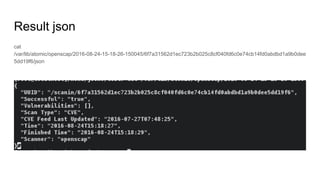
This document provides an overview of OpenSCAP, an open-source security compliance solution that implements the Security Content Automation Protocol (SCAP). It details the importance of continuous security compliance and vulnerability assessment, particularly for Docker images/containers. The presentation also discusses integration with Red Hat products, demo examples, and the advantages and limitations of using OpenSCAP.










![Result report is created but some error messages..
[root@localhost]/home/jooho/test# oscap-docker image docker.io/rhel7 xccdf eval --report result.html
--profile standard /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml
WARNING: Skipping http://www.redhat.com/security/data/oval/Red_Hat_Enterprise_Linux_7.xml file
which is referenced from XCCDF content
Command: oscap xccdf eval --report result.html --profile standard
/usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml failed!
Error was:
Command '['oscap', 'xccdf', 'eval', '--report', 'result.html', '--profile', 'standard',
'/usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml']' returned non-zero exit status 2](https://image.slidesharecdn.com/openscap2-160927015608/85/OpenSCAP-Overview-security-scanning-for-docker-image-and-container-12-320.jpg)

![Result report is generated successfully
[root@localhost]/home/jooho/test# oscap-docker image-cve docker.io/rhel7
--report result.html
Definition oval:com.redhat.rhsa:def:20161633: false
Definition oval:com.redhat.rhsa:def:20161632: false
…..
Definition oval:com.redhat.rhsa:def:20140675: false
Evaluation done.](https://image.slidesharecdn.com/openscap2-160927015608/85/OpenSCAP-Overview-security-scanning-for-docker-image-and-container-14-320.jpg)
![Result report is created but some error messages..
[root@localhost]/home/jooho/test# oscap-docker container 4c0 xccdf eval --report result.html --profile
standard /usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml
WARNING: Skipping http://www.redhat.com/security/data/oval/Red_Hat_Enterprise_Linux_7.xml file
which is referenced from XCCDF content
Command: oscap xccdf eval --report result.html --profile standard
/usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml failed!
Error was:
Command '['oscap', 'xccdf', 'eval', '--report', 'result.html', '--profile', 'standard',
'/usr/share/xml/scap/ssg/content/ssg-rhel7-xccdf.xml']' returned non-zero exit status 2](https://image.slidesharecdn.com/openscap2-160927015608/85/OpenSCAP-Overview-security-scanning-for-docker-image-and-container-16-320.jpg)

![Result report is generated successfully
[root@localhost]/home/jooho/test# oscap-docker container-cve 4c0e74dc5094
--report result.html
Definition oval:com.redhat.rhsa:def:20161633: false
Definition oval:com.redhat.rhsa:def:20161632: false
…
Definition oval:com.redhat.rhsa:def:20140675: false
Evaluation done.](https://image.slidesharecdn.com/openscap2-160927015608/85/OpenSCAP-Overview-security-scanning-for-docker-image-and-container-18-320.jpg)

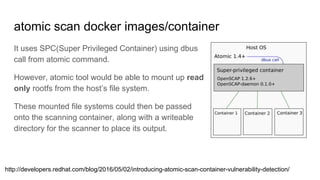

![Generated result json file on host successfully.
[root@localhost]/home/jooho/test# atomic scan docker.io/rhel7
docker run -it --rm -v /etc/localtime:/etc/localtime -v /run/atomic/2016-08-24-15-18-26-150045:/scanin -v
/var/lib/atomic/openscap/2016-08-24-15-18-26-150045:/scanout:rw,Z -v /etc/oscapd:/etc/oscapd:ro rhel7/openscap
oscapd-evaluate scan --no-standard-compliance --targets chroots-in-dir:///scanin --output /scanout
Usage of loopback devices is strongly discouraged for production use. Either use `--storage-opt dm.thinpooldev` or use
`--storage-opt dm.no_warn_on_loop_devices=true` to suppress this warning.
docker.io/rhel7 (6f7a31562d1ec72)
docker.io/rhel7 passed the scan
Files associated with this scan are in /var/lib/atomic/openscap/2016-08-24-15-18-26-150045.](https://image.slidesharecdn.com/openscap2-160927015608/85/OpenSCAP-Overview-security-scanning-for-docker-image-and-container-24-320.jpg)