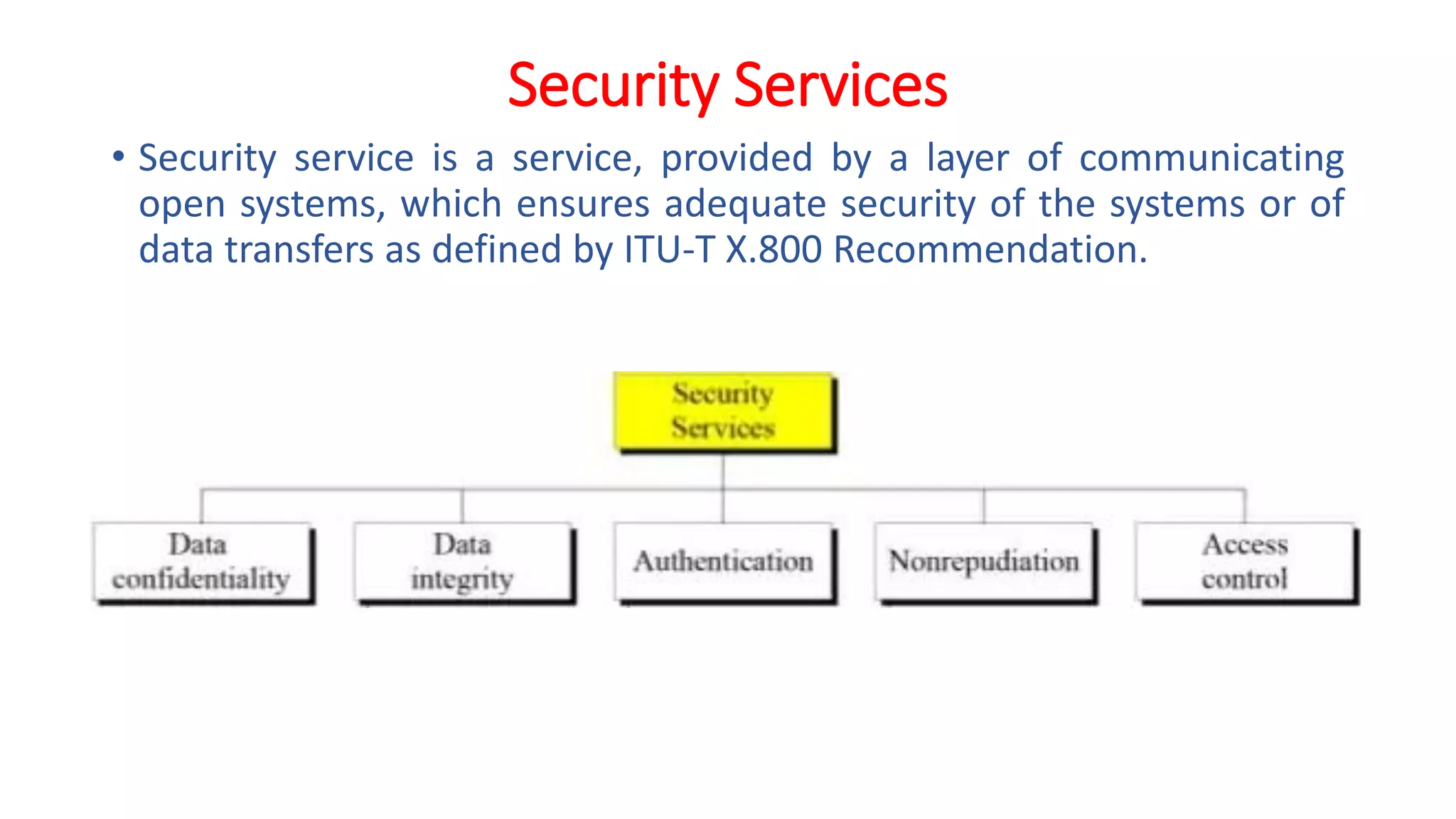
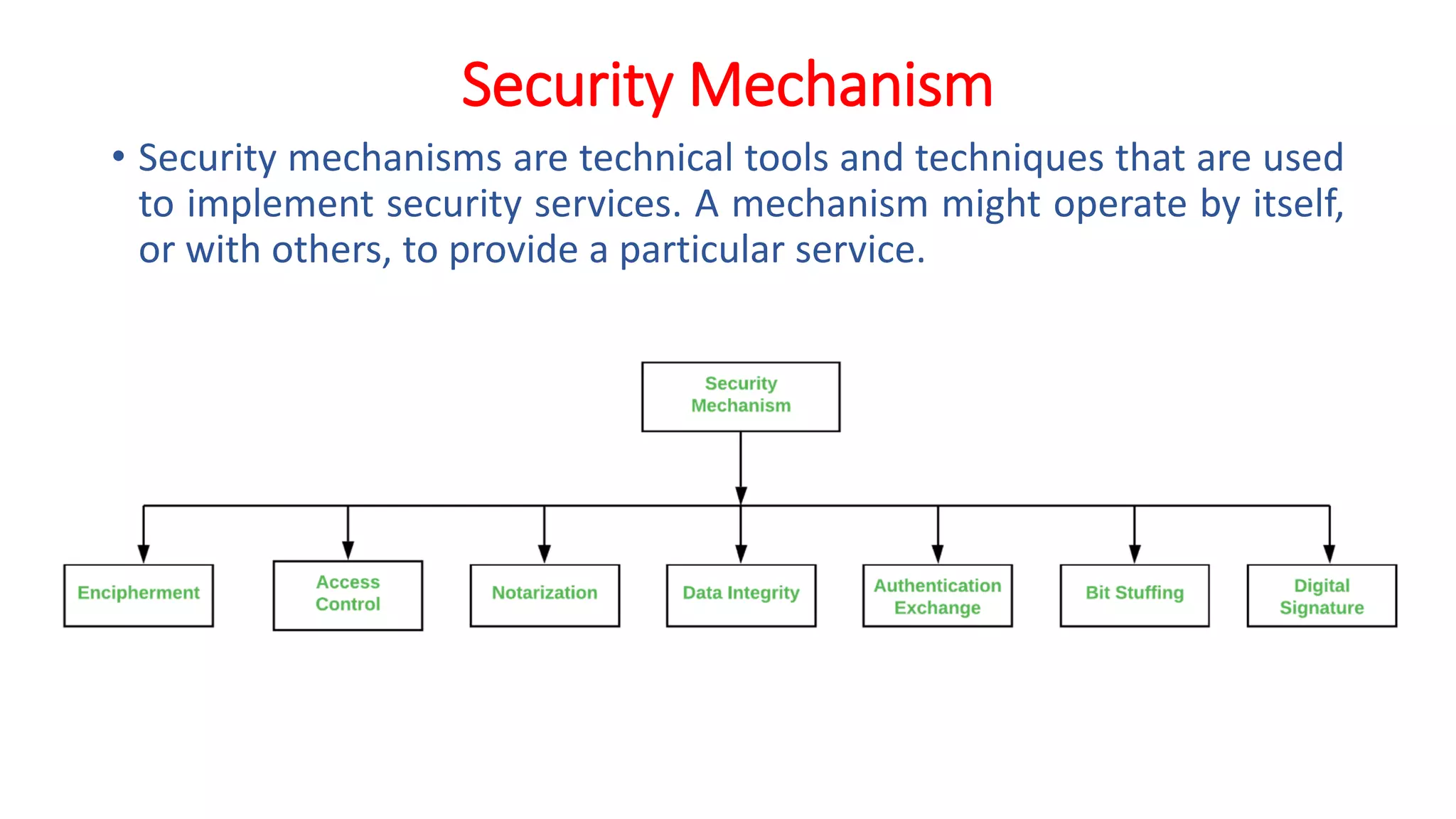
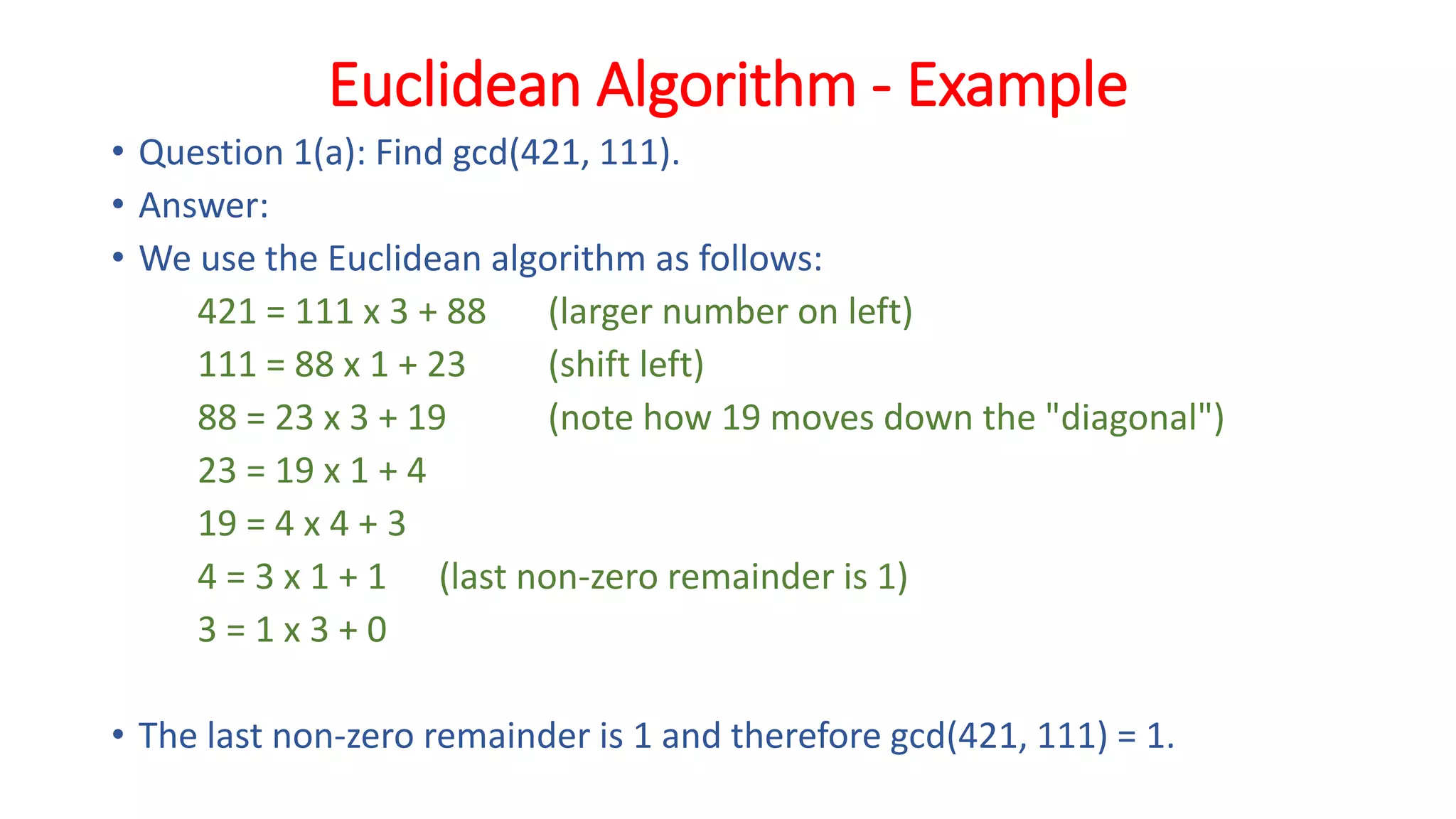
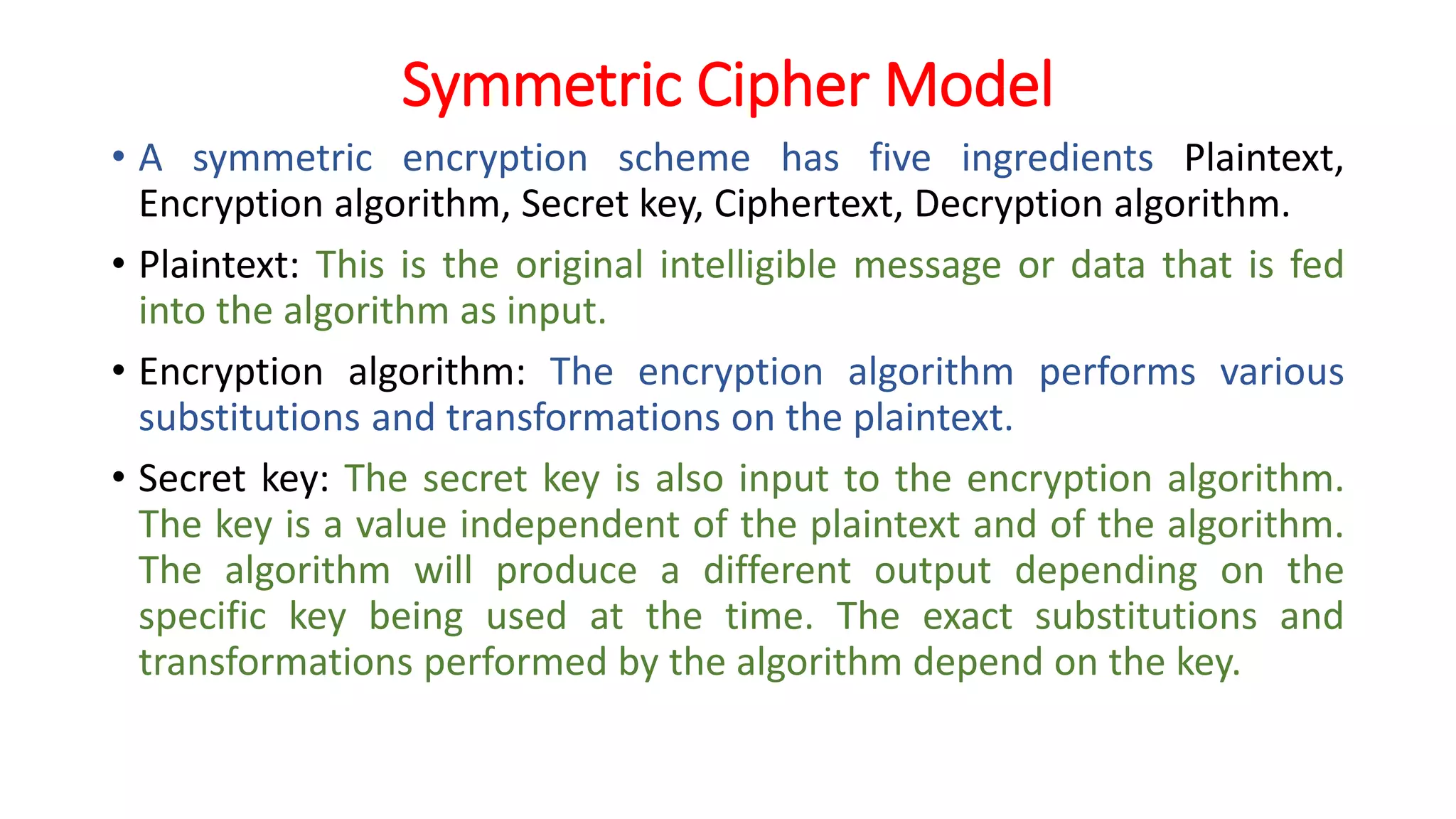
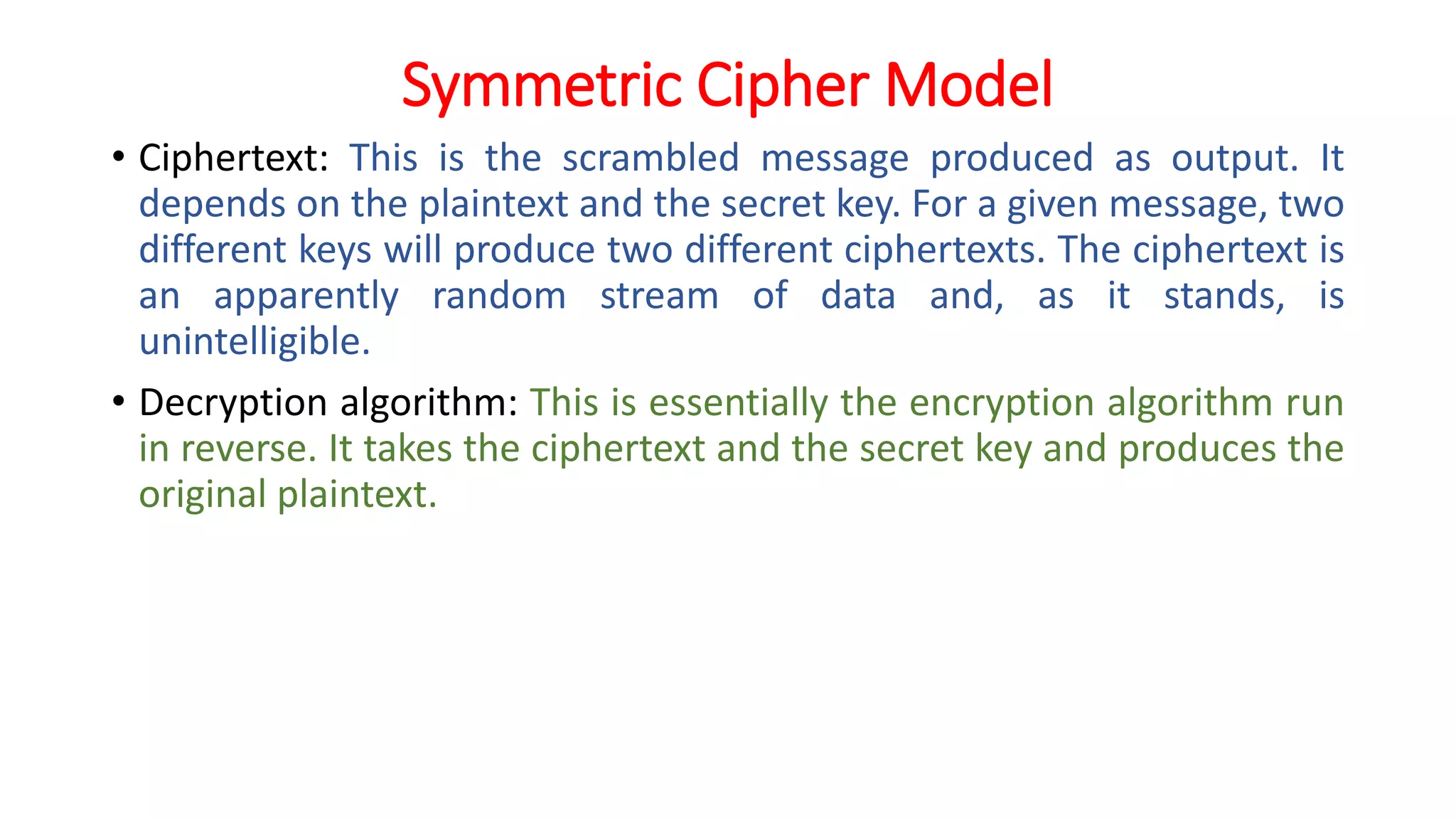
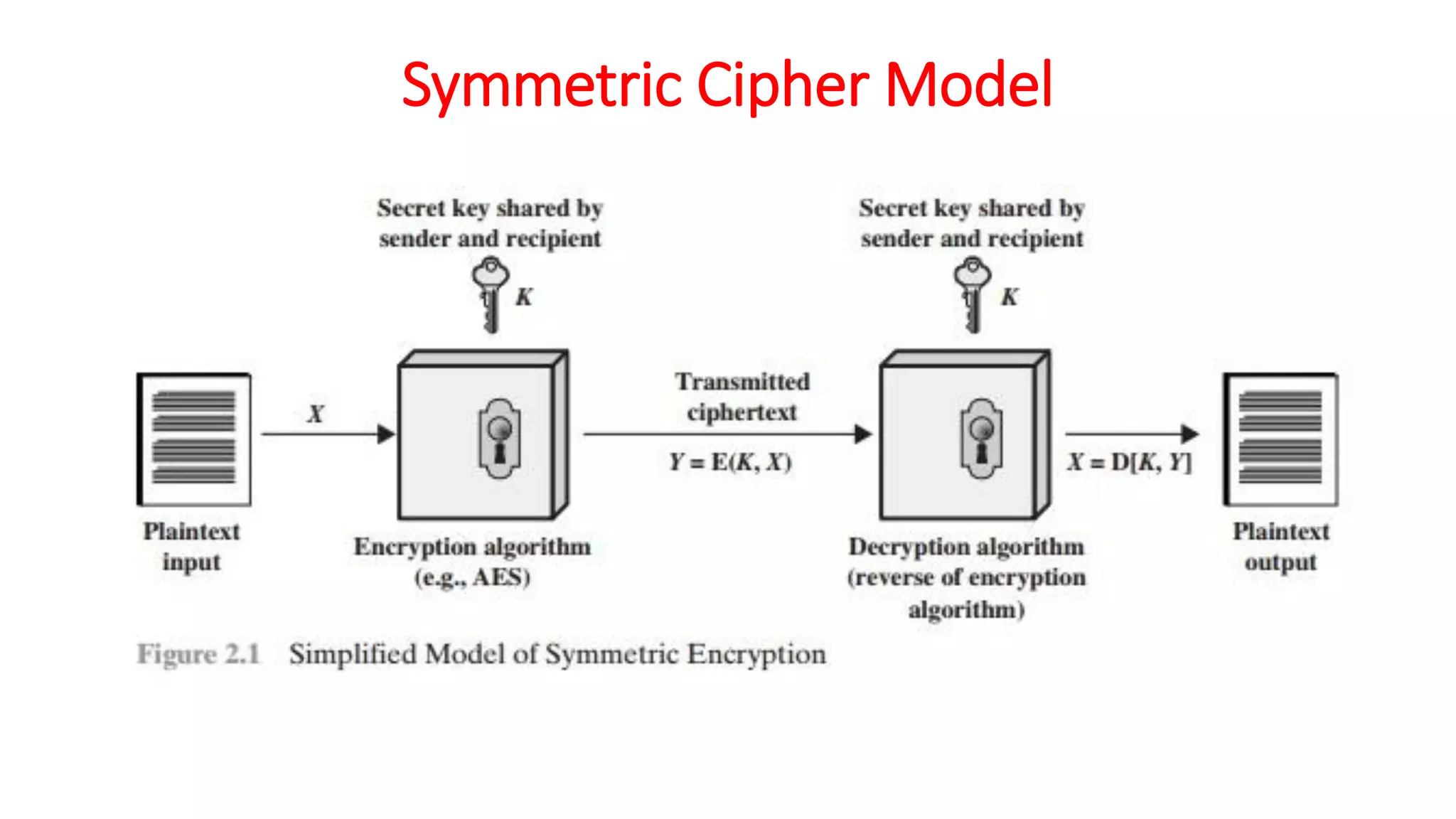
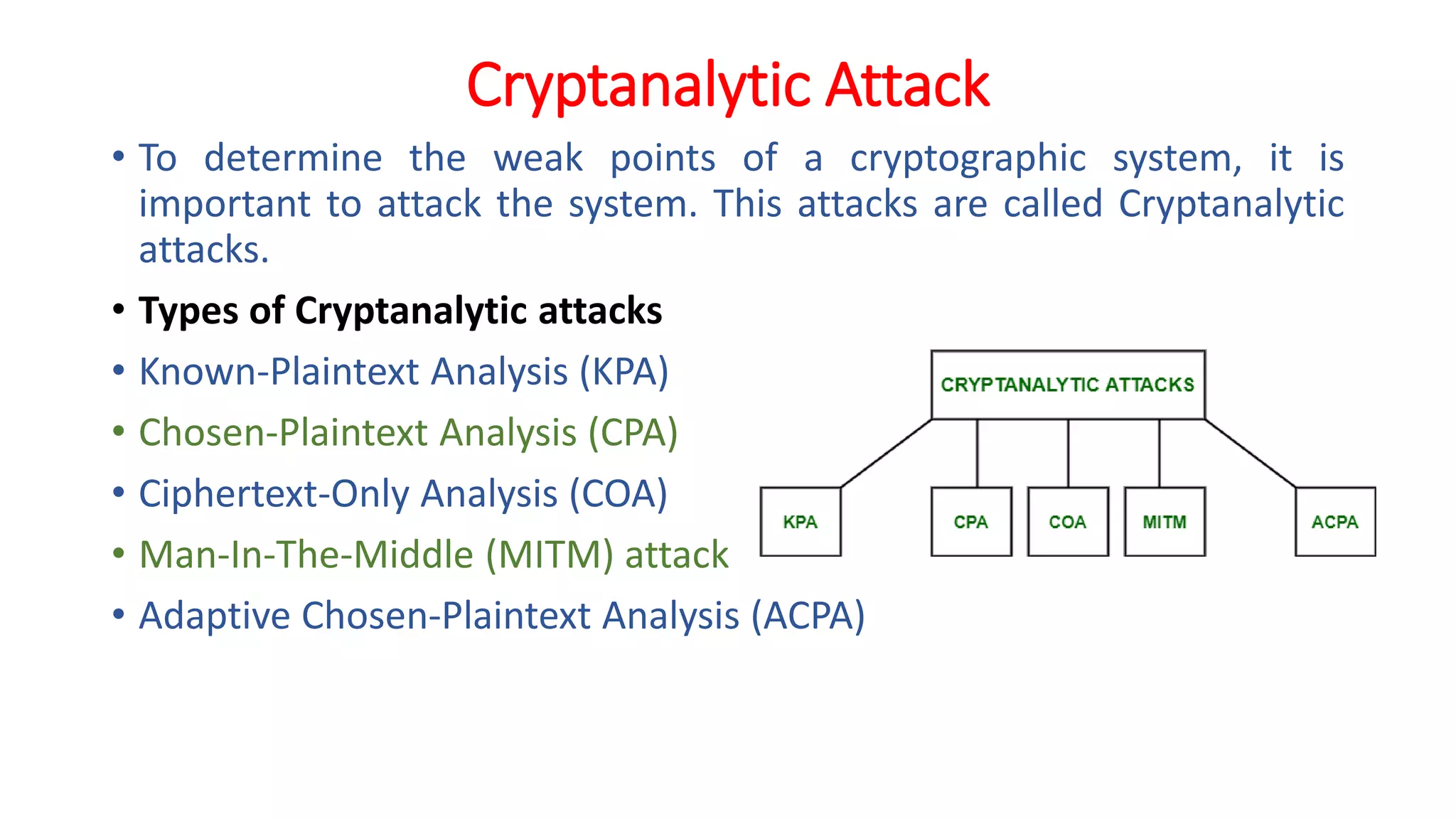
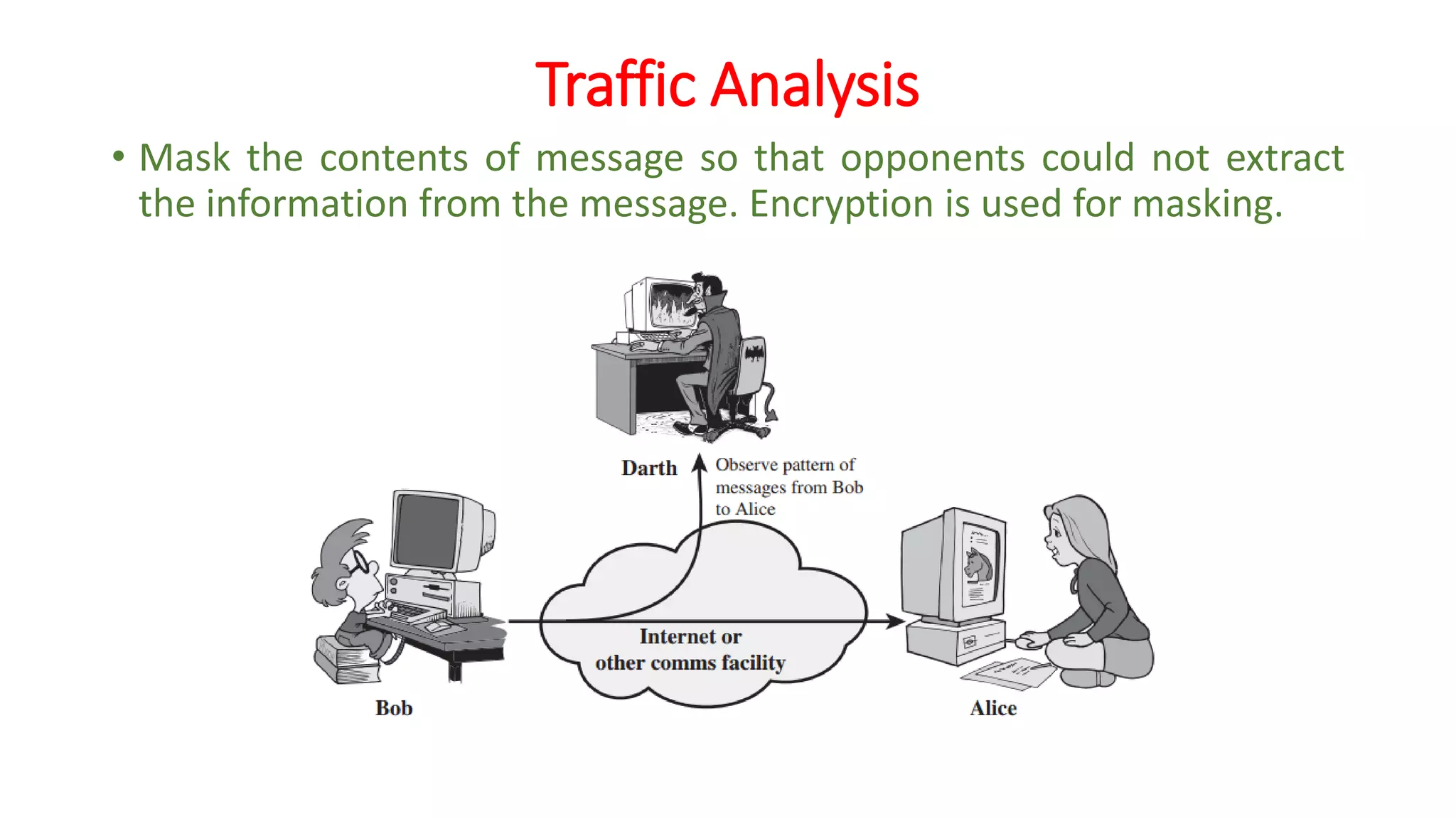
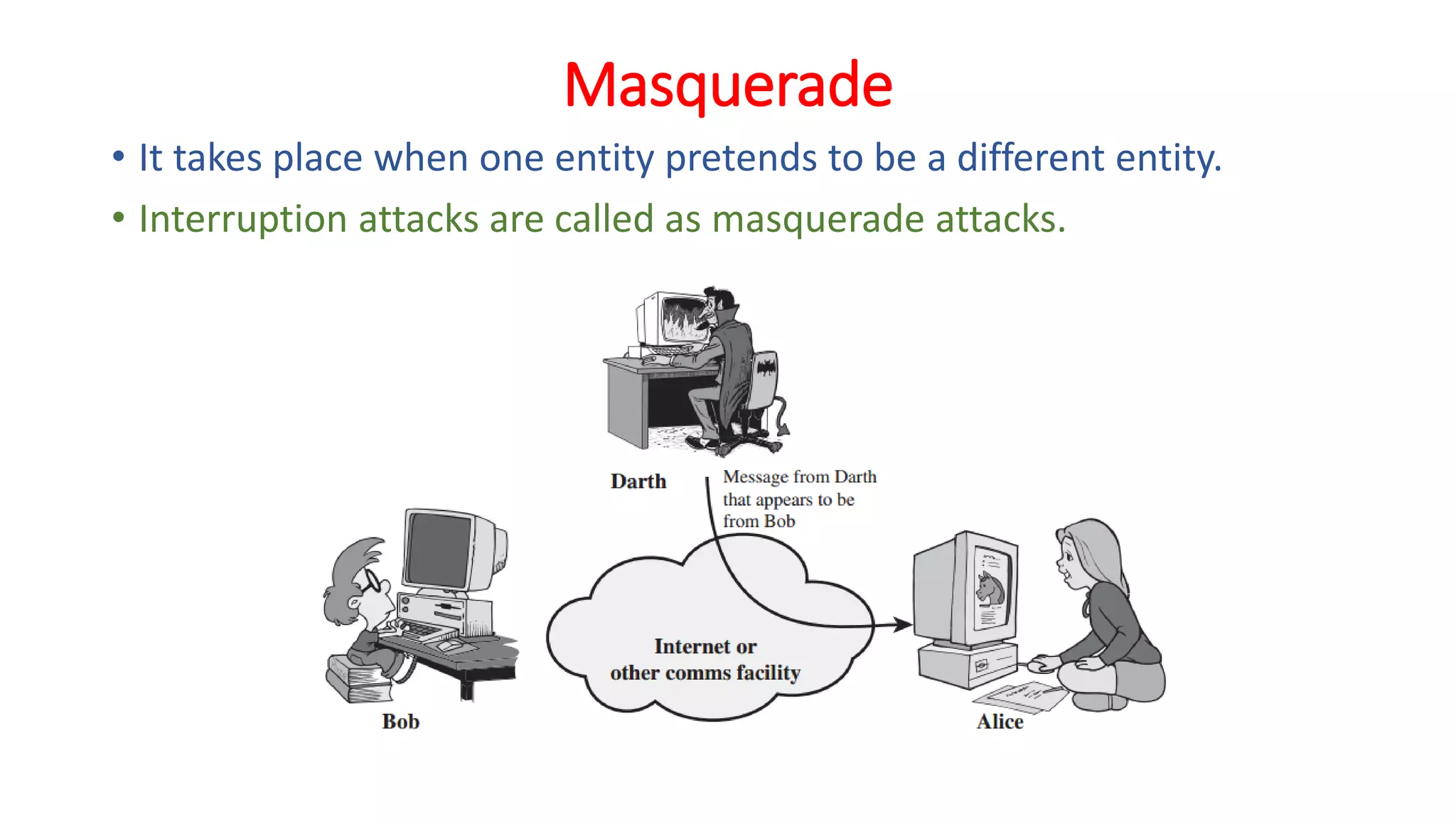
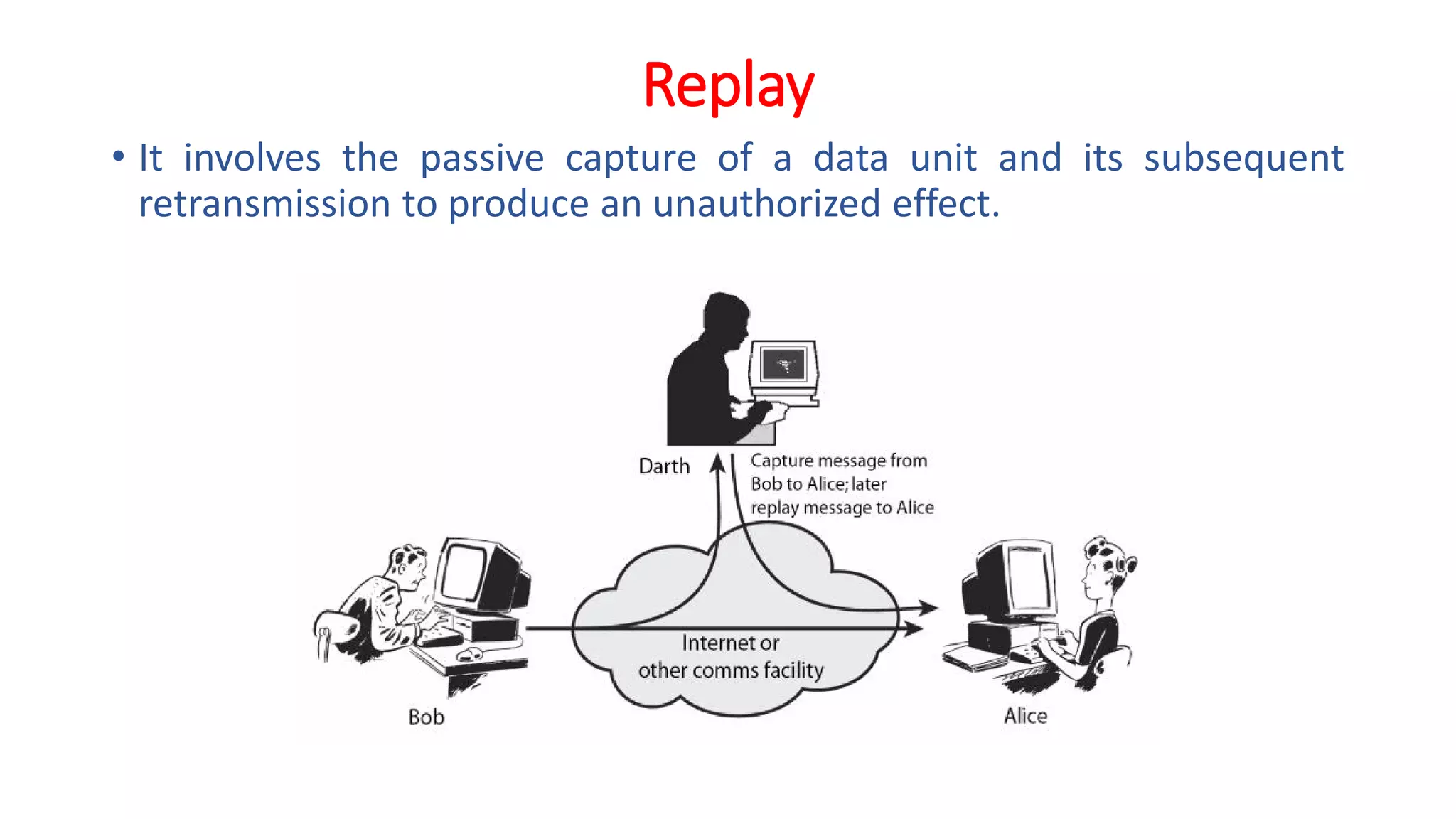
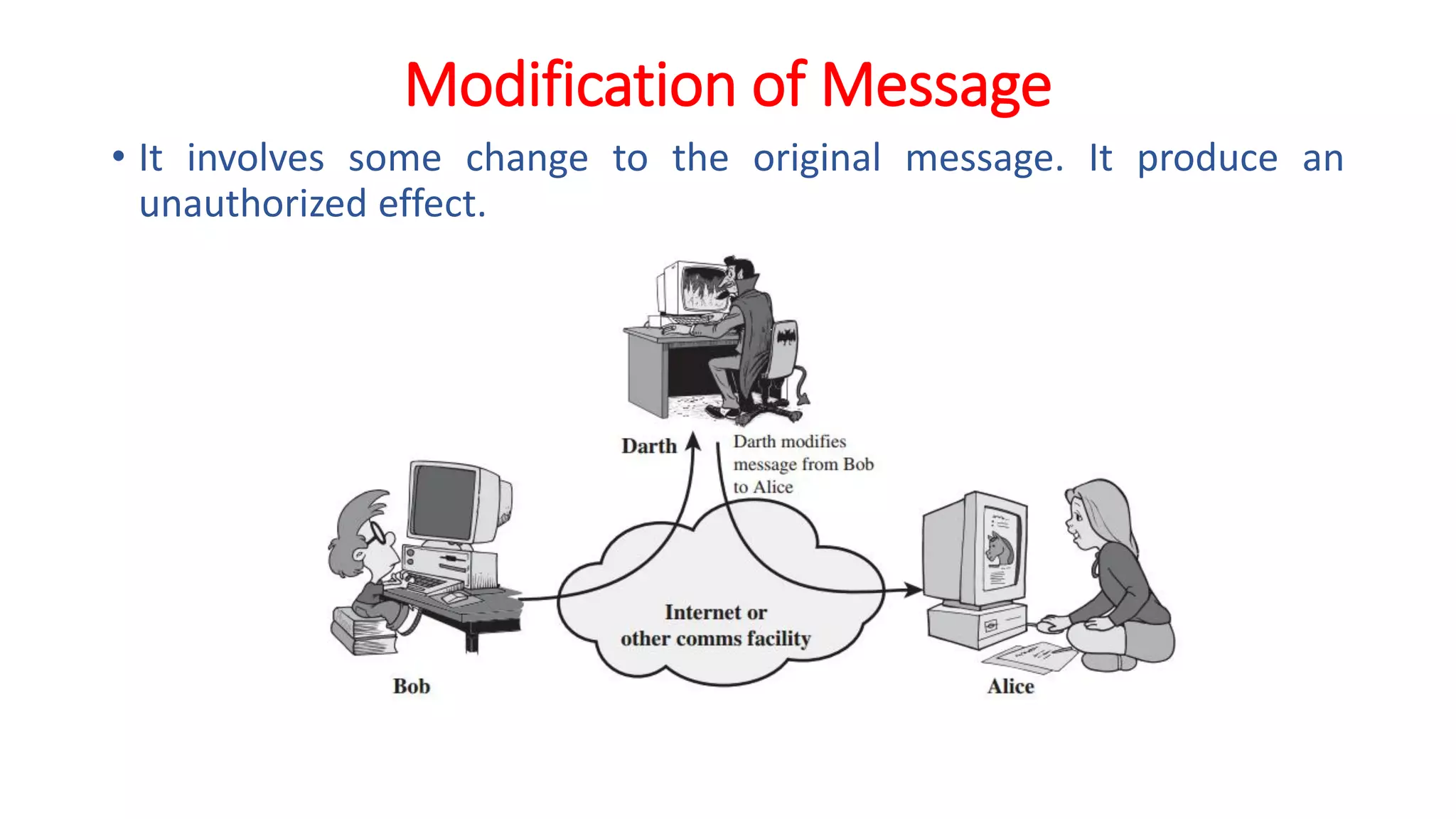
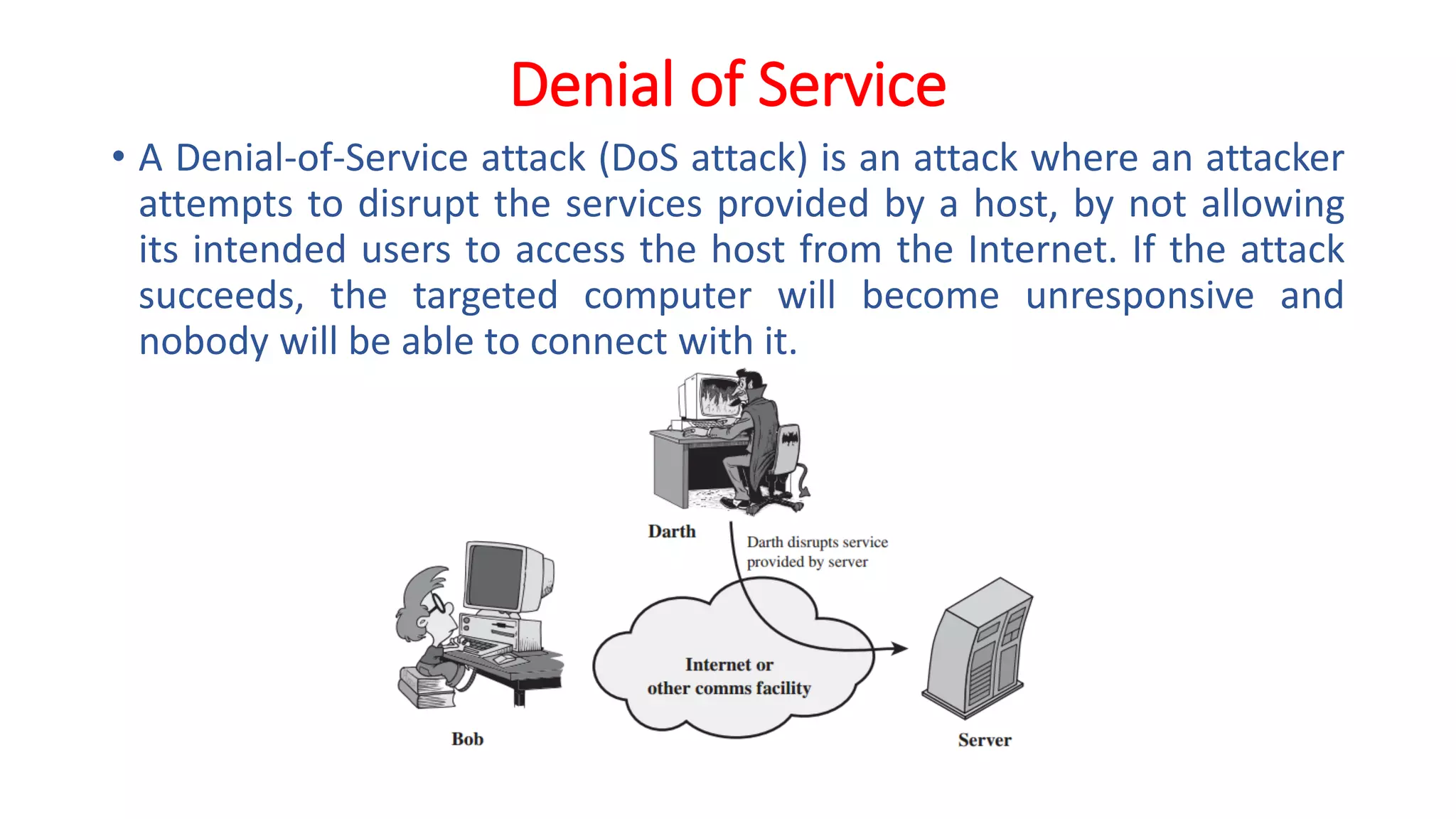
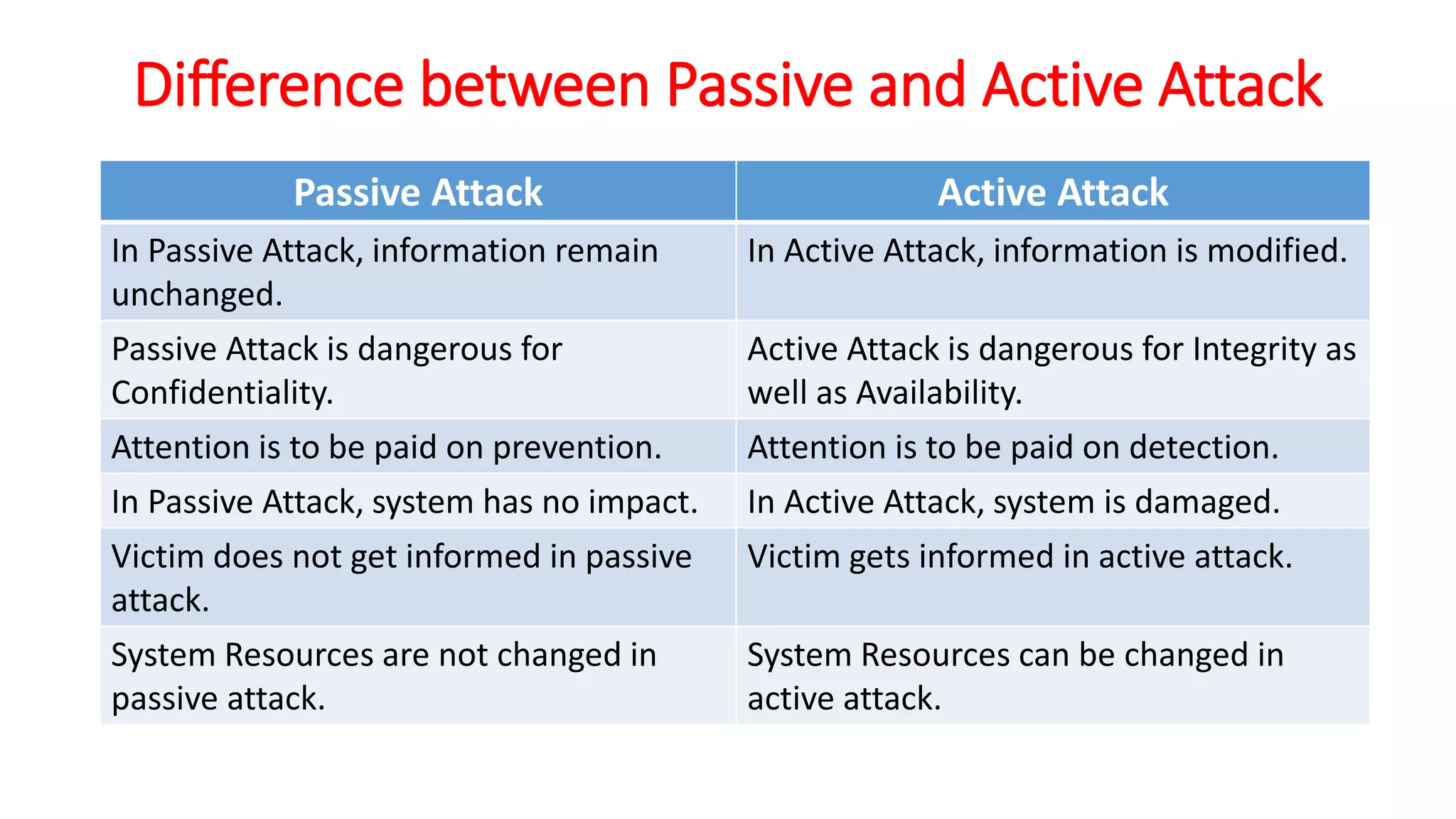
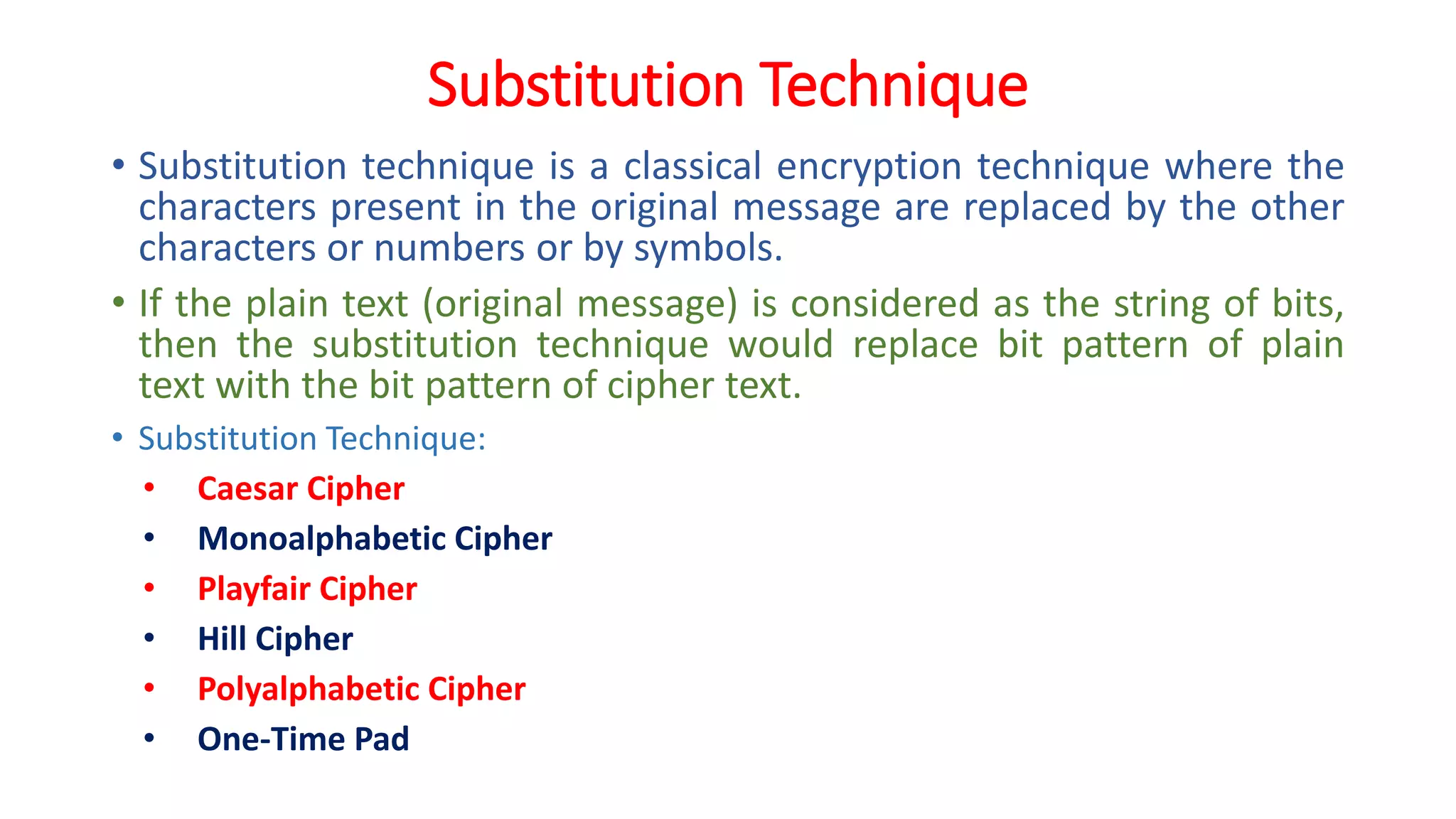
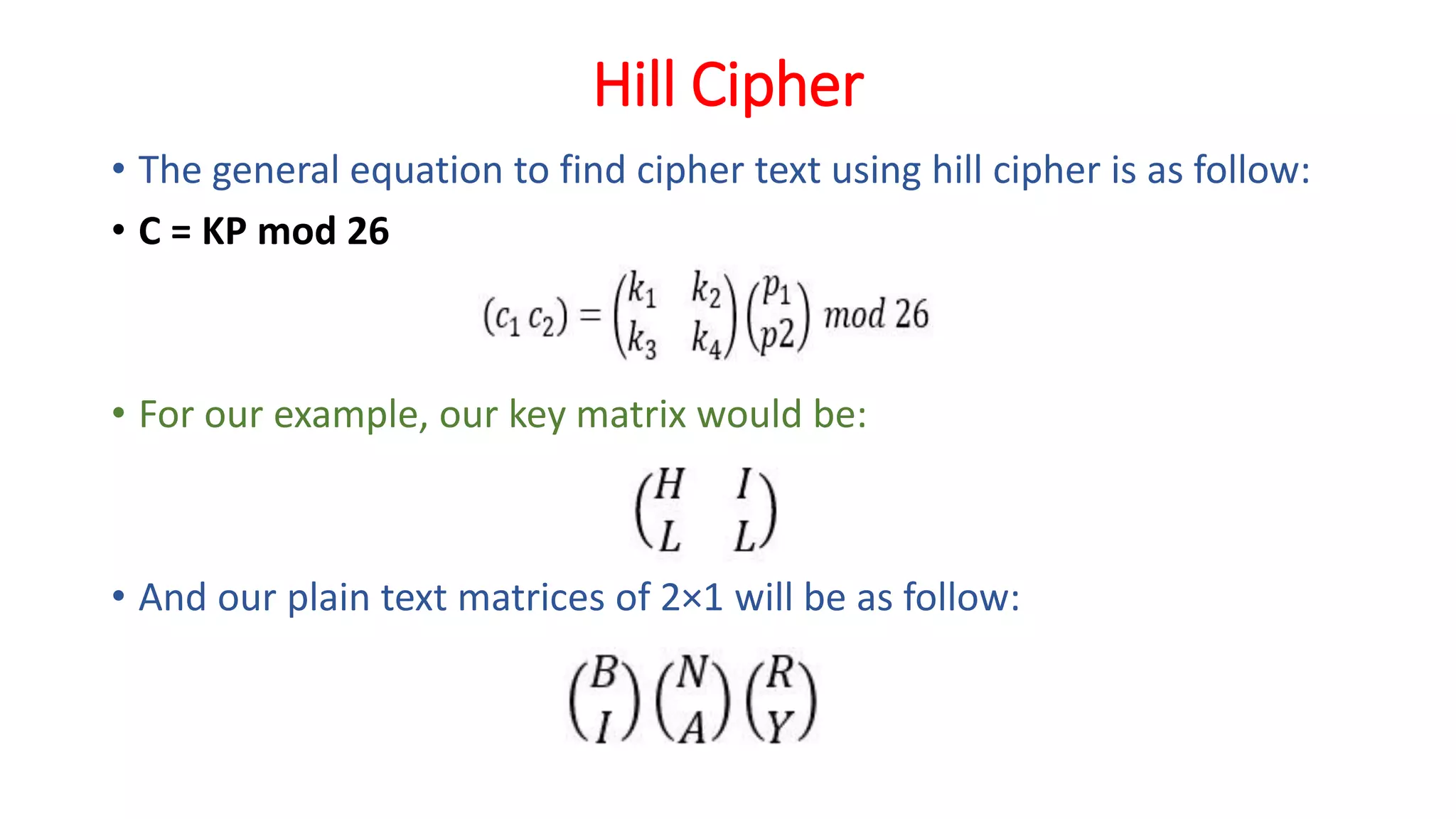
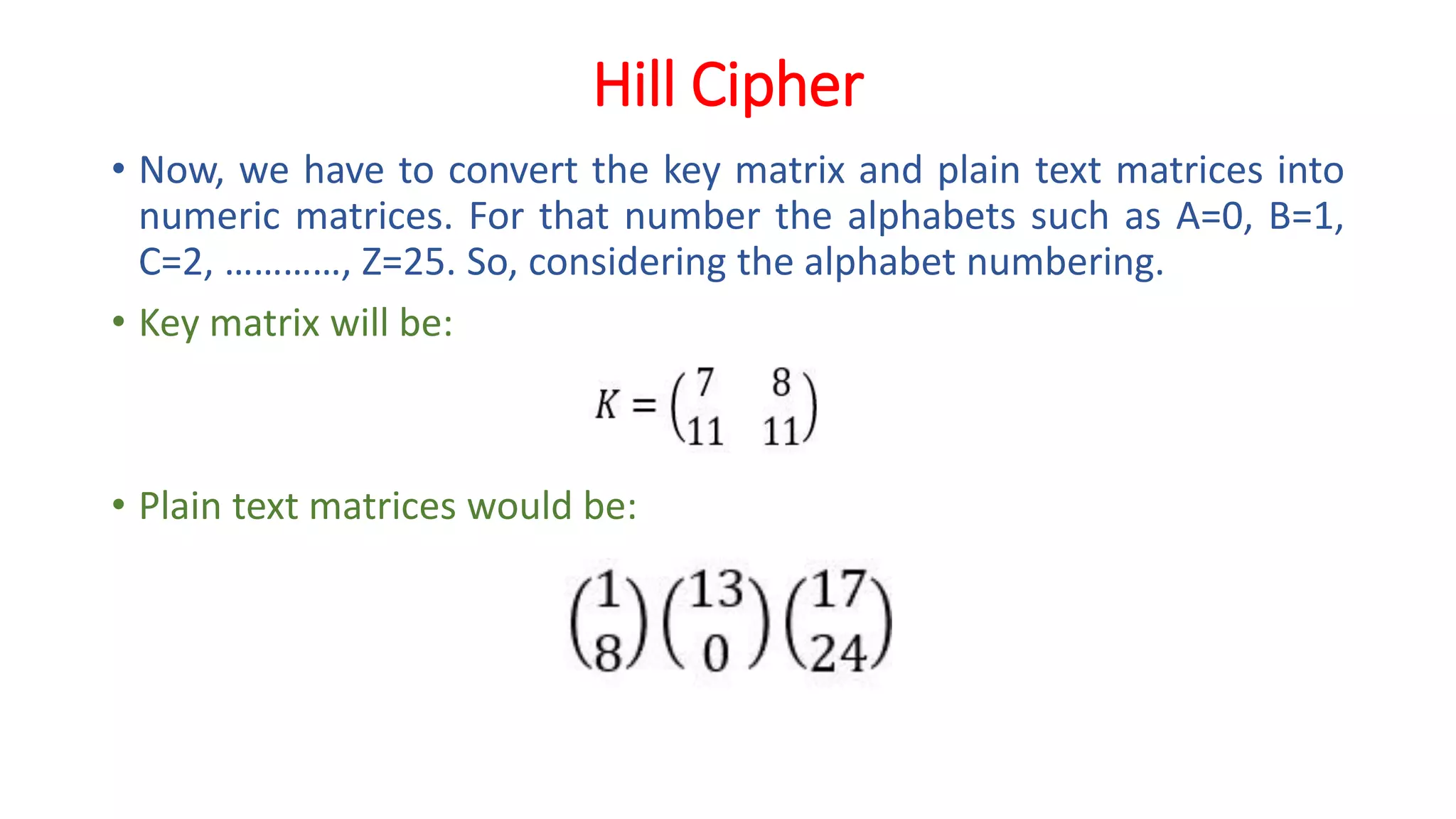
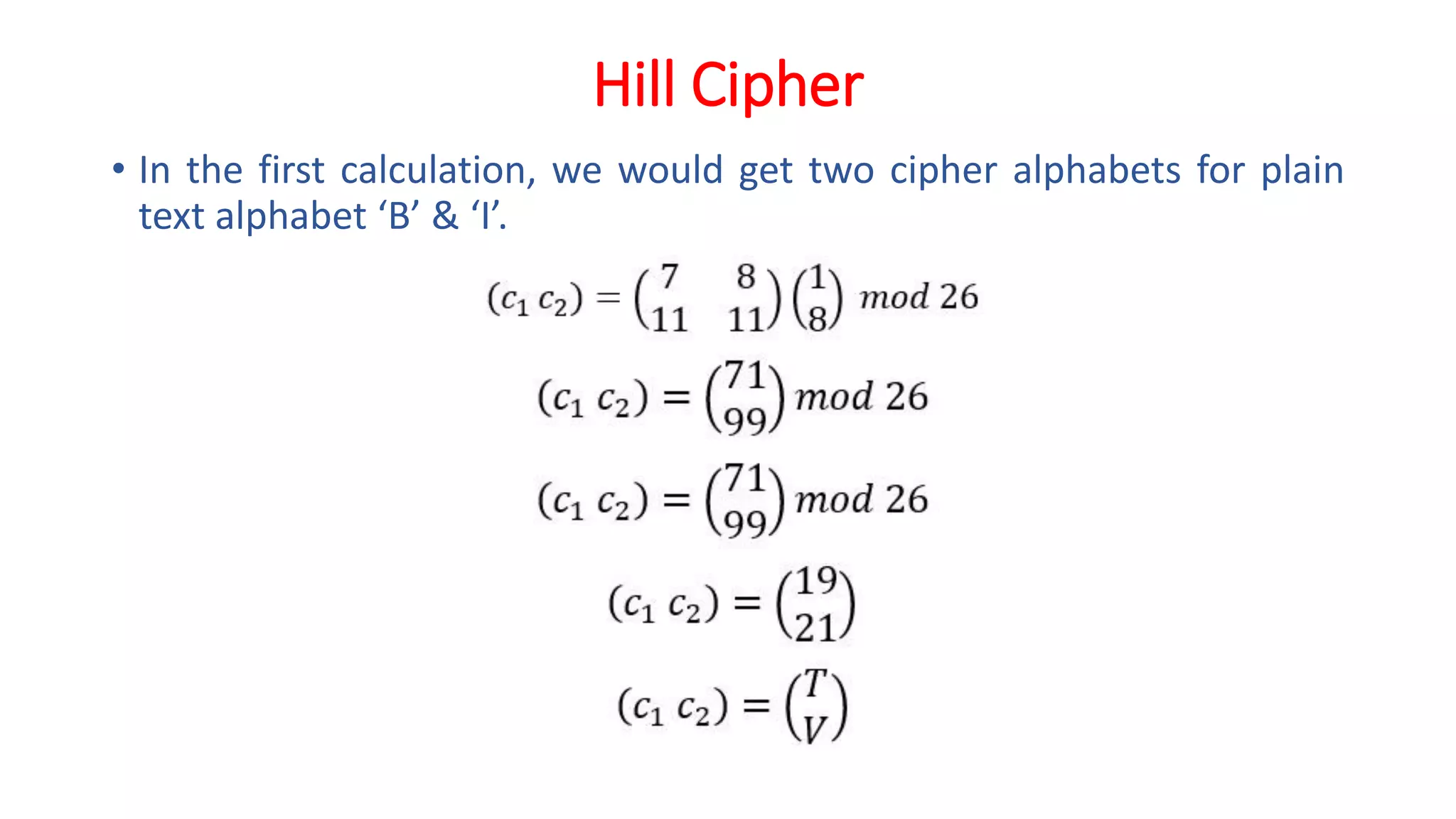
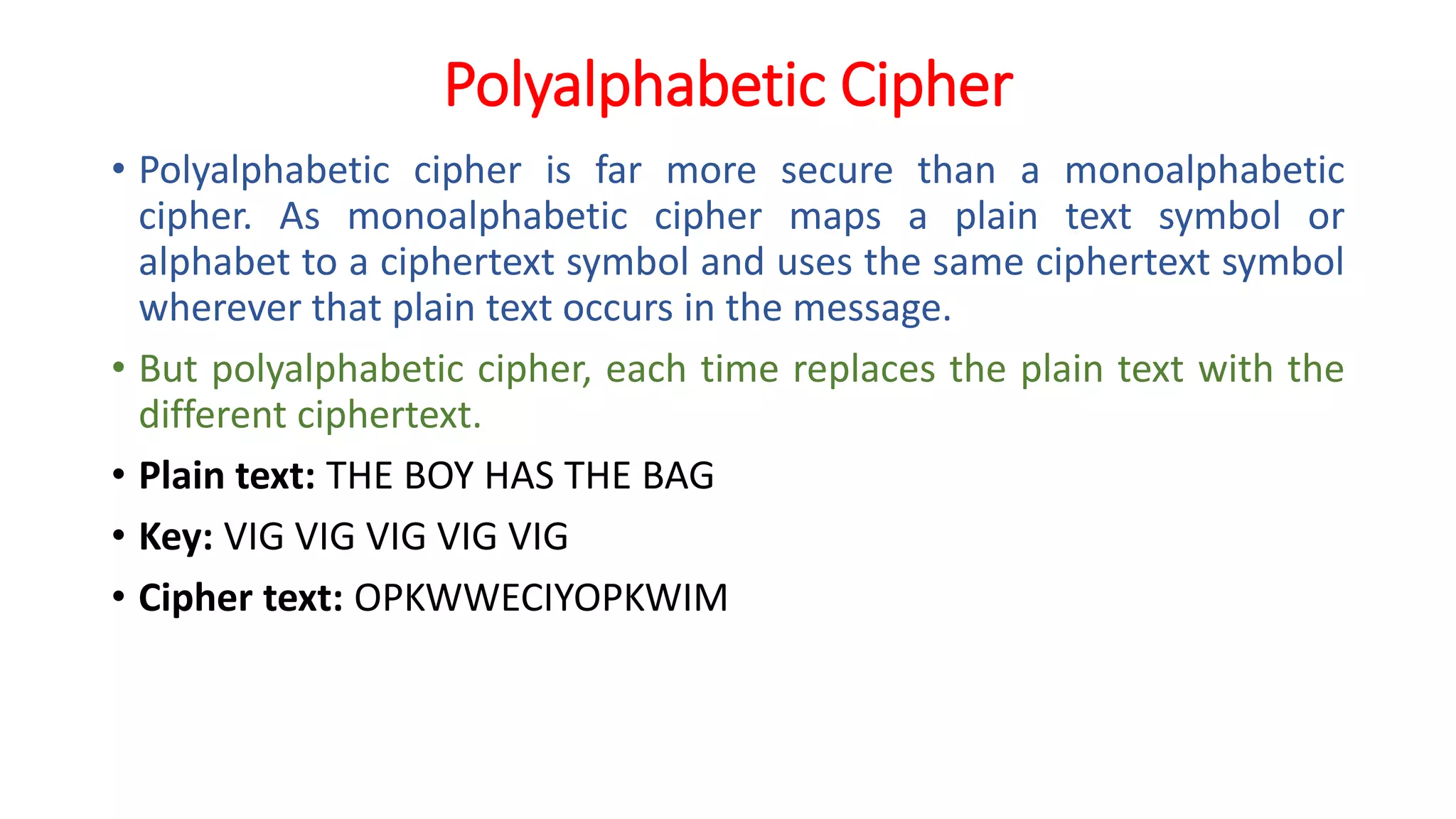
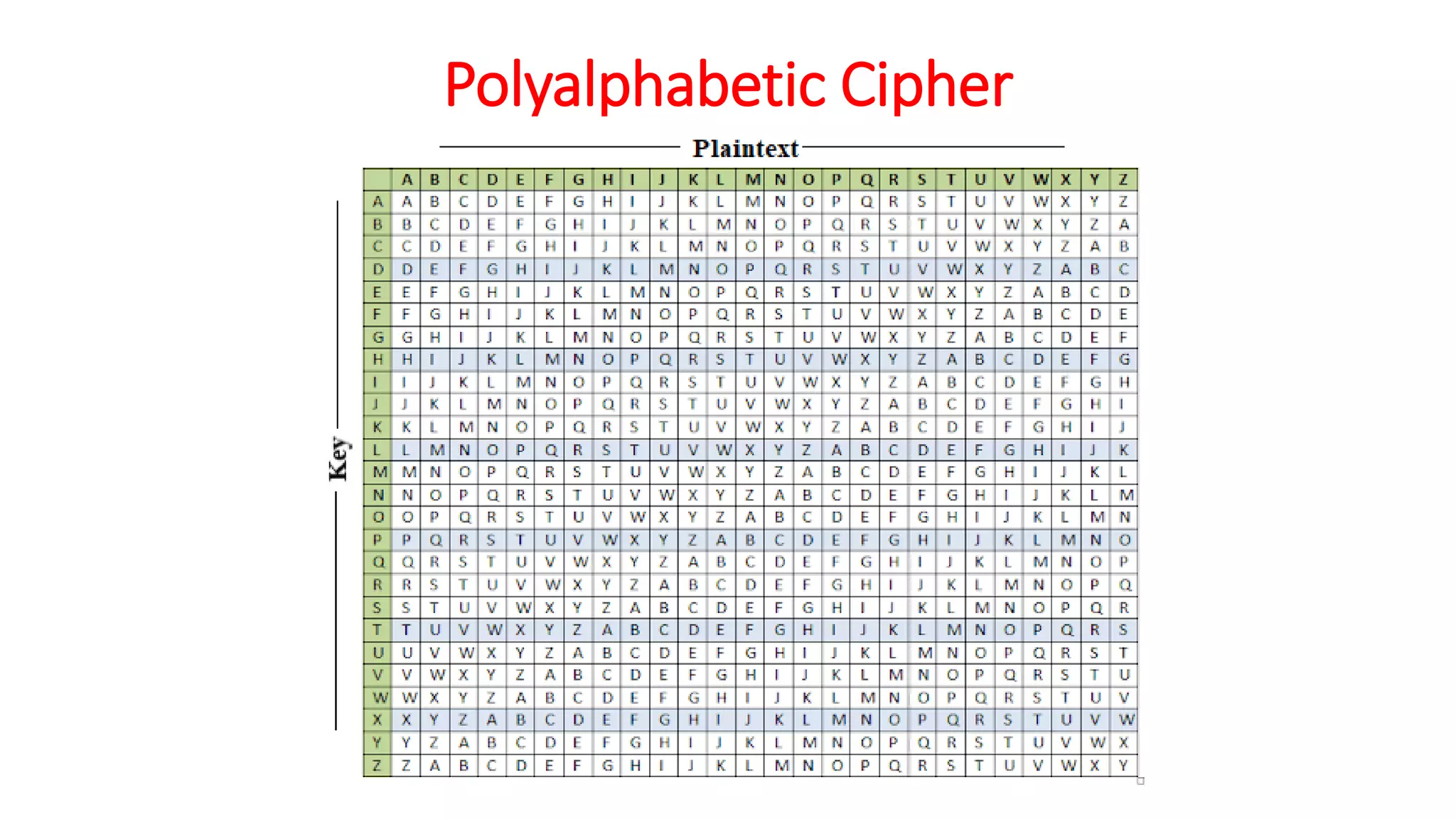
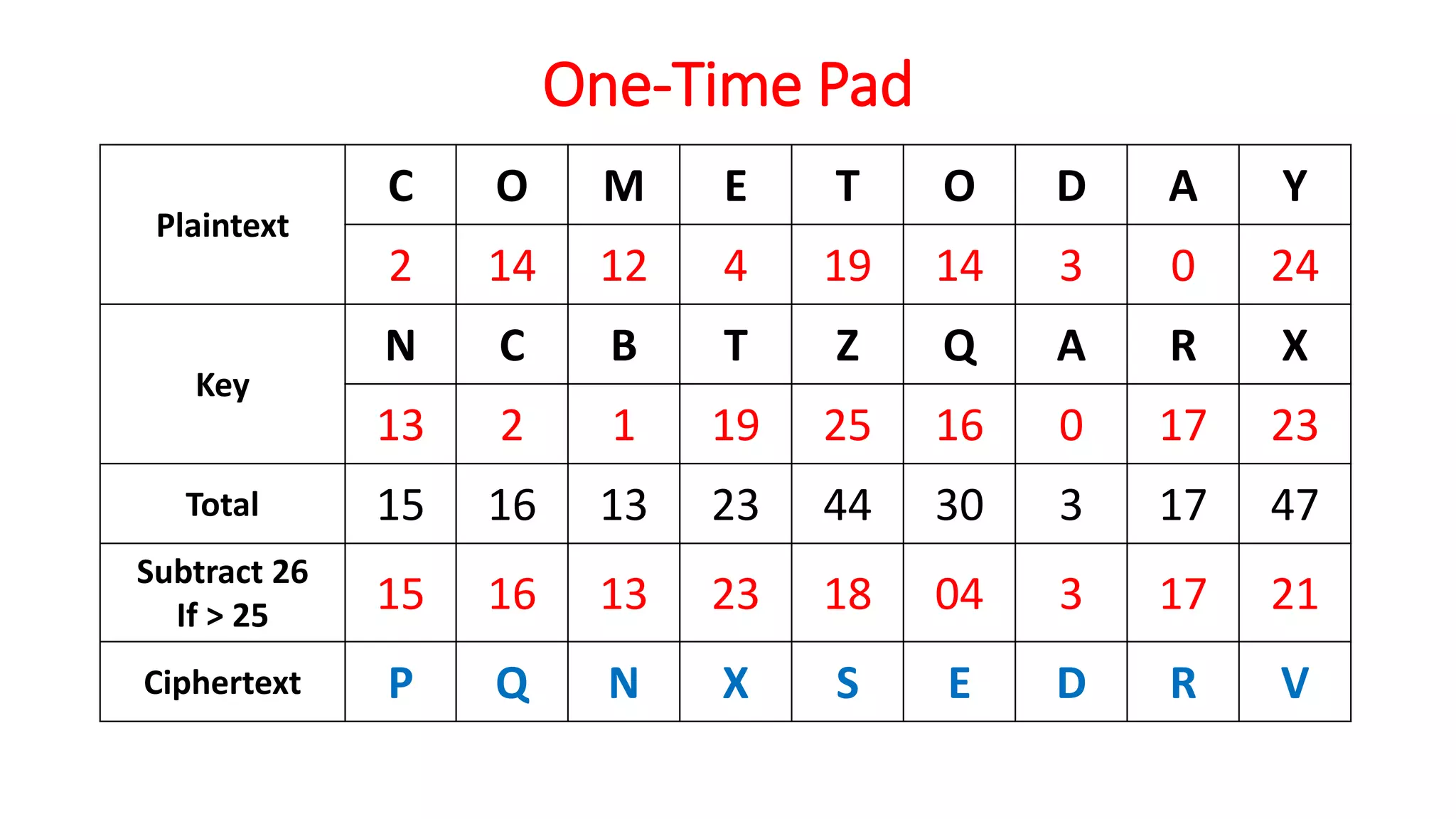
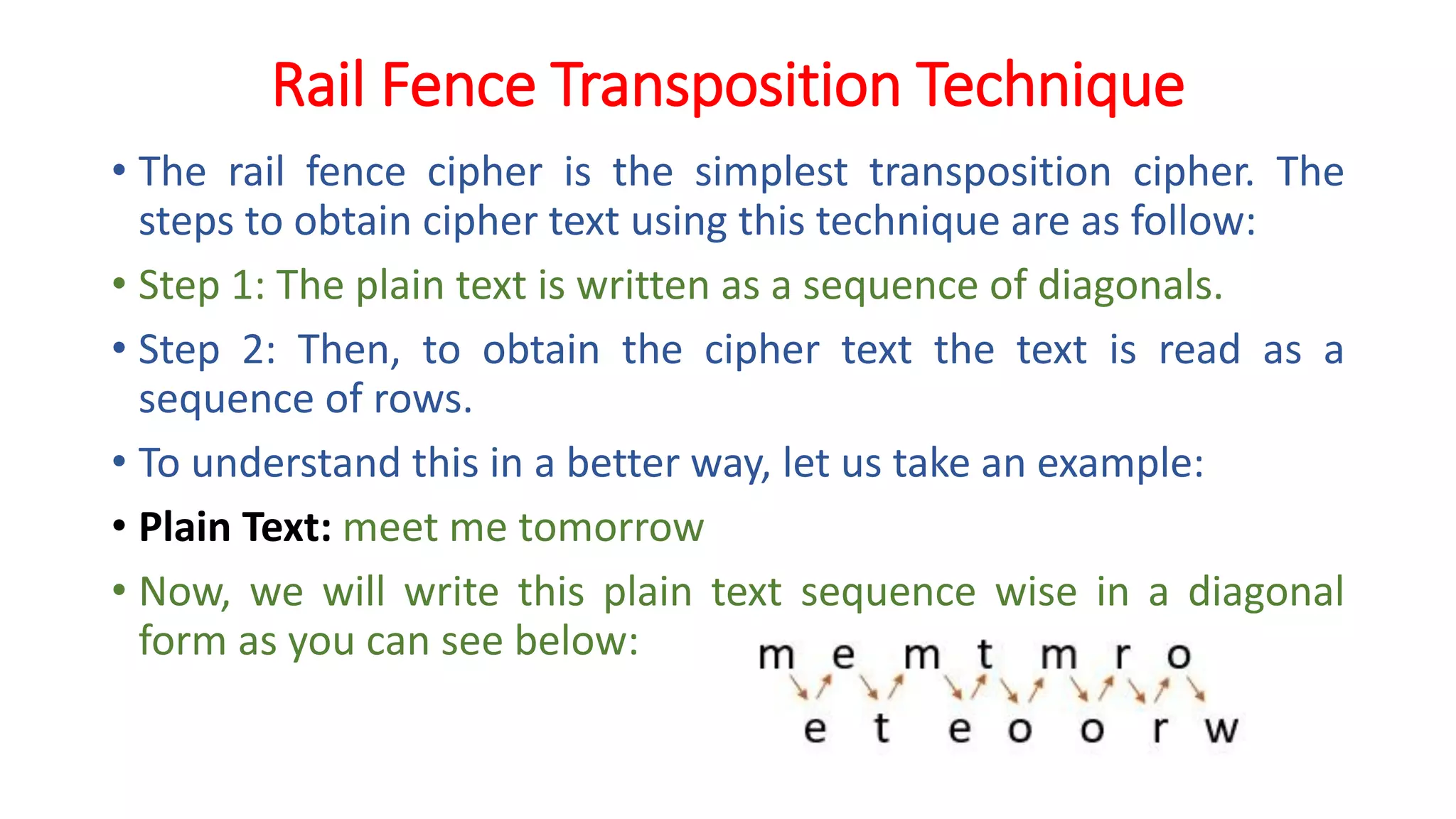
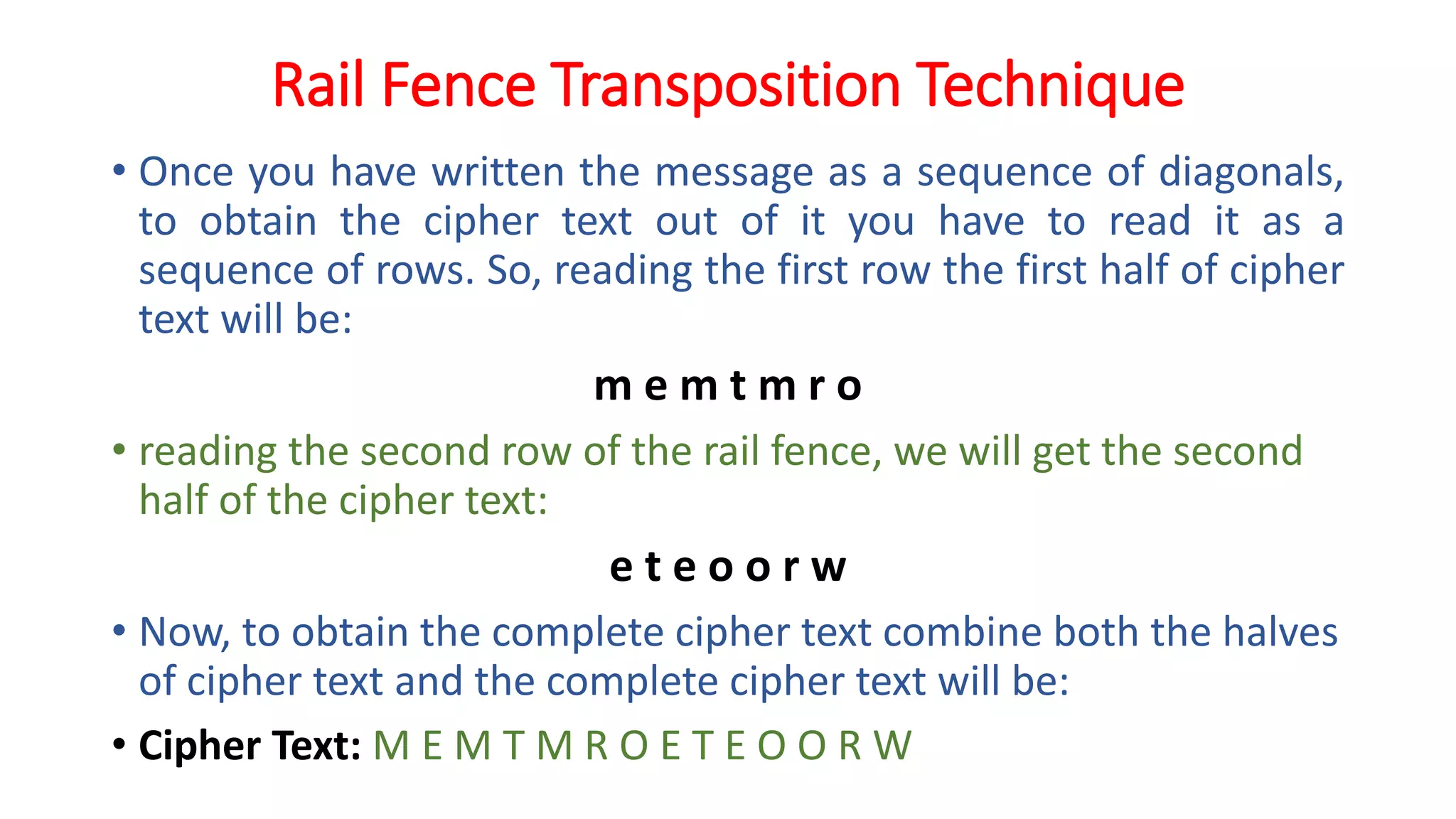
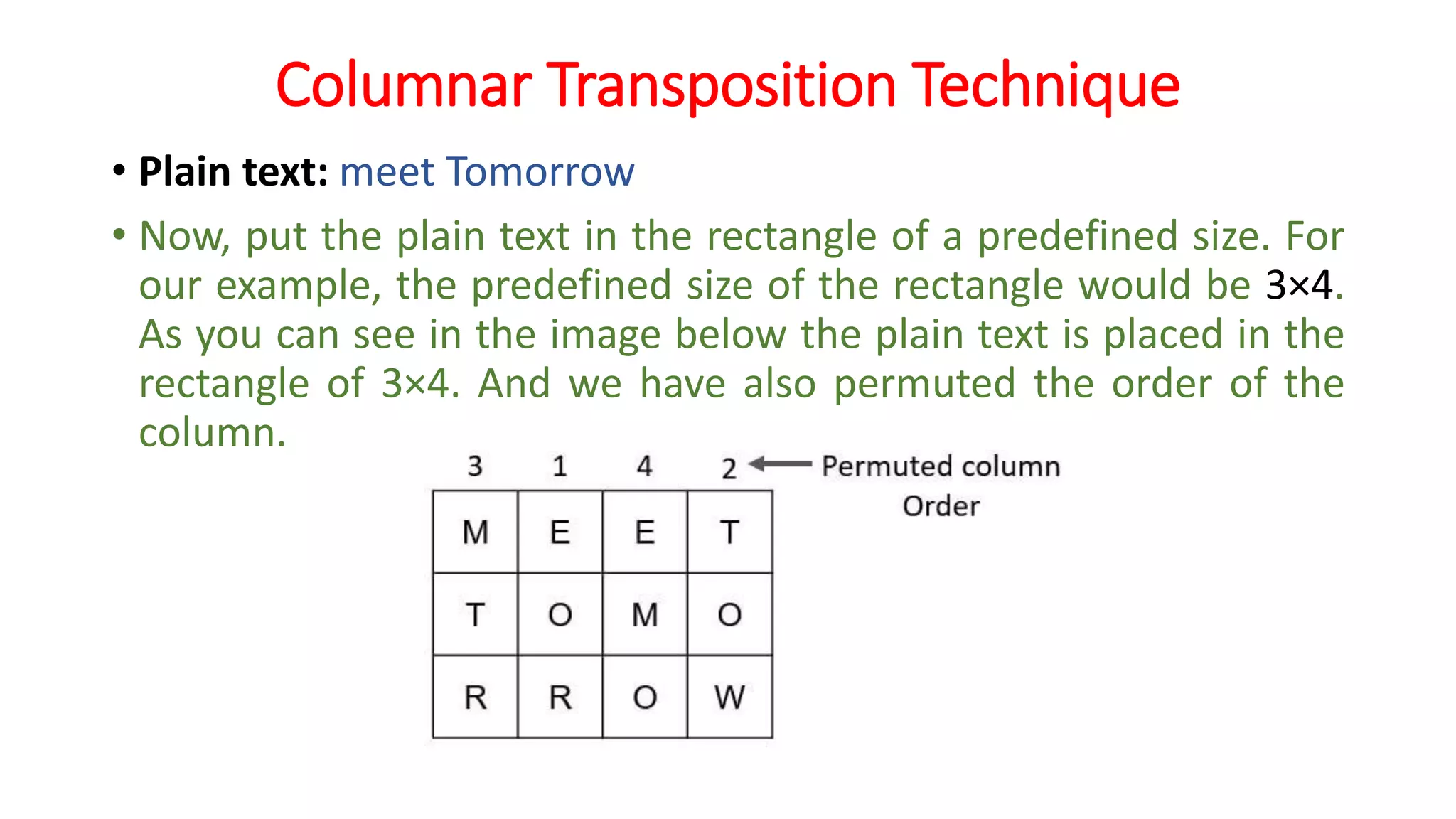
The document provides an extensive overview of cryptography and network security, detailing concepts such as security services, mechanisms, and attacks. It covers the importance of data protection, authentication, access control, confidentiality, integrity, and non-repudiation. Additionally, it explores various techniques for encryption, cryptanalysis, and elaborates on passive and active security attacks.