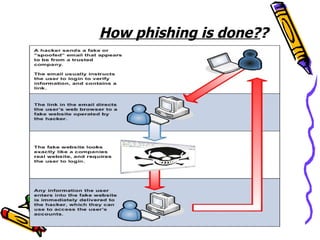
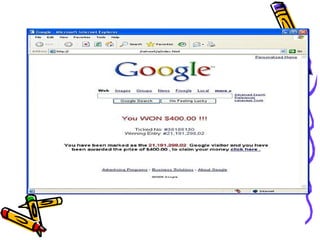
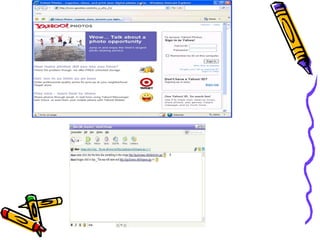
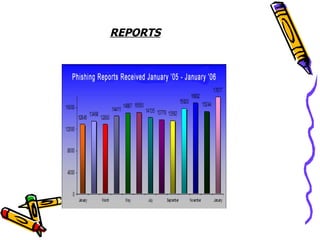
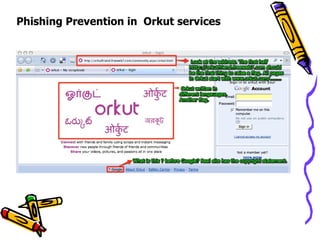
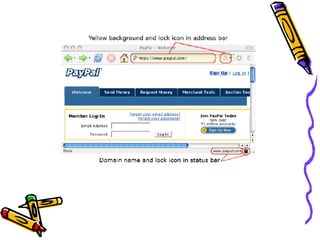
The document discusses phishing, which is a criminal activity using social engineering to fraudulently acquire sensitive information like passwords and credit card details. Phishers masquerade as trustworthy entities through electronic communications. Types of phishing include using JavaScript to alter address bars or using a trusted website's scripts against victims. The document provides examples of PayPal and Yahoo phishing and discusses the damage caused as well as prevention methods like anti-phishing software, challenge questions, and verification tools.