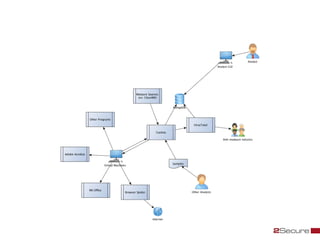
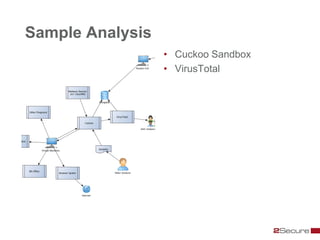
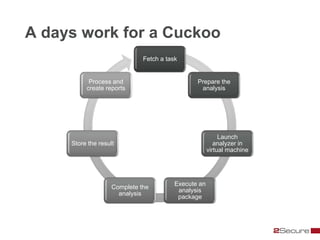
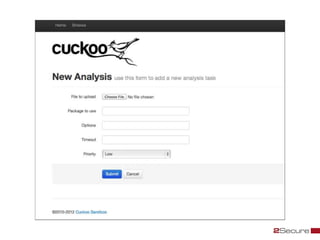
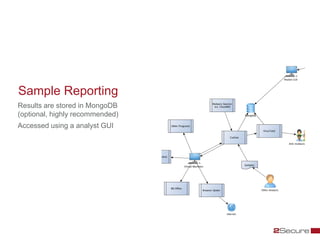
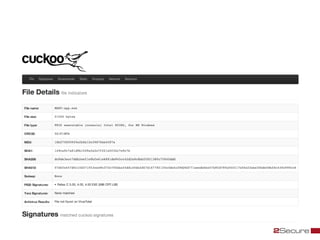
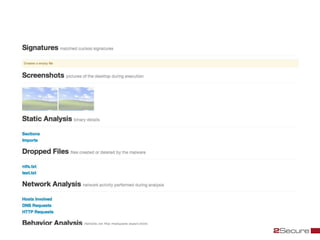
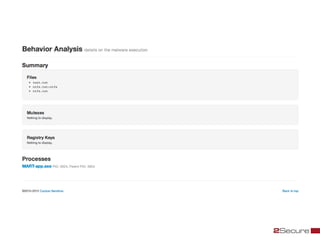
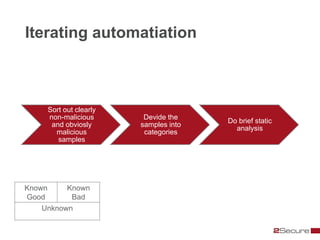
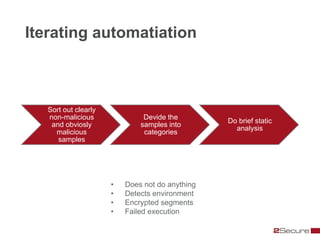
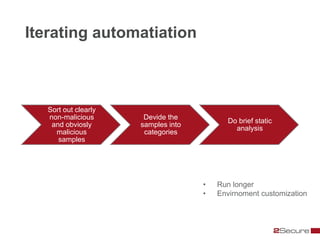
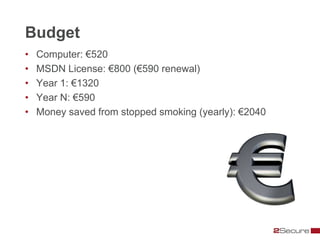
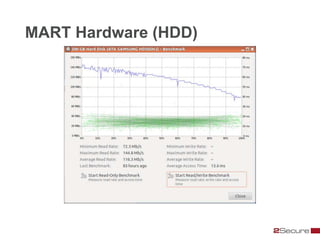
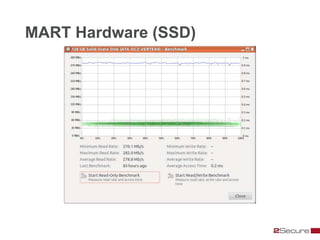
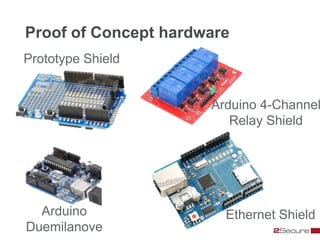
This document discusses Michael Boman's hobby of analyzing malware samples. It describes how he initially analyzed samples manually in a virtual environment but found it time consuming. He then created the Malware Analysis Research Toolkit (MART) project to automate the process. MART uses tools like Cuckoo Sandbox to analyze samples in virtual machines. It also includes components for sample acquisition, analysis, reporting, and data mining. The document discusses challenges with virtual machine analysis and ways to iterate the automation, such as doing brief static analysis on samples. It provides an overview of the hardware used in Boman's malware lab and discusses next steps for the project.