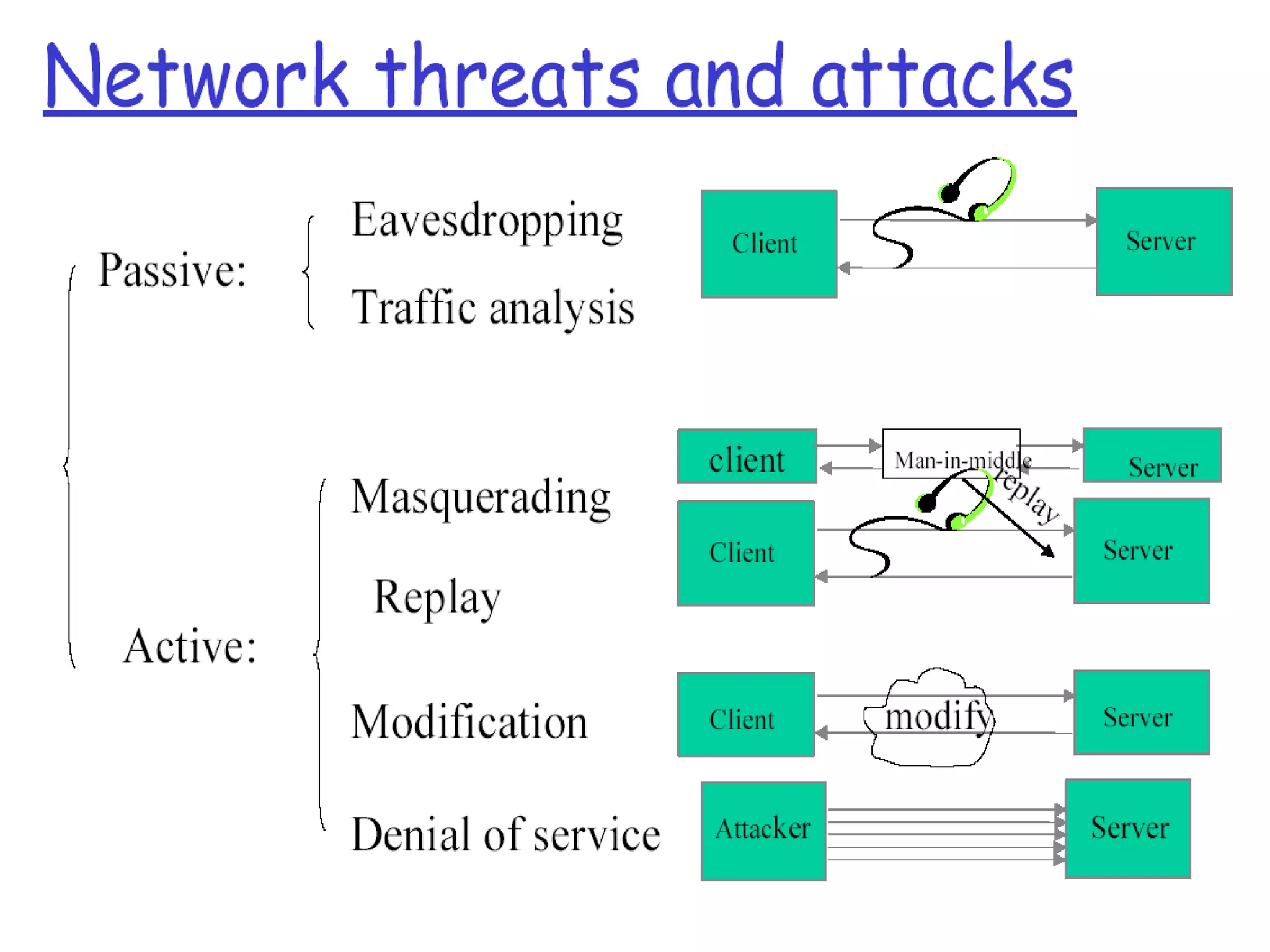
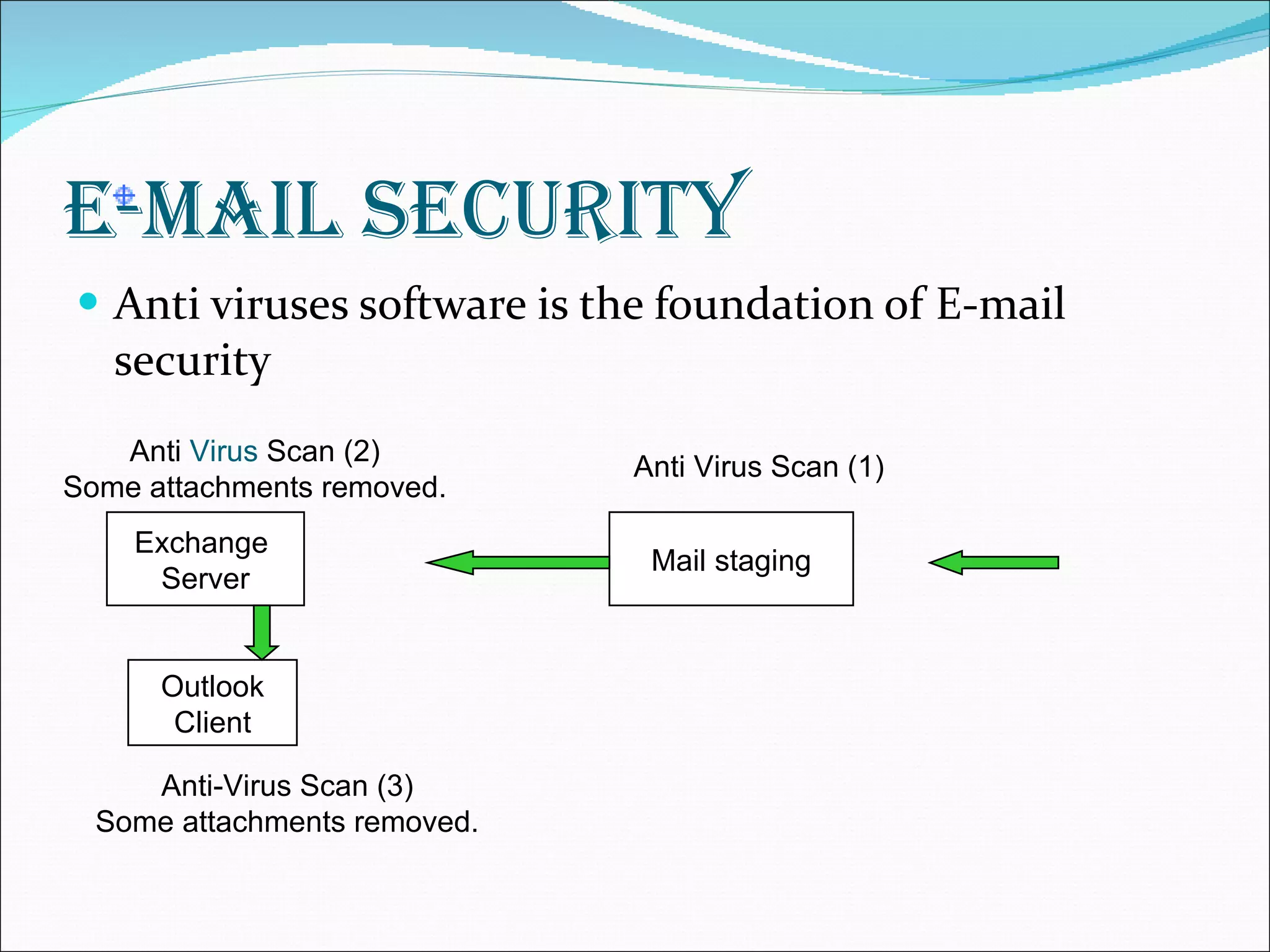
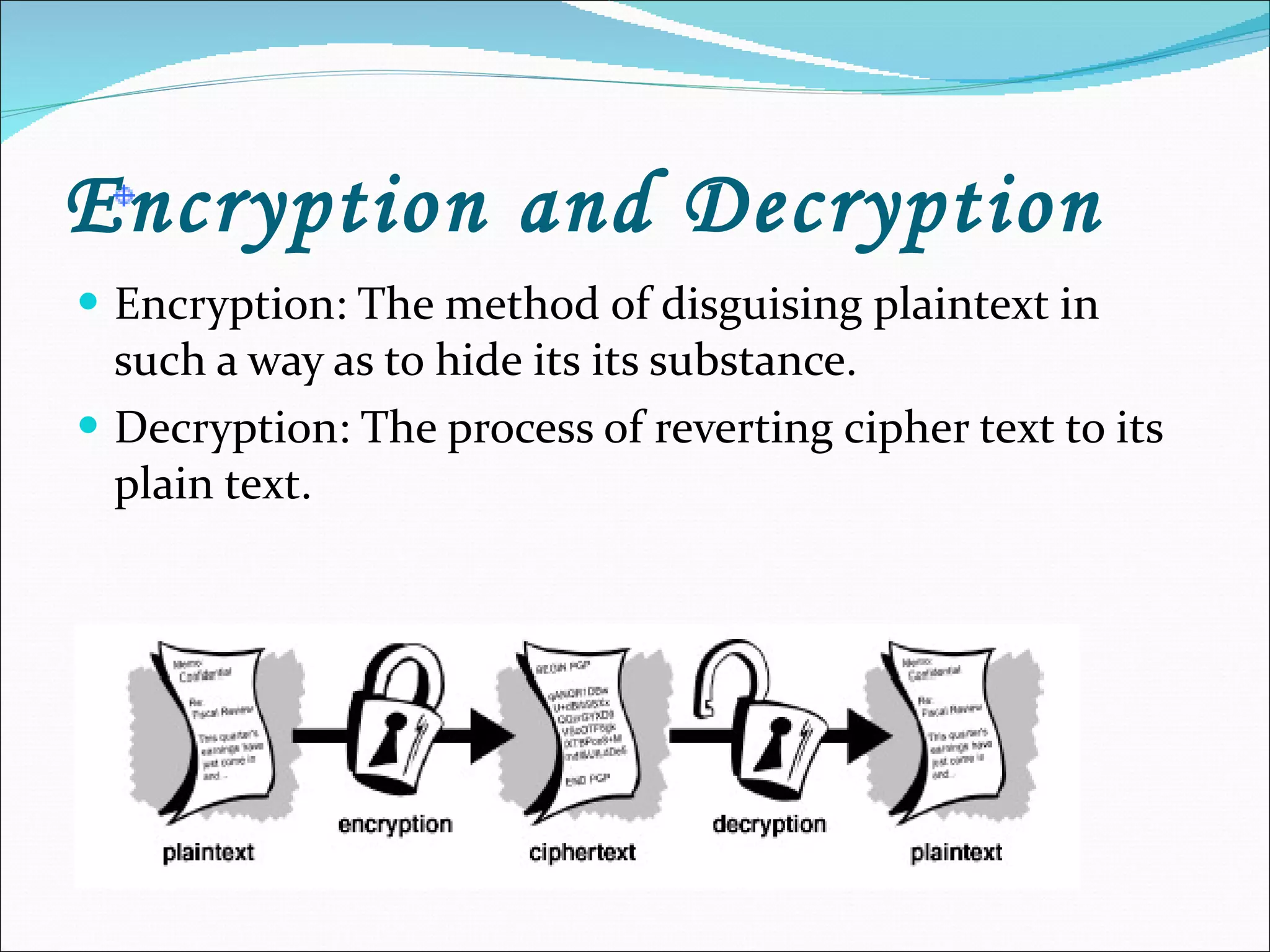
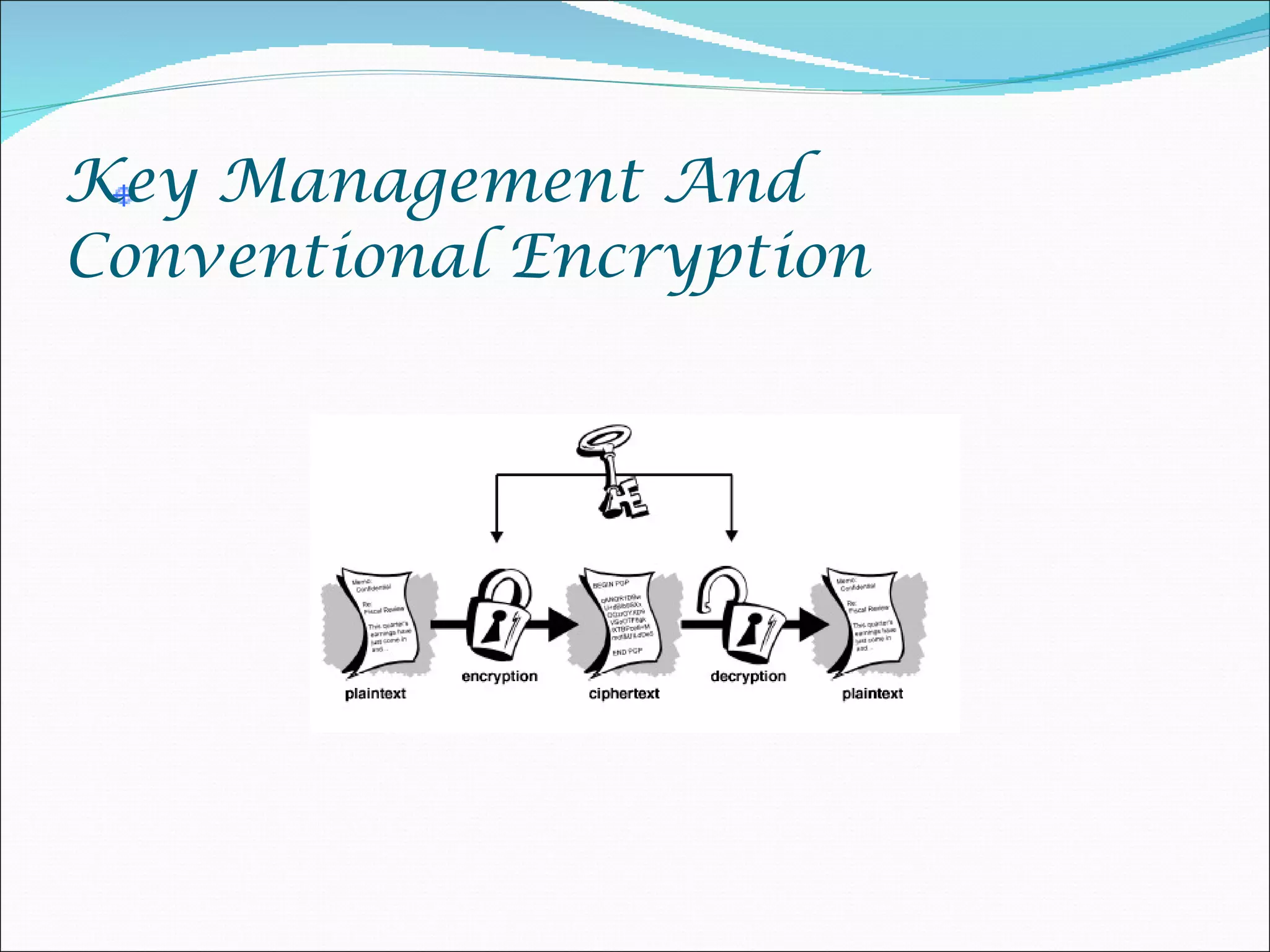
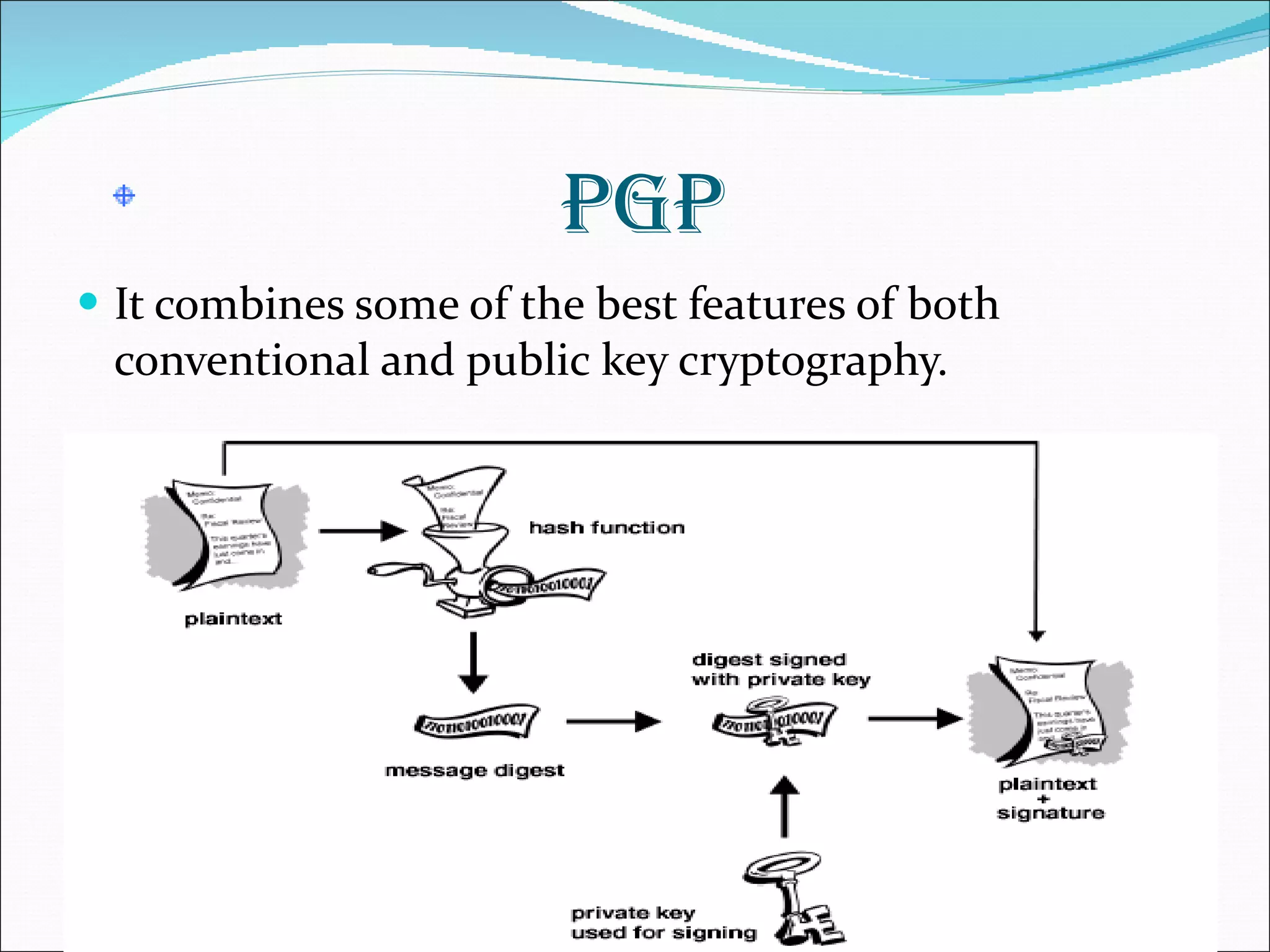
The document discusses network security and cryptography, emphasizing the importance of preventing unauthorized access and detecting breaches in computer systems. It provides guidelines for password security, email protection, and the evolving threats from blended and phishing attacks, as well as an overview of cryptographic methods including conventional and public key cryptography. The conclusion highlights that achieving security requires collective cooperation and consistent practices from all users.