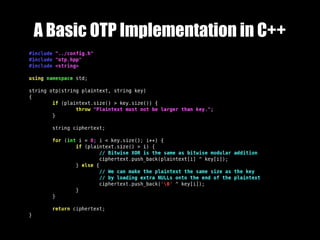
One-Time Pad (OTP) encryption uses truly random keys that are only used once to encrypt plaintext. If the keys are random, only used once, and securely transferred and destroyed, then OTP provides perfect secrecy since the ciphertext reveals no information about the plaintext. However, achieving these strict conditions is difficult in practice, requiring solutions for secure key generation, transfer, storage and destruction. While OTP provides unbreakable encryption theoretically, more practical algorithms are needed to address its limitations.