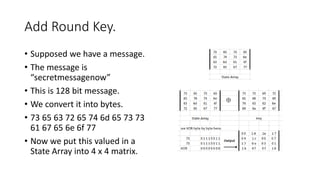
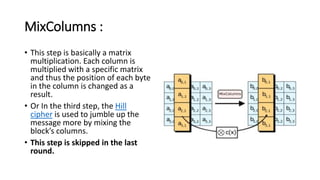
The document provides information about the Advanced Encryption Standard (AES) encryption algorithm. It describes AES as a symmetric block cipher chosen by the U.S. government to protect classified information. The document outlines the development and selection process for AES, describing how it was intended to replace the aging Data Encryption Standard (DES). It also provides details about the AES algorithm, including that it uses 128, 192, or 256-bit keys and encryption is performed through 10-14 rounds of processing involving byte substitution, shifting rows of data, mixing columns, and combining with the encryption key.



![• NIST stated that the newer, advanced encryption algorithm would be
unclassified and must be "capable of protecting sensitive government
information well into the [21st] century." It was intended to be easy to
implement in hardware and software, as well as in restricted
environments -- such as a smart card -- and offer decent defenses
against various attack techniques.
• AES was created for the U.S. government with additional voluntary,
free use in public or private, commercial or noncommercial programs
that provide encryption services. However, nongovernmental
organizations choosing to use AES are subject to limitations created by
U.S. export control.](https://image.slidesharecdn.com/lecture007aes-230405192636-c7f194e0/85/Lecture-007-AES-pptx-4-320.jpg)














![Detailed Structure
1. One noteworthy feature of this structure is
that it is not a Feistel structure. Recall that, in
the classic Feistel structure, half of the data
block is used to
modify the other half of the data block and t
hen the halves are swapped. AES instead
processes the entire data block as a single
matrix during each round using substitutions
and permutation.
2. The key that is provided as input is expand
ed into an array of forty-four 32-
bit words, w[i]. Four distinct words (128 bits)
serve as a round key for each round;](https://image.slidesharecdn.com/lecture007aes-230405192636-c7f194e0/85/Lecture-007-AES-pptx-20-320.jpg)