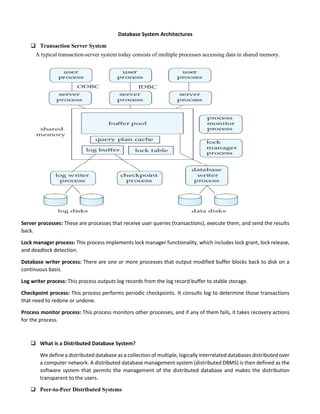
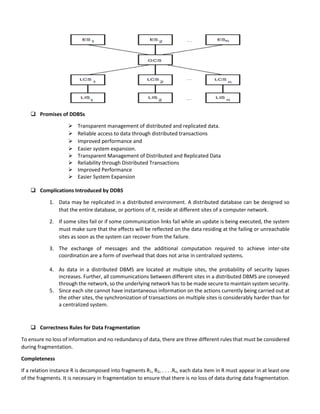
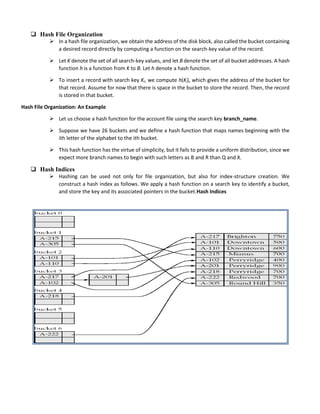
This document discusses database system architectures and distributed database systems. It covers transaction server systems, distributed database definitions, promises of distributed databases, complications introduced, and design issues. It also provides examples of horizontal and vertical data fragmentation and discusses parallel database architectures, components, and data partitioning techniques.