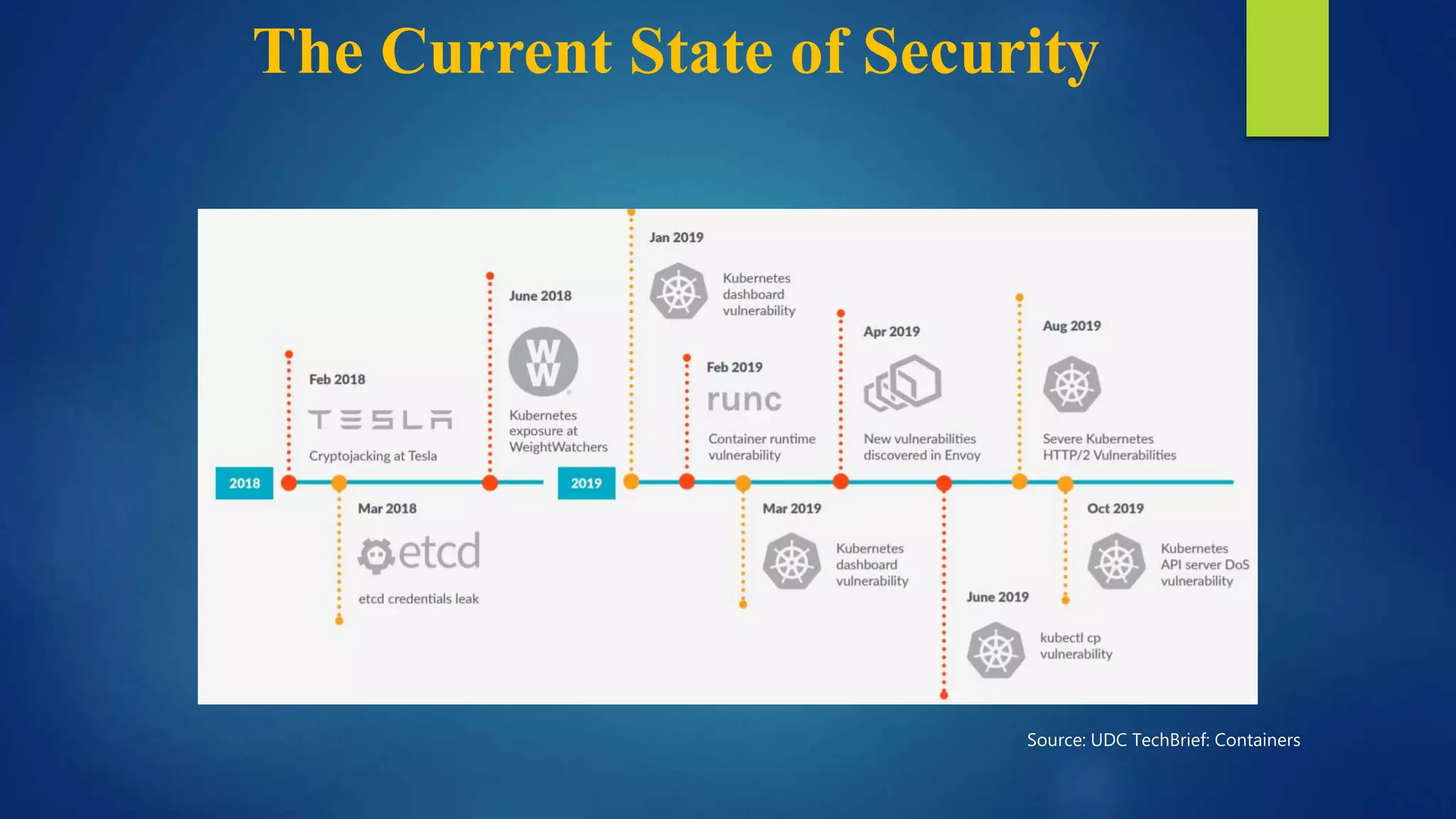
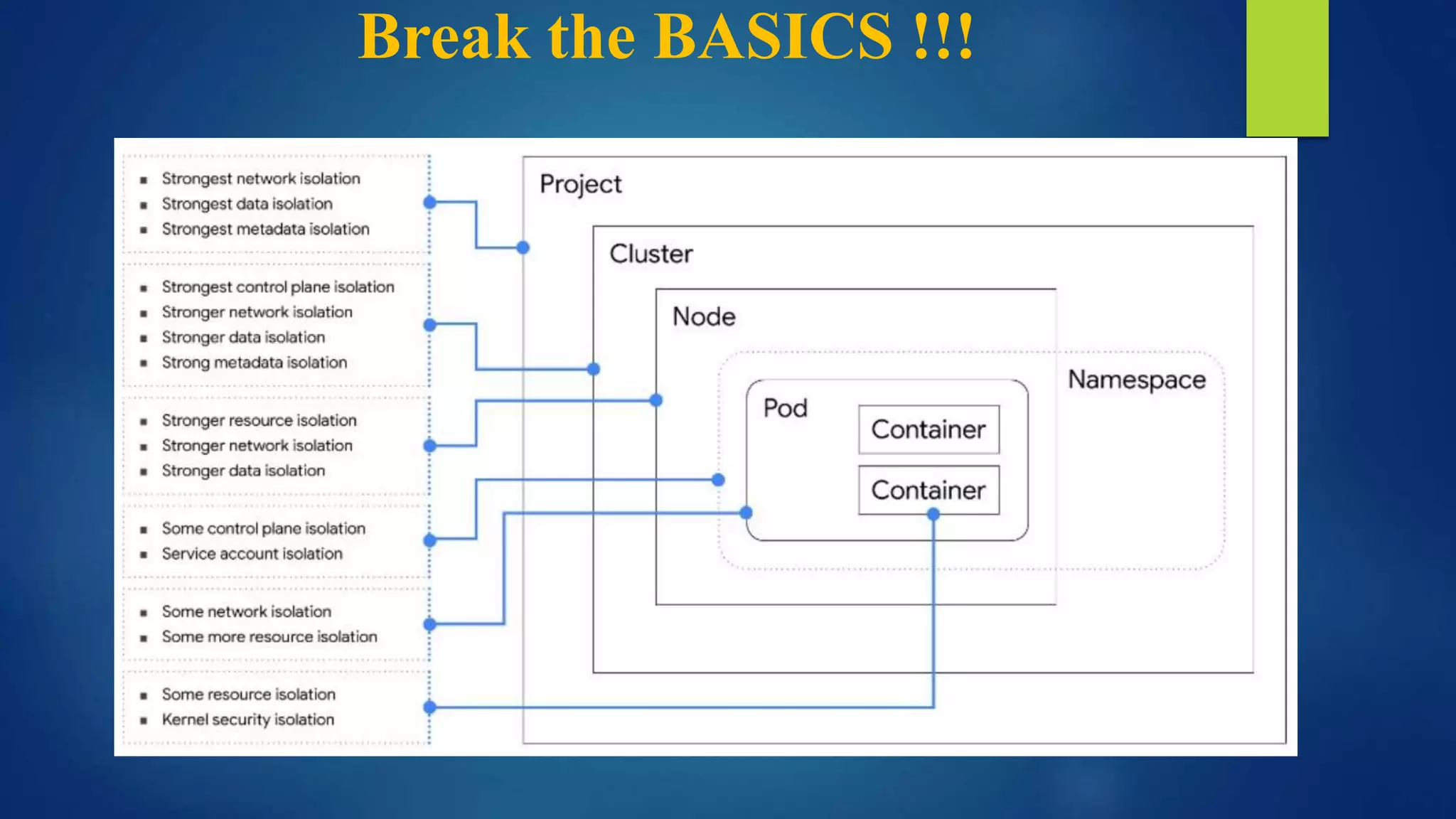
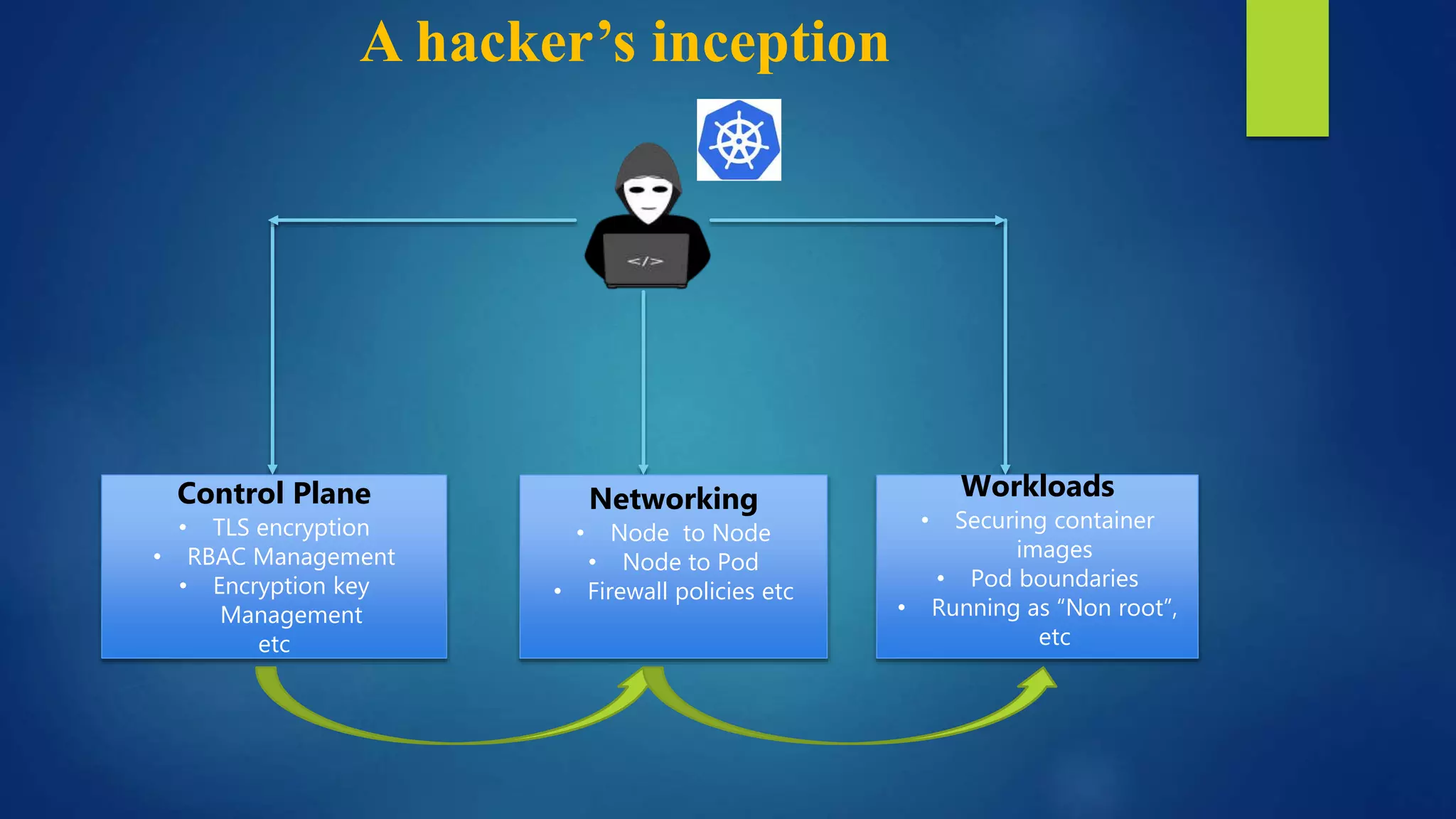
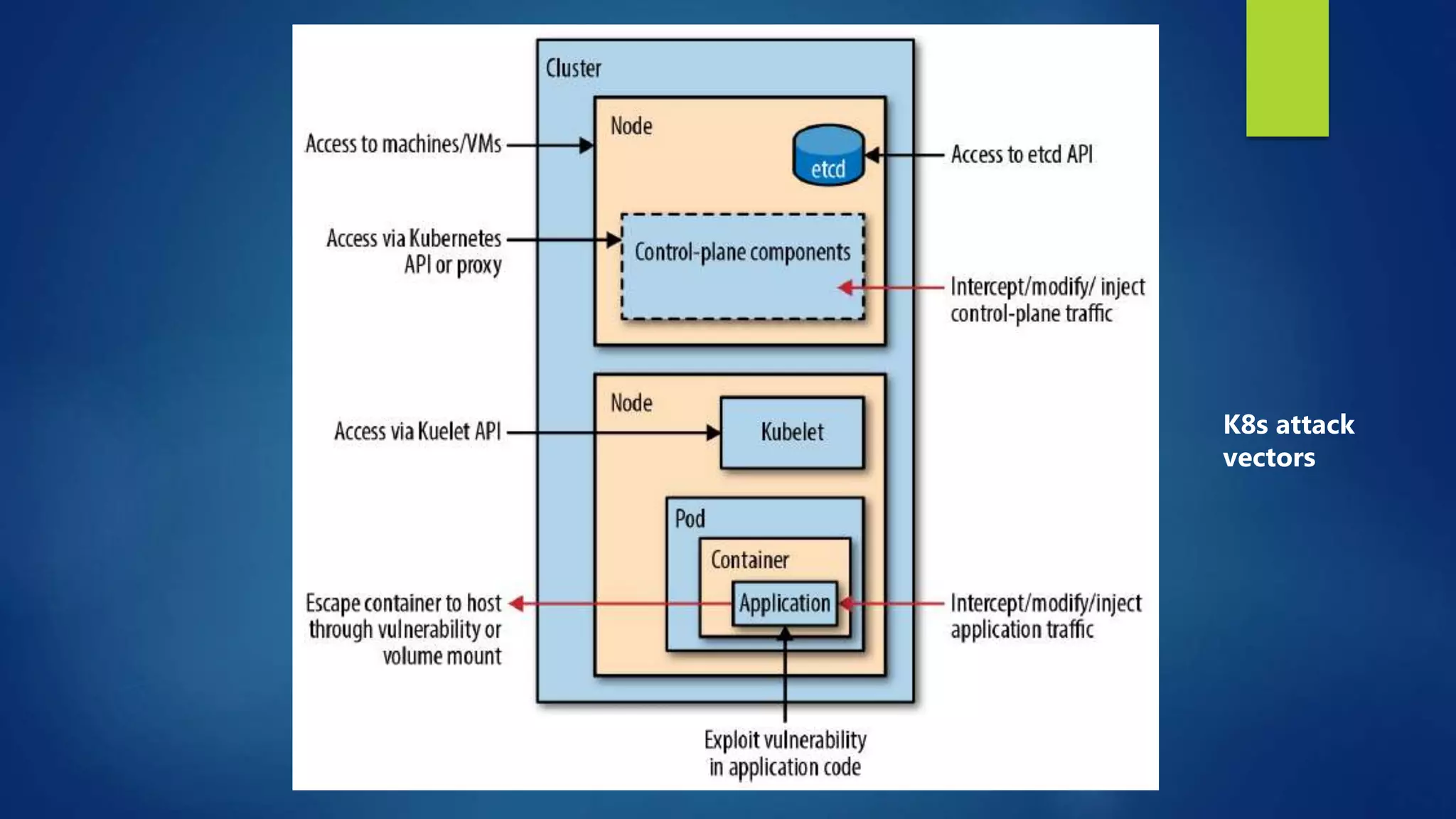
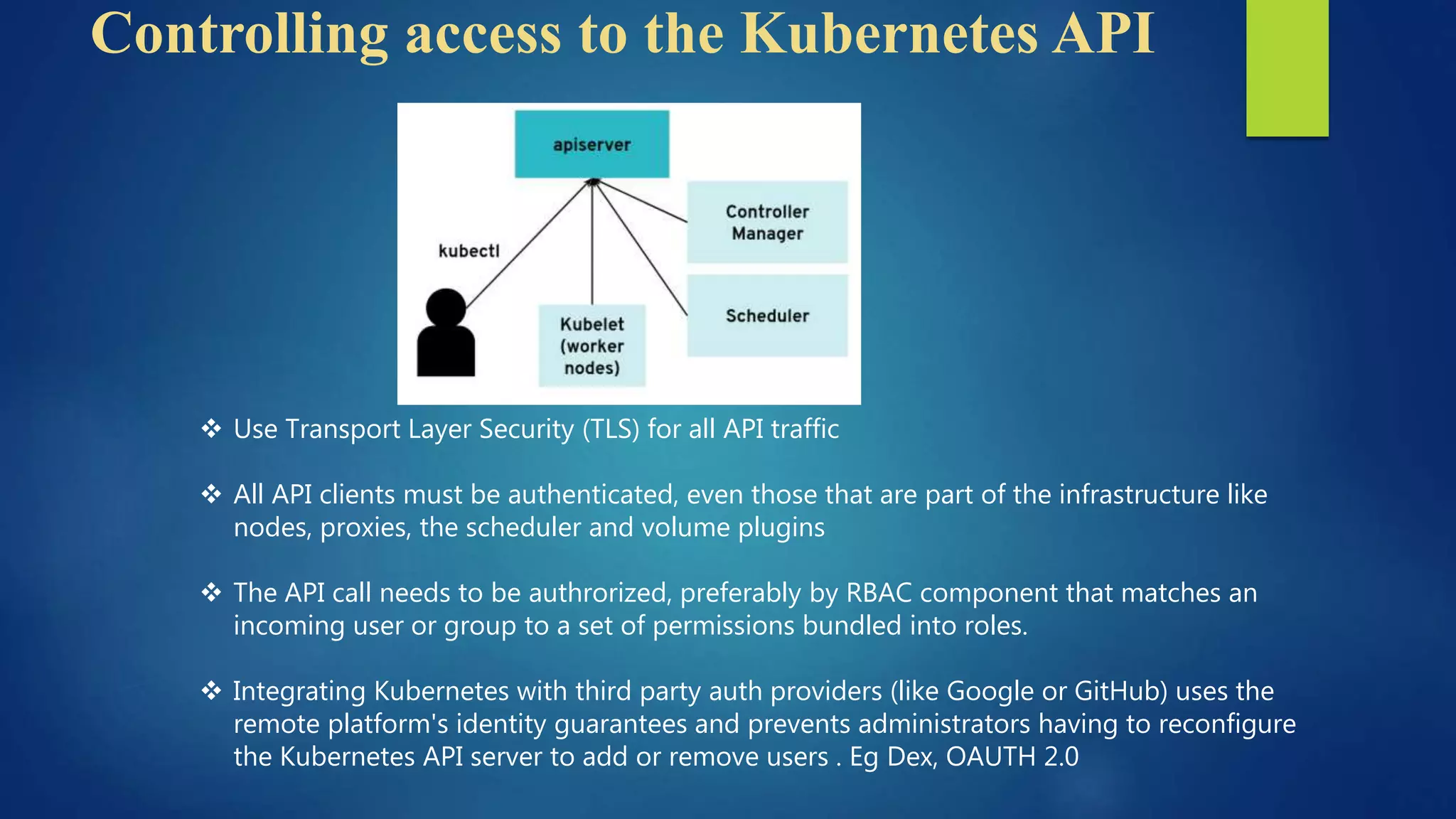
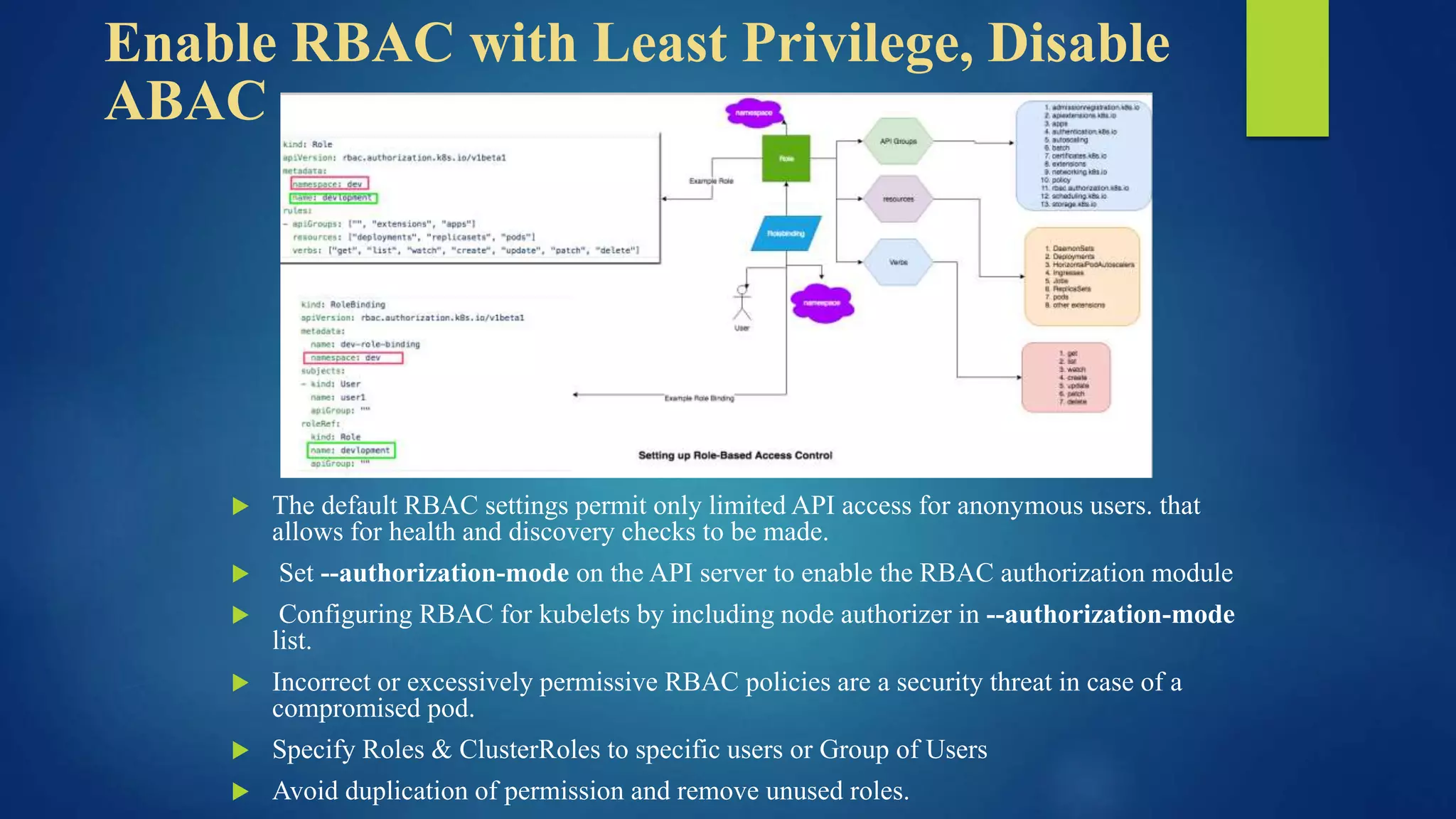
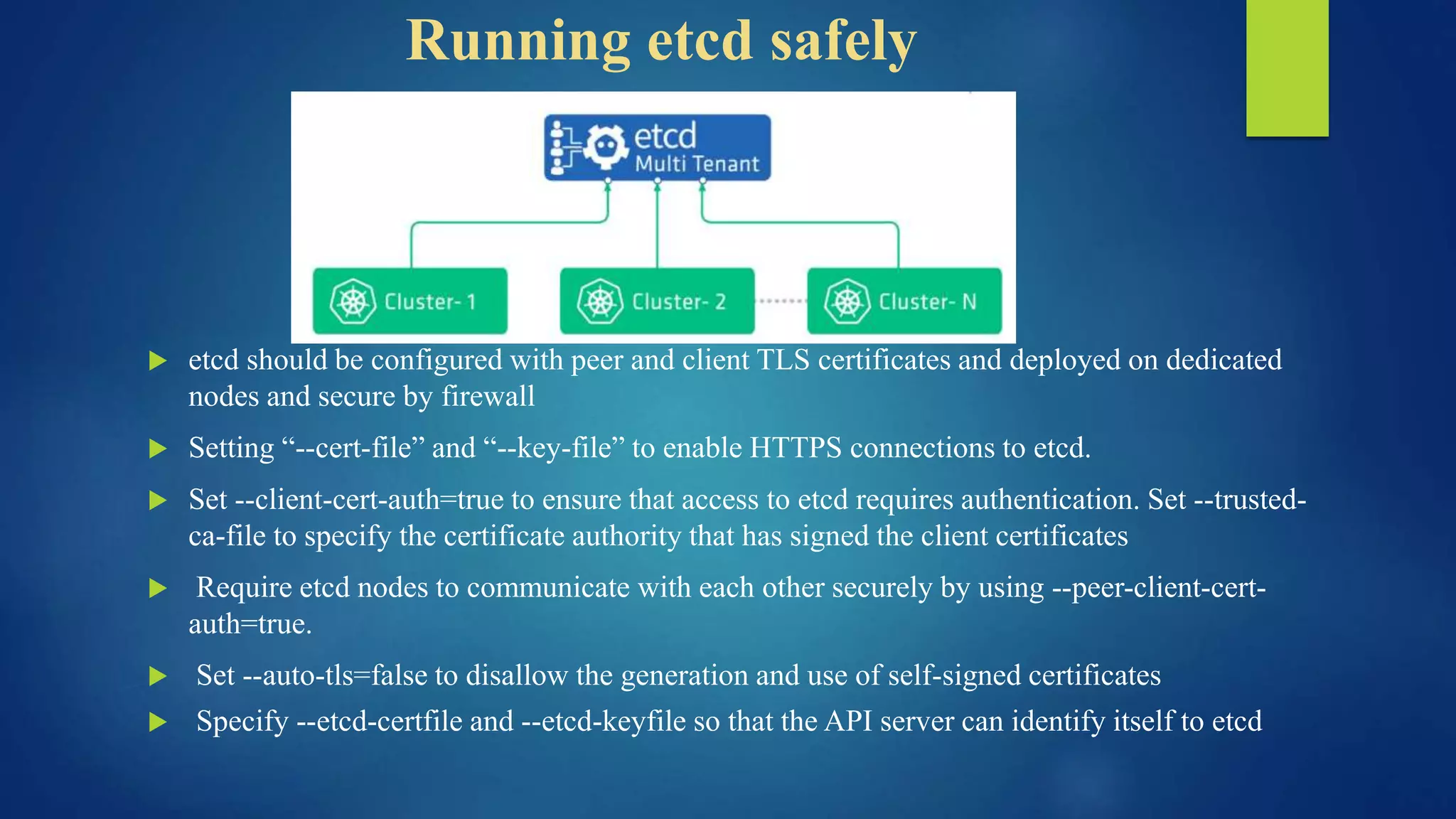
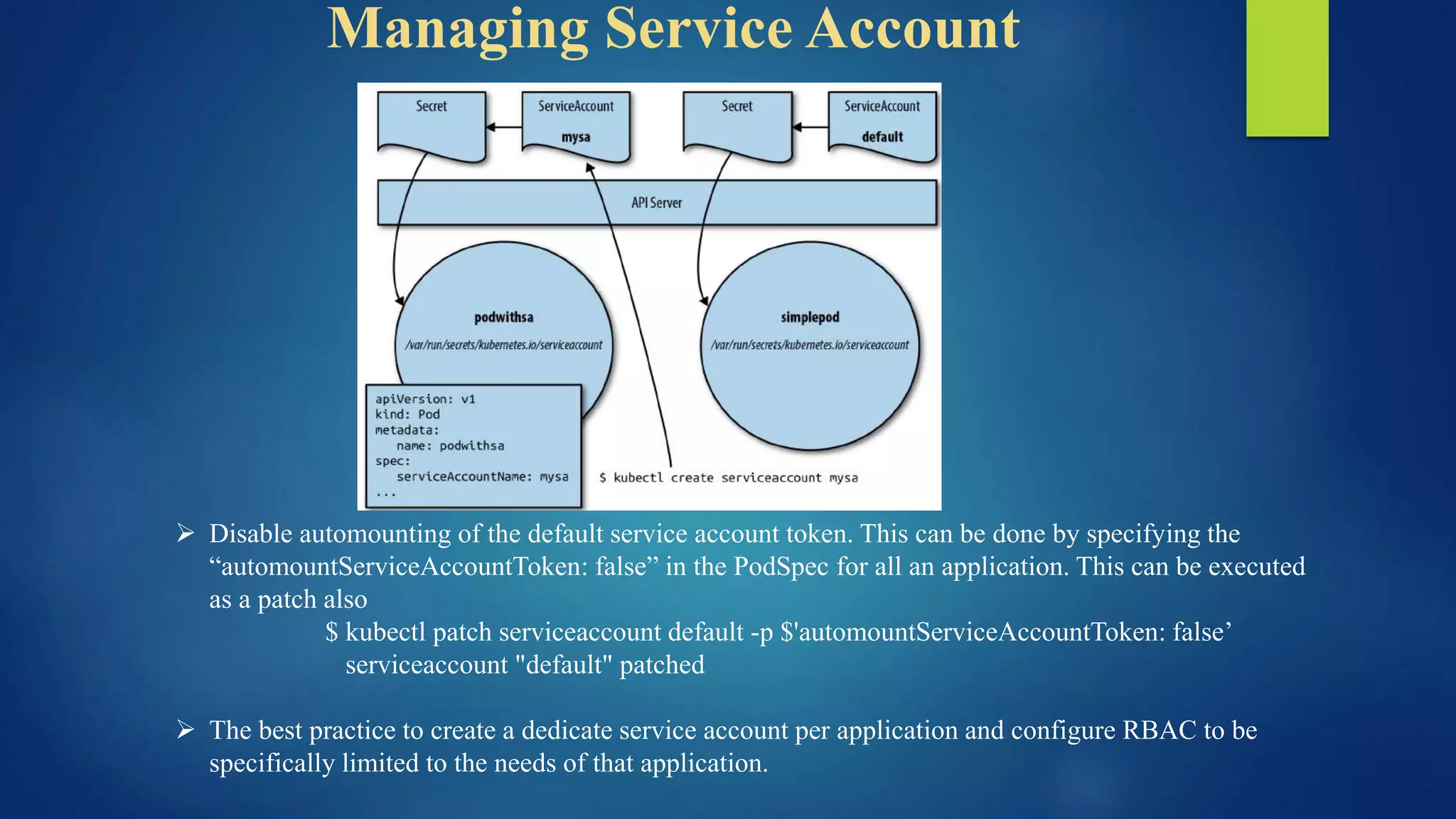
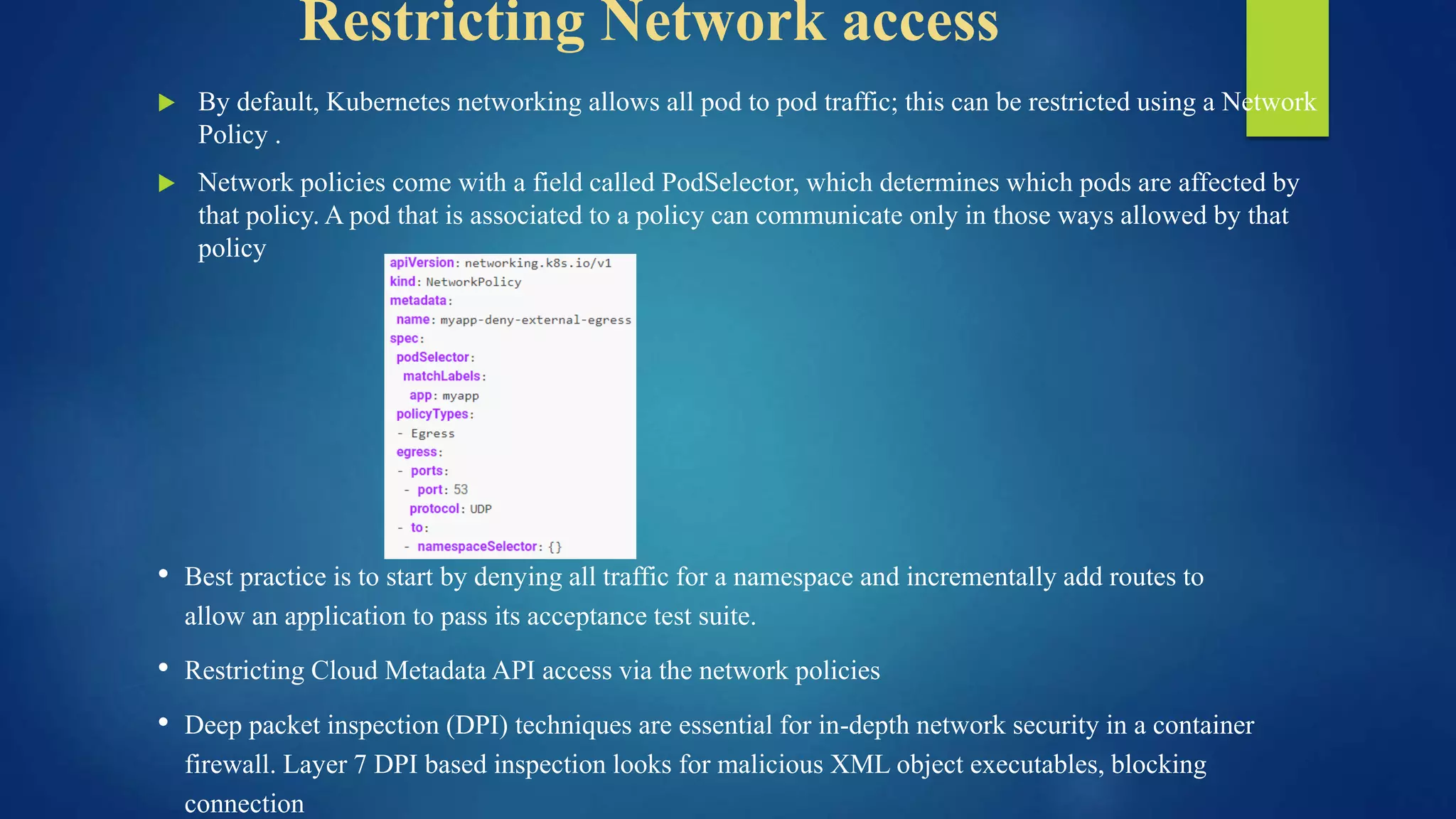
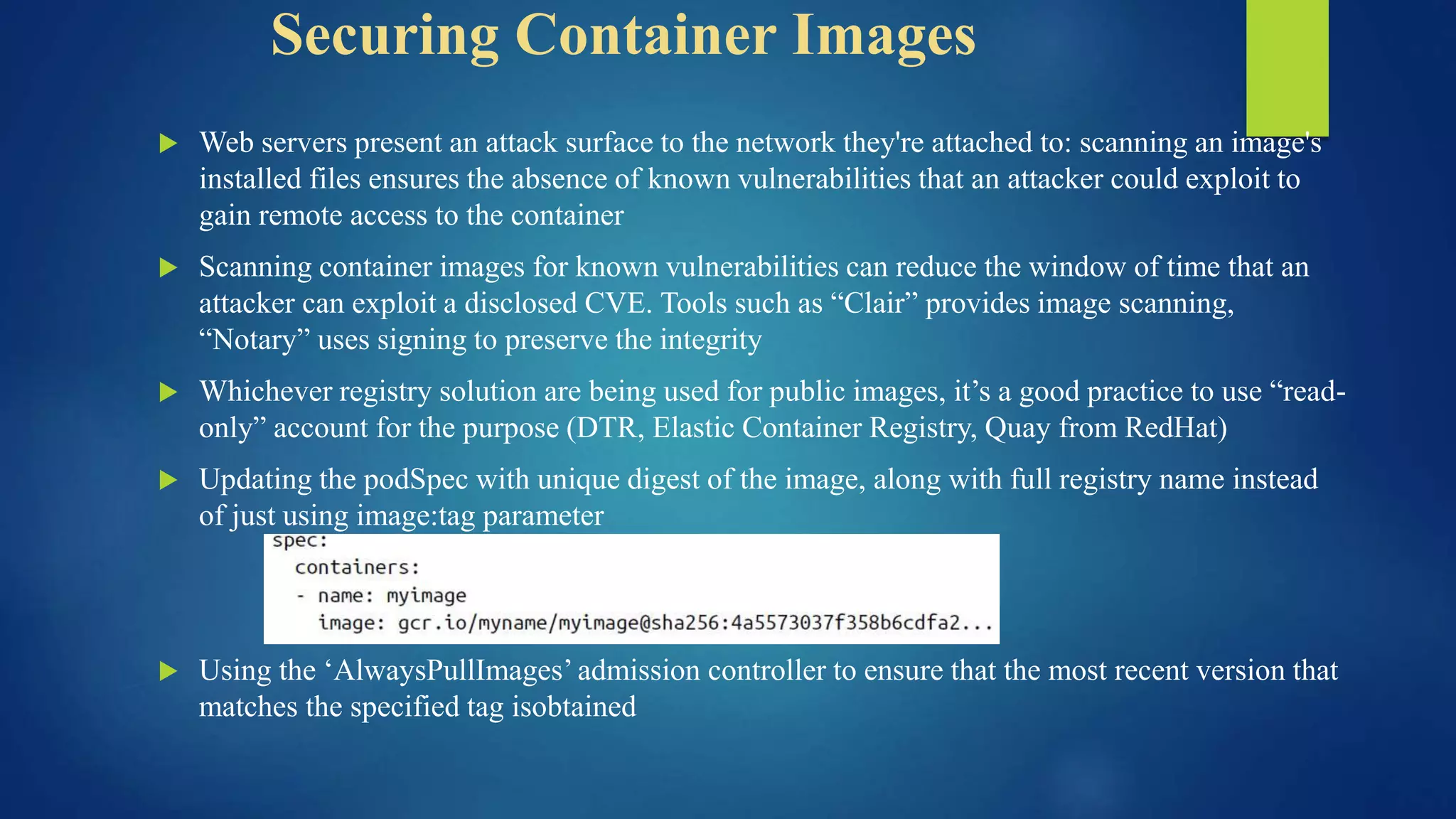
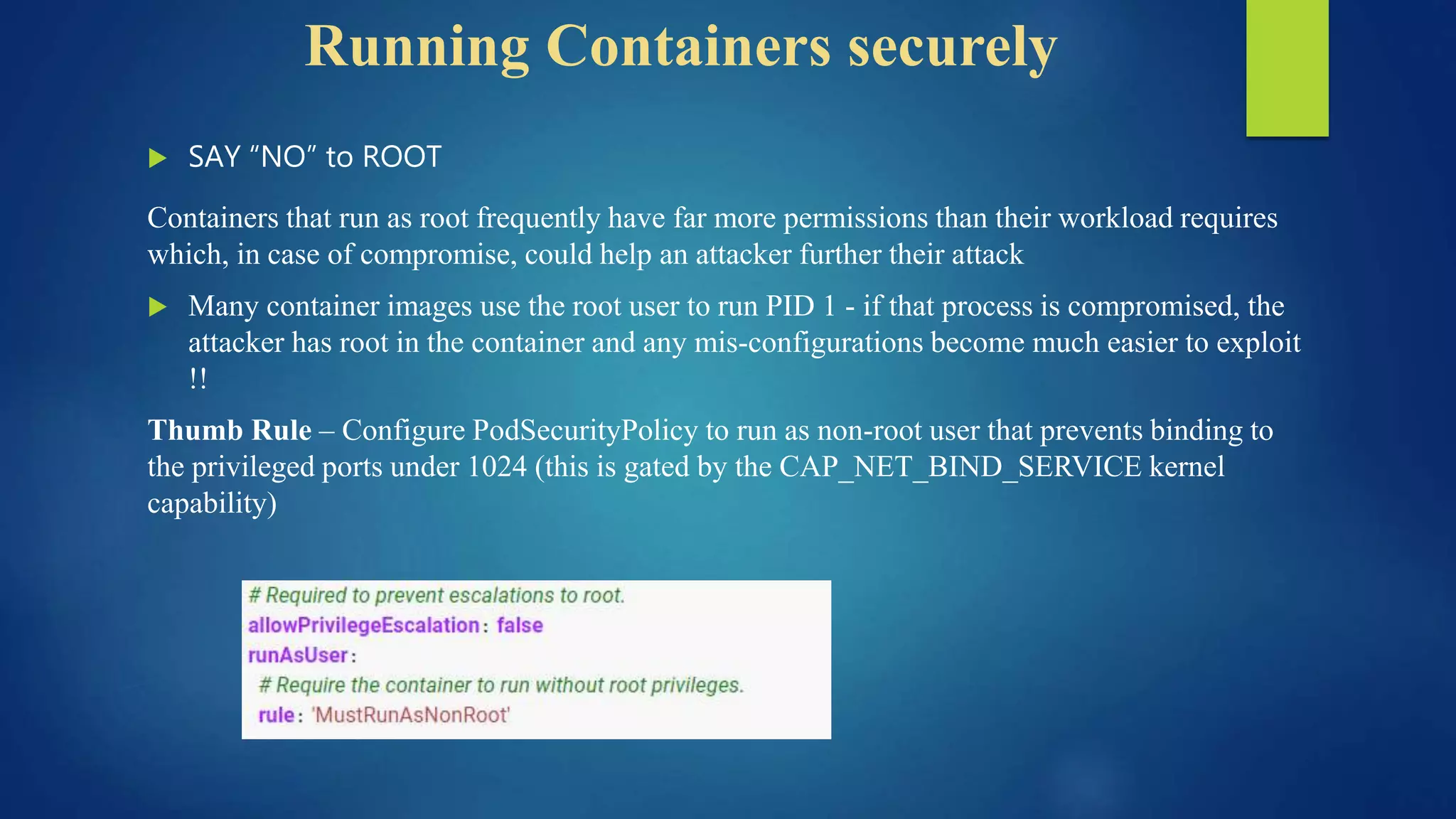
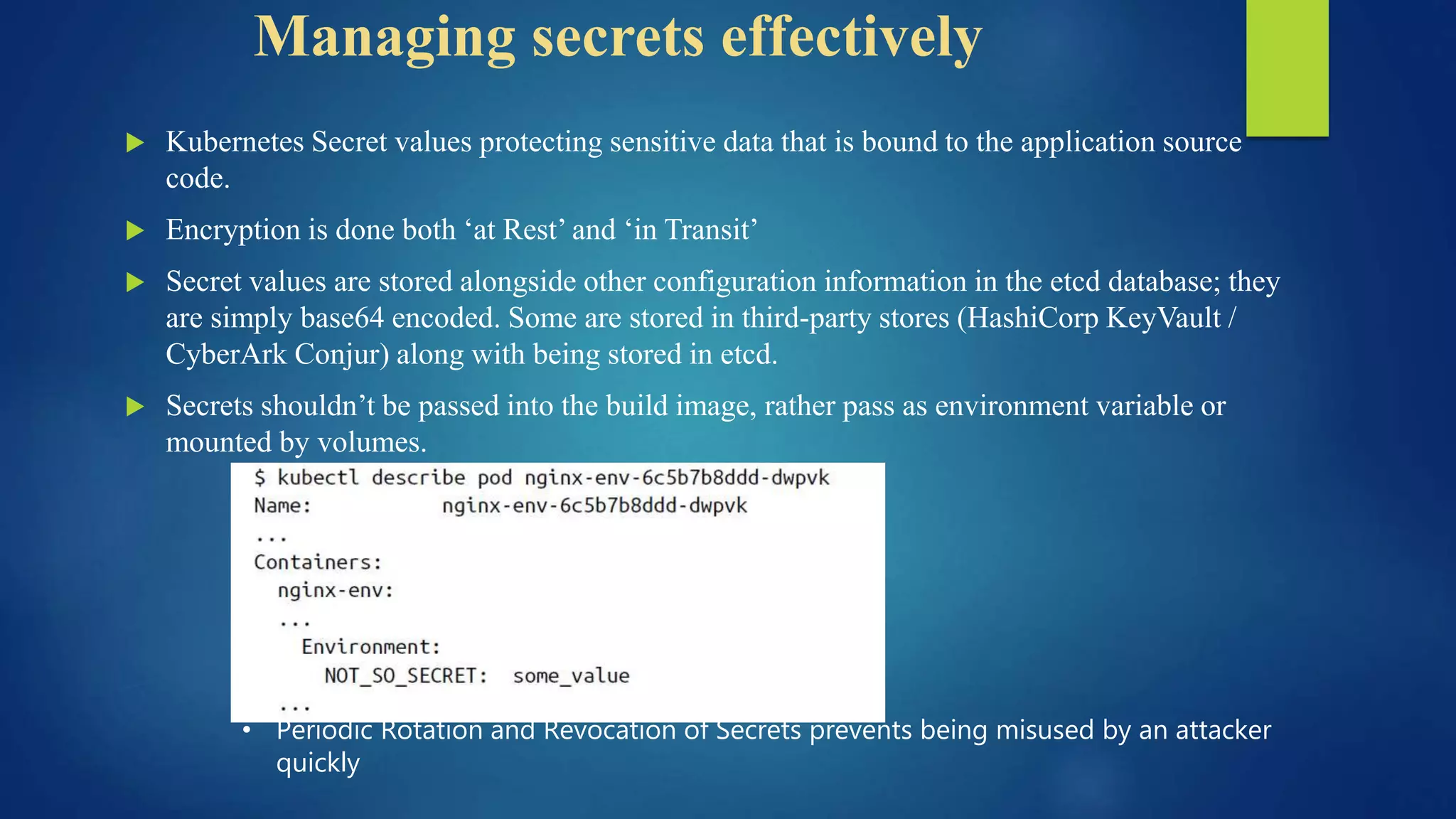
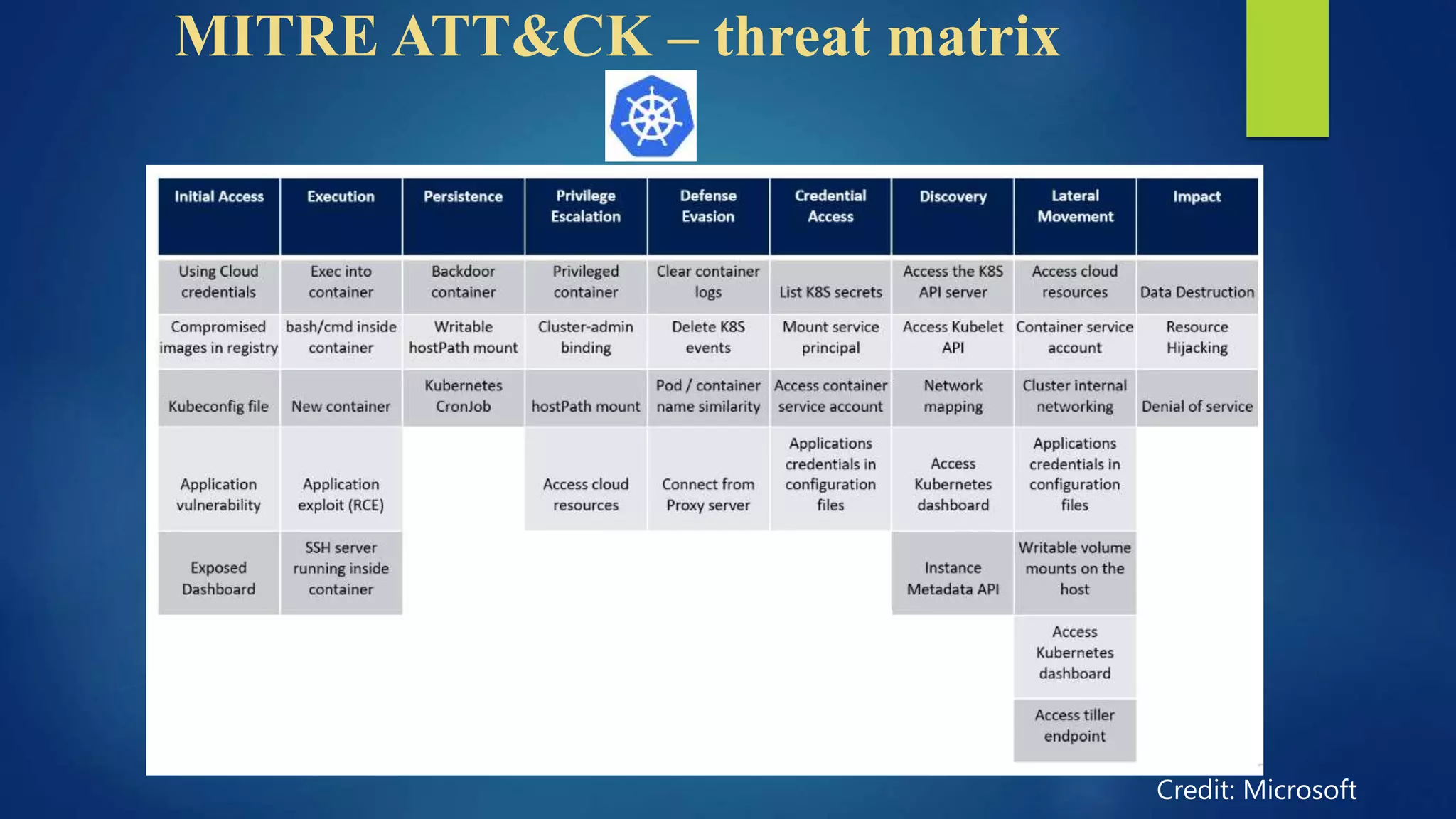
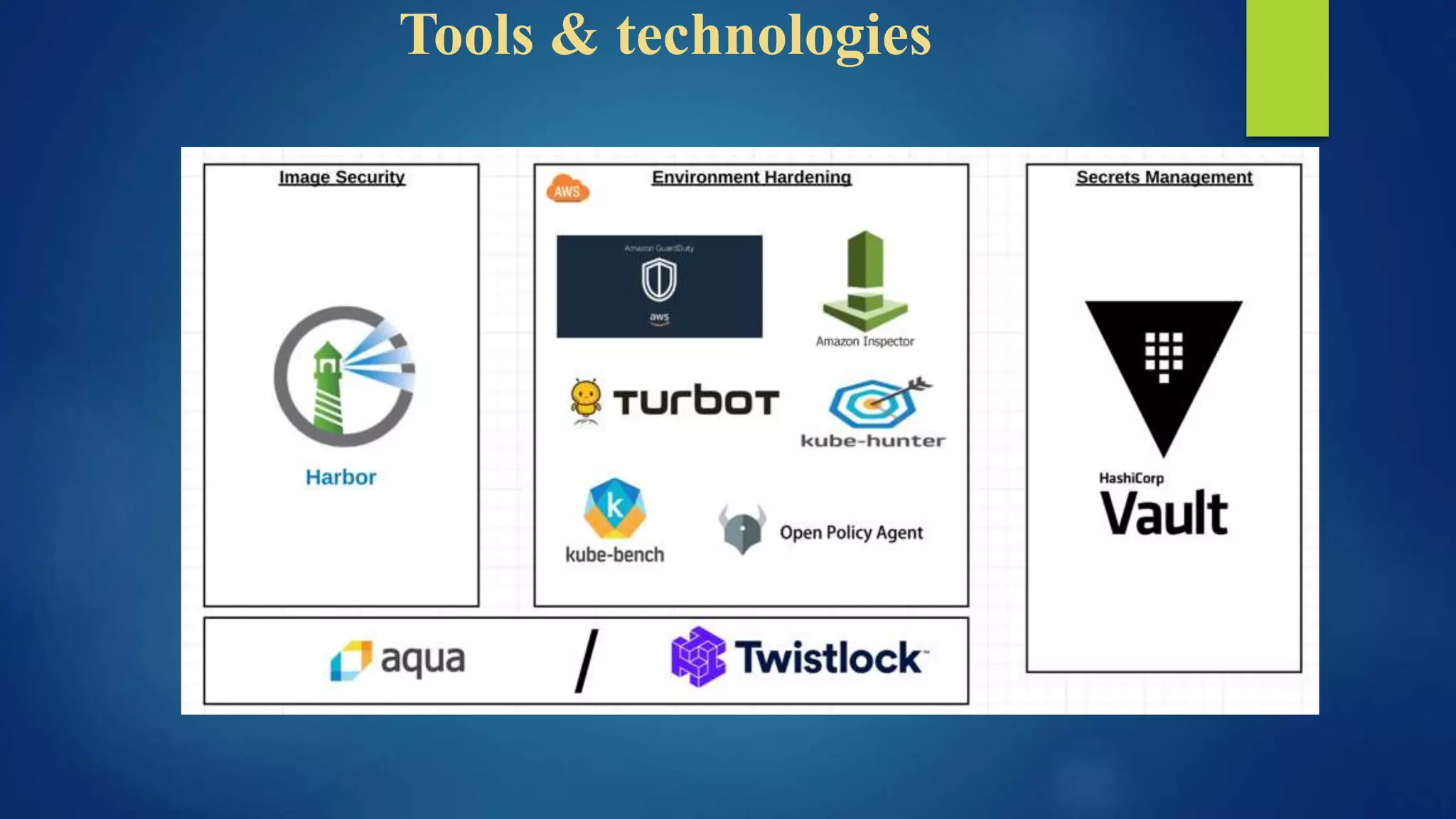
The document outlines essential security practices for Kubernetes environments, focusing on mitigating risks such as insider attacks, unauthorized access, and securing workloads. Key recommendations include implementing RBAC with least privilege, monitoring pod communications, restricting network access, and securing container images. It also emphasizes the importance of managing secrets effectively and adopting service mesh for enhanced security in a microservices architecture.