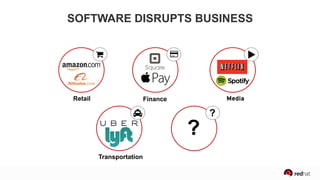
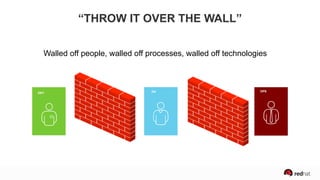
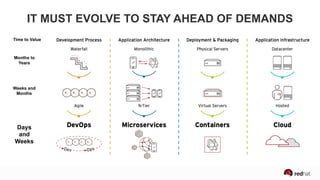
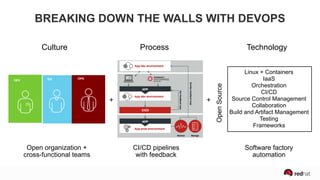
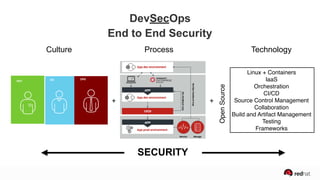
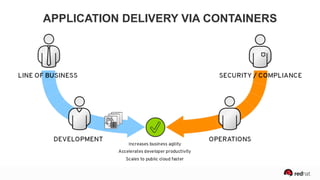
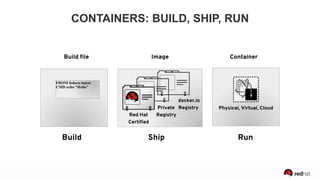
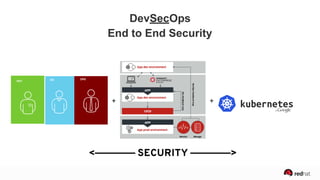
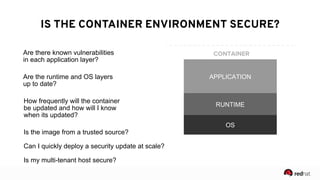
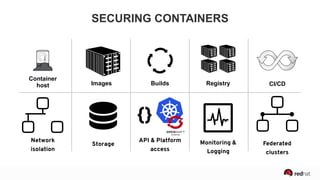
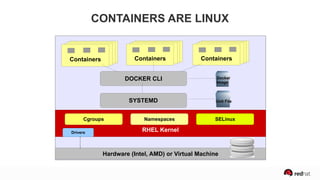
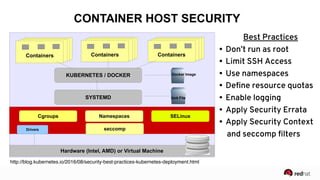
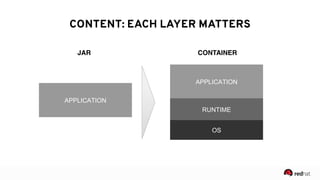
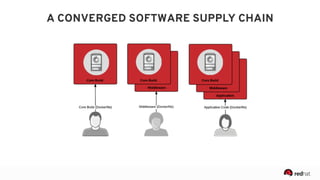
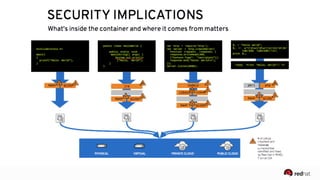
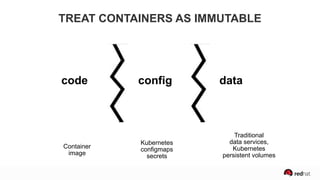
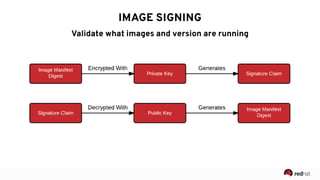
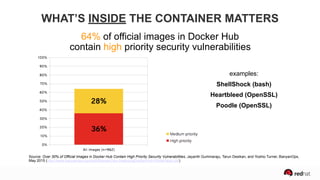
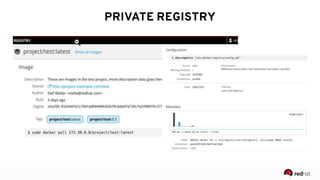
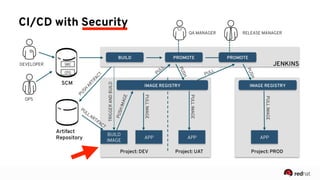
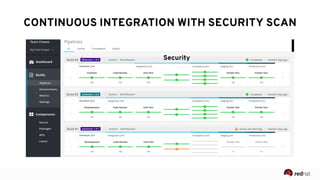
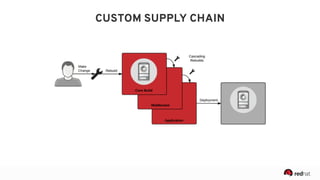
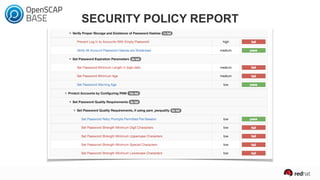
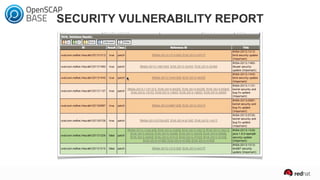
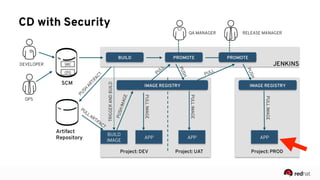
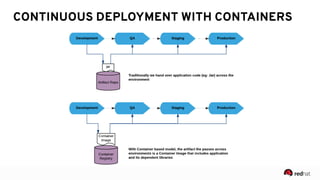
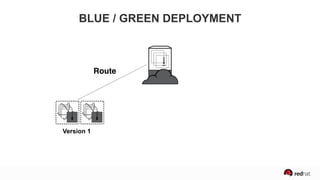
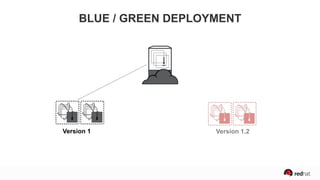
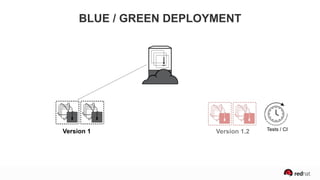
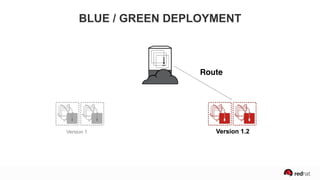
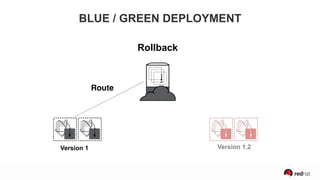
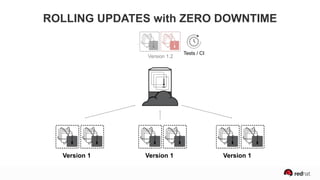
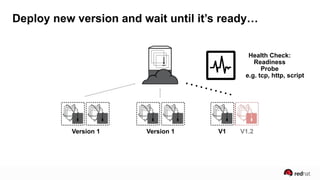
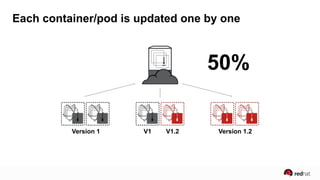
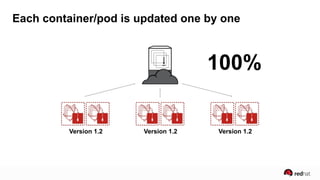
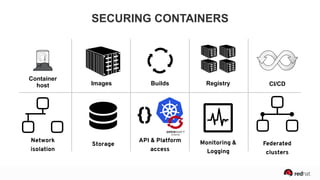
The presentation discusses the integration of security into DevOps practices, emphasizing the importance of DevSecOps and container security. It highlights challenges such as treating security as an afterthought, and outlines best practices for securing containerized applications, including continuous integration and deployment strategies. Additional focus is given to compliance, vulnerability scanning, and the need for collaboration across teams to ensure comprehensive security in software delivery.