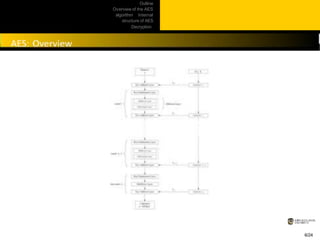
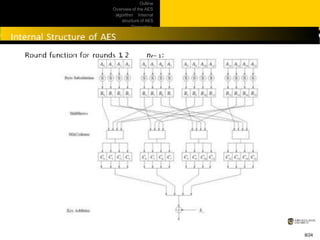
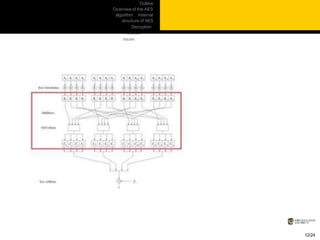
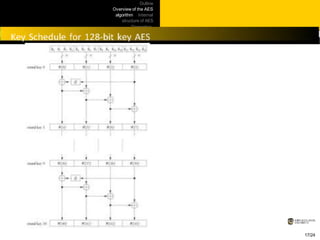
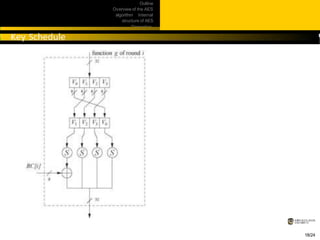
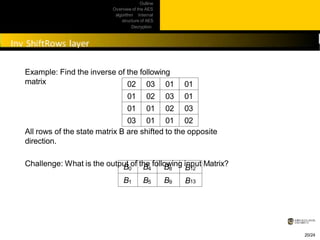
This document provides an overview of the AES algorithm. It discusses how AES was chosen as the encryption standard by NIST, with support for 128, 192, and 256-bit keys. The internal structure of AES is then explained, including the byte substitution layer, diffusion layer consisting of shift rows and mix columns, and key addition layer. Decryption is described as the inverse of these layers. Practical issues like software and hardware implementation efficiency are also covered.