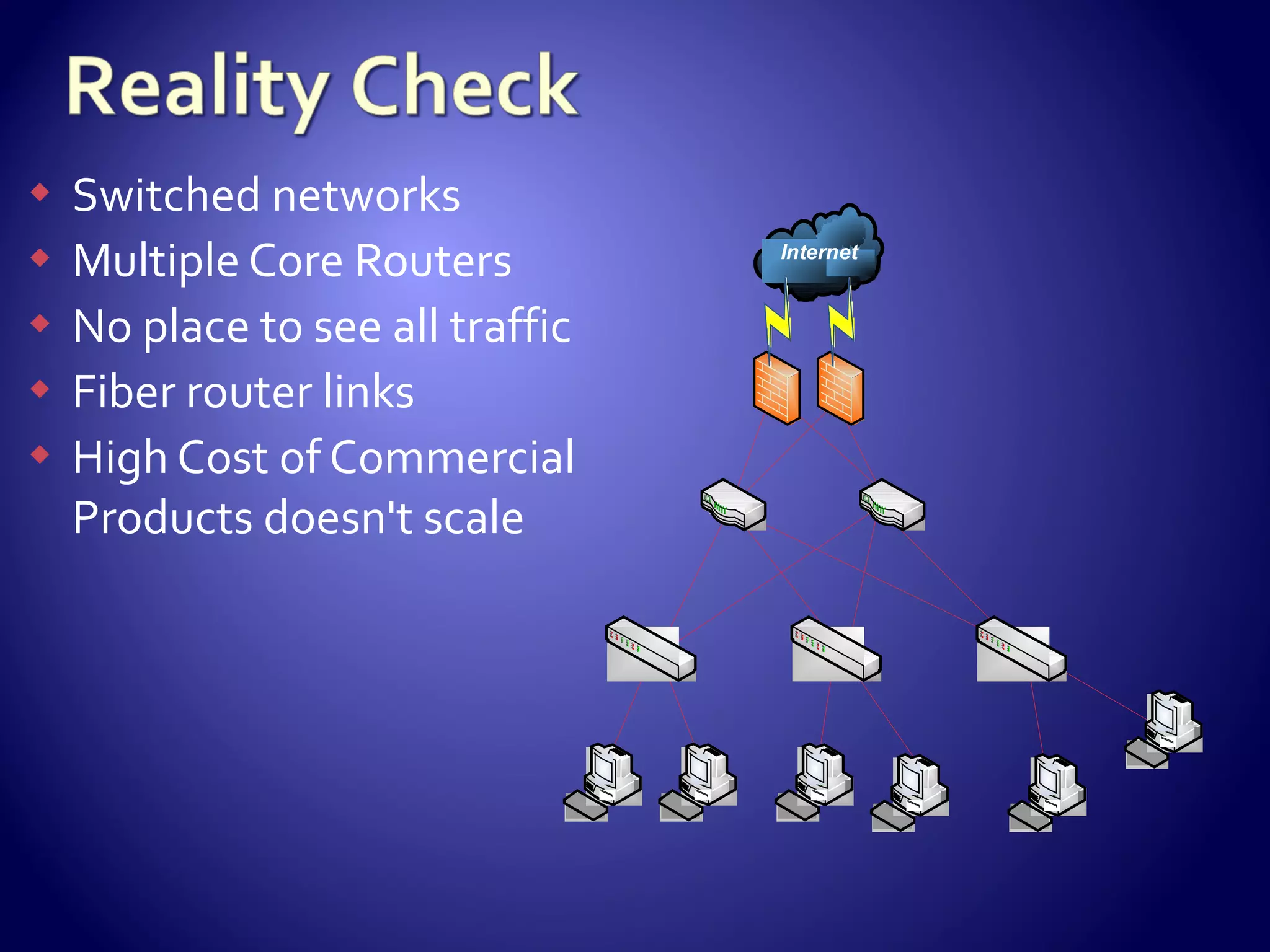
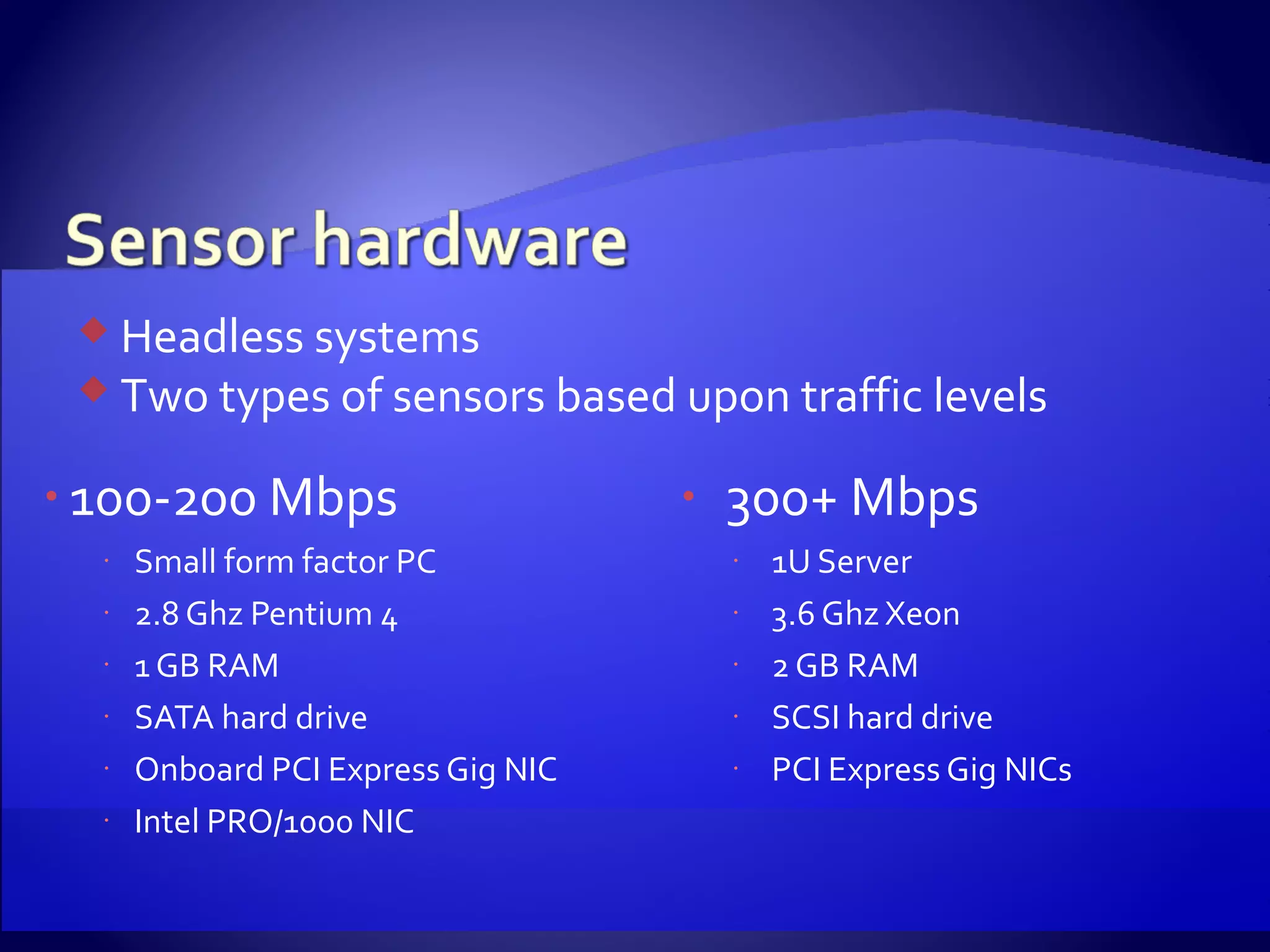
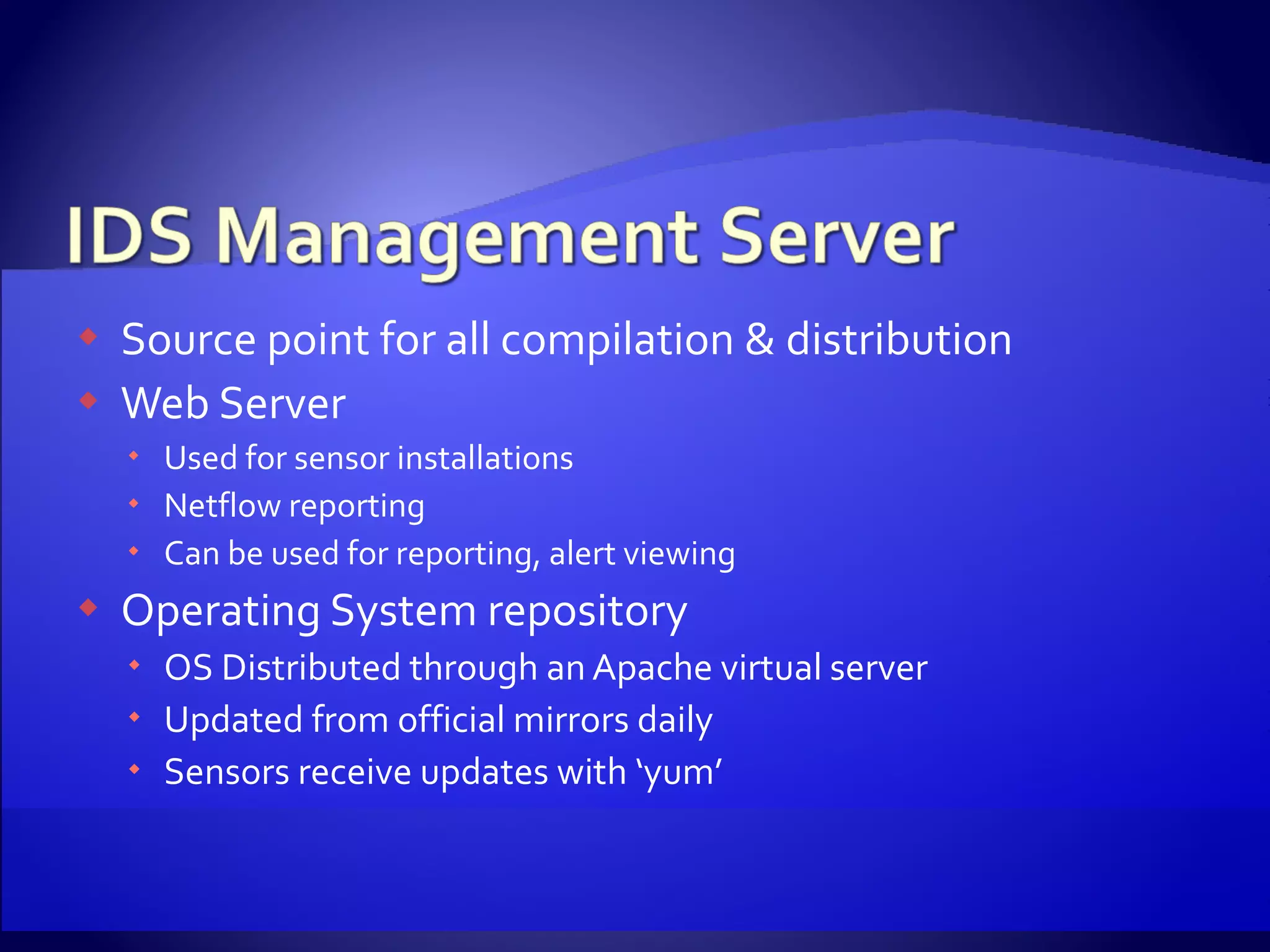
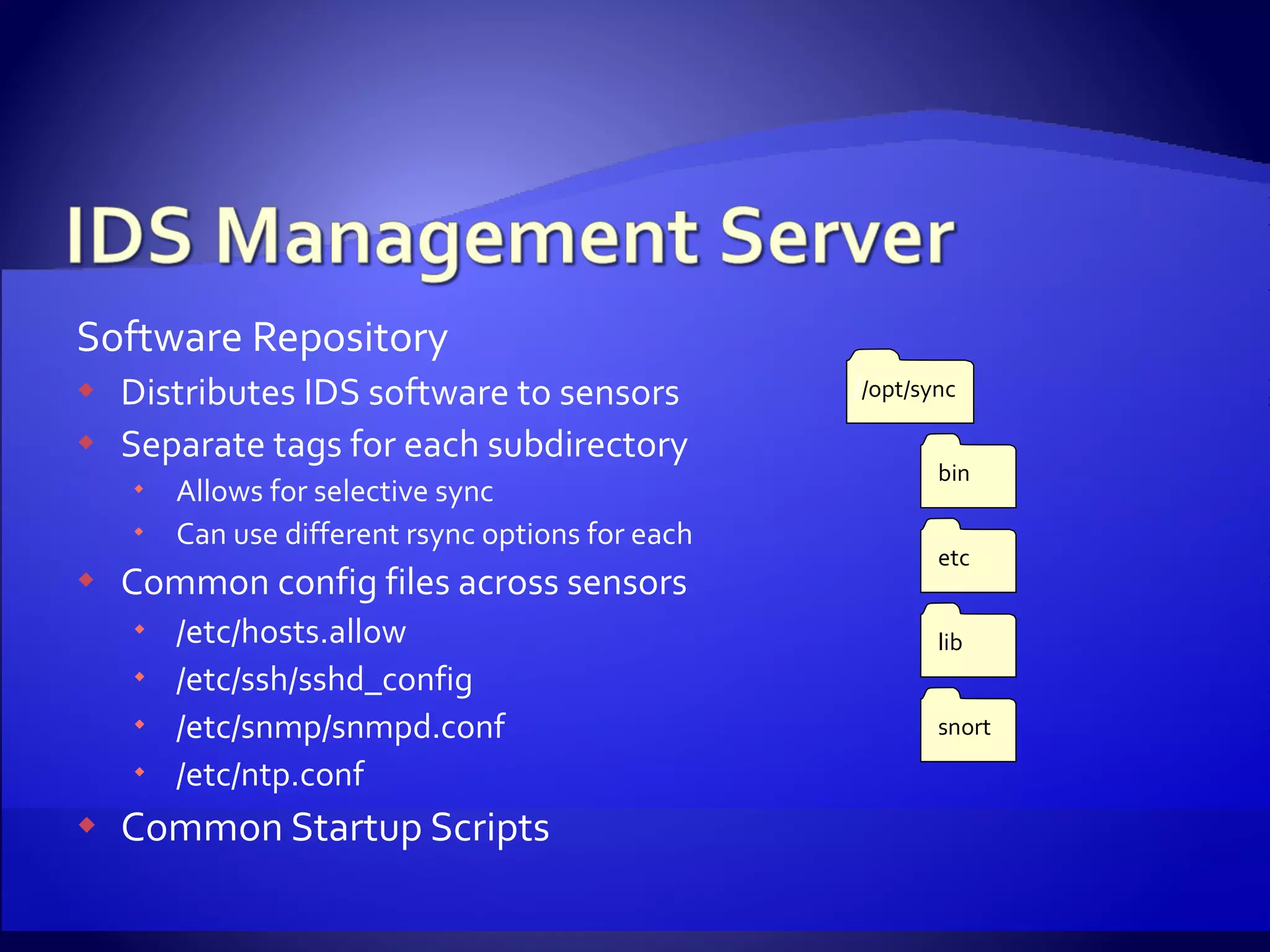
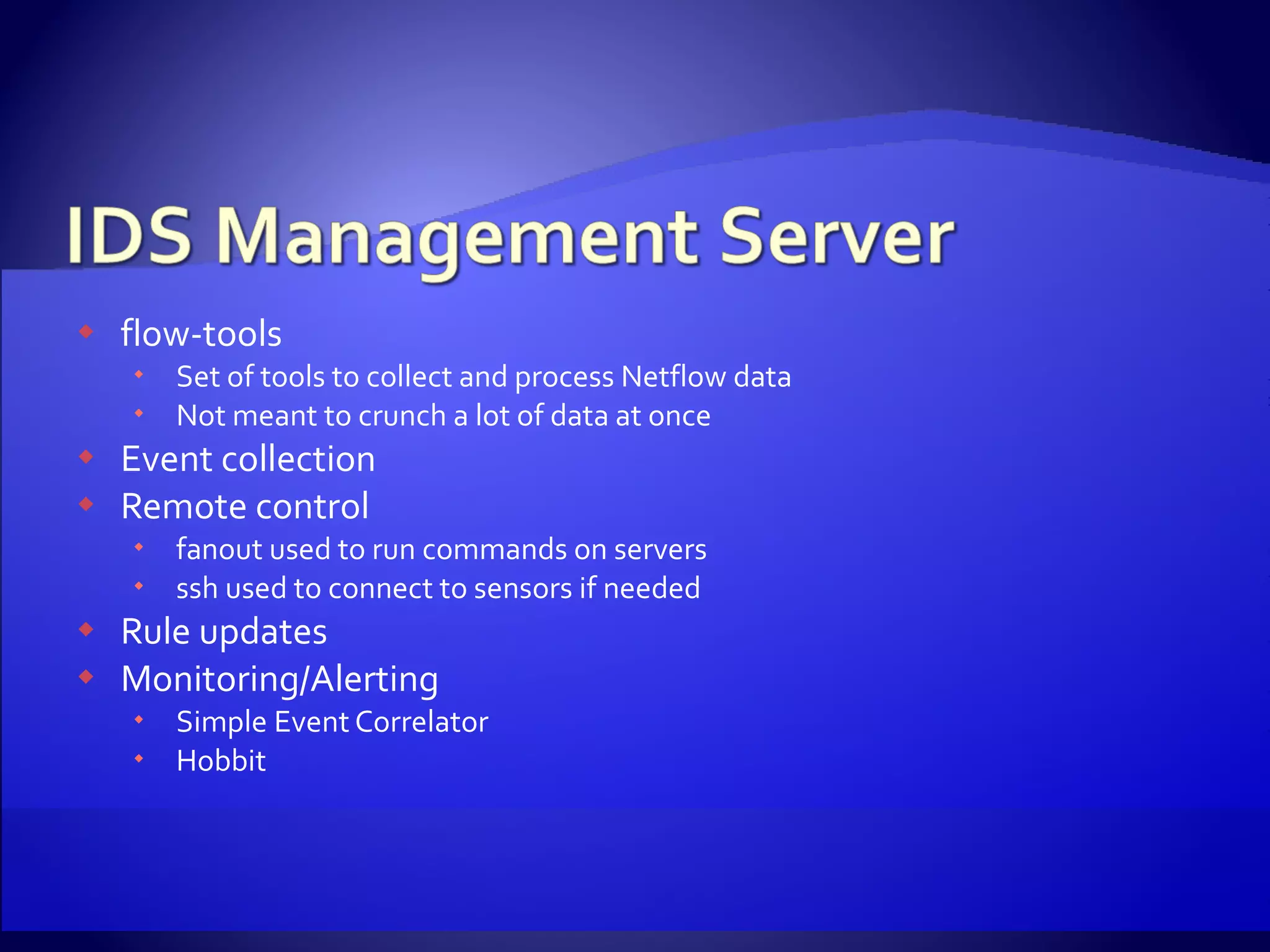
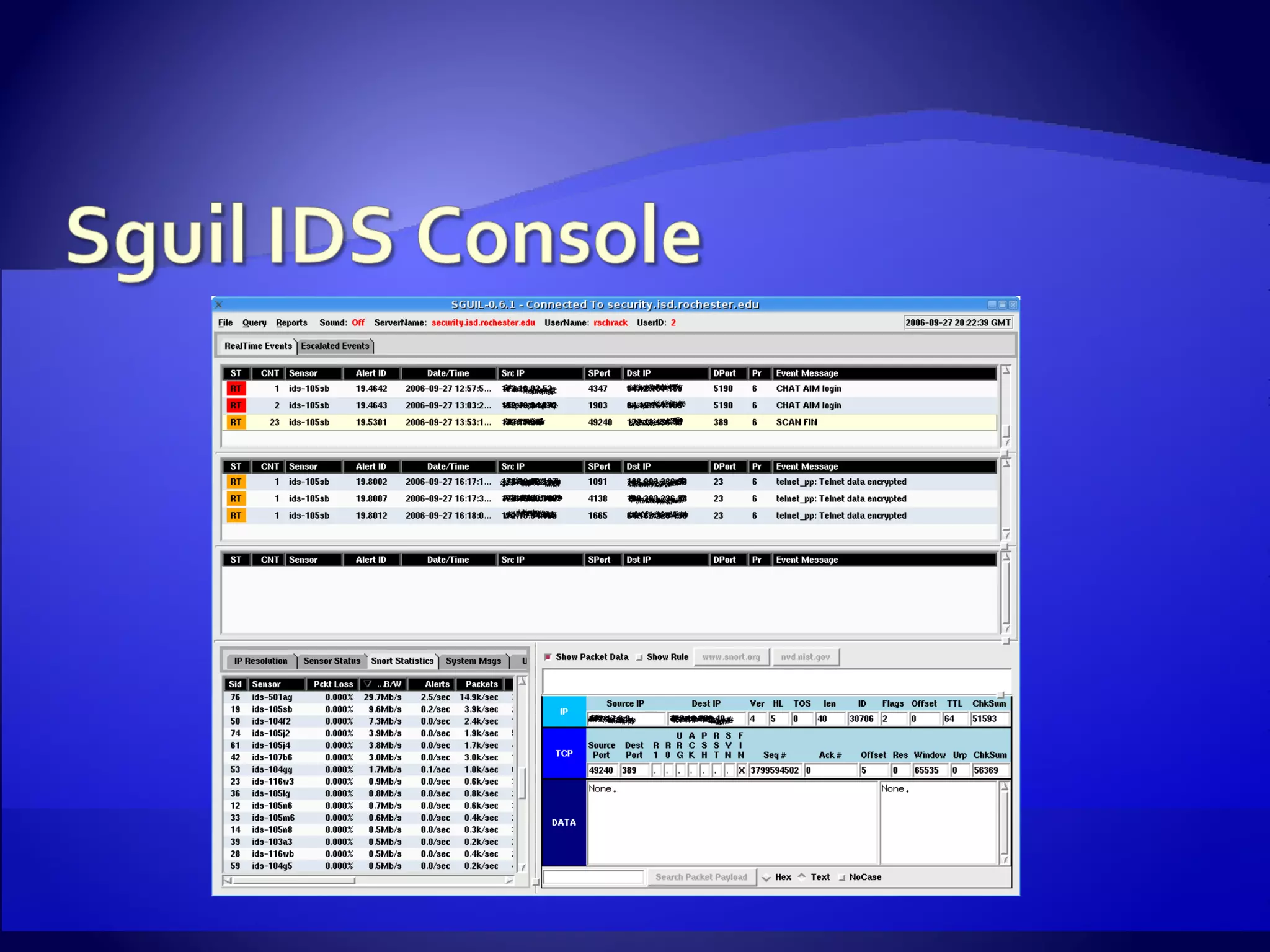
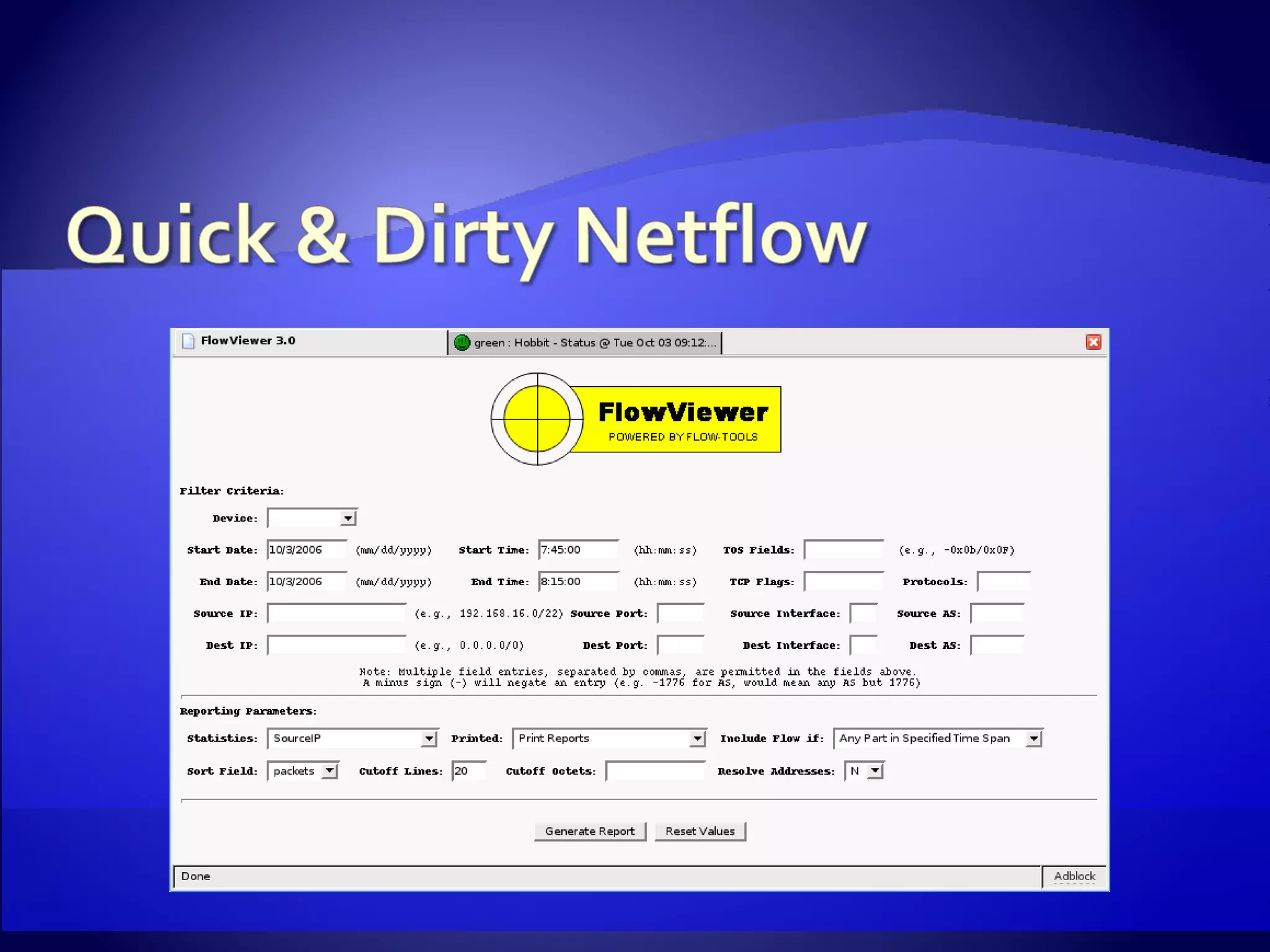
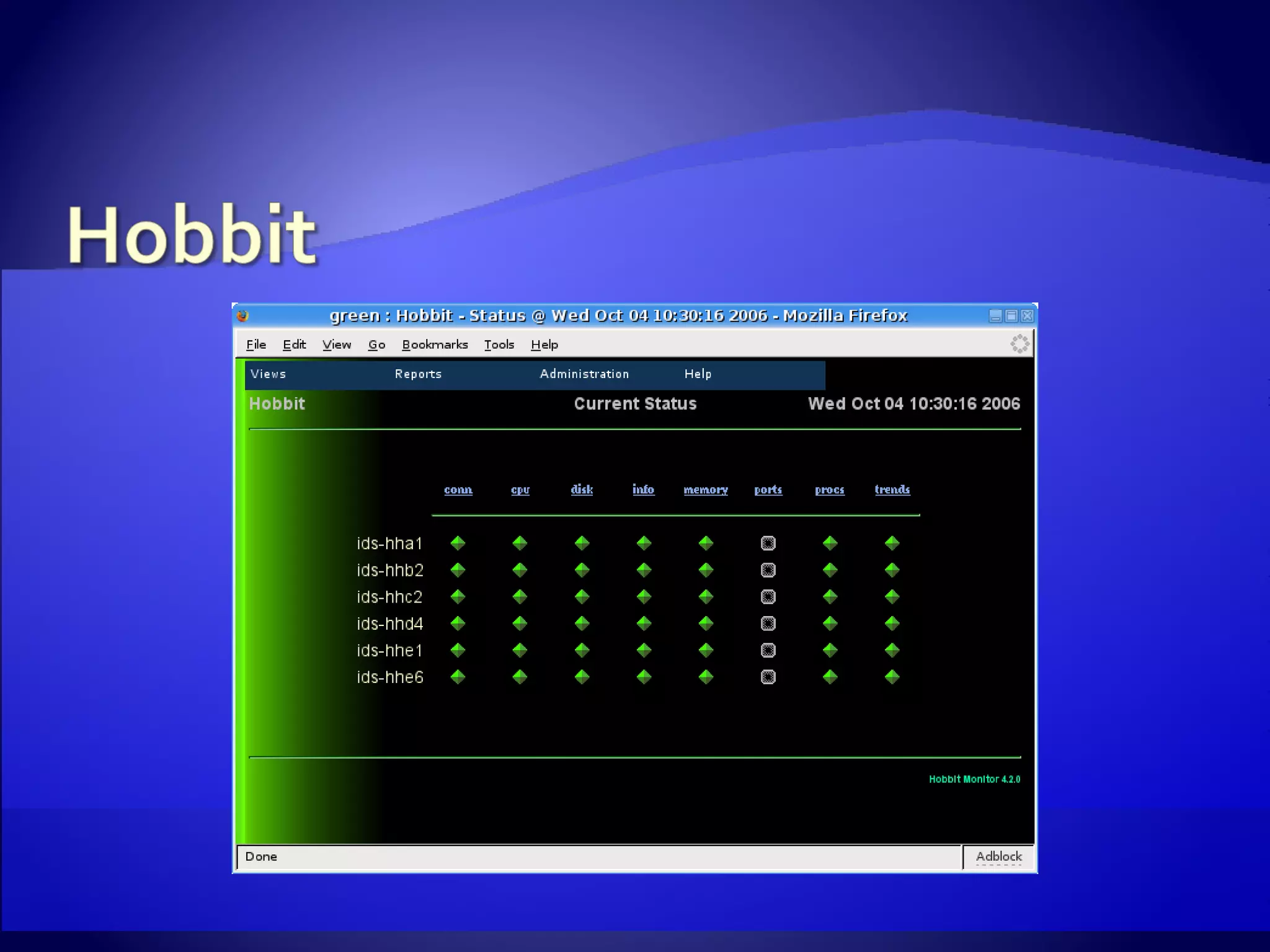
The document discusses setting up an intrusion detection system using open source software. It describes using CentOS, Snort, Barnyard, and other tools on commodity PC hardware to monitor network traffic and generate alerts in a low-cost way. Sensors are installed across the network to monitor traffic at different speeds and report back to a central management server.