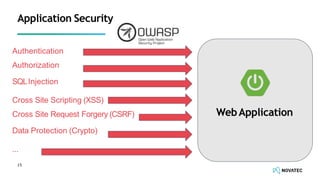
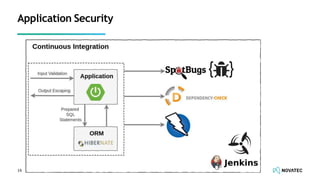
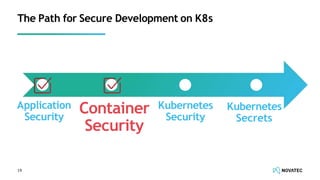
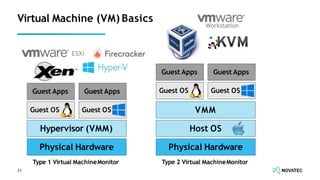
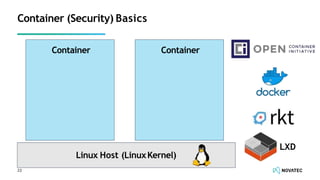
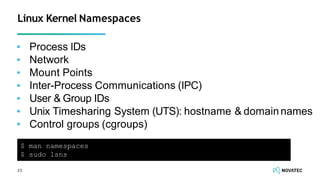
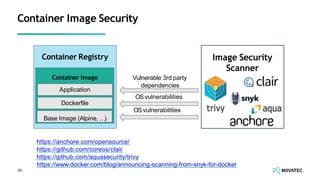
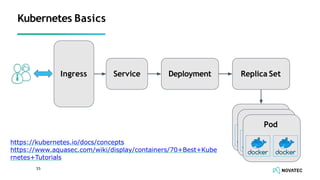
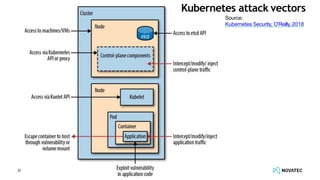
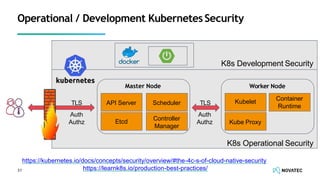
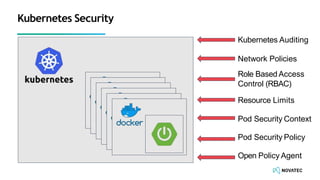
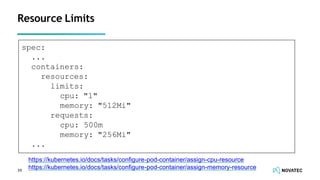
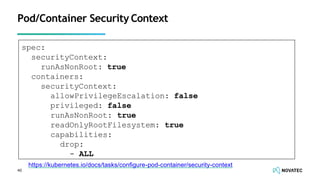
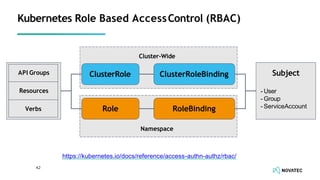
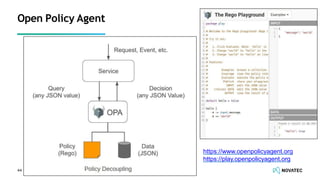
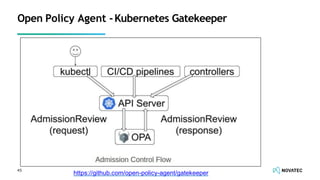
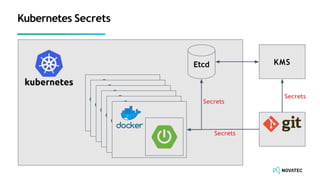
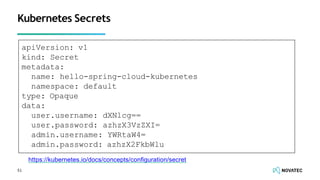
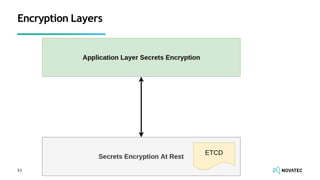
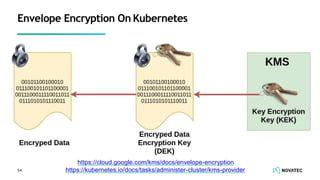
The document is a comprehensive overview of secure development practices in Kubernetes, focusing on application, container, and Kubernetes security, as well as the management of Kubernetes secrets. It outlines various security vulnerabilities, offers best practices for securing applications and containers, and emphasizes the importance of encrypting secrets and avoiding hardcoding sensitive information. Resources and links for further reading and practical demonstrations are provided throughout the document.