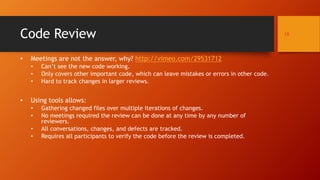
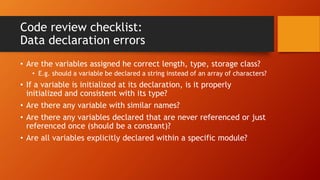
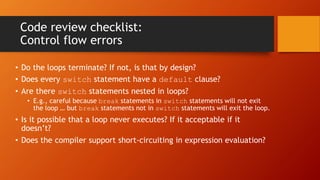
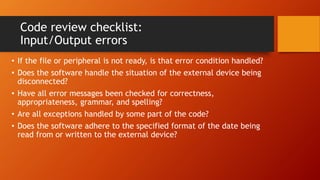
The document outlines methodologies for enhancing cyber defense through software walkthroughs, code reviews, and pair programming, emphasizing the importance of scrutinizing both hardware and software to prevent cyber threats. It discusses formal and informal approaches to software inspections, detailing best practices for conducting reviews and identifying potential defects in code. Additionally, it highlights the necessity of local industry and academic collaboration to reduce foreign dependency in cyber defense capabilities.








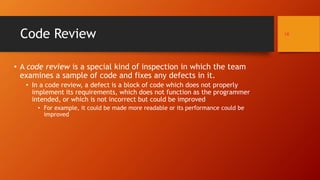
![DEFINITION
In software engineering, a walkthrough is a form of software peer
review "in which a designer or programmer leads members of the
development team and other interested parties go through a software
product, and the participants ask questions and make comments about
possible errors, violation of development standards, and other
problems.
[IEEE Std. 1028-1997, IEEE Standard for Software Reviews, clause 3.8]
Software Walkthroughs](https://image.slidesharecdn.com/brdrfaheempptmypresswwalkthru-190131053009/85/Capability-Building-for-Cyber-Defense-Software-Walk-through-and-Screening-9-320.jpg)