This document provides an overview of IP security (IPSec) by discussing:
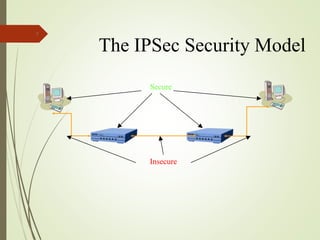
1. The security issues with the original IP protocol design and the goals of IPSec to address authentication, data integrity, and confidentiality.
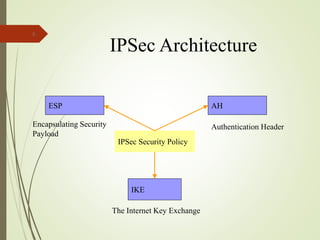
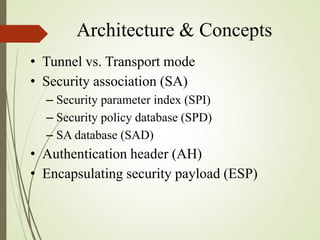
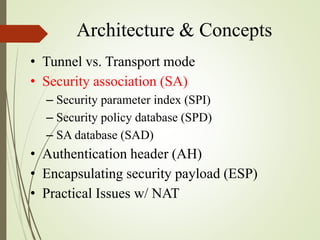
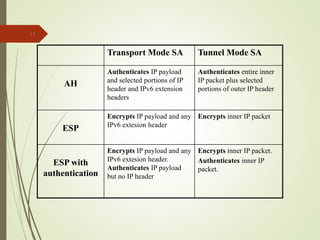
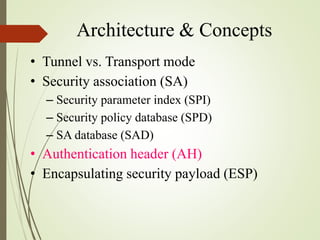
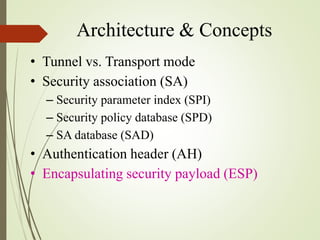
2. The key components of IPSec including the security association (SA), security policy database (SPD), authentication header (AH), and encapsulating security payload (ESP).
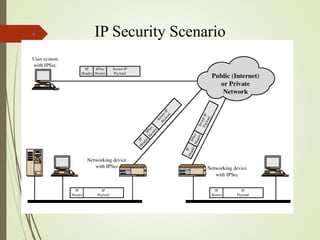
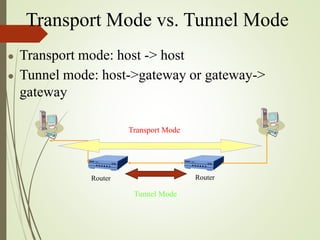
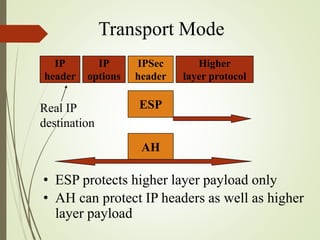
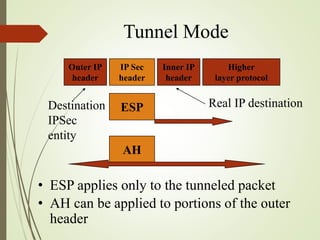
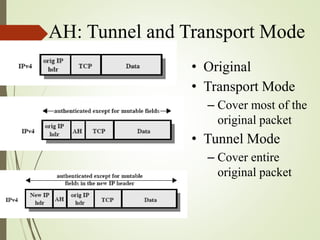
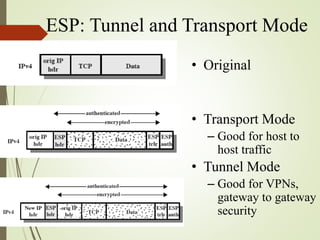
3. How IPSec implements tunnel and transport modes to secure host-to-host or gateway-to-gateway communications.