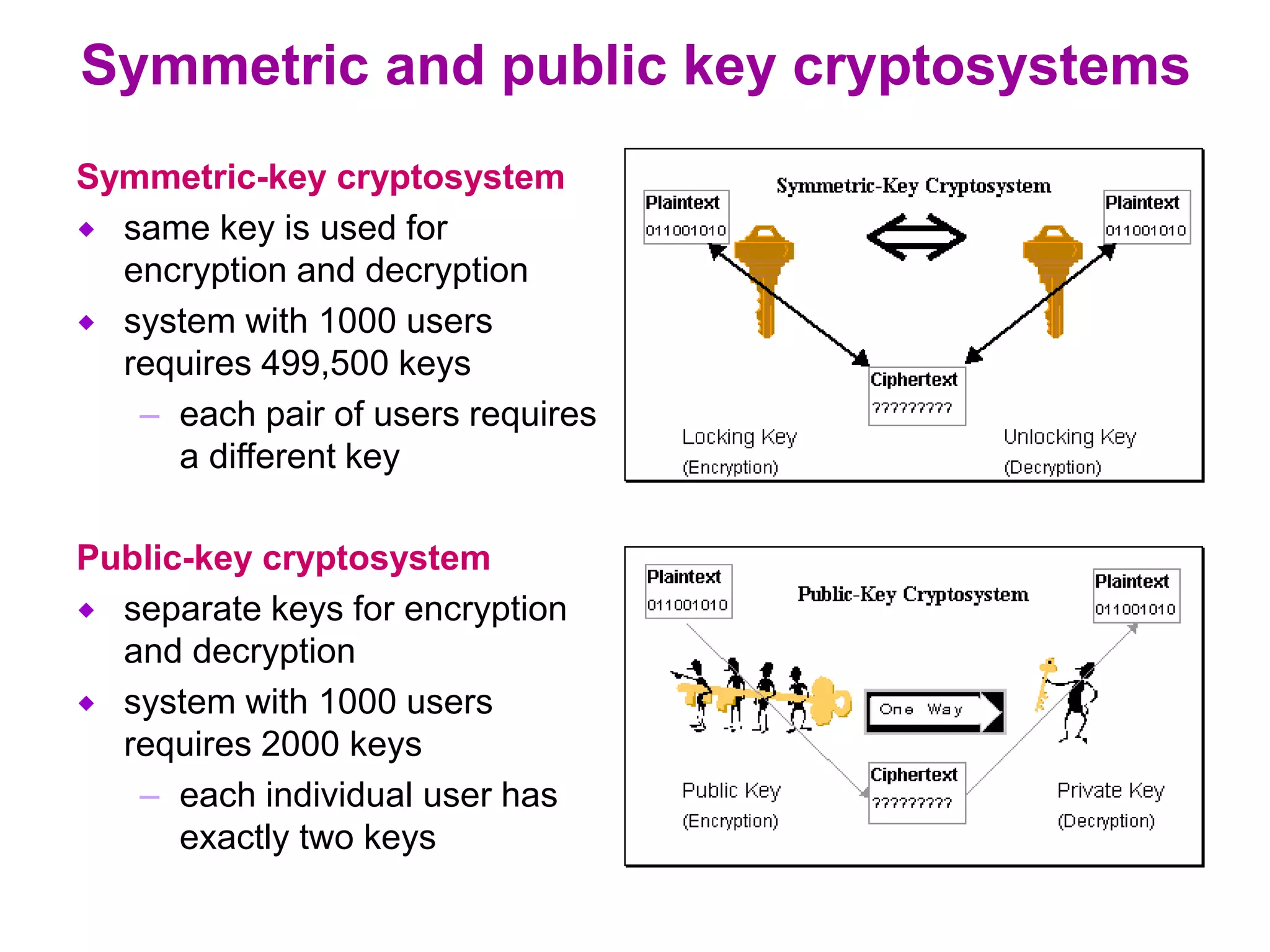
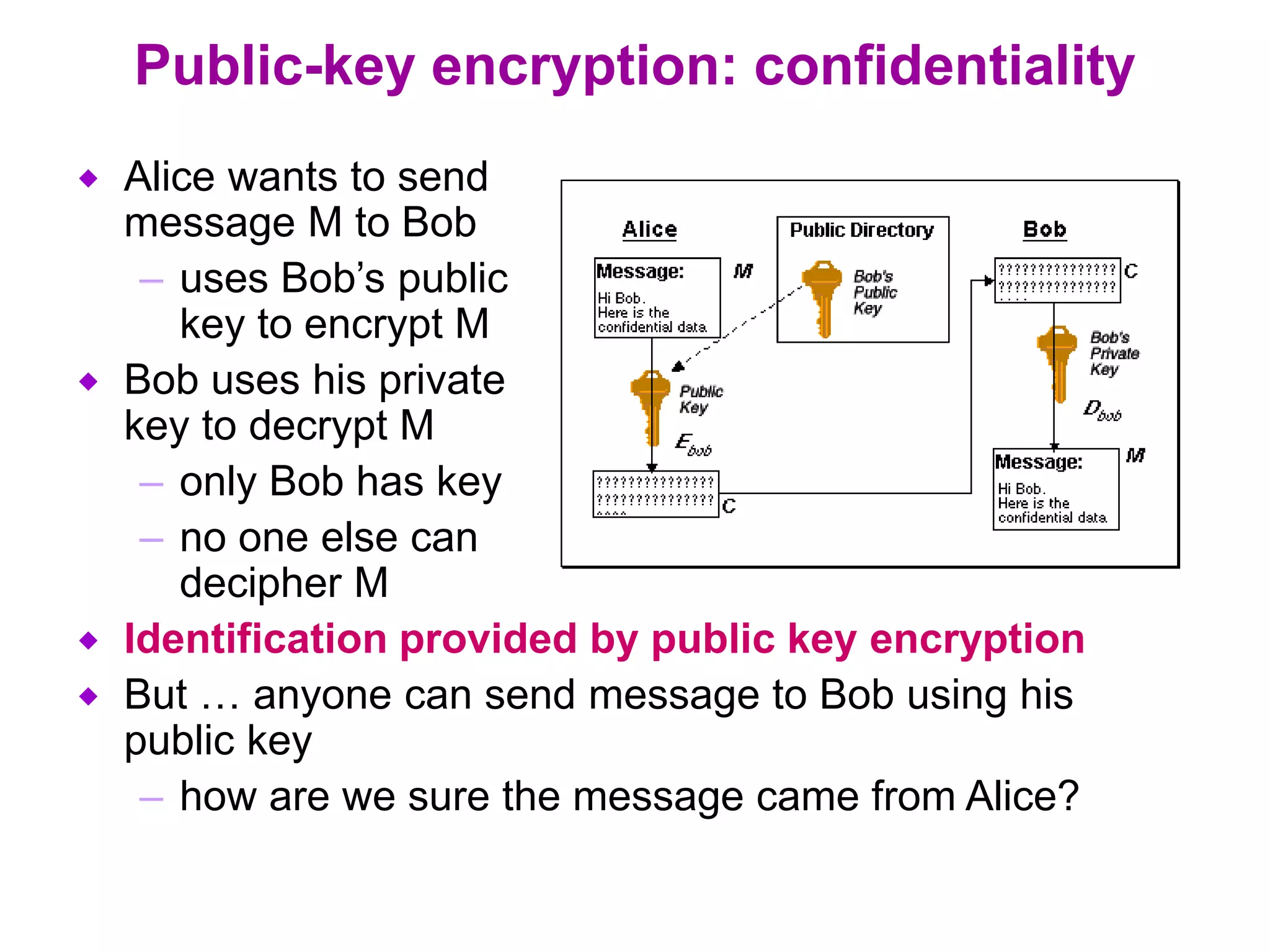
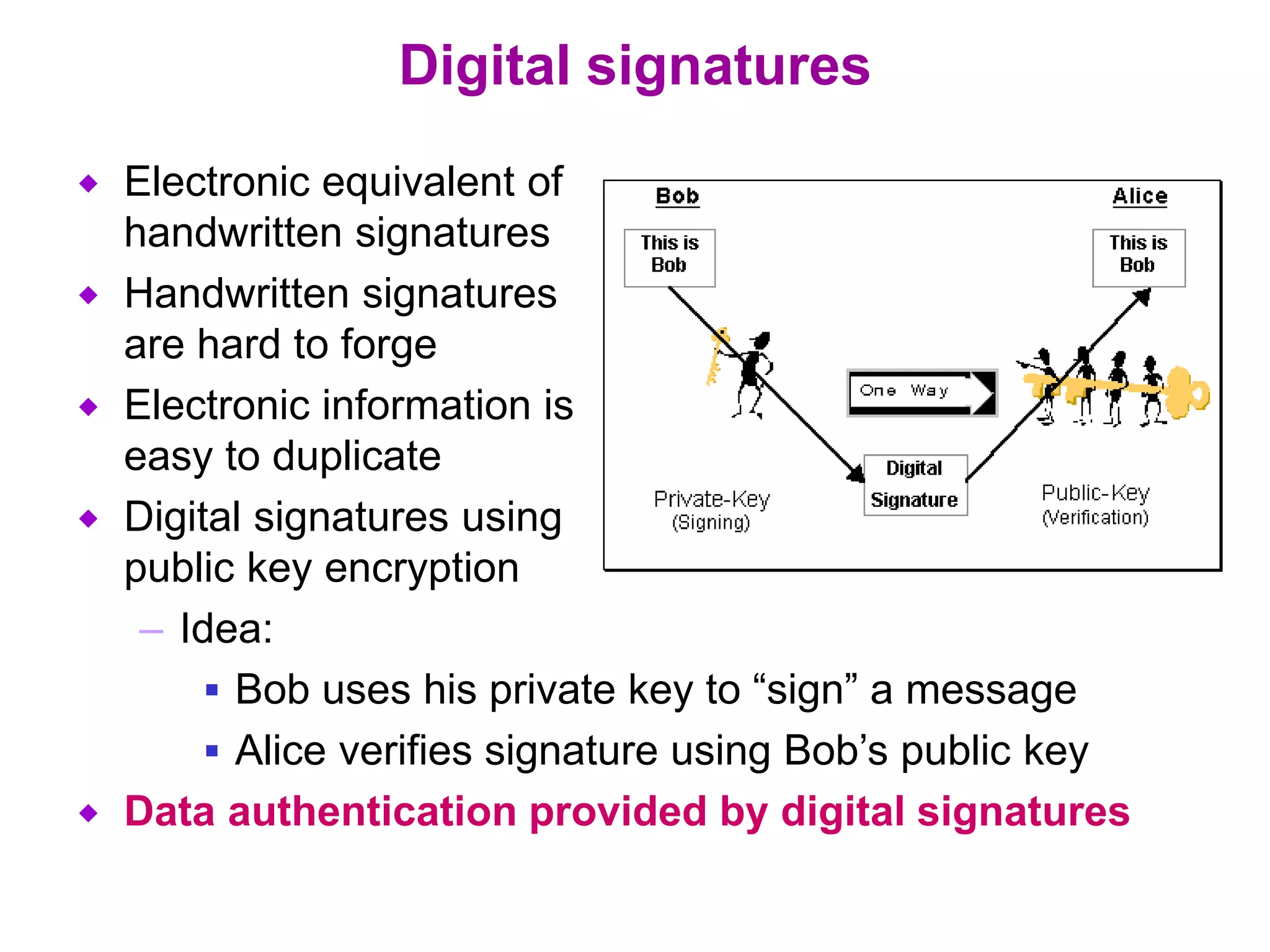
Information security involves all measures taken to protect electronic data from unauthorized access, use, disclosure, alteration or destruction. It aims to provide confidentiality by concealing data, integrity by ensuring data is authentic and unmodified, and availability by maintaining efficient system function even with security provisions. While no single measure ensures complete security, cryptographic systems can potentially provide high levels of security through confidentiality, integrity and availability. Public key encryption uses separate keys for encryption and decryption, allowing secure communication for large networks, while digital signatures and certification authorities provide authentication. Prevention, detection and response work together to secure systems and minimize risks from security attacks.