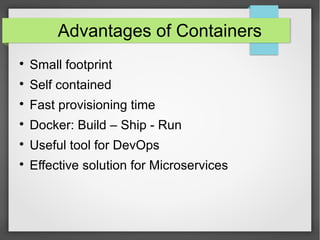
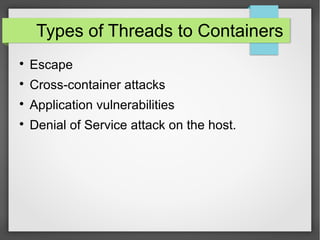
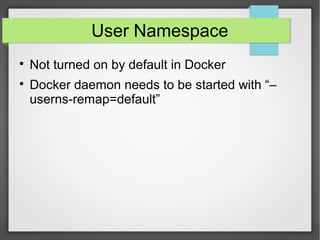
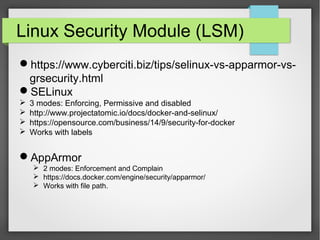
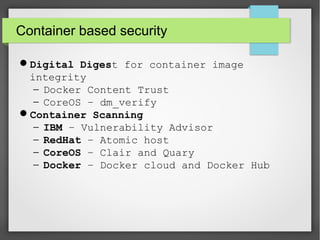
This document discusses container security. It outlines the advantages and disadvantages of containers, including their small footprint, fast provisioning time, and ability to enable effective microservices. However, containers also pose security risks like reduced isolation and potential for cross-container attacks. The document then examines different approaches to container security, including host-based methods using namespaces, control groups, and Linux Security Modules, as well as container-based scanning and third-party security offerings. It provides examples of configuring security controls and evaluating containers for vulnerabilities.