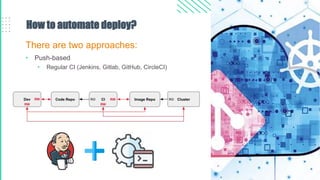
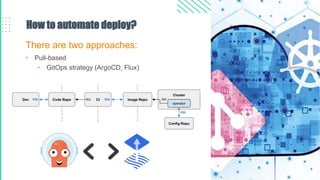
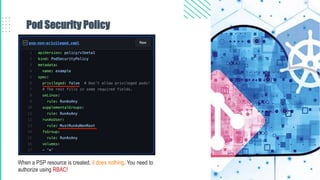
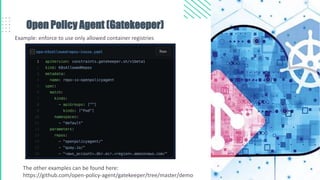
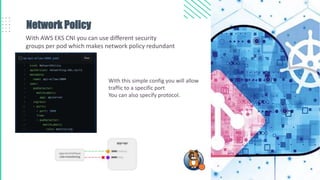
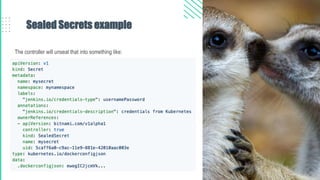
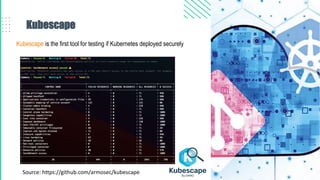
The document outlines best practices for Kubernetes and container security, highlighting the importance of vulnerability scanning, restricted permissions, and periodic reviews to minimize attack surfaces. It details specific strategies for enhancing security, including design patterns in Dockerfile and deployment methods, as well as tools for auditing and monitoring Kubernetes environments. Furthermore, it discusses key principles such as the 'principle of least privilege' and the necessity of managing secrets properly within the Kubernetes ecosystem.

![[devops@stage ~]$ cat ABOUT_ME.md
• 6+ years of commercial DevOps experience. Overall 8+ years of
Engineering
• Member of Technology Office
• Member of the Center of Excellence
• Successfully migrated, rolled out, consulted over 15 projects in
the healthcare, gambling, automotive, e-commerce industries
• Certified SAFe Agile Software Engineer
• Addicted to IoT and Smart Home
• Cyclist, promoter of a healthy lifestyle
Volodymyr Shynkar
Senior Lead DevOps Engineer at Intellias
[devops@stage ~]$](https://image.slidesharecdn.com/kubernetesandcontainersecurity-210924122516/85/Kubernetes-and-container-security-2-320.jpg)