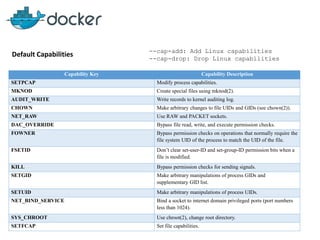
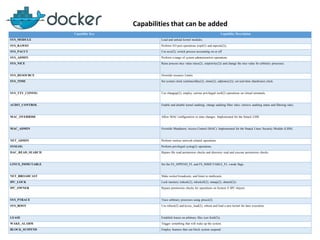
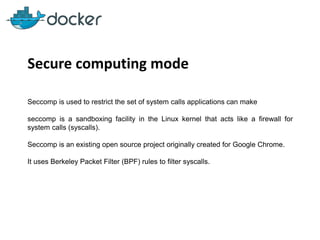
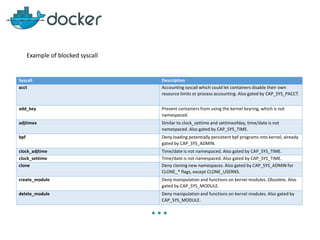
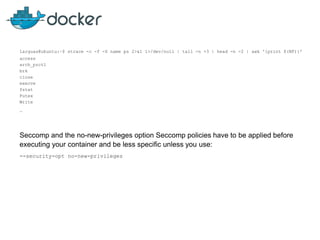
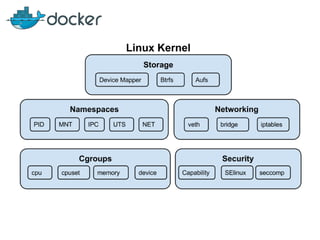
This document discusses security mechanisms in Docker containers, including control groups (cgroups) to limit resources, namespaces to isolate processes, and capabilities to restrict privileges. It covers secure computing modes like seccomp that sandbox system calls. Linux security modules like AppArmor and SELinux are also mentioned, along with best practices for the Docker daemon and container security overall.





![User Namespaces
Docker introduced support for user
namespace in version 1.10
run as user :
--user UID:GID
Need root inside container :
--userns-remap [uid[:gid]]
Docker daemon needs to be started with : --userns-
remap=username/uid:groupname/gid”. Using “default” will create “dockremap” user
(--userns-remap=defaults)](https://image.slidesharecdn.com/dockersecurity-170315112536/85/Docker-Security-Paradigm-12-320.jpg)