacysecretsyoursystemsmaybetelling-190130155844/75/Privacy-Secrets-Your-Systems-May-Be-Telling-15-2048.jpg)









