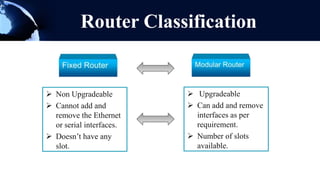
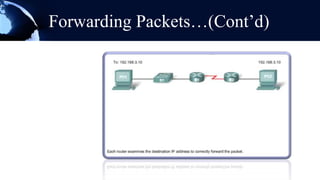
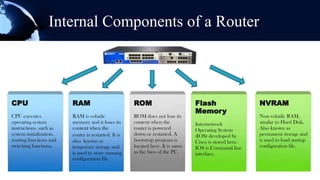
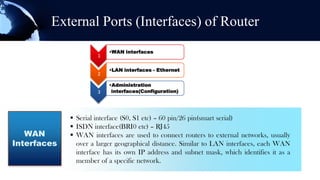
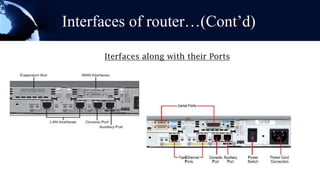
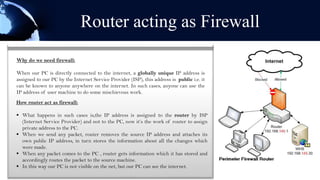
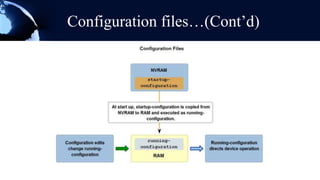
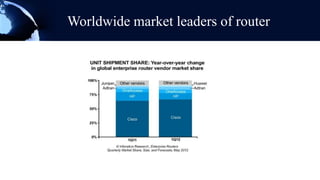
A router is a networking device that forwards data packets between computer networks. It chooses the best path within the network to send data from one PC to another. Routers use internal components like a CPU, RAM, and flash memory to run an operating system like Cisco IOS, which allows it to perform routing functions. Routers have external ports that connect to both local area networks and wide area networks. Routers can also act as firewalls by hiding private IP addresses and only exposing a public IP address to the internet, protecting devices on the private network.