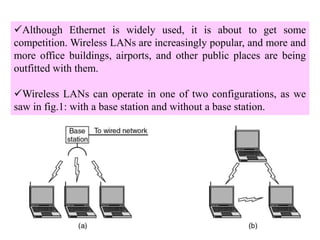
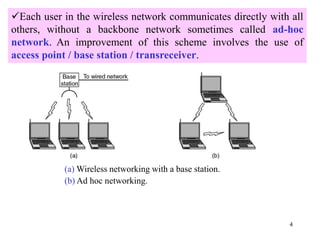
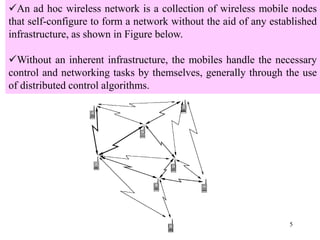
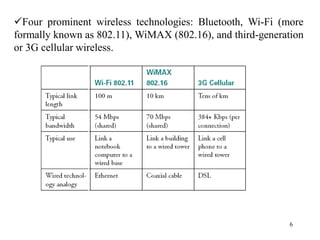
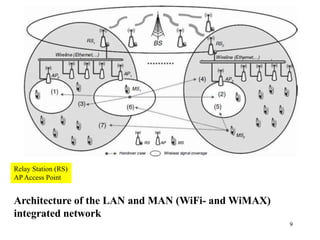
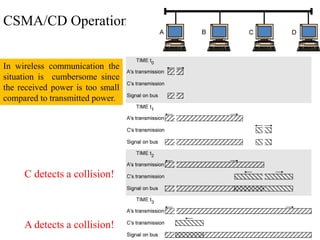
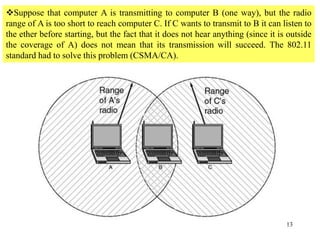
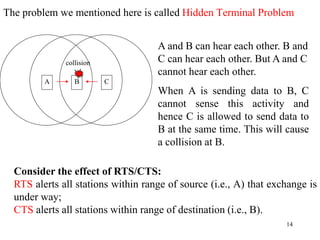
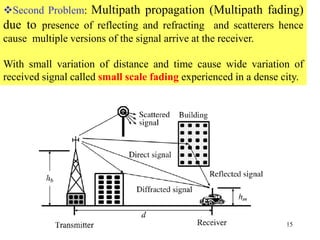
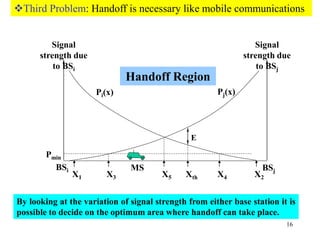
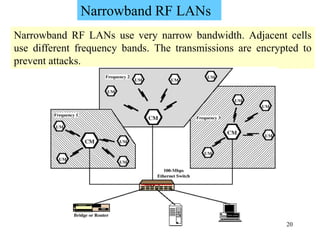
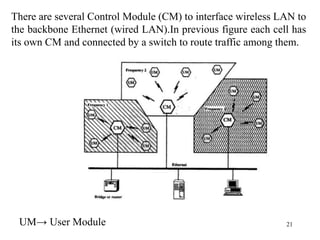
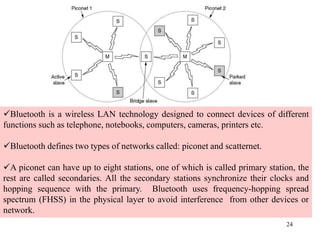
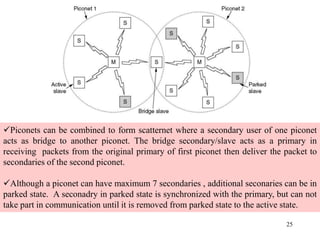
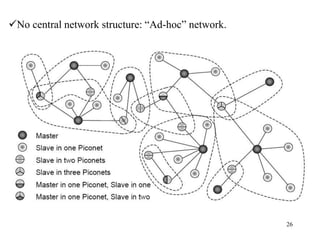
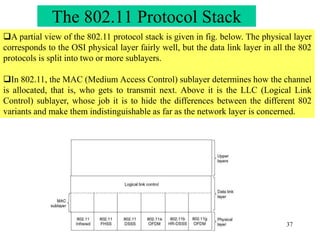
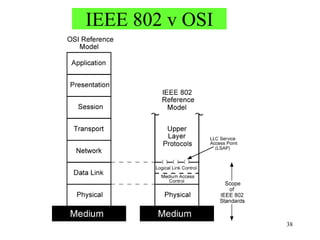
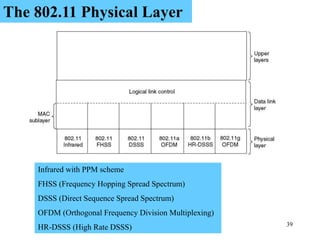
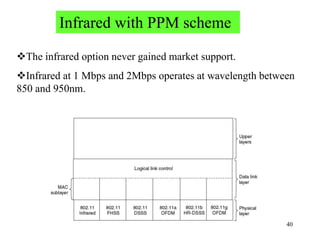
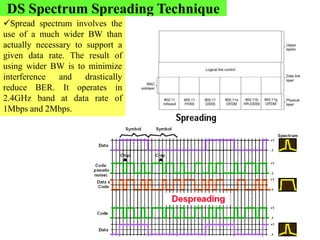
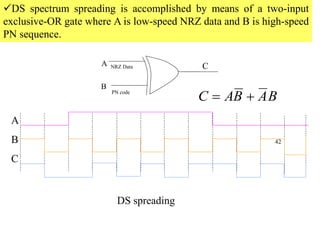
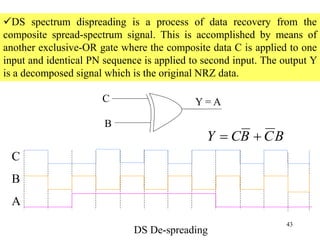
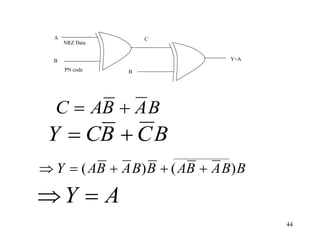
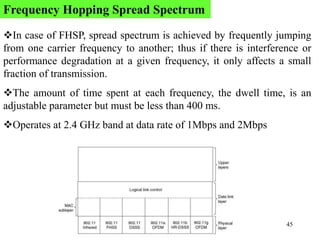
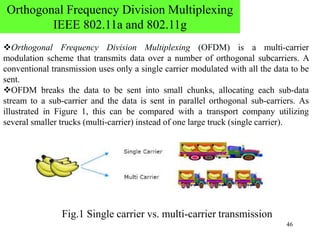
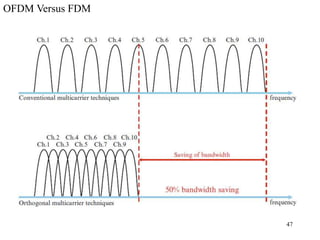
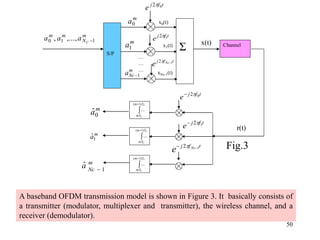
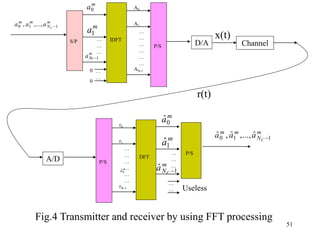
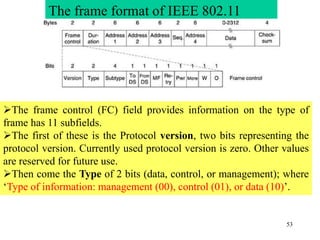
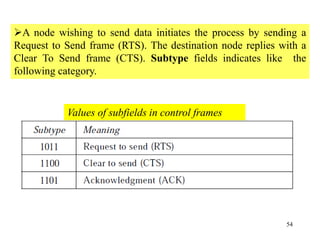
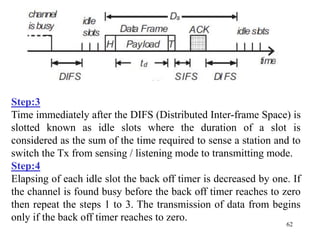
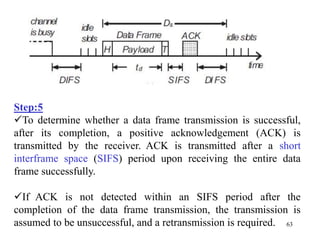
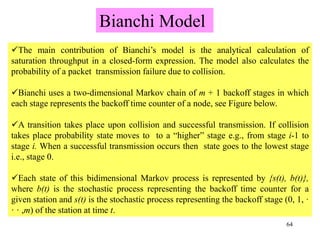
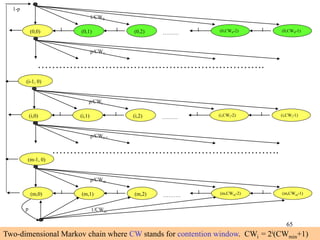
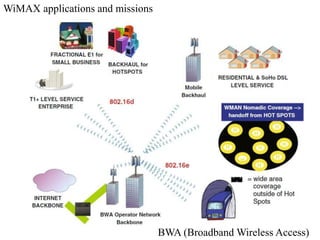
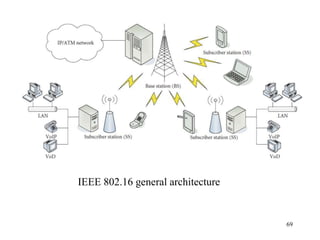
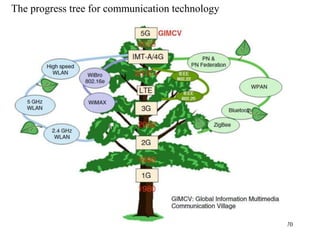
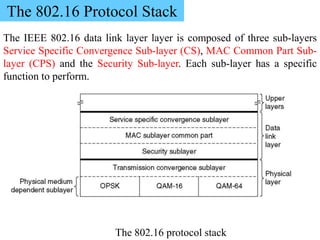
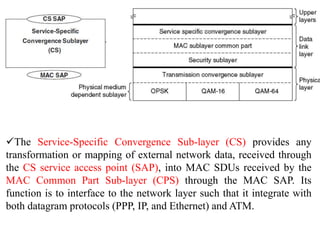
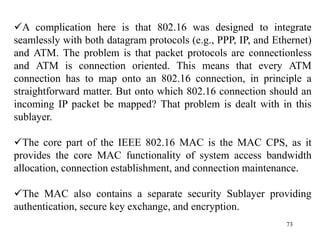
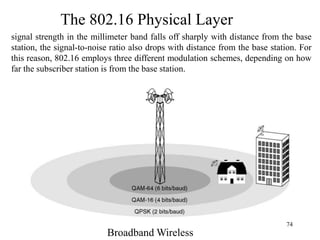
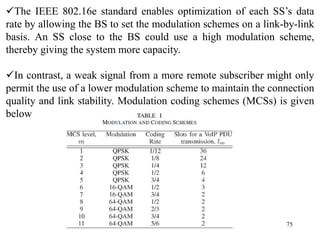
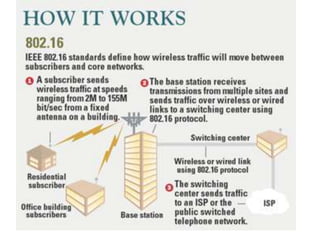
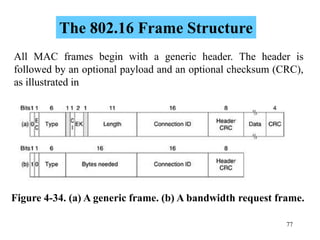
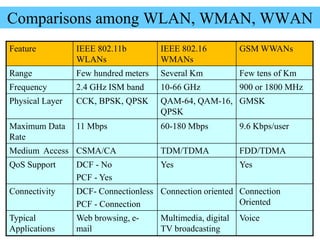
Wireless communication technologies like Wi-Fi, Bluetooth, and WiMAX allow devices to connect to networks without cables. Wireless LANs use radio signals to enable connectivity within small areas like buildings or campuses. They can operate with or without a central base station and provide mobility as users move around. However, wireless networks face challenges including interference between nearby transmissions and ensuring connectivity as users move between different base station signals. Standards use techniques like spread spectrum transmission and handoff processes to mitigate these issues.