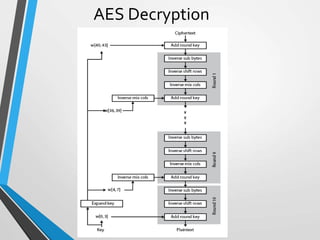
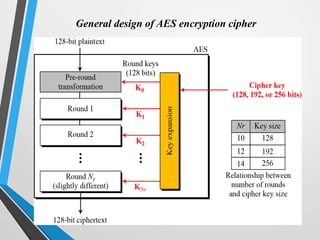
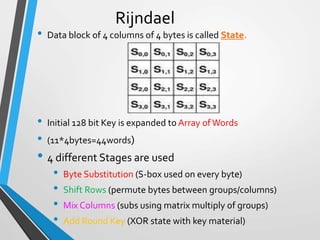
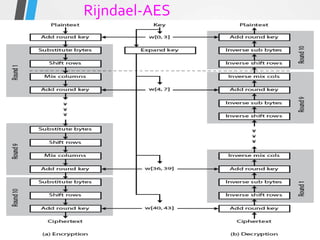
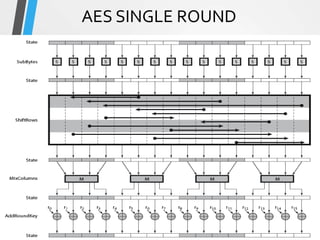
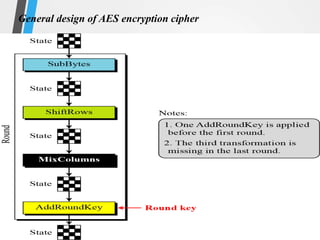
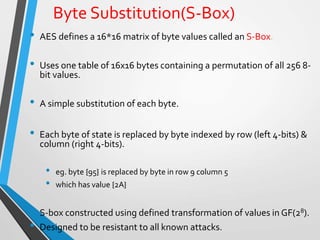
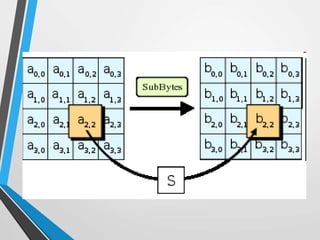
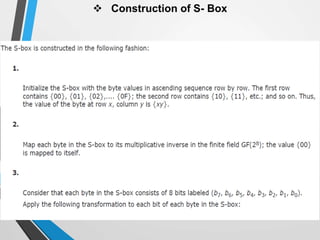
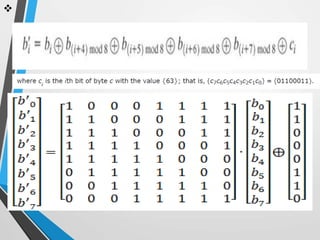
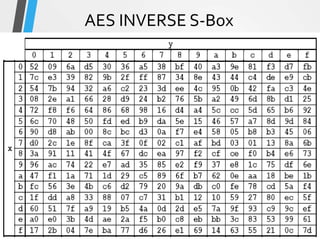
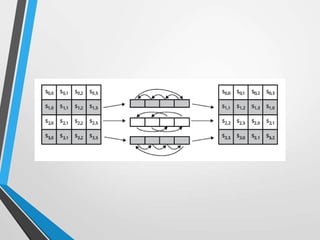
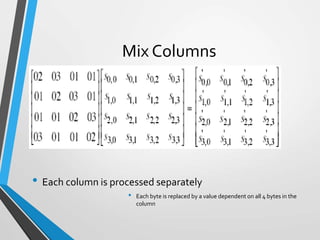
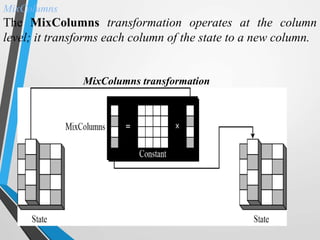
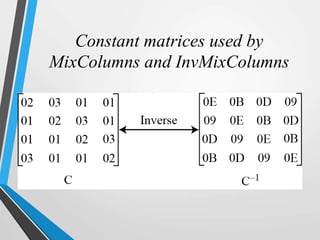
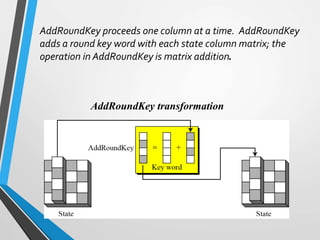
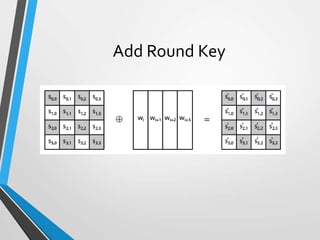
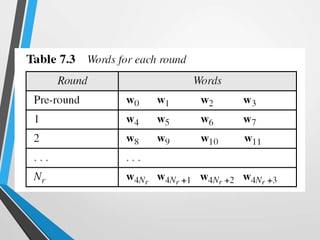
The document discusses the Advanced Encryption Standard (AES). It describes AES as a symmetric block cipher selected by the U.S. National Institute of Standards and Technology (NIST) in 2001 to replace the Data Encryption Standard (DES). AES uses a variable block size of 128 bits and a key size of 128, 192, or 256 bits. The cipher operates on a 4x4 column-byte state and has 10, 12, or 14 rounds depending on the key size. Each round consists of byte substitution, shift rows, mix columns, and add round key transformations.
















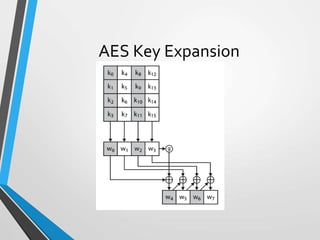
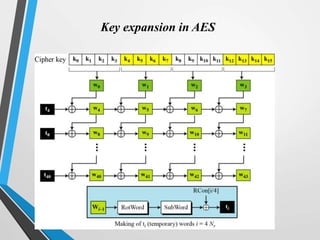
![Key Expansion(every 4th word)
• For a word whose posn inW array is a multiple of 4.
• The Function “g” consists of the following subfns
• Rotword-one byte left shift on a word.
• SubWord-byte substitution on each byte of its input word
using the S-Box
• Result of steps 1 and 2 are XORed using a round constatnt
Rcon[j].
• Round Constant is a word in which the 3 right most bytes
are always 0.
• Round const is diff for each round and is defined as
• Rcon[j]=(RC[j],0,0,0), with RC[1]=1;RC[j]=2*RC[j-1].
• Multiplication is defined over GF(2^8).
• [ie,01,02,04,08,10,20,40,80,1B,36]](https://image.slidesharecdn.com/module-2-part-3-aes-230609060409-d2820b51/85/AES-ppt-36-320.jpg)