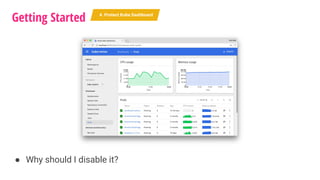
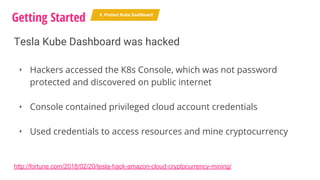
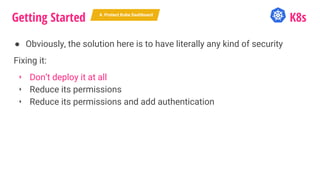
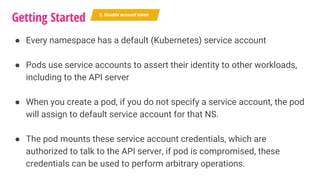
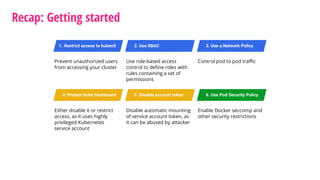
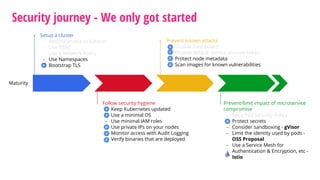
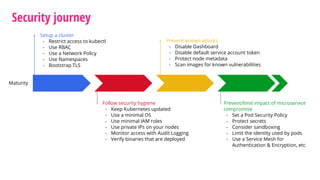
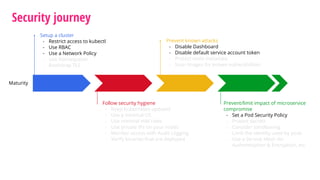
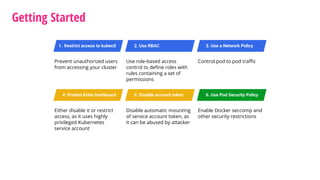
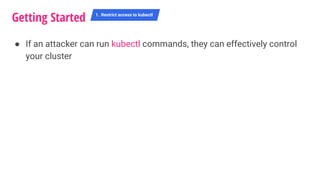
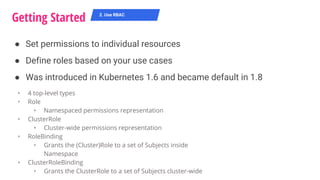
The document outlines a security journey for Kubernetes, highlighting key aspects such as the importance of restricting access, utilizing RBAC for role management, and employing network policies for pod traffic control. It details security measures like protecting the Kubernetes dashboard, disabling service account token auto-mounting, and implementing pod security policies to safeguard containerized applications. Additionally, it provides a recap of best practices to enhance Kubernetes security and prevent unauthorized access.







![Getting Started 1. Restrict access to kubectl
K8s
name: kubernetes-allow-ssh-to-controller-api
type: compute.v1.firewall
properties:
allowed:
- IPProtocol: tcp
ports: ["6443"]
sourceTags: ["ssh-bastion"]
sourceRanges: ["10.10.0.0/16"]
targetTags: ["k8s-controller"]
network: global/networks/default
● Enforce Bastion model via Firewall
● In GCP, Firewall definition would look something like this:](https://image.slidesharecdn.com/k8s-securityjourney-180829053612/85/Kubernetes-Security-Journey-17-320.jpg)

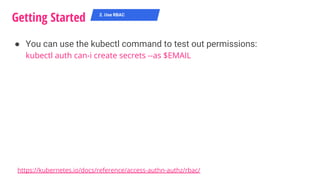
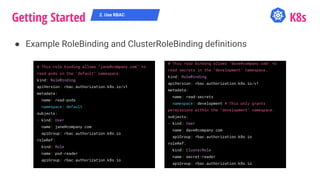
![Getting Started K8s
● Enable it on creation time with flag --authorization-mode=RBAC
● Example Role and ClusterRole definitions
● As of 1.9 you can also create ClusterRoles by aggregating roles
together using aggregationRule
2. Use RBAC
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-reader
rules:
- apiGroups: [""] # "" indicates the core API group
resources: ["pods", "pods/logs"]
verbs: ["get", "watch", "list"]
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
# "namespace" omitted since ClusterRoles are not
namespaced
name: secret-reader
rules:
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get", "watch", "list"]](https://image.slidesharecdn.com/k8s-securityjourney-180829053612/85/Kubernetes-Security-Journey-21-320.jpg)

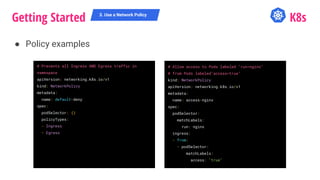
![@QVIK
# Allow DNS inside the cluster for all namespaces by default
$ kubectl --context $CONTEXT label namespace kube-system name=kube-system
$ for ns in "${NAMESPACES[@]}"; do
kubectl --context $CONTEXT --namespace $ns apply -f - <<EOF
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-dns-access
spec:
podSelector:
matchLabels: {}
policyTypes:
- Egress
egress:
- to:
- namespaceSelector:
matchLabels:
name: kube-system
ports:
- protocol: UDP
port: 53
EOF
done](https://image.slidesharecdn.com/k8s-securityjourney-180829053612/85/Kubernetes-Security-Journey-26-320.jpg)