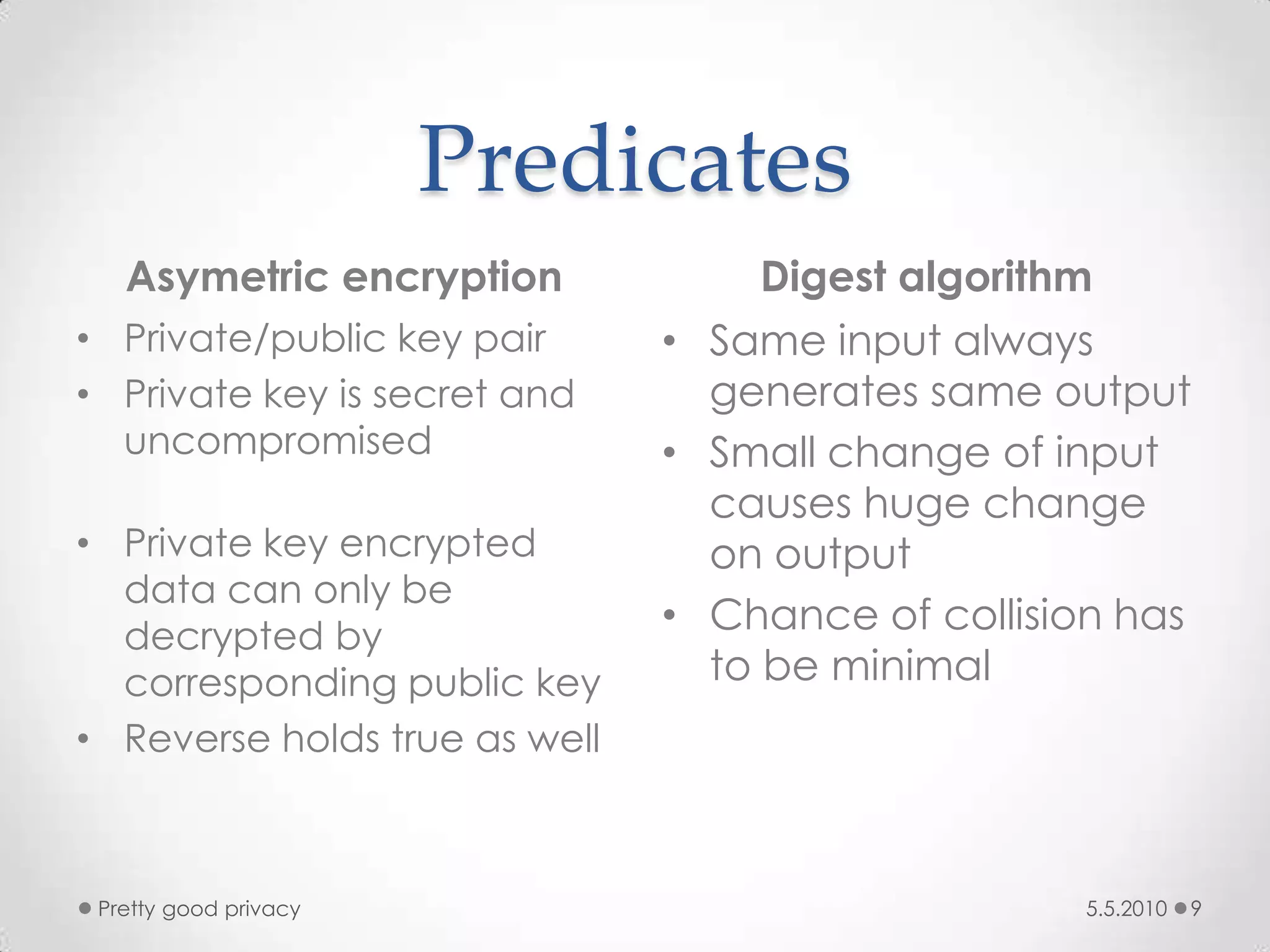
This document discusses the need for email security and introduces Pretty Good Privacy (PGP) as a solution. PGP addresses issues with the SMTP protocol like lack of authentication, encryption, and size limits. It features encryption with public/private key pairs to ensure confidentiality and authentication. PGP also supports compression and segmentation to improve bandwidth and avoid size limits when sending encrypted emails across different platforms.