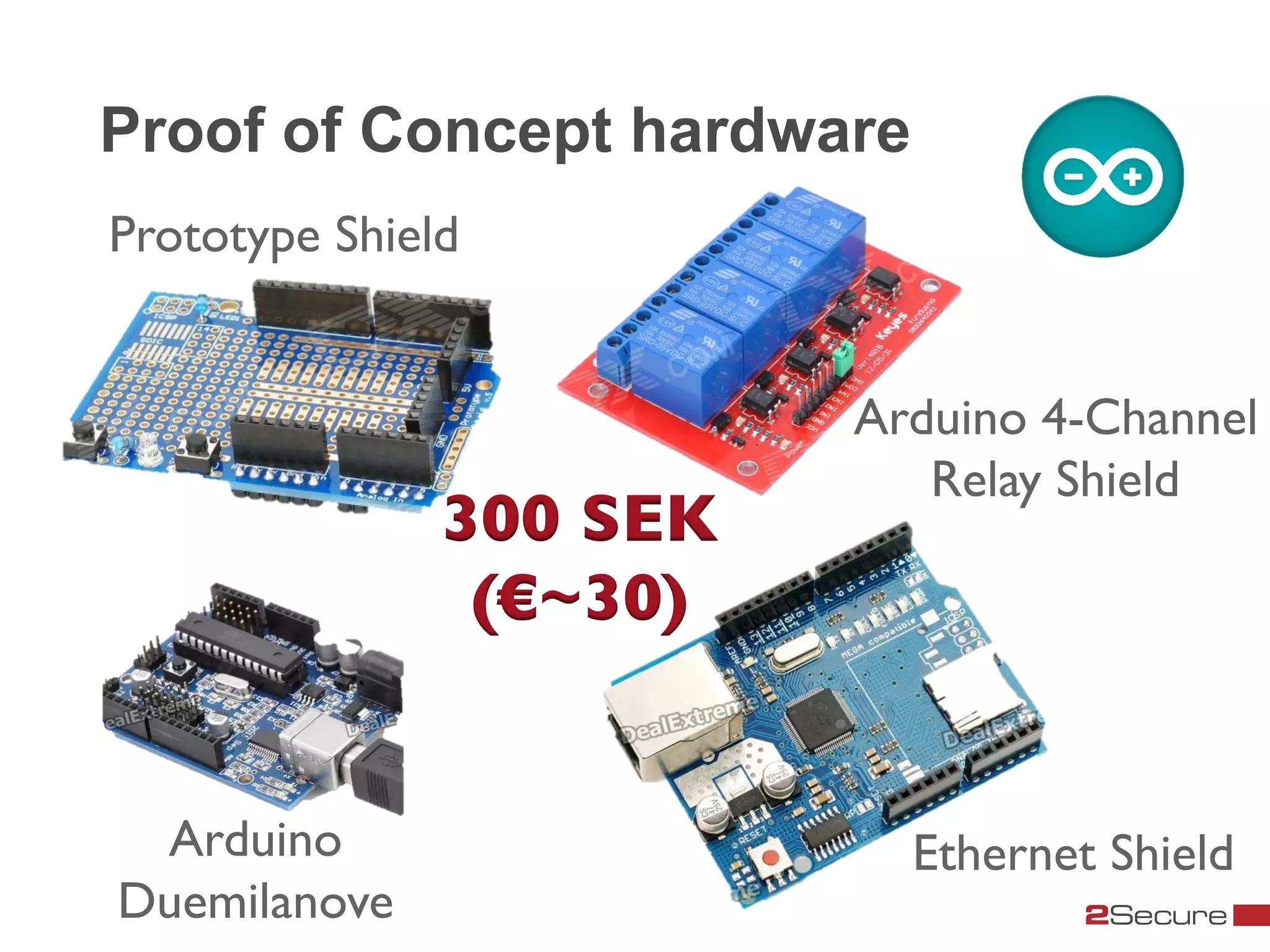
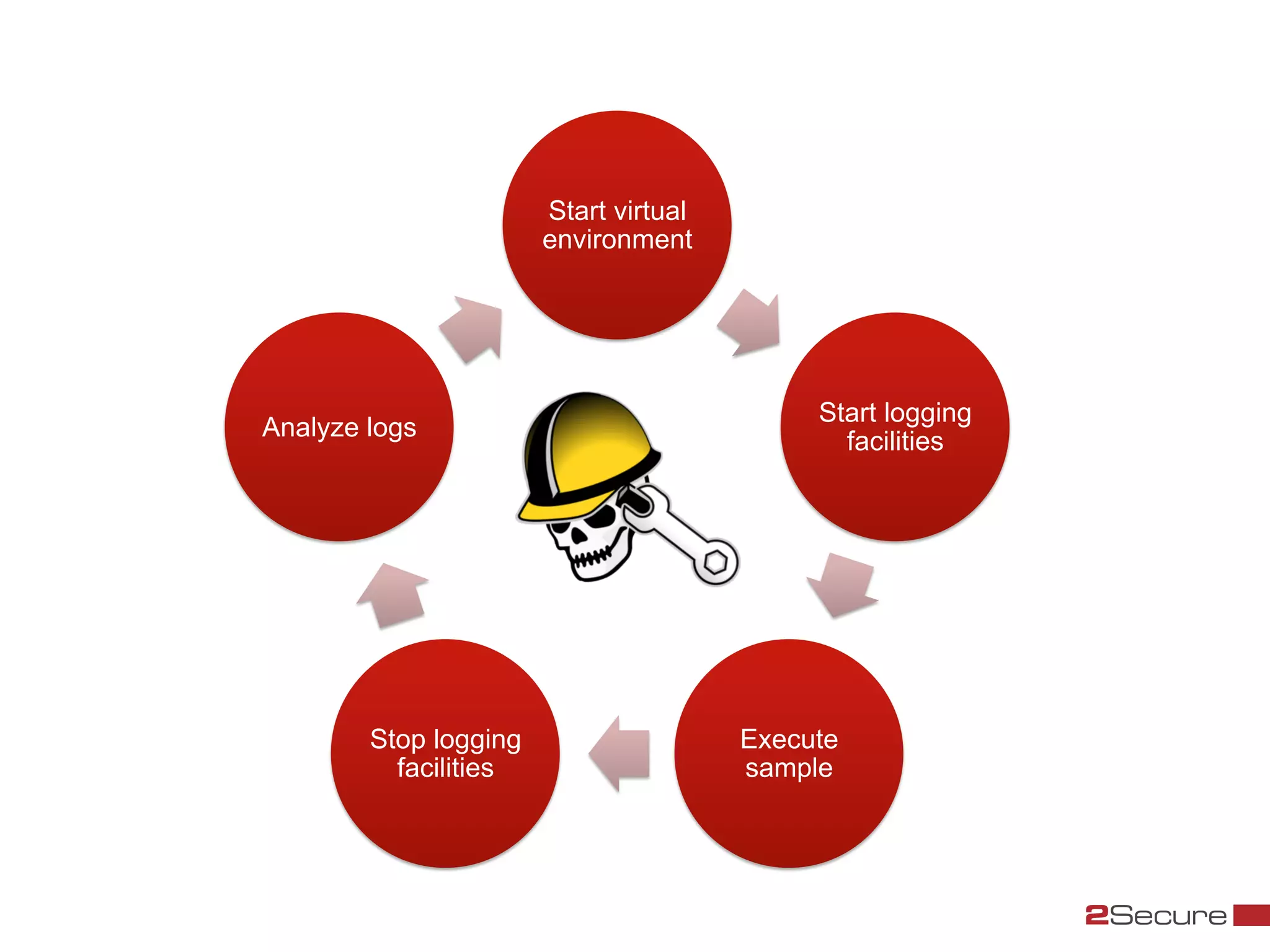
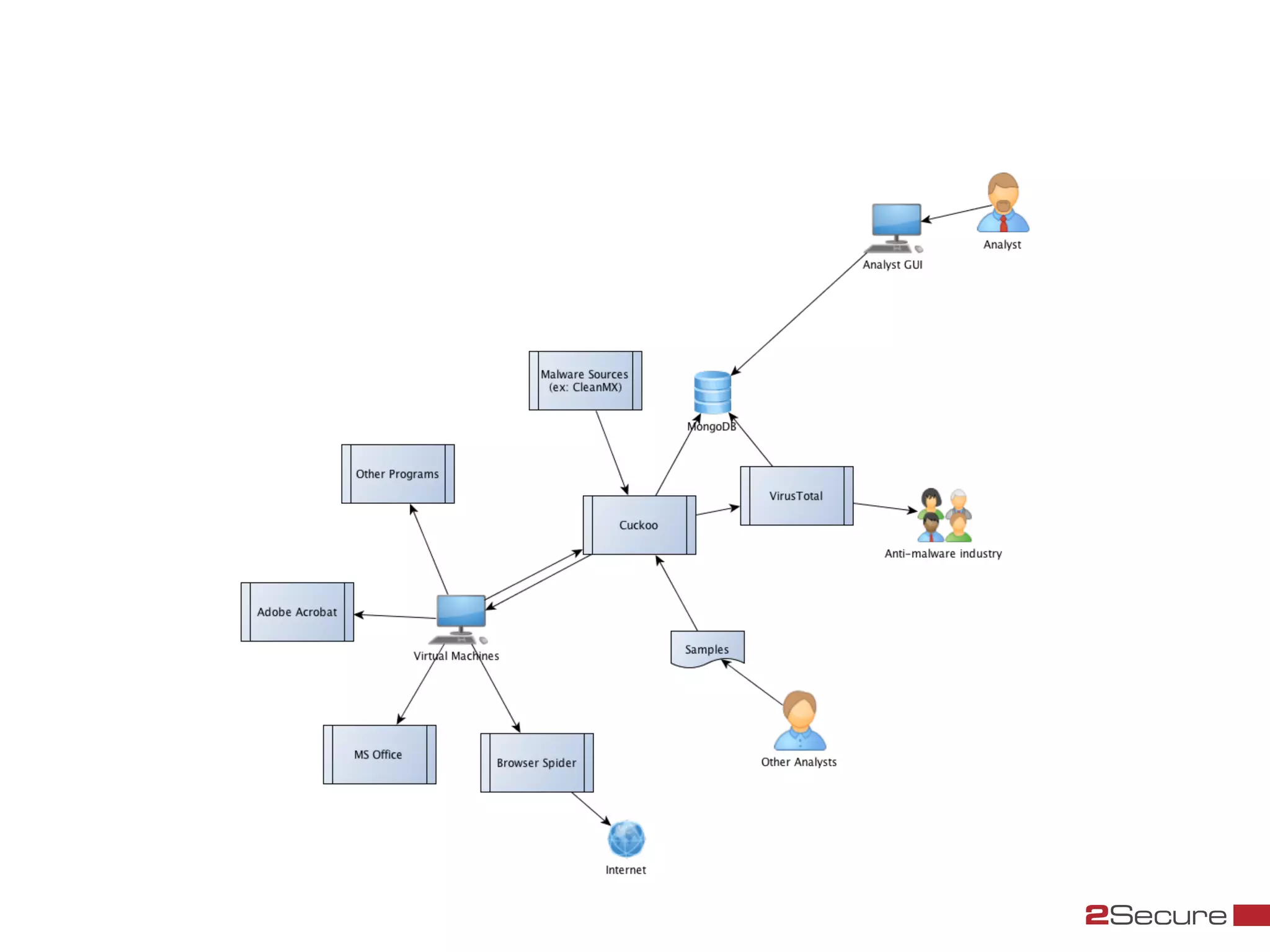
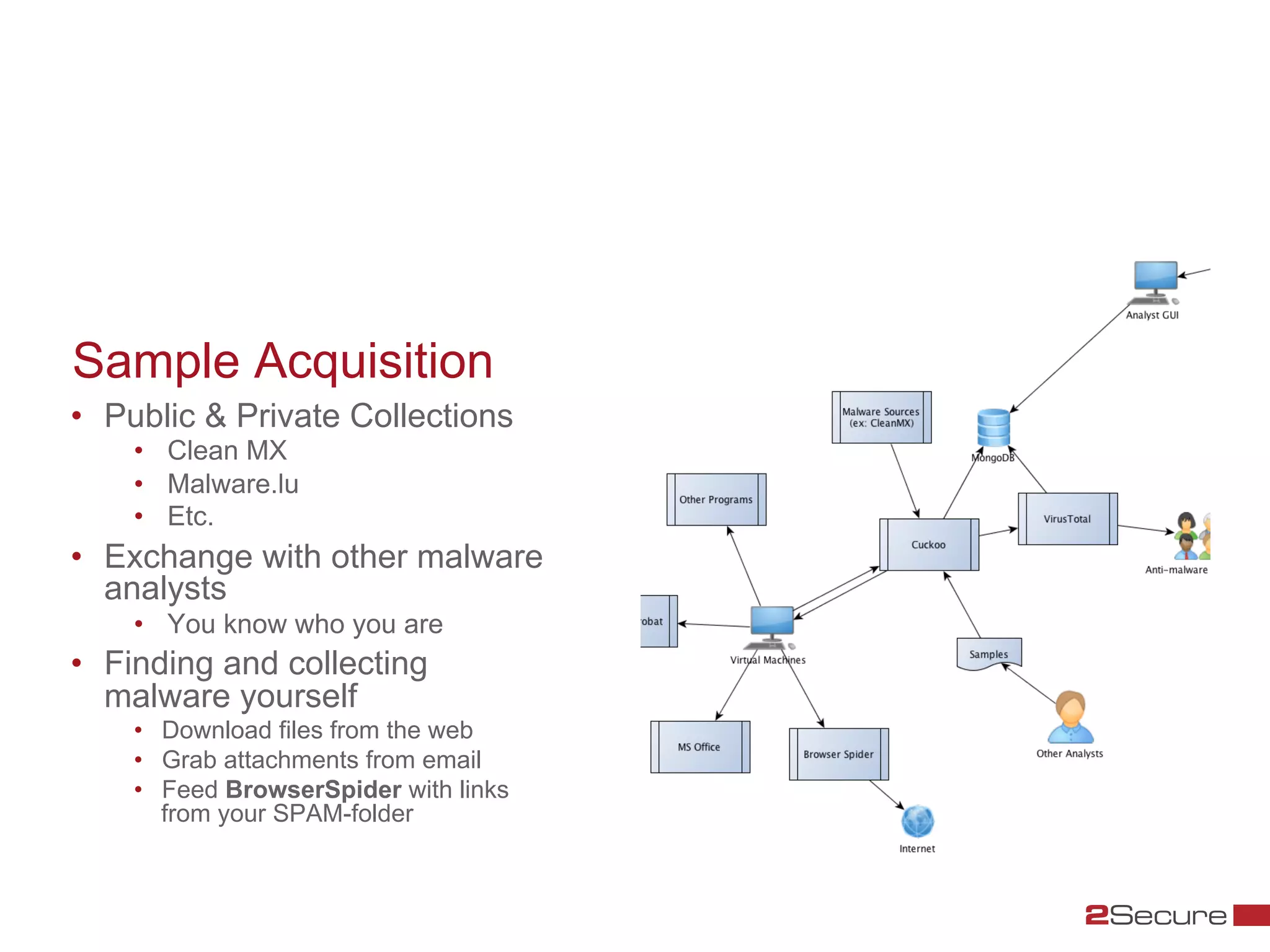
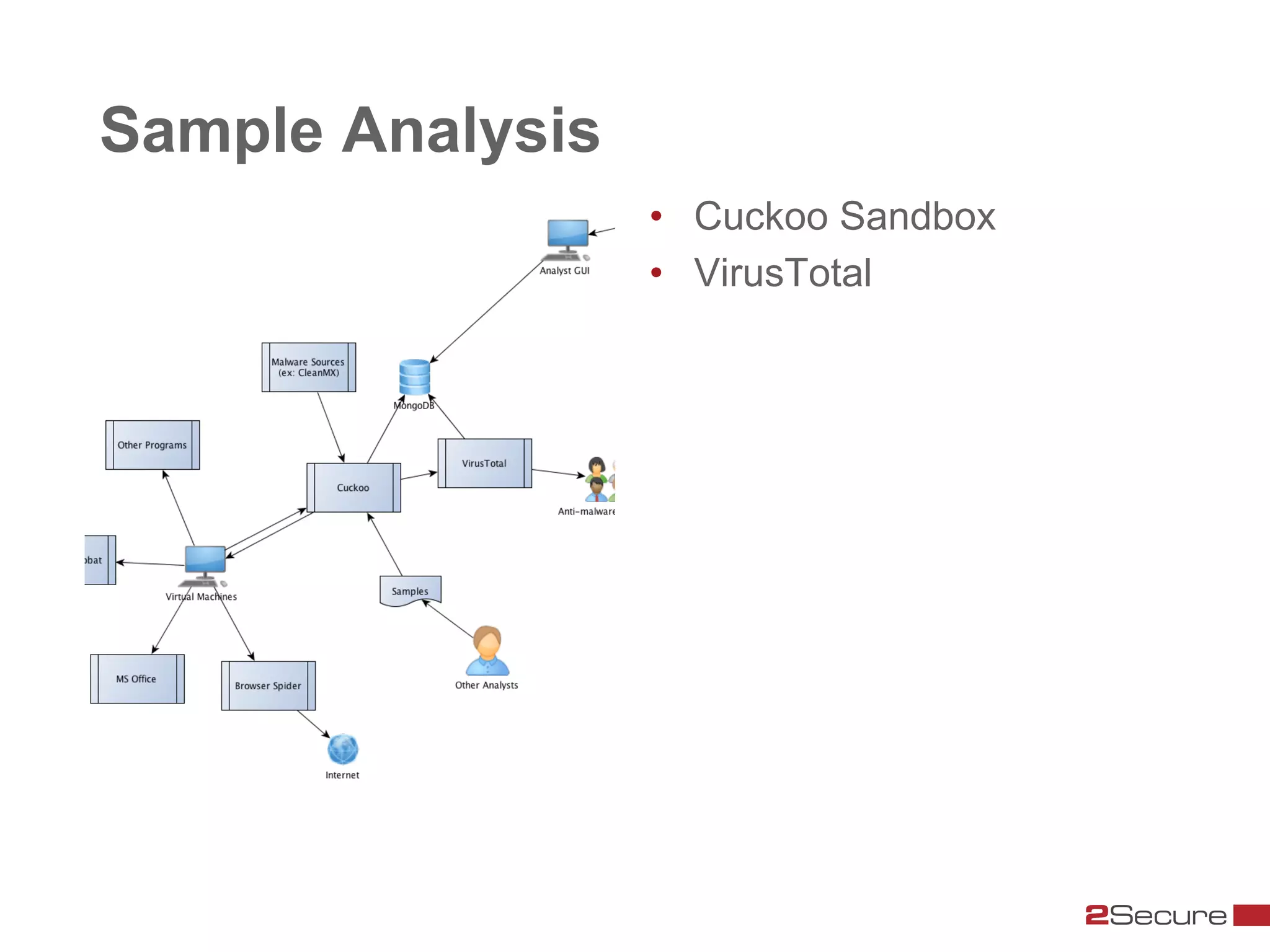
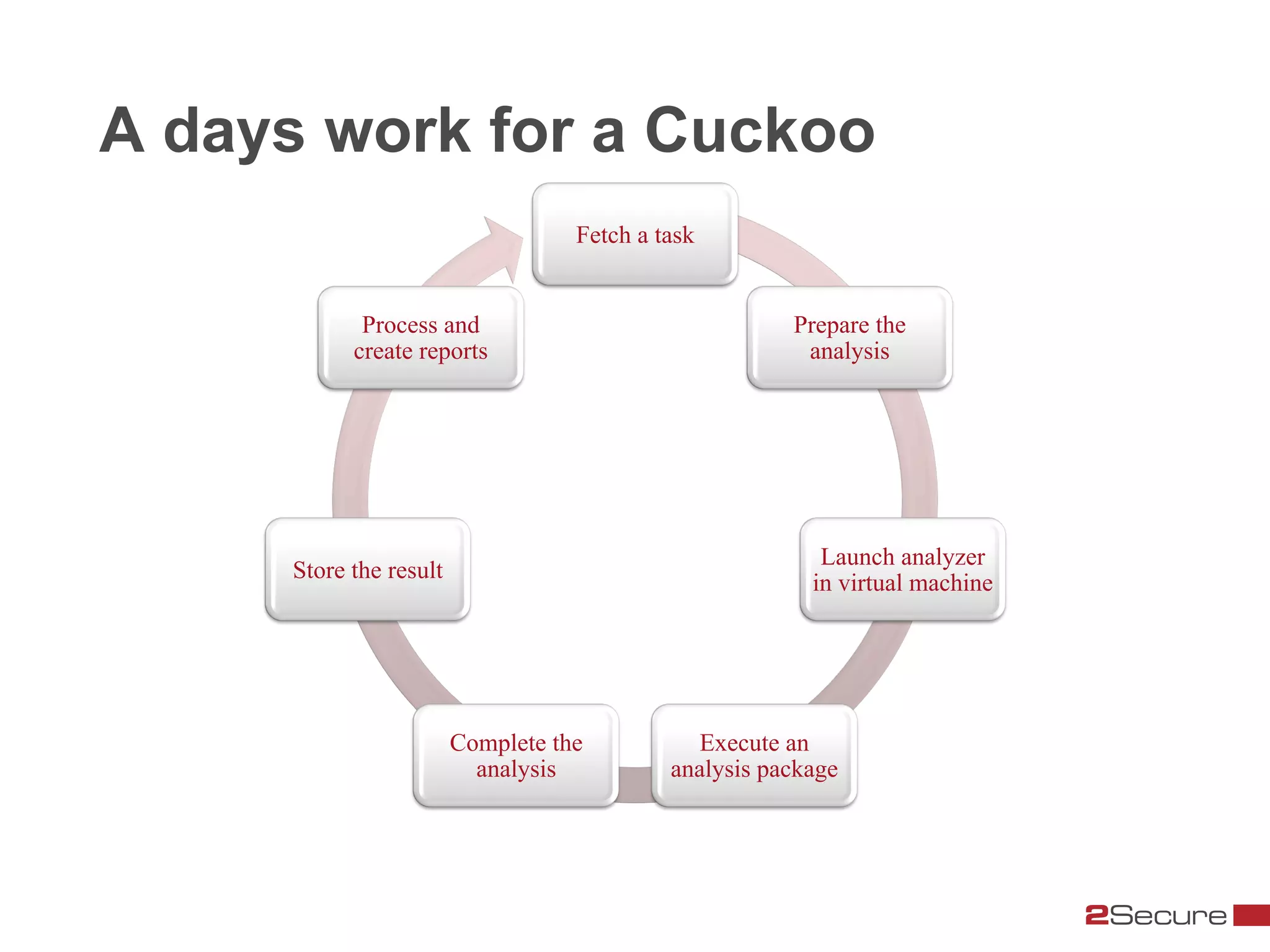
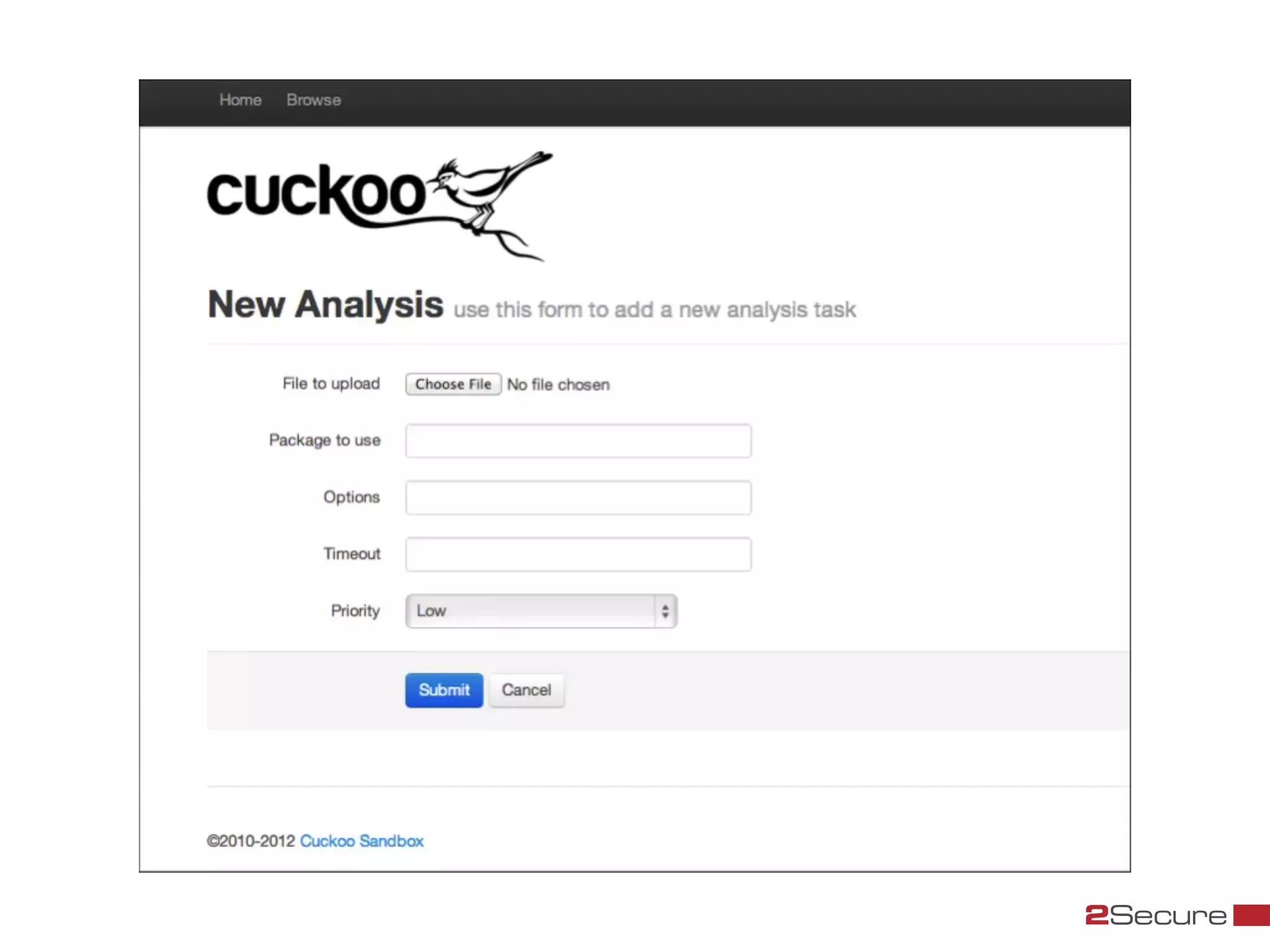
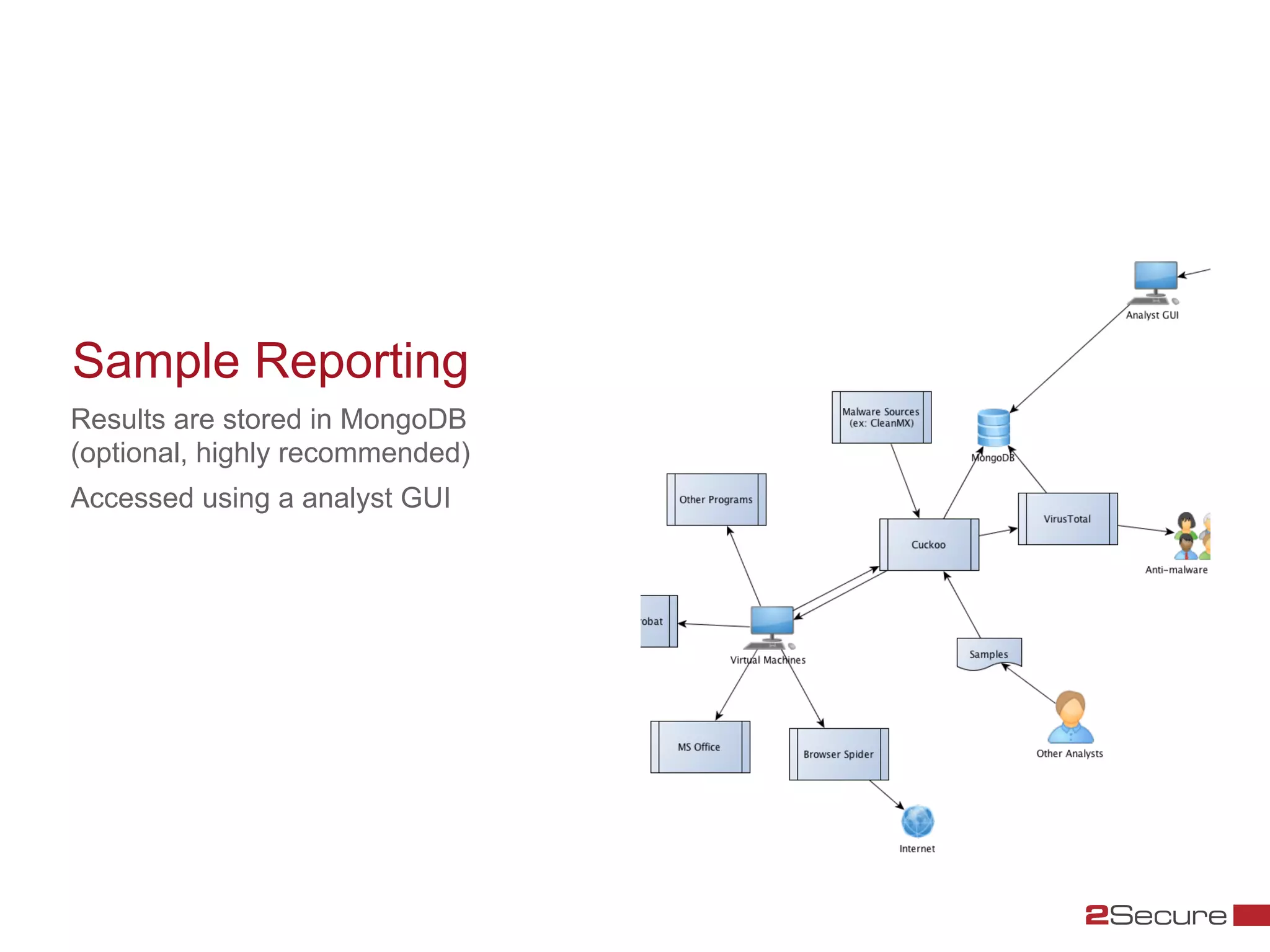
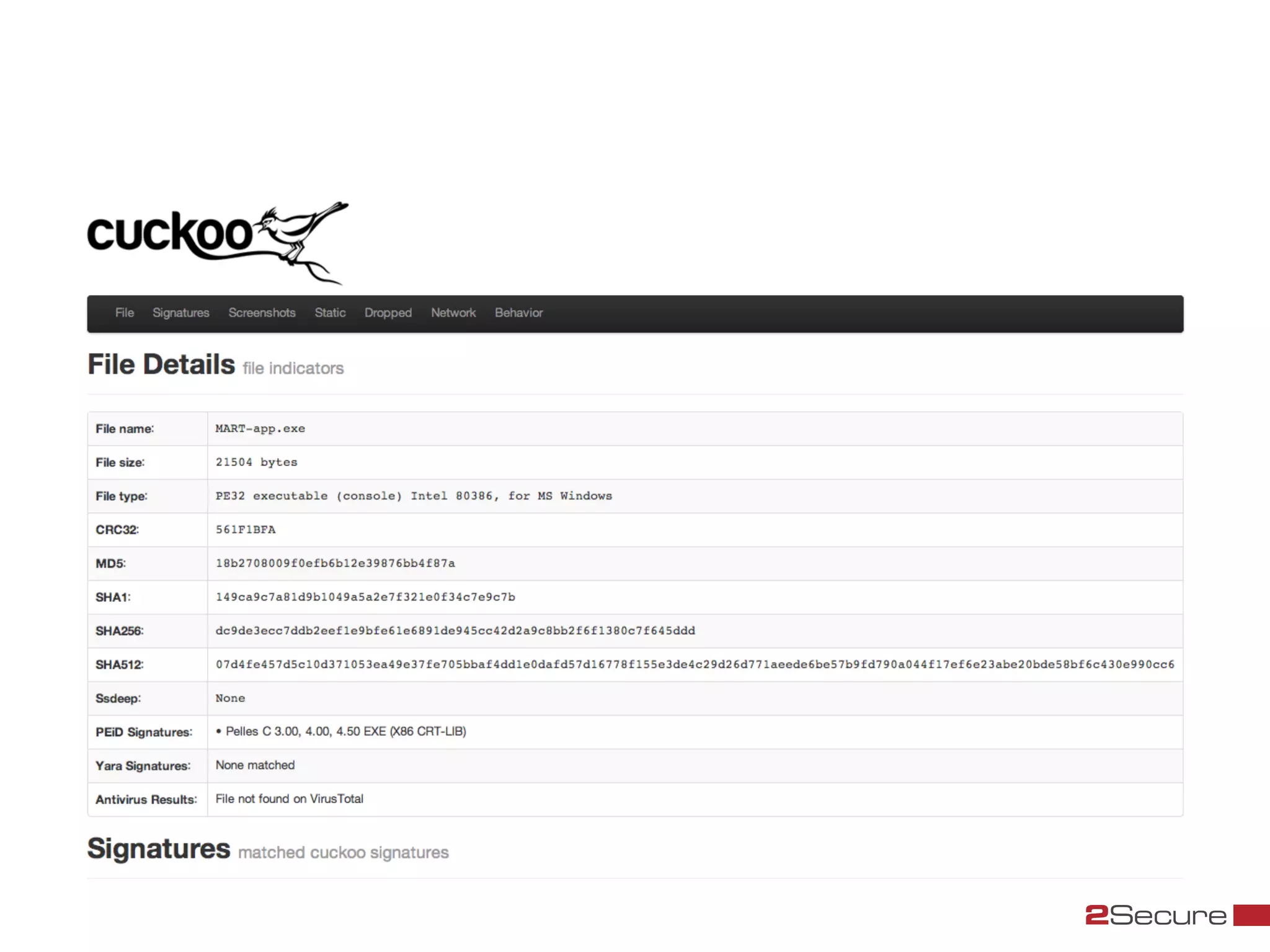
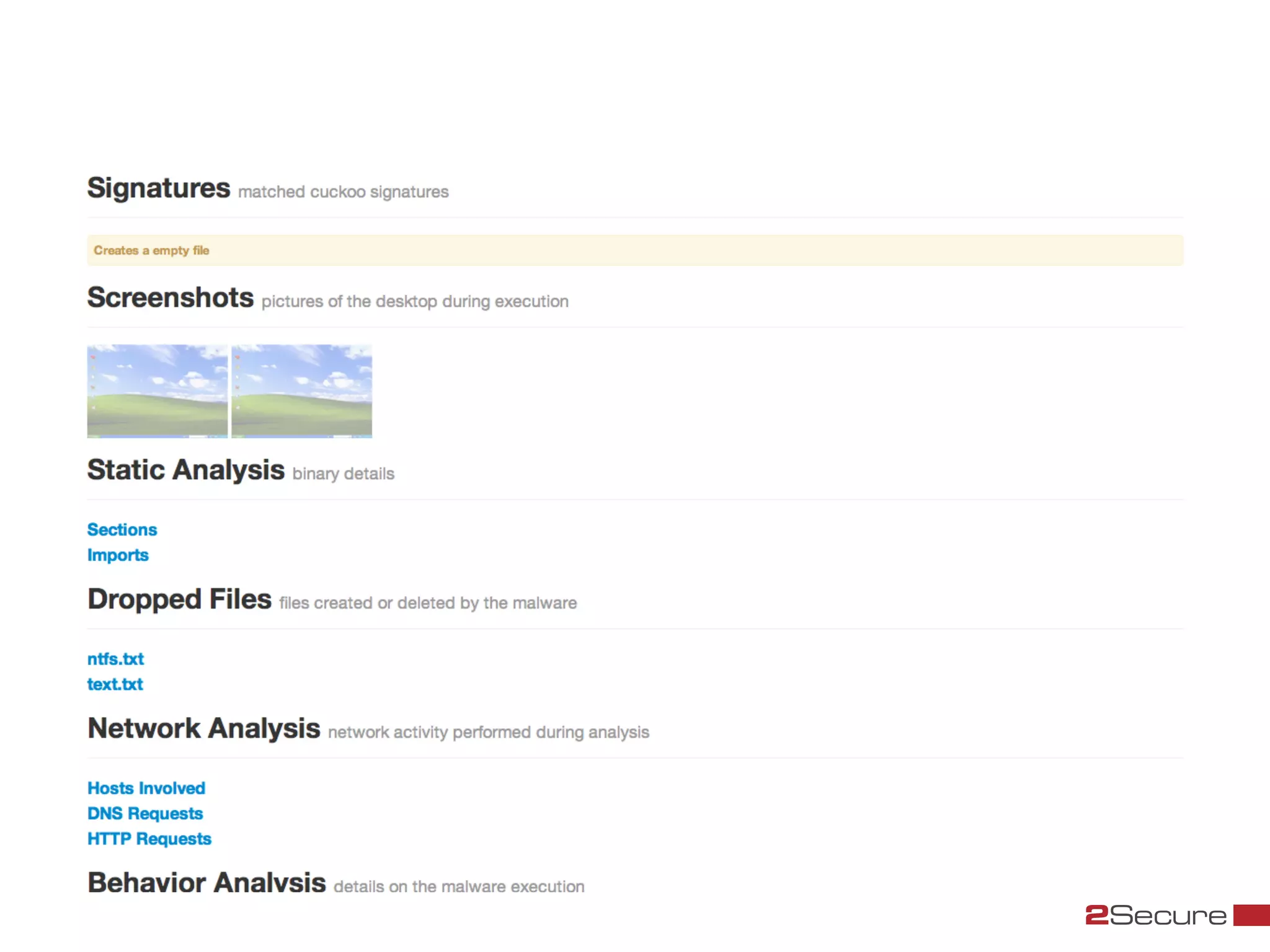
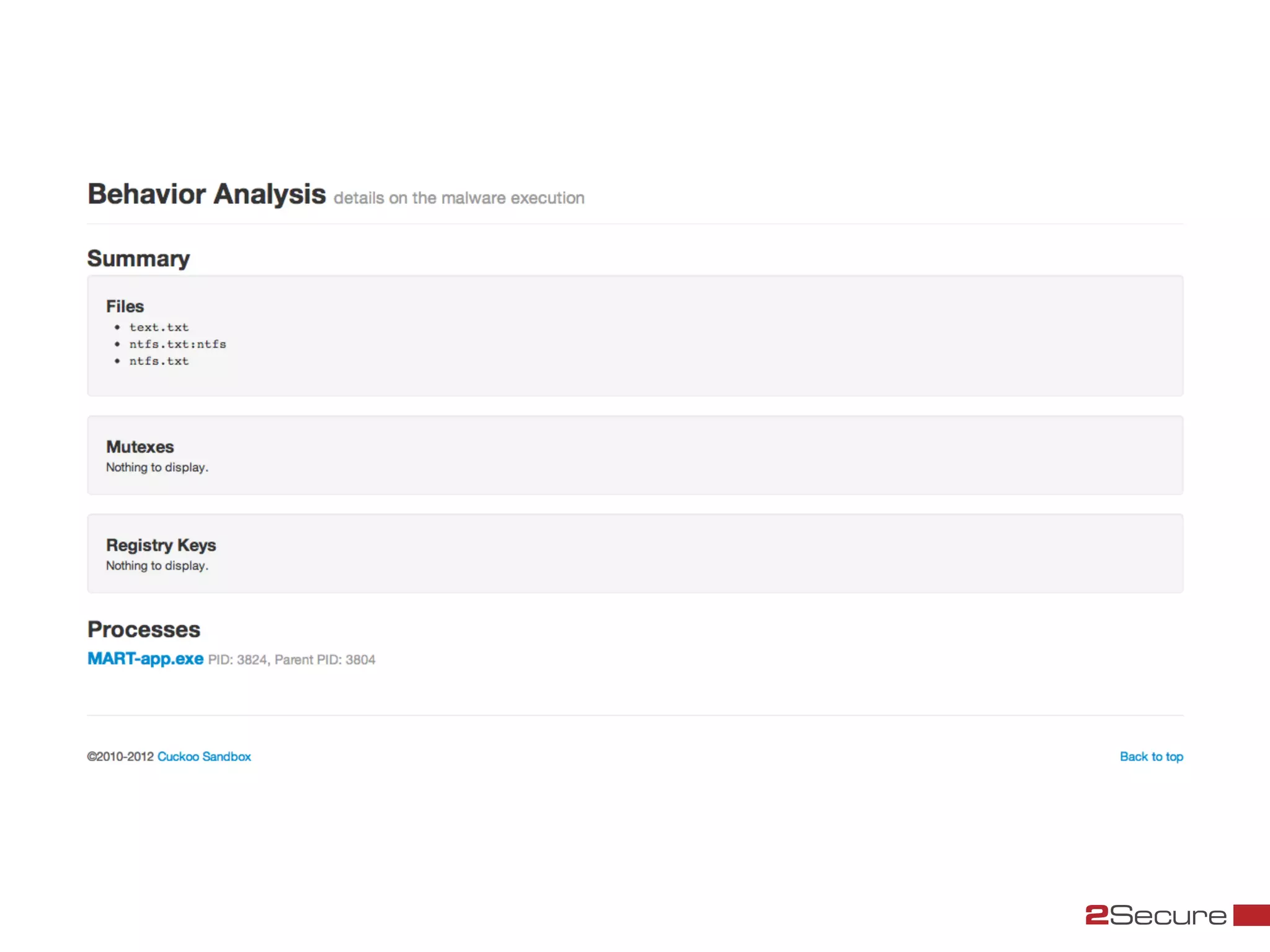
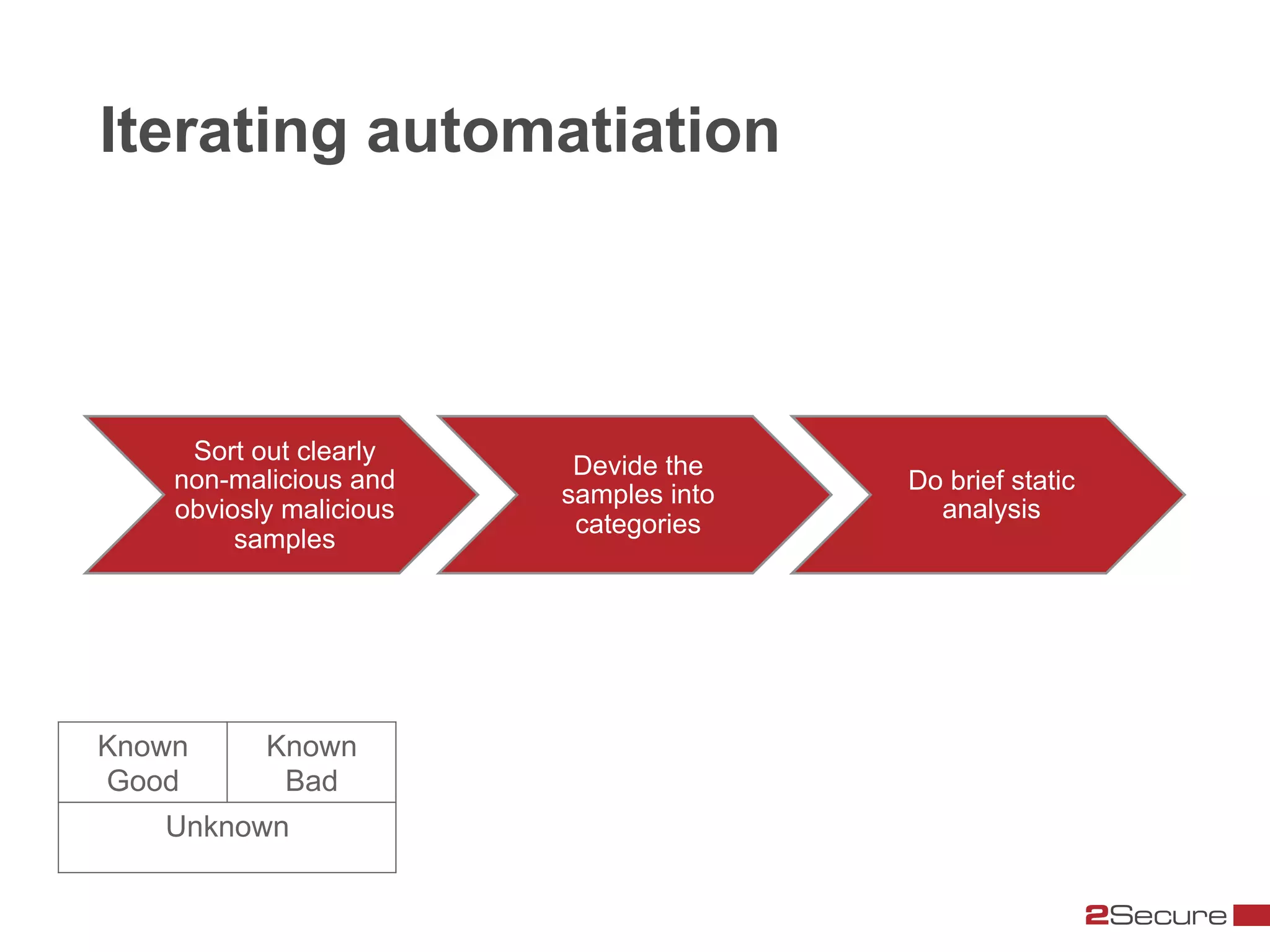
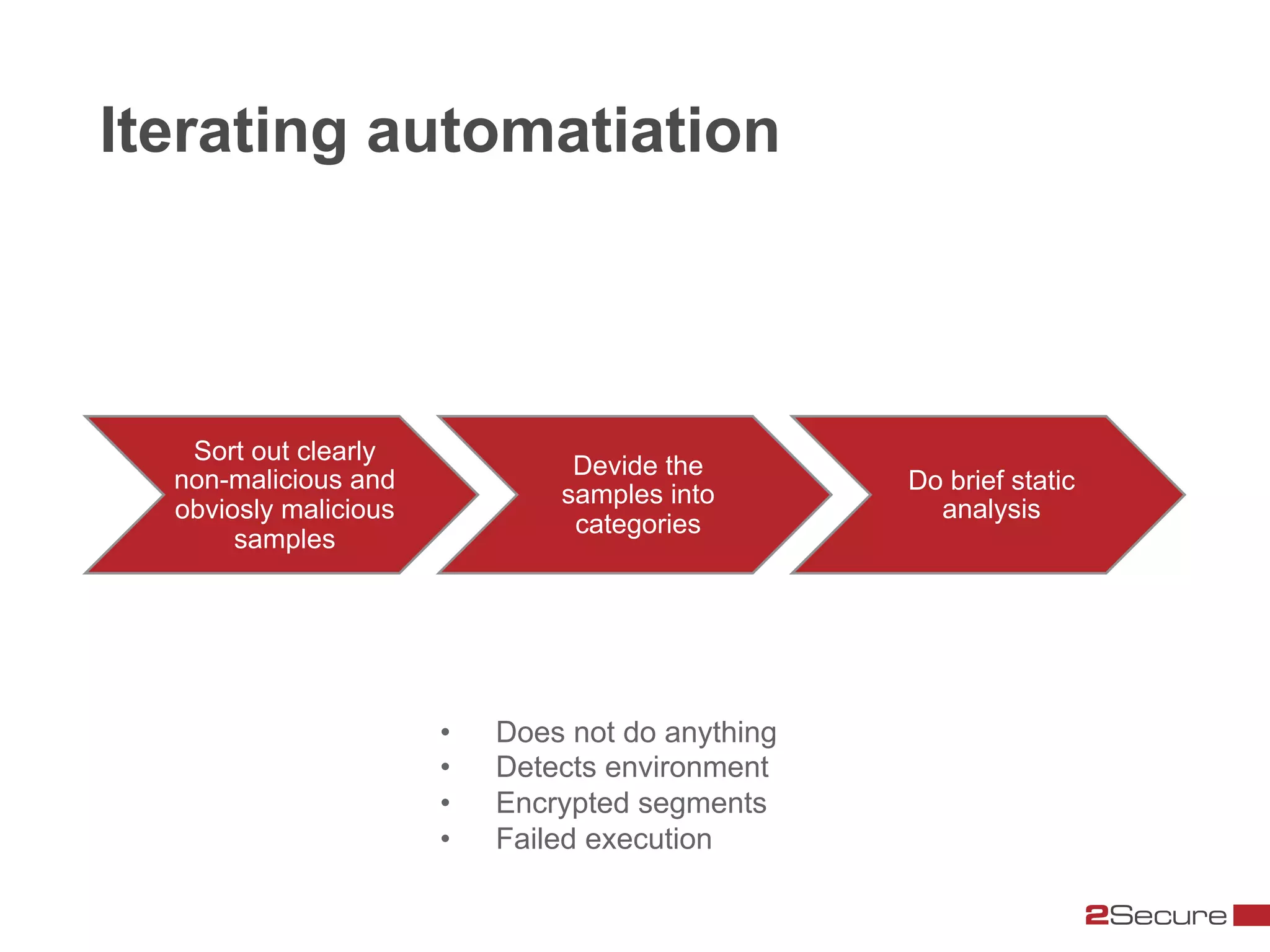
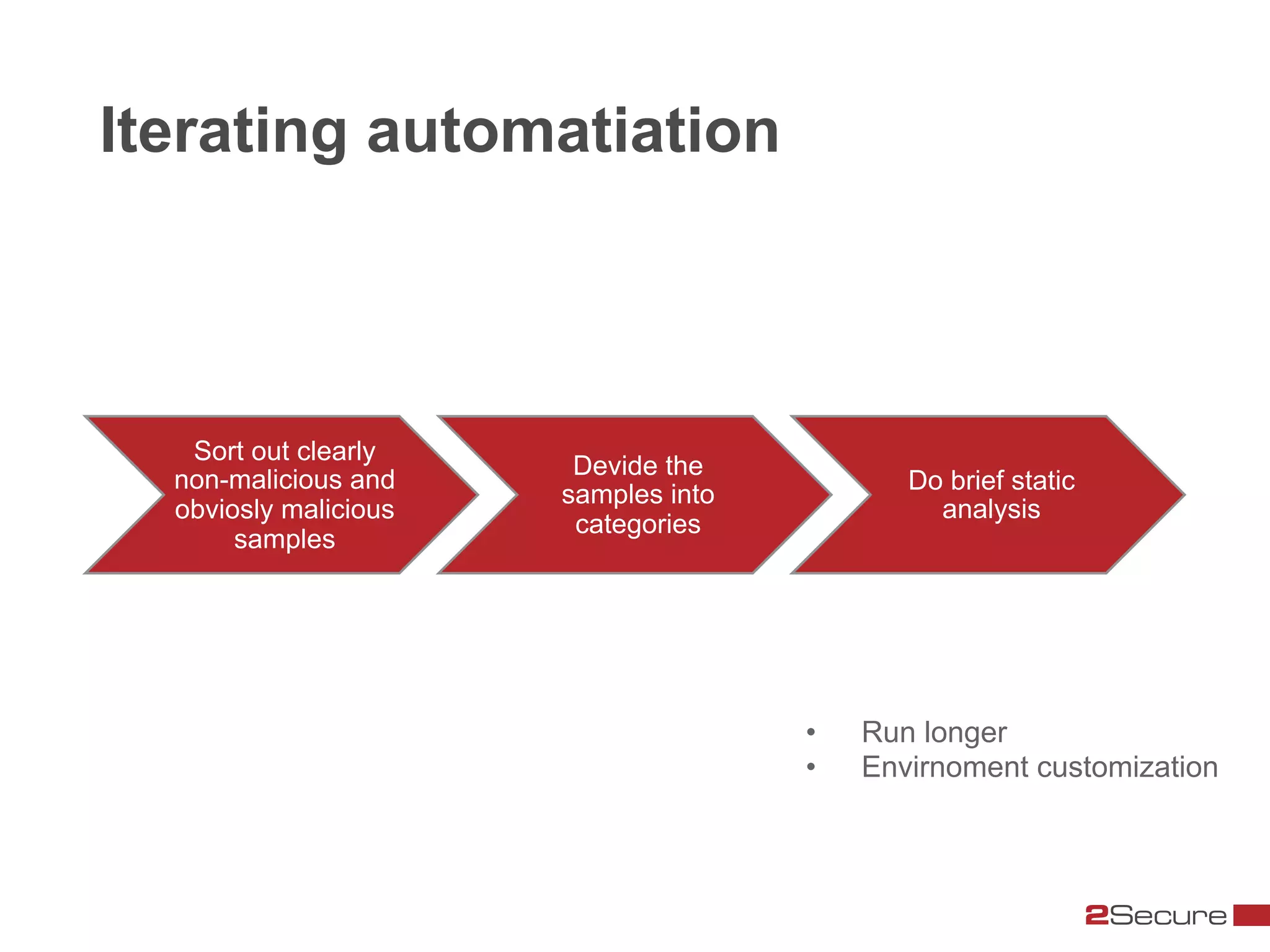
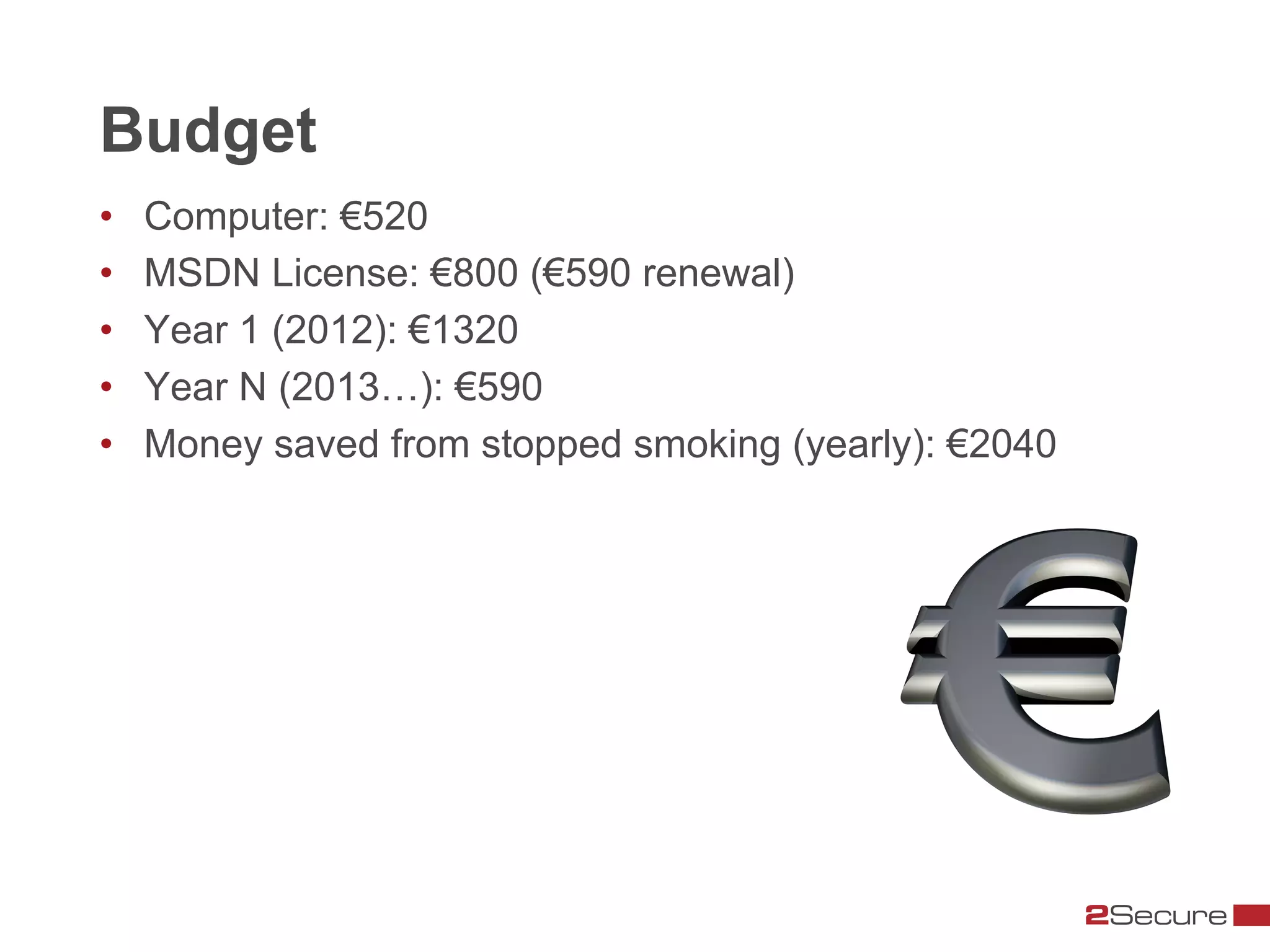
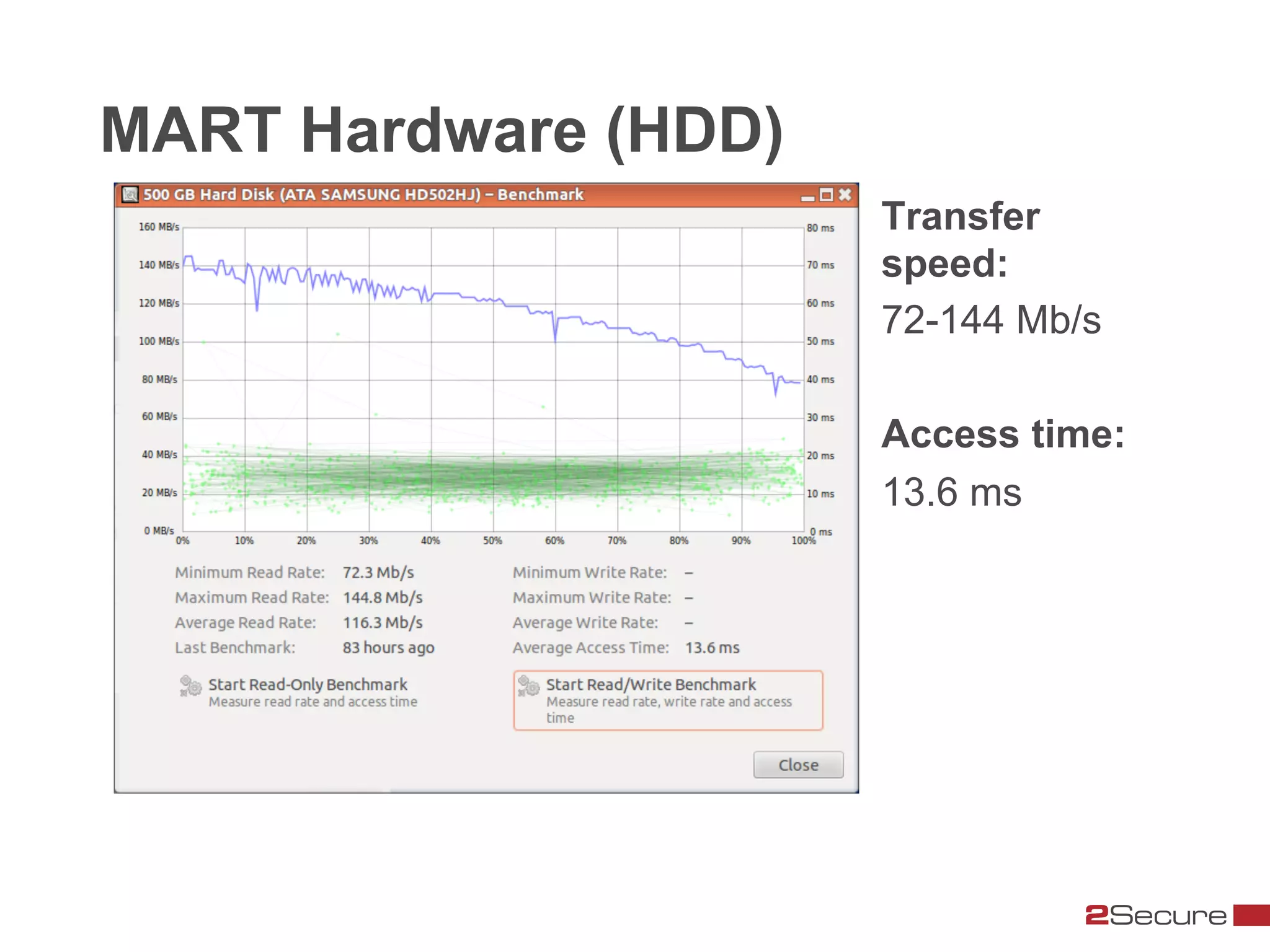
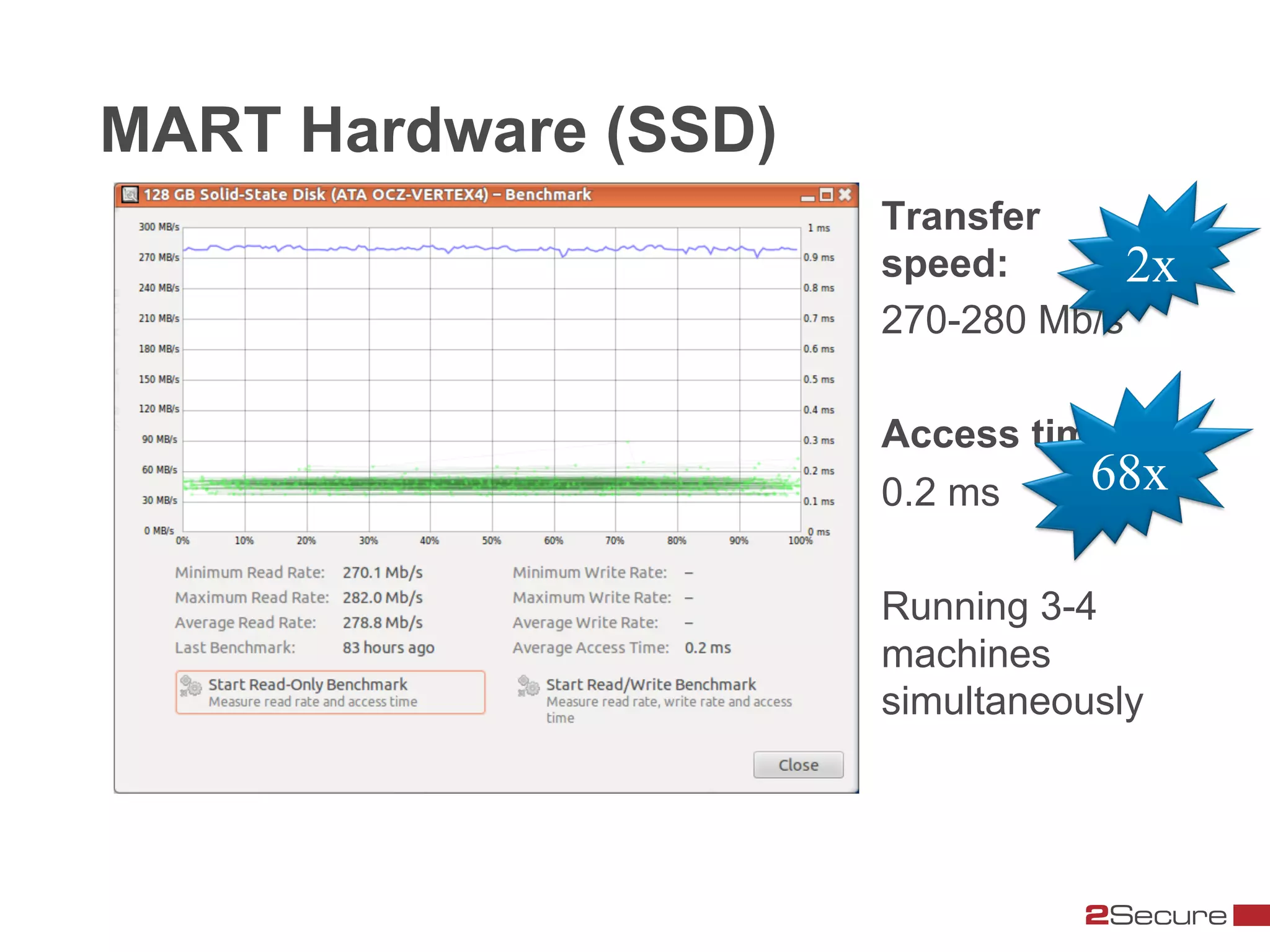
The document discusses budget-friendly strategies for malware analysis, emphasizing automation and efficient use of resources to achieve quality results quickly. It introduces the MART project, a malware analysis toolkit that includes components for sample acquisition and analysis, and highlights common challenges in virtual machine analysis. Key recommendations include investing in hardware that supports multiple virtual machines and leveraging community resources for malware collection and exchange.














![Existing barebone implementations
• BareBox
• BareBox: Efficient Malware Analysis on Bare-Metal
• Dhilung Kirat, Giovanni Vigna, Christopher Kruegel
• ACSAC 2011
• No code has been released
• NVMTrace
• Entrapment: Tricking Malware with Transparent,
Scalable Malware Analysis
• Paul Royal
• Blackhat 2012 EUROPE
• Requires special hardware (Intelligent Platform
Management Interface [IPMI])](https://image.slidesharecdn.com/martpresentation-deepsec-121219042336-phpapp02/75/Malware-Analysis-on-a-Shoestring-Budget-39-2048.jpg)