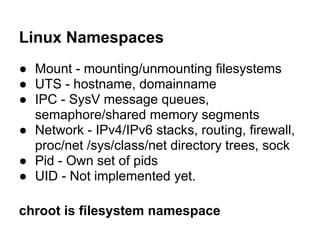
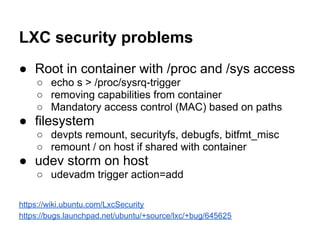
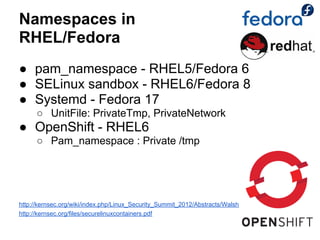
The document discusses the security of Linux containers in cloud environments, focusing on the integration of Linux containers (LXC) with mandatory access control mechanisms. It reviews various security technologies, identifies potential vulnerabilities, and proposes solutions to enhance the security of containerized applications. The presentation also highlights the differences between virtualization and containerization, emphasizing that containers offer lightweight solutions for resource allocation and separation.




![libvirt-lxc = API + LXC + SELinux
● Container virtualization
● Boot “init” binary
● sVirt SELinux TE + MCS
● Firewall ebtables/ip[6]tables
● Host FS passthrough bind mounts
● CGroups resource control
RadHat based distributions
libvirt-sandbox](https://image.slidesharecdn.com/fsec2012-securityoflinuxcontainersinthecloud-120920033632-phpapp02/85/Security-of-Linux-containers-in-the-cloud-10-320.jpg)