The document outlines the history and development of container technology in Unix systems, starting from the chroot technology of the 1980s to the creation of Docker in 2013. It explains the differences between virtual machines and containers, their various types, and their underlying Linux containment features such as namespaces and cgroups. Furthermore, it introduces tools for managing containers, including LXC and LXD, and discusses use cases and commands for initiating and managing container lifecycles.






















![Initialize
$ l x d i n i t
Would you l i k e to use LXD c l u s t e r i n g ? ( yes / no ) [ d e f a u l t =no ] : no
Do you want to c o n f i g u r e a new storage pool ? ( yes / no ) [ d e f a u l t = yes ] : yes
Name of the new storage pool [ d e f a u l t = d e f a u l t ] : mystorage
Would you l i k e to connect to a MAAS s e r v e r ? ( yes / no ) [ d e f a u l t =no ] : no
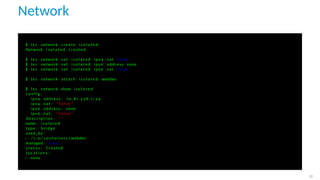
Would you l i k e to create a new l o c a l network bridge ? ( yes / no ) [ d e f a u l t = yes ] : yes
What should the new bridge be c a l l e d ? [ d e f a u l t = lxdbr0 ] : l x d l o c a l
What IPv4 address should be used ? ( CIDR subnet notation , " auto " or " none " )
[ d e f a u l t = auto ] : auto
What IPv6 address should be used ? ( CIDR subnet notation , " auto " or " none " )
[ d e f a u l t = auto ] : none
Would you l i k e LXD to be a v a i l a b l e over the network ? ( yes / no ) [ d e f a u l t =no ] : no
Would you l i k e s t a l e cached images to be updated a u t o m a t i c a l l y ? ( yes / no )
[ d e f a u l t = yes ] no
Would you l i k e a YAML " l x d i n i t " preseed to be p r i n t e d ? ( yes / no )
[ d e f a u l t =no ] : yes
23](https://image.slidesharecdn.com/containertausig-200528084327/85/SBA-Live-Academy-Secure-Containers-for-Developer-by-Mathias-Tausig-24-320.jpg)
![BTRFS storage
$ l x c storage create mybtrfs b t r f s source =/ dev / loop0
Storage pool mybtrfs created
$ df −h
F i l e s y s t e m S i z e Used A v a i l Use% Mounted on
udev 7 ,8G 0 7 ,8G 0% / dev
tmpfs 1 ,6G 2 ,0M 1 ,6G 1% / run
/ dev / sda2 1 1 7G 1 1 G 100G 10% /
[ . . . ]
/ dev / loop0 30G 17M 28G 1% / var / l i b / l x d / storage−pools / mybtrfs
$ l x c storage show mybtrfs
c o n f i g :
source : 031 d08f0−ed03−4f39 −8274−03fc4a12688c
v o l a t i l e . i n i t i a l _ s o u r c e : / dev / loop0
d e s c r i p t i o n : " "
name : mybtrfs
d r i v e r : b t r f s
used_by : [ ]
s t a t u s : Created
l o c a t i o n s :
− none
27](https://image.slidesharecdn.com/containertausig-200528084327/85/SBA-Live-Academy-Secure-Containers-for-Developer-by-Mathias-Tausig-28-320.jpg)
![Profile
$ l x c p r o f i l e create myprof
$ cat lxd−p r o f i l e −myprof . yaml
c o n f i g :
user . vendor−data : |
# cloud−c o n f i g
users :
− name : ubuntu
ssh_authorized_keys :
− ssh−ed25519 AAAAC3Nza [ . . . ] oJmMZ7Y5YlrYA mat@office
s h e l l : / bin / bash
d e s c r i p t i o n : My brandnew LXD p r o f i l e
devices :
eth0 :
name : eth0
n i c t y p e : bridged
parent : l x d l o c a l
type : n i c
root :
path : /
pool : mybtrfs
type : d i s k
s i z e : 10GB
name : myprofile
$ l x c p r o f i l e e d i t myprof < lxd−p r o f i l e −myprof . yaml
28](https://image.slidesharecdn.com/containertausig-200528084327/85/SBA-Live-Academy-Secure-Containers-for-Developer-by-Mathias-Tausig-29-320.jpg)
![Profile
$ l x c launch ubuntu : 1 8 . 0 4 web −−p r o f i l e myprof
$ l x c p r o f i l e show myprof
c o n f i g :
user . vendor−data : |
# cloud−c o n f i g
users :
− name : ubuntu
ssh_authorized_keys :
− ssh−ed25519 AAAAC3Nza [ . . . ] oJmMZ7Y5YlrYA mat@office
s h e l l : / bin / bash
group : sudo
d e s c r i p t i o n : My brandnew LXD p r o f i l e
devices :
eth0 :
name : eth0
n i c t y p e : bridged
parent : l x d l o c a l
type : n i c
root :
path : /
pool : mybtrfs
s i z e : 10GB
type : d i s k
name : myprof
used_by : [ web ]
29](https://image.slidesharecdn.com/containertausig-200528084327/85/SBA-Live-Academy-Secure-Containers-for-Developer-by-Mathias-Tausig-30-320.jpg)
![Shared Disk
$ l x c c o n f i g device add t e s t s r c d i r d i s k path =/home/ ubuntu / s r c source =/home/my/ s r c
Device s r c d i r added to shared
$ ssh ubuntu@10 . 4 5 . 2 3 8 . 1 6 7
ubuntu@shared : ~$ mount
/ dev /dm−5 on / type b t r f s ( rw , relatime , ssd , [ . . . ] )
none on / dev type tmpfs ( rw , relatime , s i z e =492k , mode=755 , uid =165536 , gid =165536)
. . .
/ dev / mapper /myvg−home on /home/ ubuntu / s r c type ext4 ( rw , relatime , data = ordered )
. . .
ubuntu@shared : ~$ df
F i l e s y s t e m 1 K−blocks Used A v a i l a b l e Use% Mounted on
/ dev /dm−5 36700160 21135324 14910740 59% /
none 492 0 492 0% / dev
udev 3898488 0 3898488 0% / dev / t t y
tmpfs 100 0 100 0% / dev / l x d
tmpfs 100 0 100 0% / dev / . lxd−mounts
tmpfs 3930688 0 3930688 0% / dev /shm
tmpfs 3930688 172 3930516 1% / run
tmpfs 5120 0 5120 0% / run / l o c k
tmpfs 3930688 0 3930688 0% / sys / f s / cgroup
/ dev / mapper /myvg−home 95593892 85171544 5523328 94% /home/ ubuntu / s r c
tmpfs 786136 0 786136 0% / run / user /1000
30](https://image.slidesharecdn.com/containertausig-200528084327/85/SBA-Live-Academy-Secure-Containers-for-Developer-by-Mathias-Tausig-31-320.jpg)
![Privileged containers
$ l x c c o n f i g set webdev s e c u r i t y . p r i v i l e g e d true
$ l x c c o n f i g show webdev
a r c h i t e c t u r e : x86_64
c o n f i g :
image . a r c h i t e c t u r e : amd64
image . d e s c r i p t i o n : ubuntu 18.04 LTS amd64 ( r e l e a s e ) ( 2 0 1 9 0 8 1 3 . 1 )
[ . . . ]
s e c u r i t y . p r i v i l e g e d : " true "
[ . . . ]
v o l a t i l e . i s o l a t e d . hwaddr : 00:16:3 e :4 f : 4 7 : 1 5
v o l a t i l e . i s o l a t e d . name : eth1
v o l a t i l e . l a s t _ s t a t e . idmap : ’ [ { " I s u i d " : true , " I s g i d " : f a l s e , " Hostid " : 1 6 5 5 3 6 , [ . . . ] } ] ’
v o l a t i l e . l a s t _ s t a t e . power : RUNNING
devices :
i s o l a t e d :
n i c t y p e : bridged
parent : i s o l a t e d
type : n i c
ephemeral : f a l s e
p r o f i l e s :
− d e f a u l t
s t a t e f u l : f a l s e
d e s c r i p t i o n : " "
32](https://image.slidesharecdn.com/containertausig-200528084327/85/SBA-Live-Academy-Secure-Containers-for-Developer-by-Mathias-Tausig-33-320.jpg)
![Privileged containers
$ l x c c o n f i g set webdev s e c u r i t y . p r i v i l e g e d true
$ l x c r e s t a r t webdev
$ l x c s h e l l webdev
root@webdev : ~# t a i l −f / var / log / s y s l o g &
Oct 1 1 16:30:30 webdev systemd [ 1 ] : Stopped t a r g e t Login Prompts .
[ . . . ]
root@webdev : ~# logout
$ ps aux | grep " t a i l −f "
root 19655 [ . . . ] 18:30 0:00 t a i l −f / var / log / s y s l o g
$ l x c c o n f i g set webdev s e c u r i t y . p r i v i l e g e d f a l s e
$ l x c r e s t a r t webdev
$ l x c s h e l l webdev
root@webdev : ~# t a i l −f / var / log / s y s l o g &
Oct 1 1 1 6 : 3 1 : 0 4 g i t o l i t e systemd [ 1 ] : S t a r t e d User Manager f o r UID 0.
[ . . . ]
root@webdev : ~# logout
$ ps aux | grep " t a i l −f "
165536 2 0 9 3 8 [ . . . ] 1 8 : 3 1 0:00 t a i l −f / var / log / s y s l o g
33](https://image.slidesharecdn.com/containertausig-200528084327/85/SBA-Live-Academy-Secure-Containers-for-Developer-by-Mathias-Tausig-34-320.jpg)

