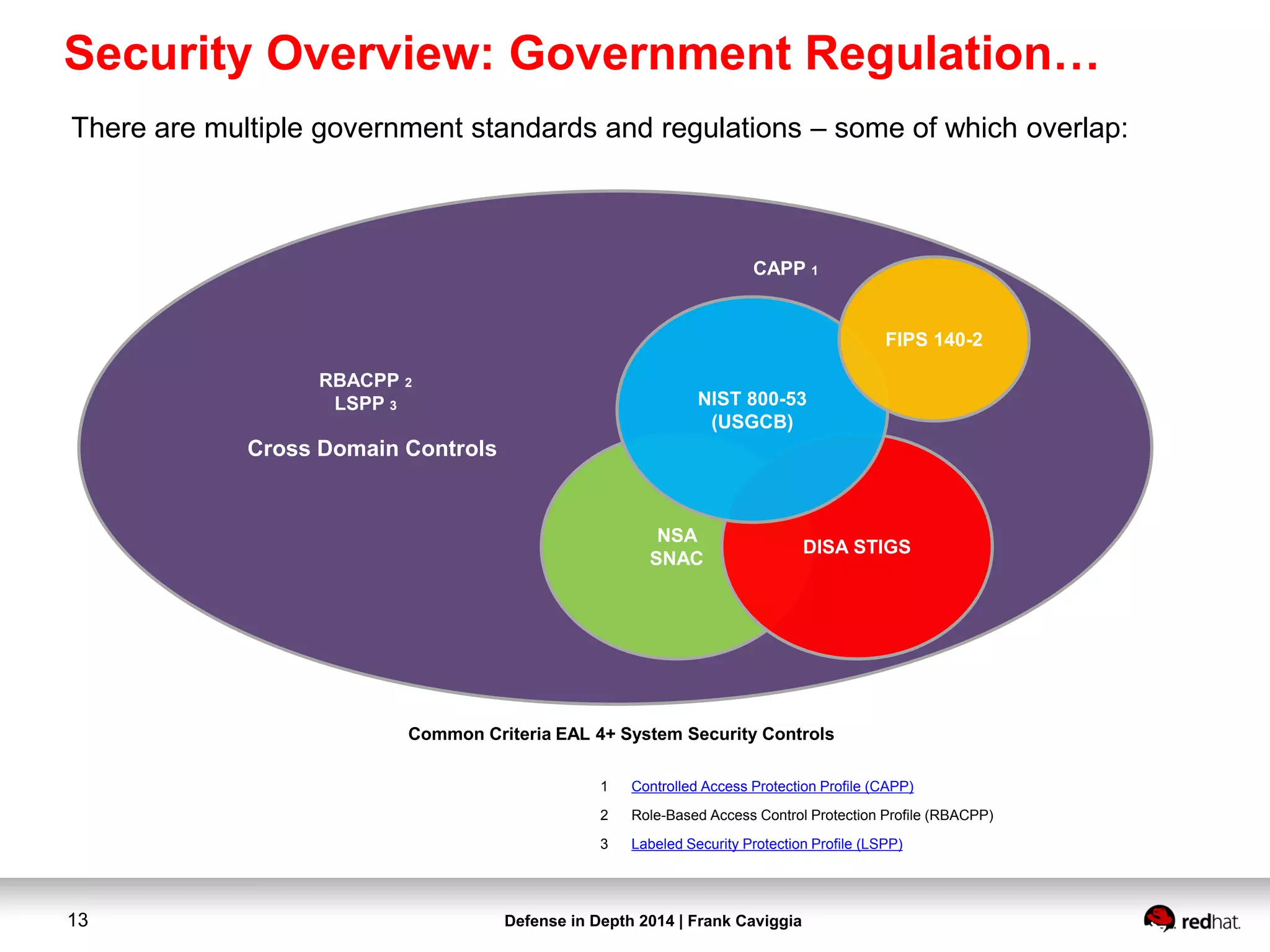
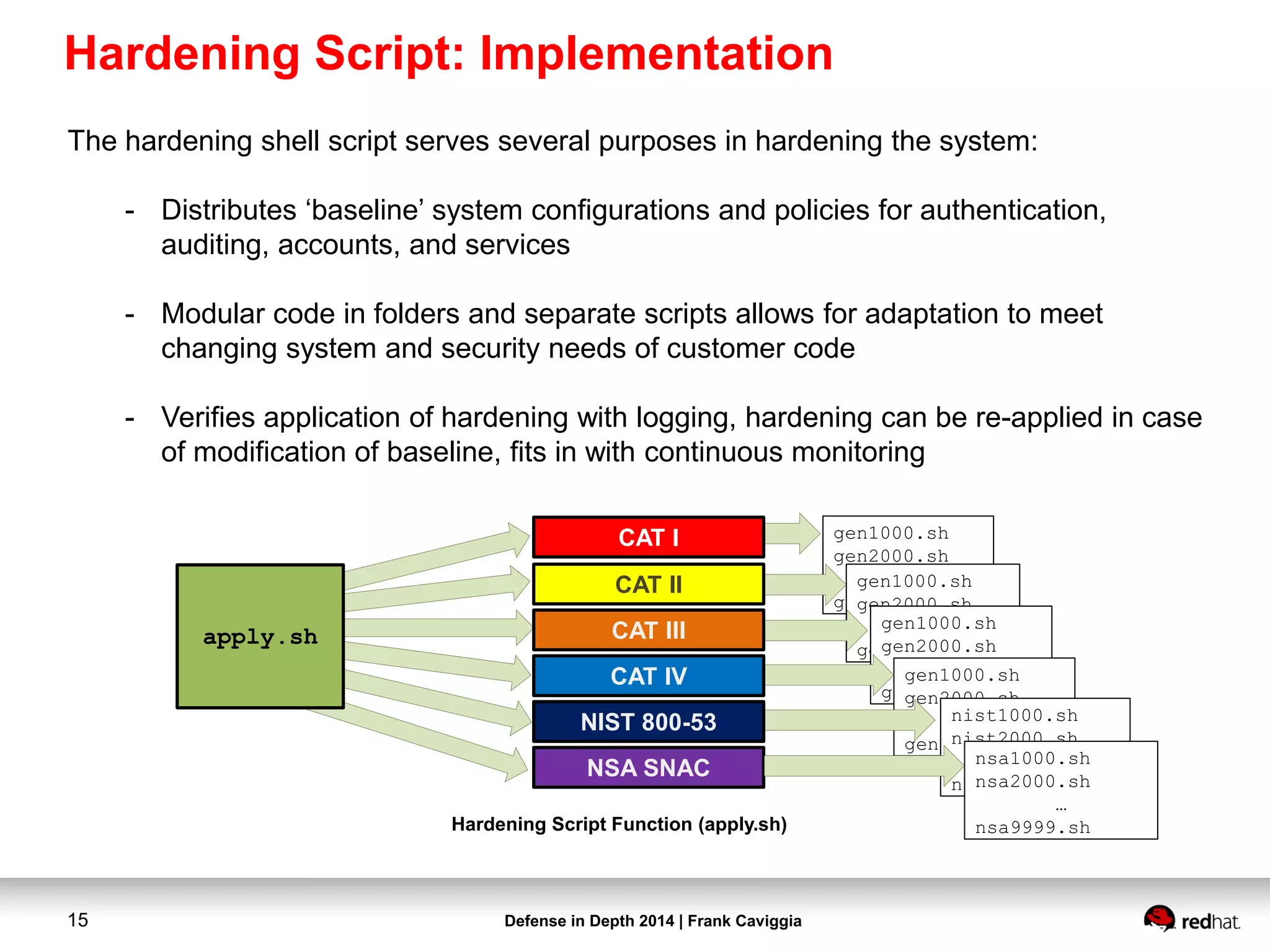
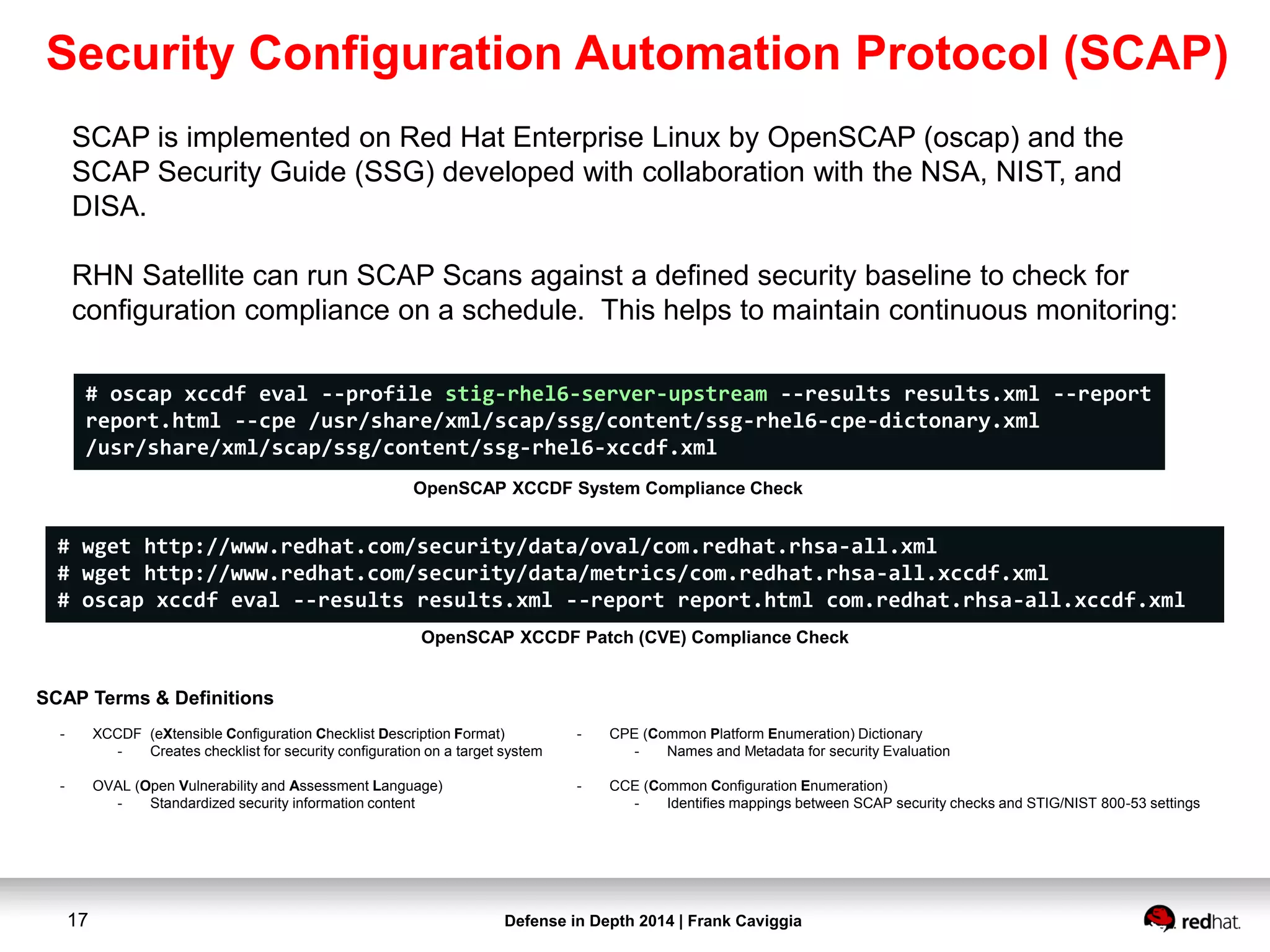
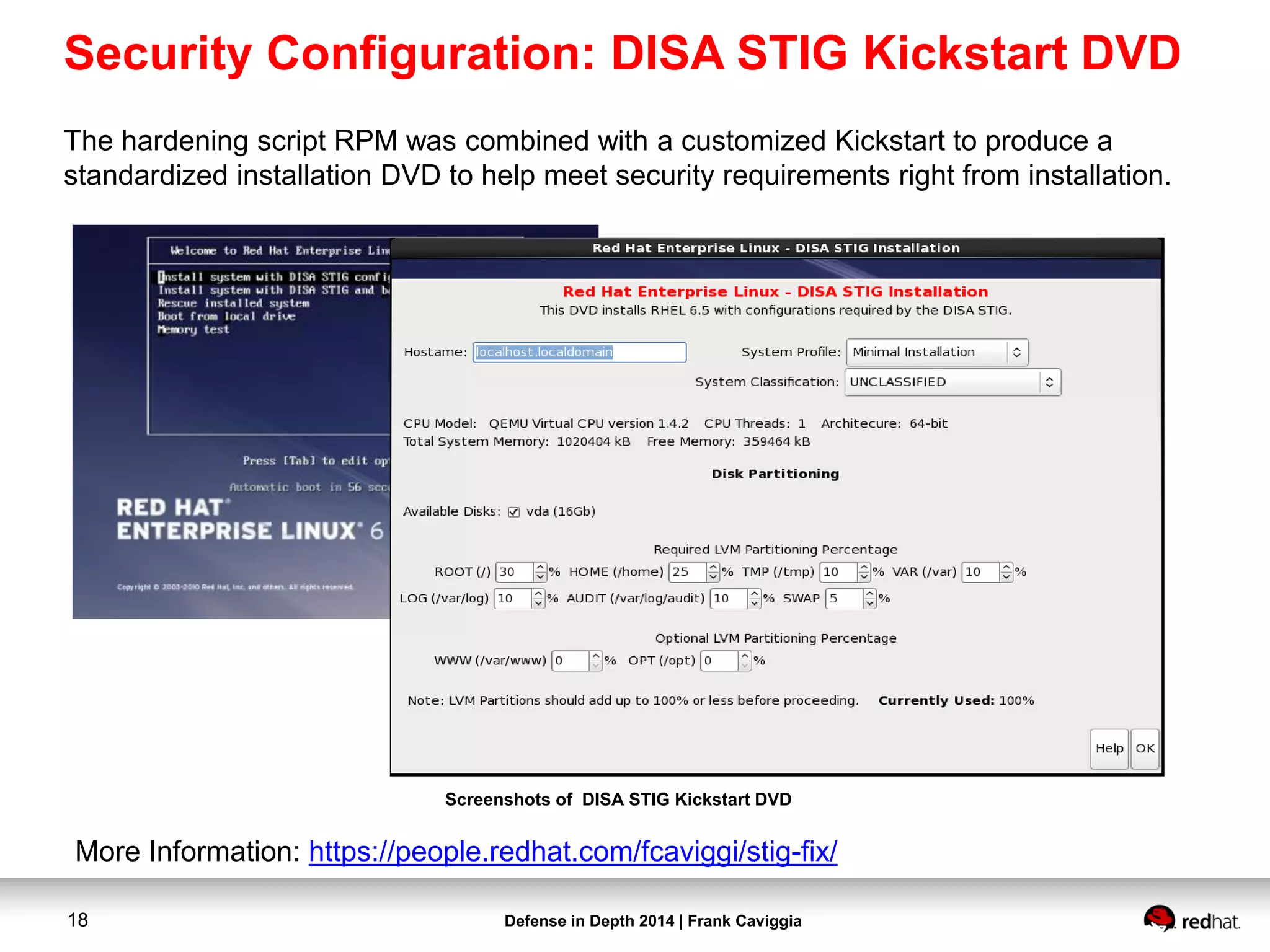
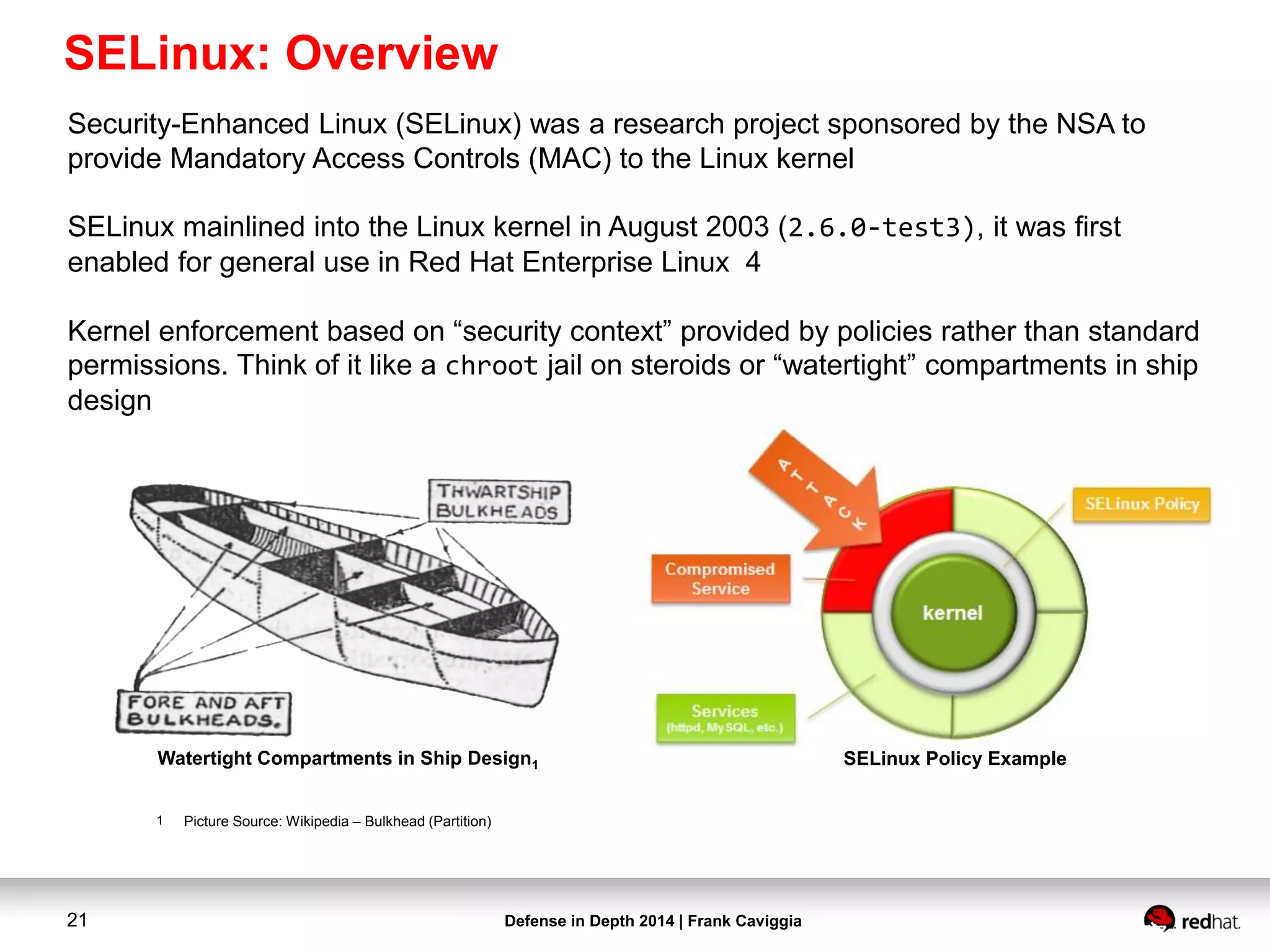
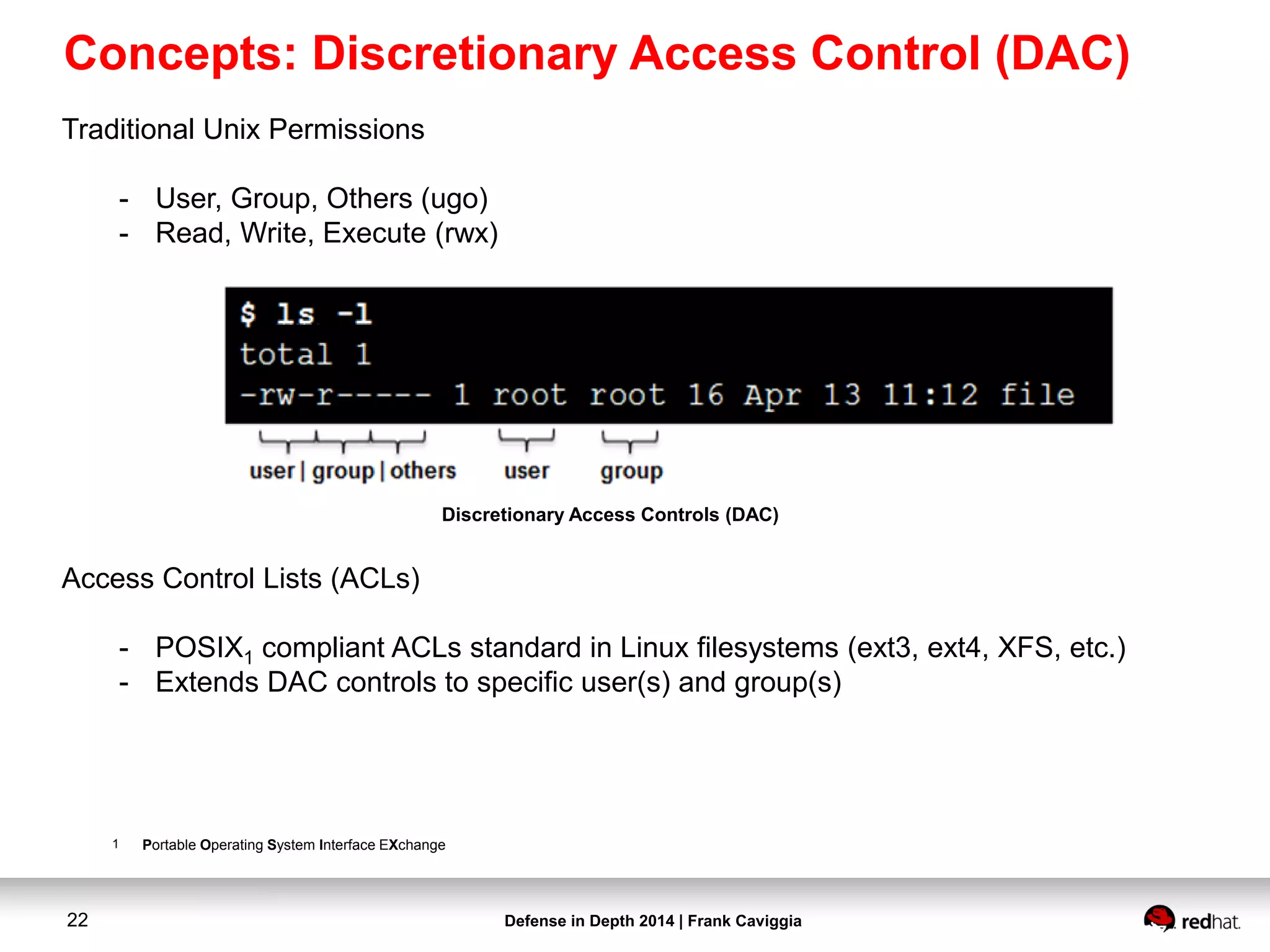
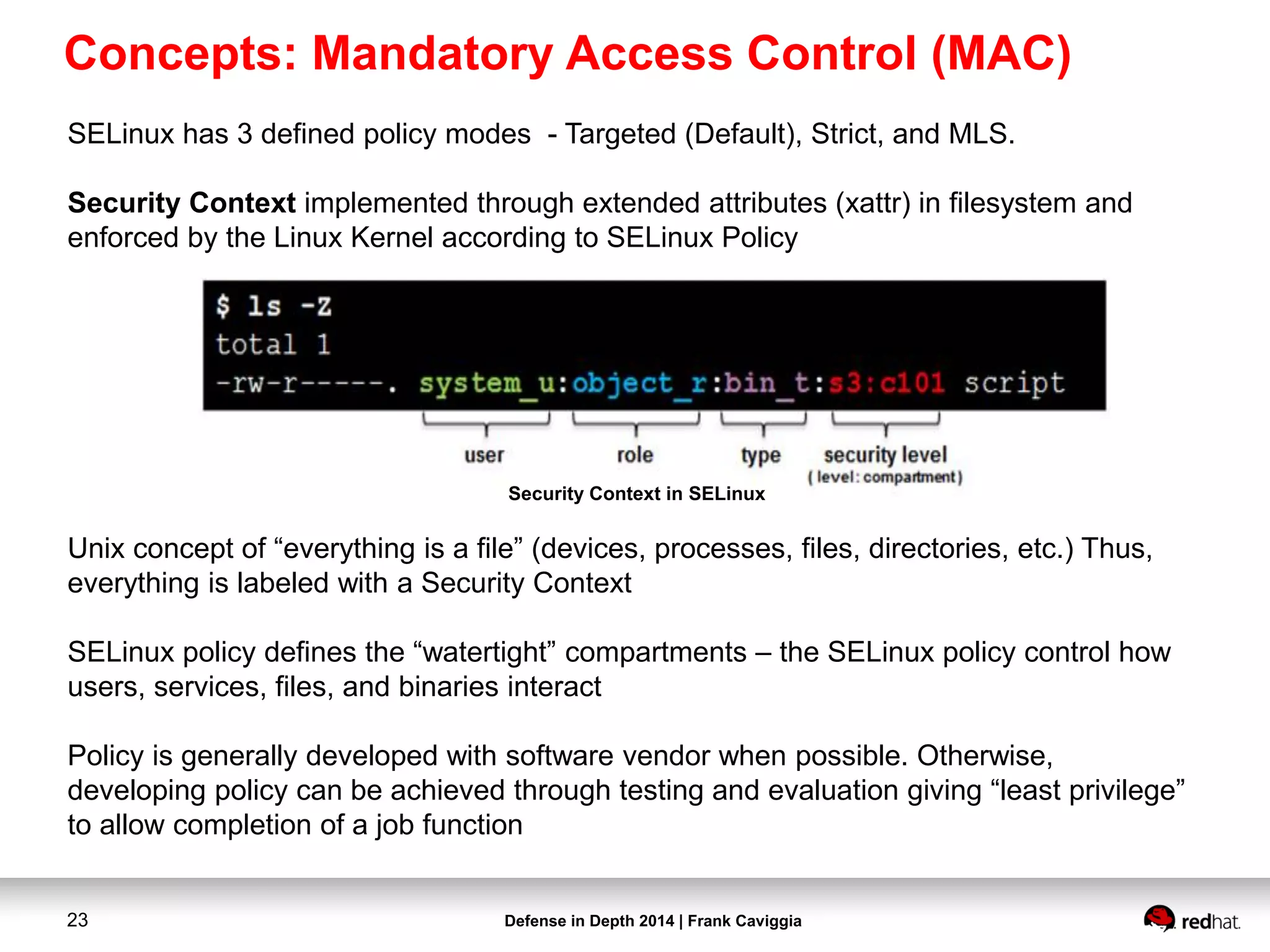
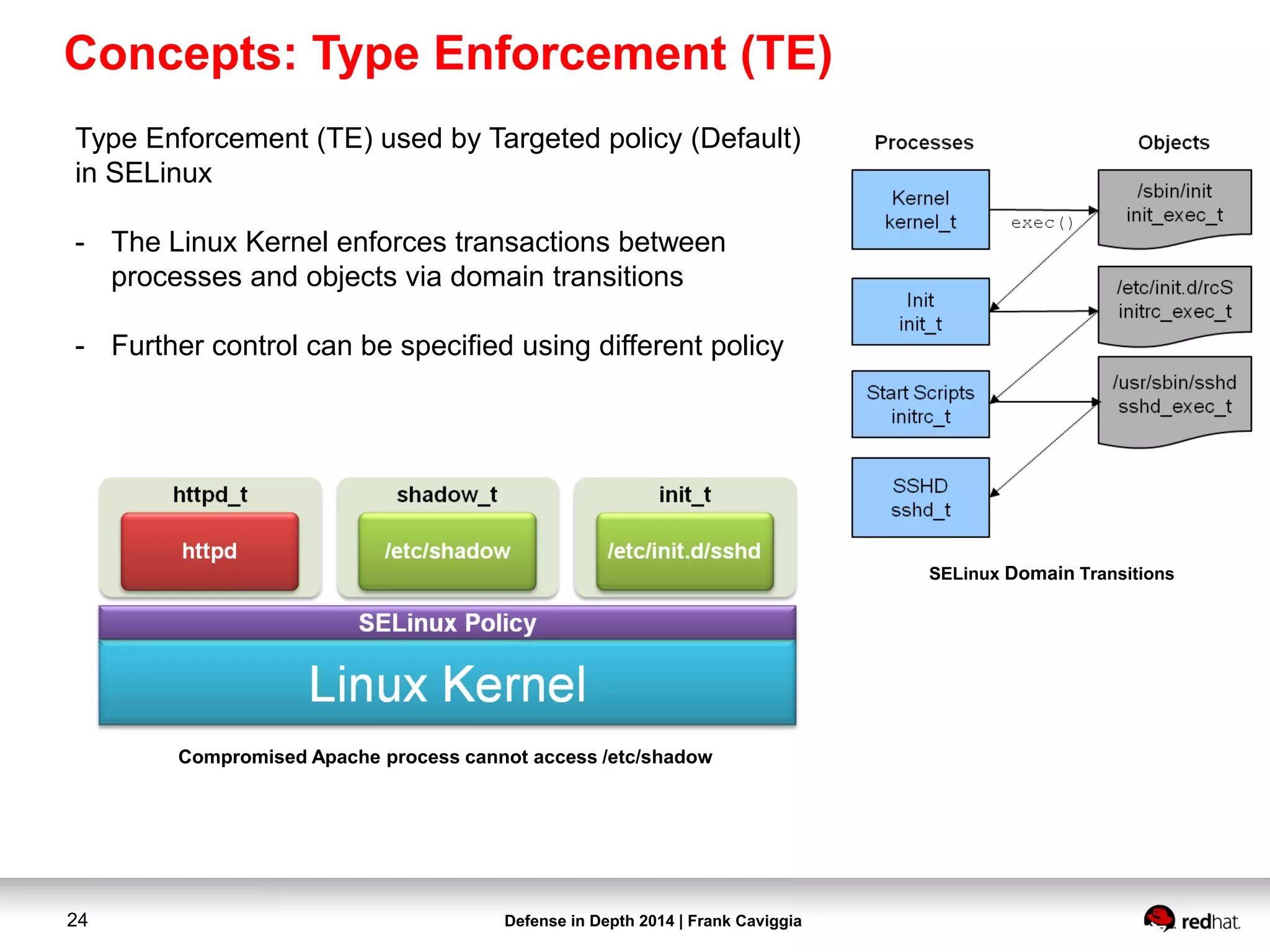
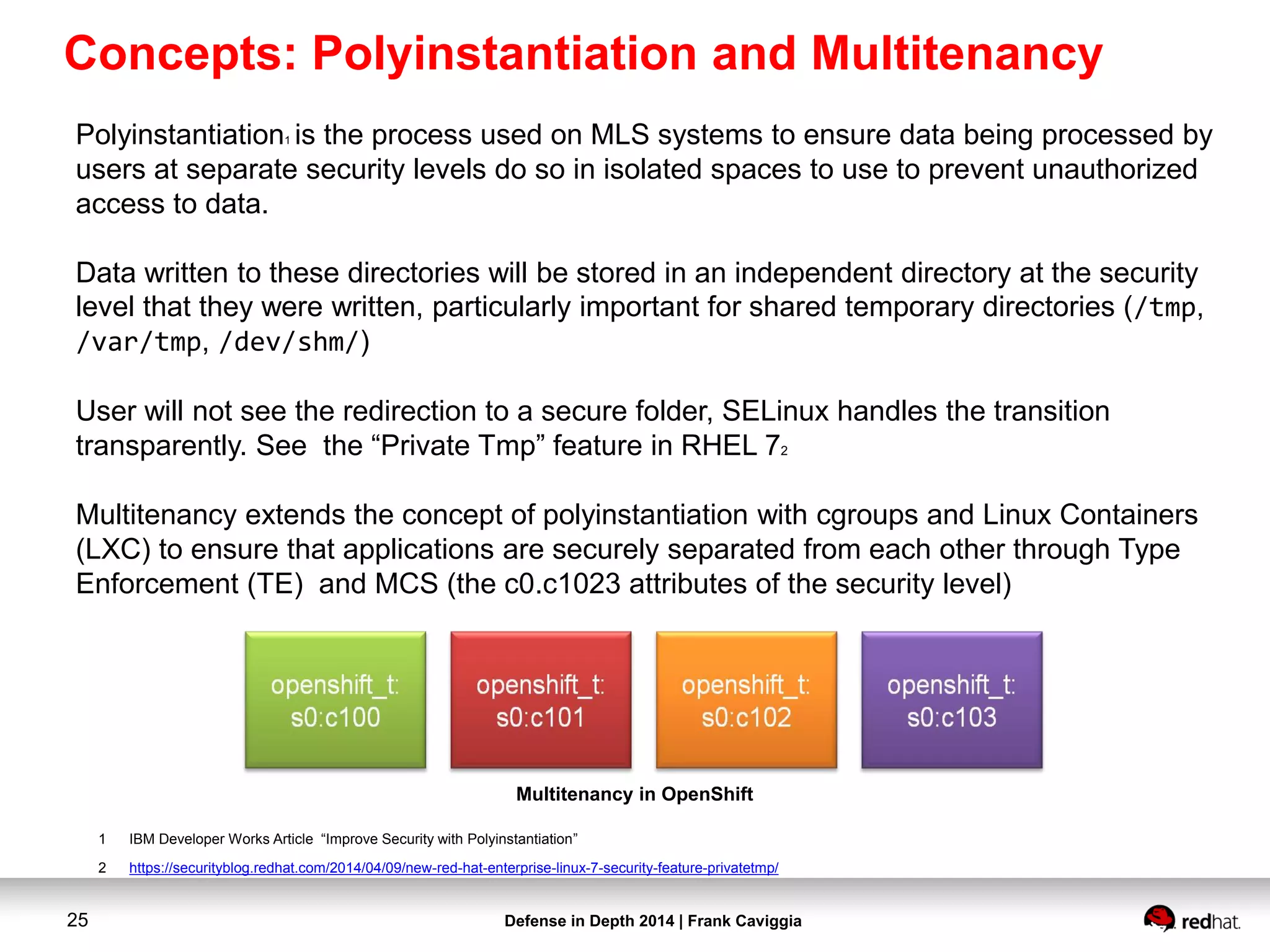
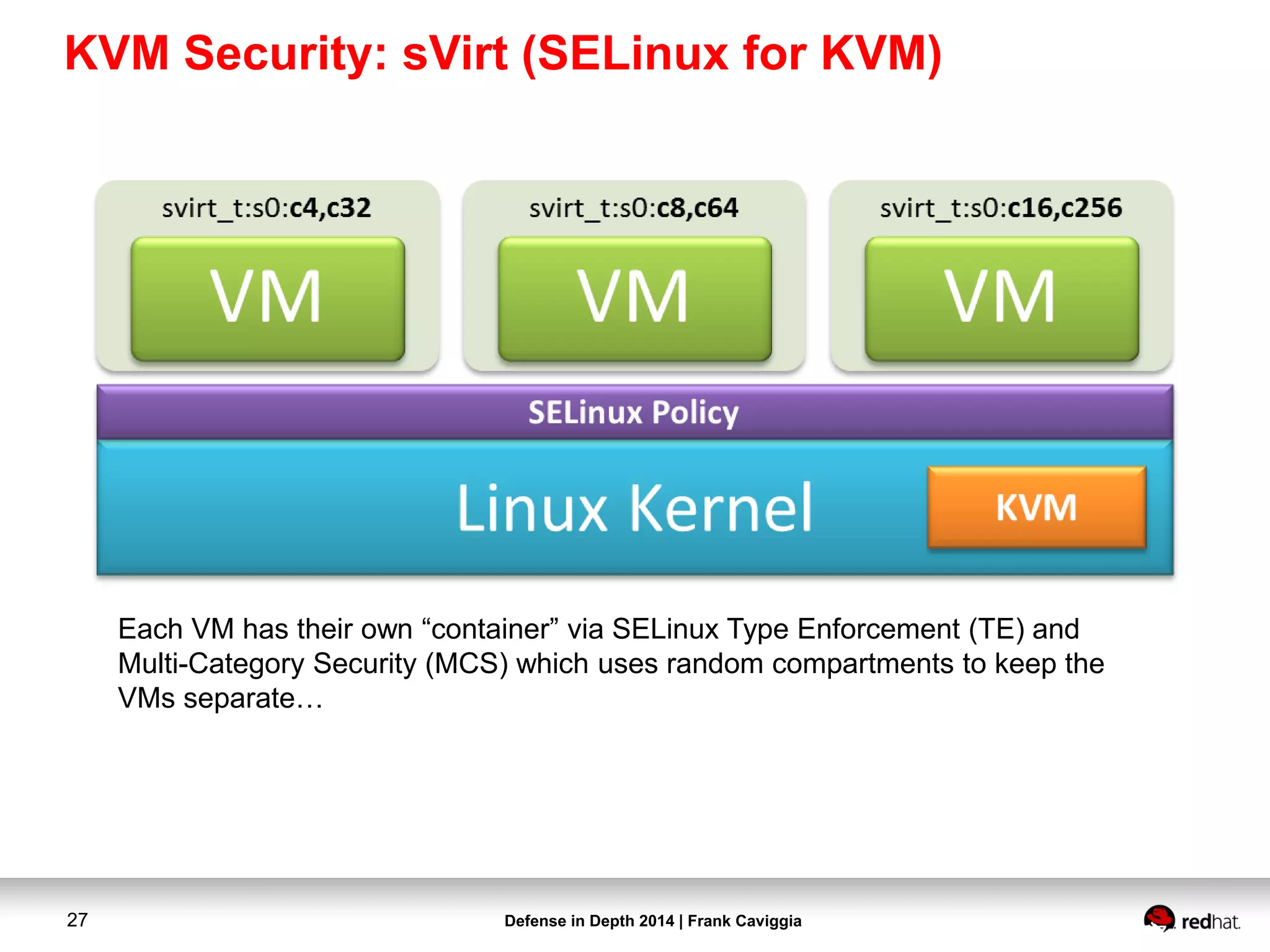
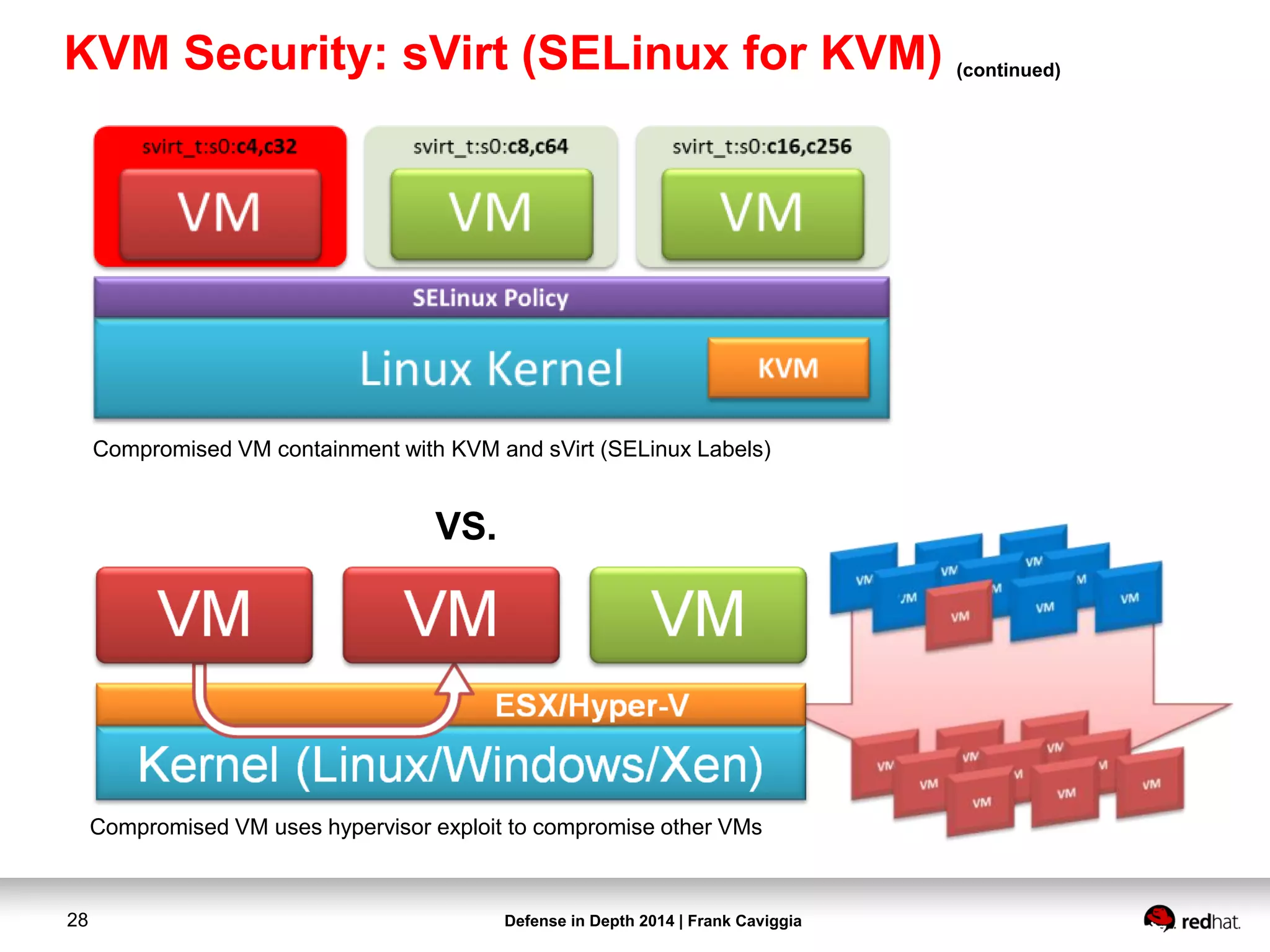
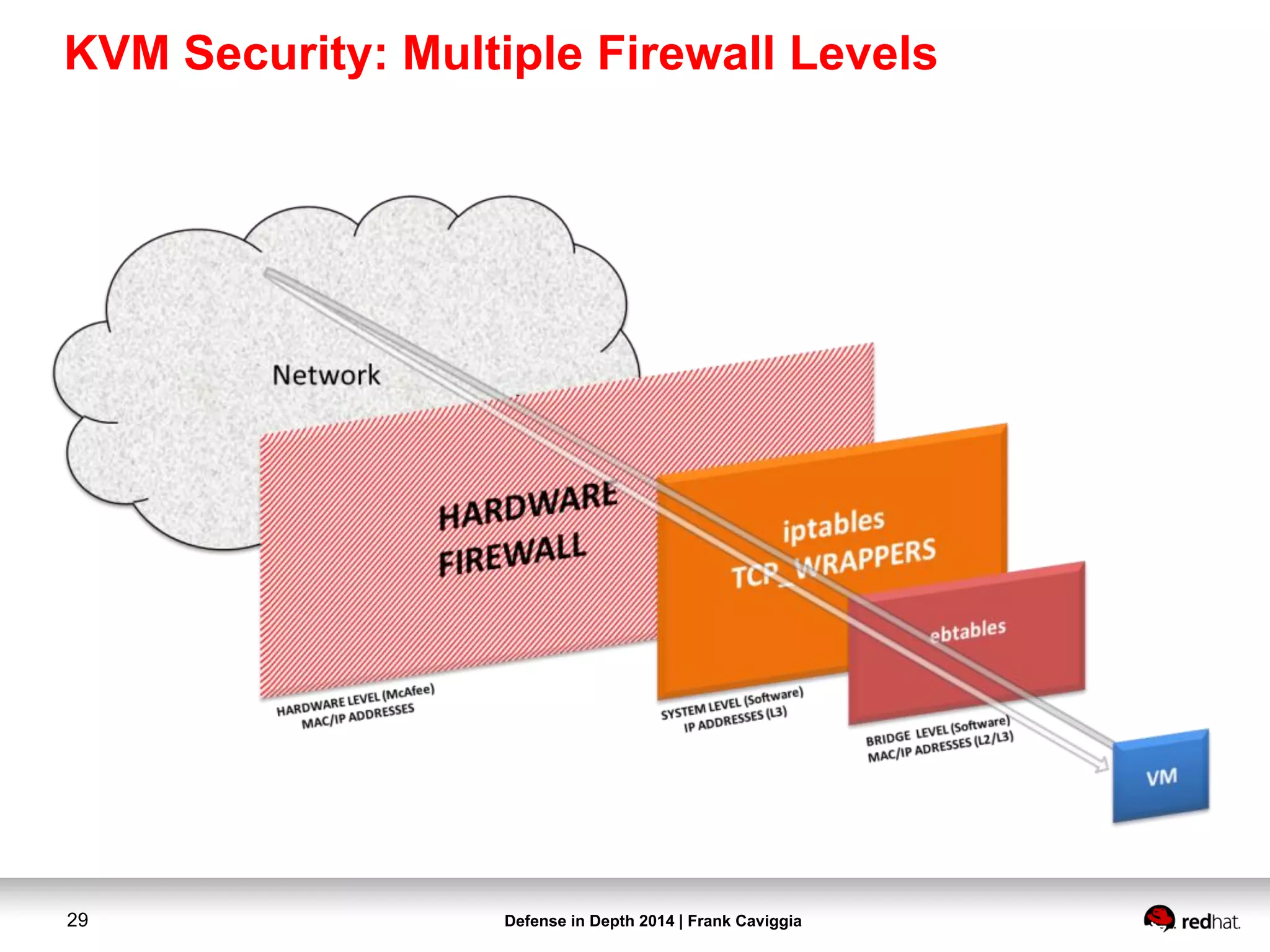
This document discusses security controls for a Red Hat Enterprise Linux virtualization environment hosting Top Secret VMs. It describes the hardware and software system configuration, including the use of KVM virtualization, Identity Management, and Satellite for patching. It also covers security concepts like SELinux and cgroups used to isolate VMs and limit resources. Hardening scripts are used to configure systems according to standards and continuous monitoring is enabled through SCAP and Satellite.


![Defense in Depth 2014 | Frank Caviggia5
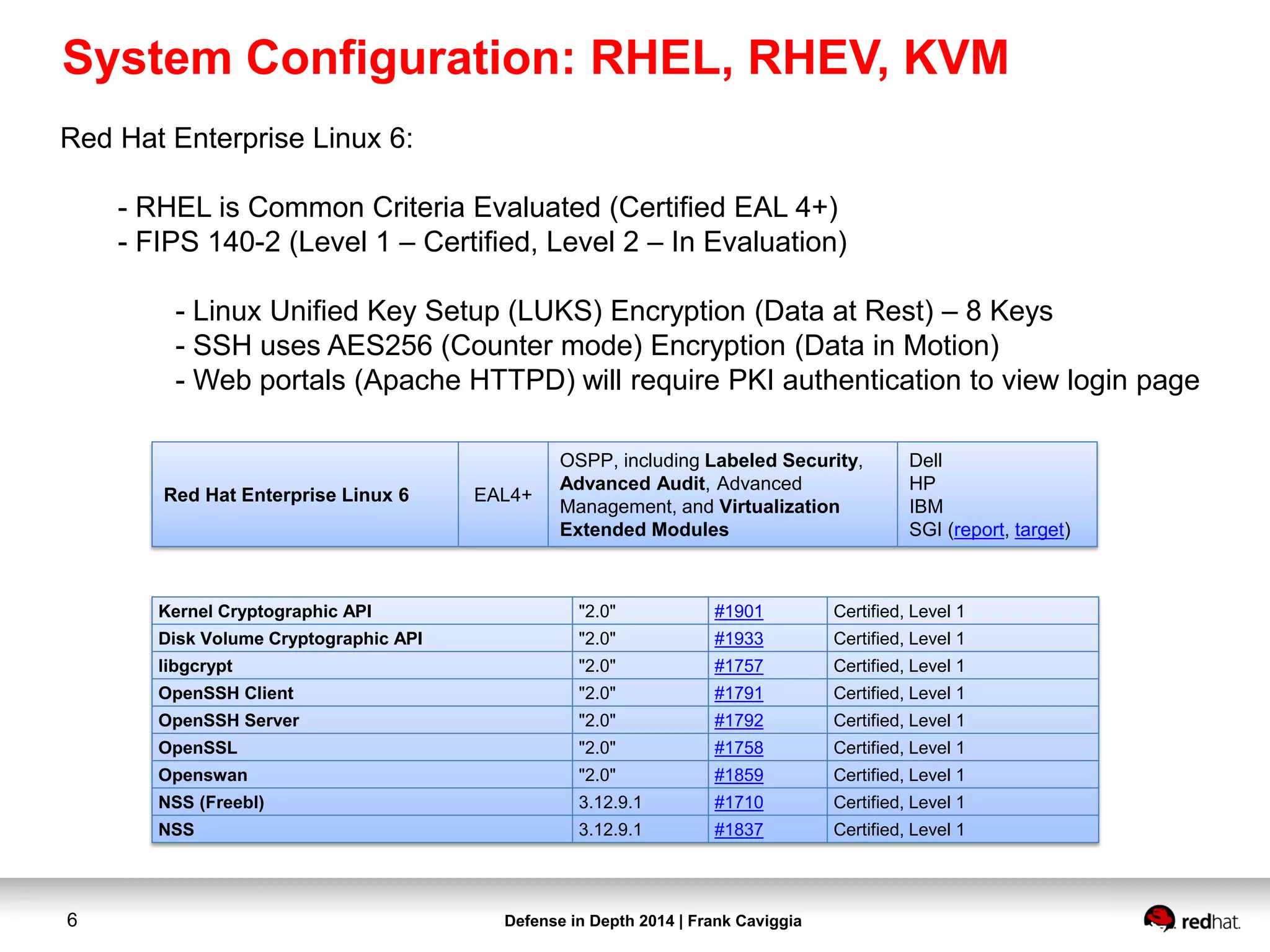
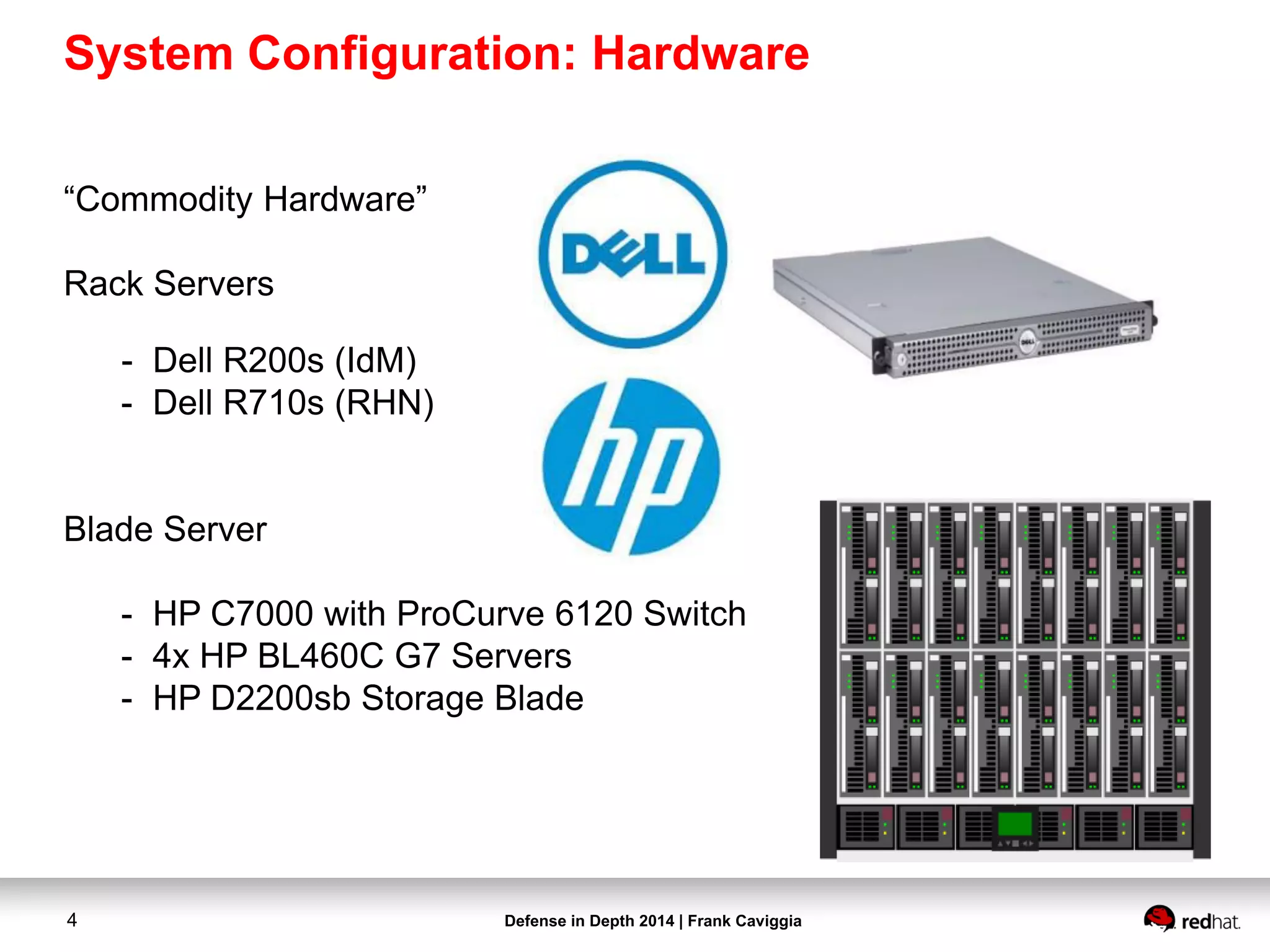
Red Hat Software
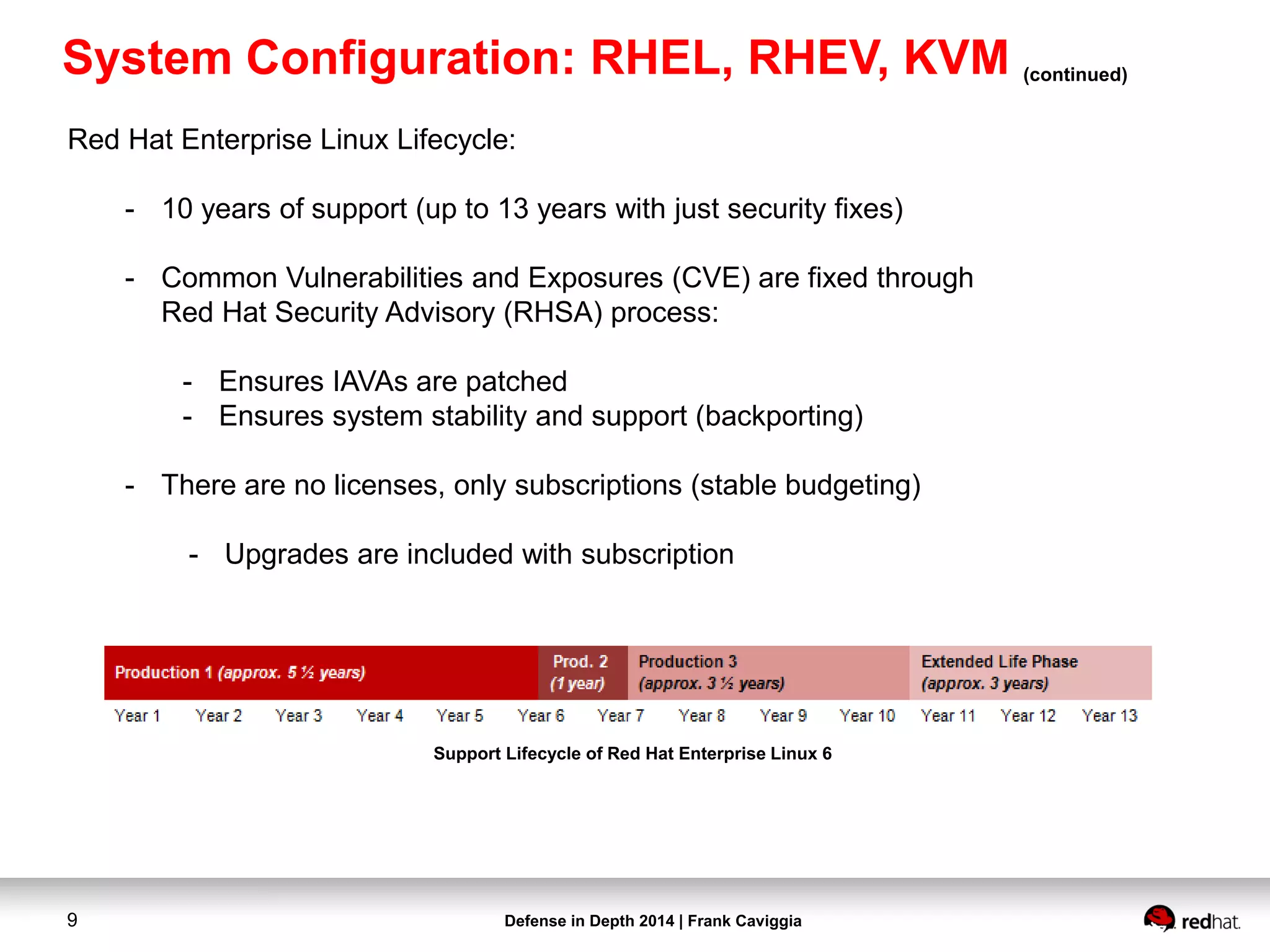
- Red Hat Enterprise Linux 6.5 Server x86_64
- Authentication (IdM) [389-DS(LDAP)/Kerberos]
- Red Hat supported version of FreeIPA
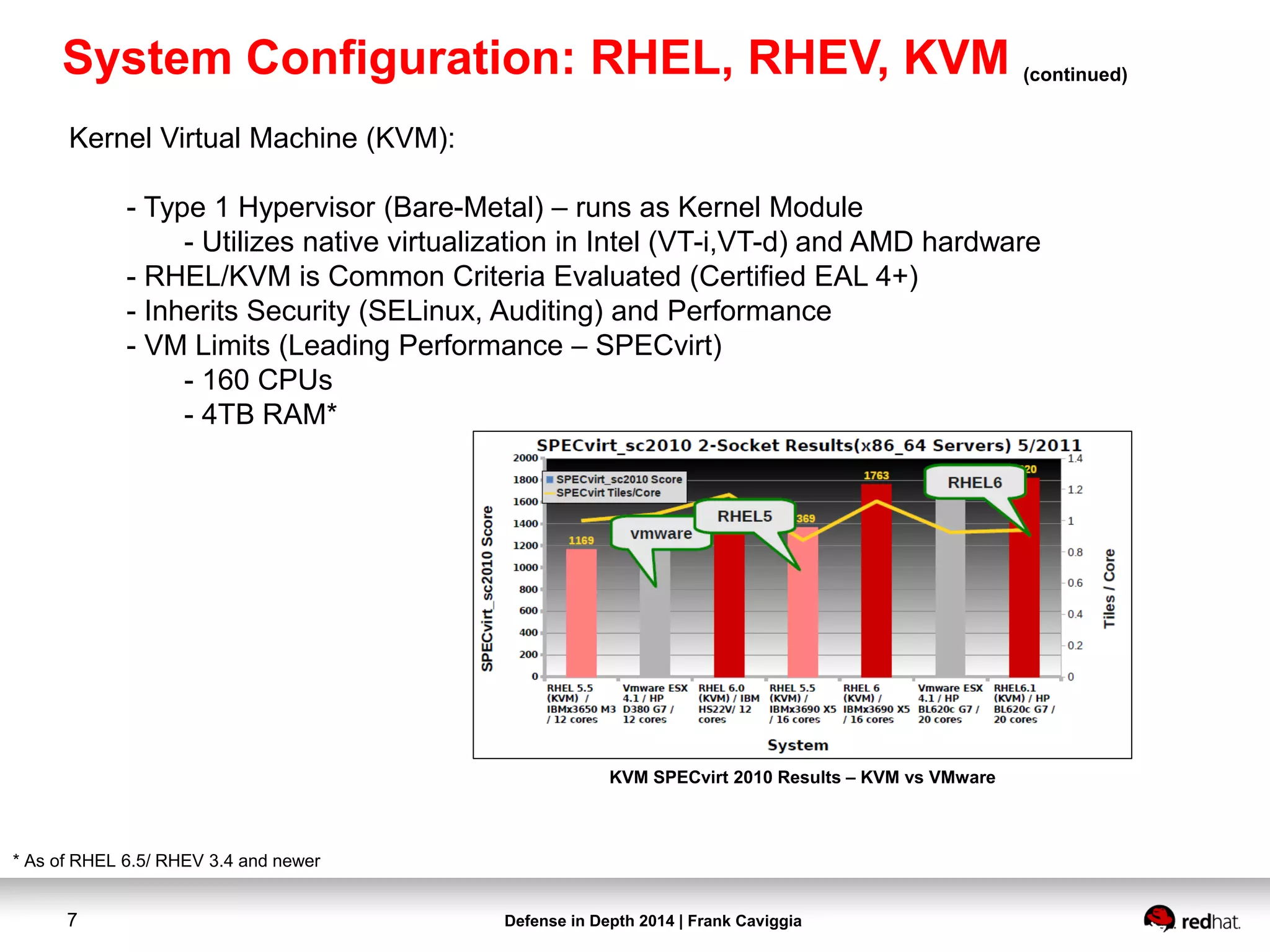
- Kernel Virtual Machine (KVM)
- Red Hat Enterprise Virtualization (RHEV) 3.3
- RHEV-M (Management Console for KVM Hypervisors)
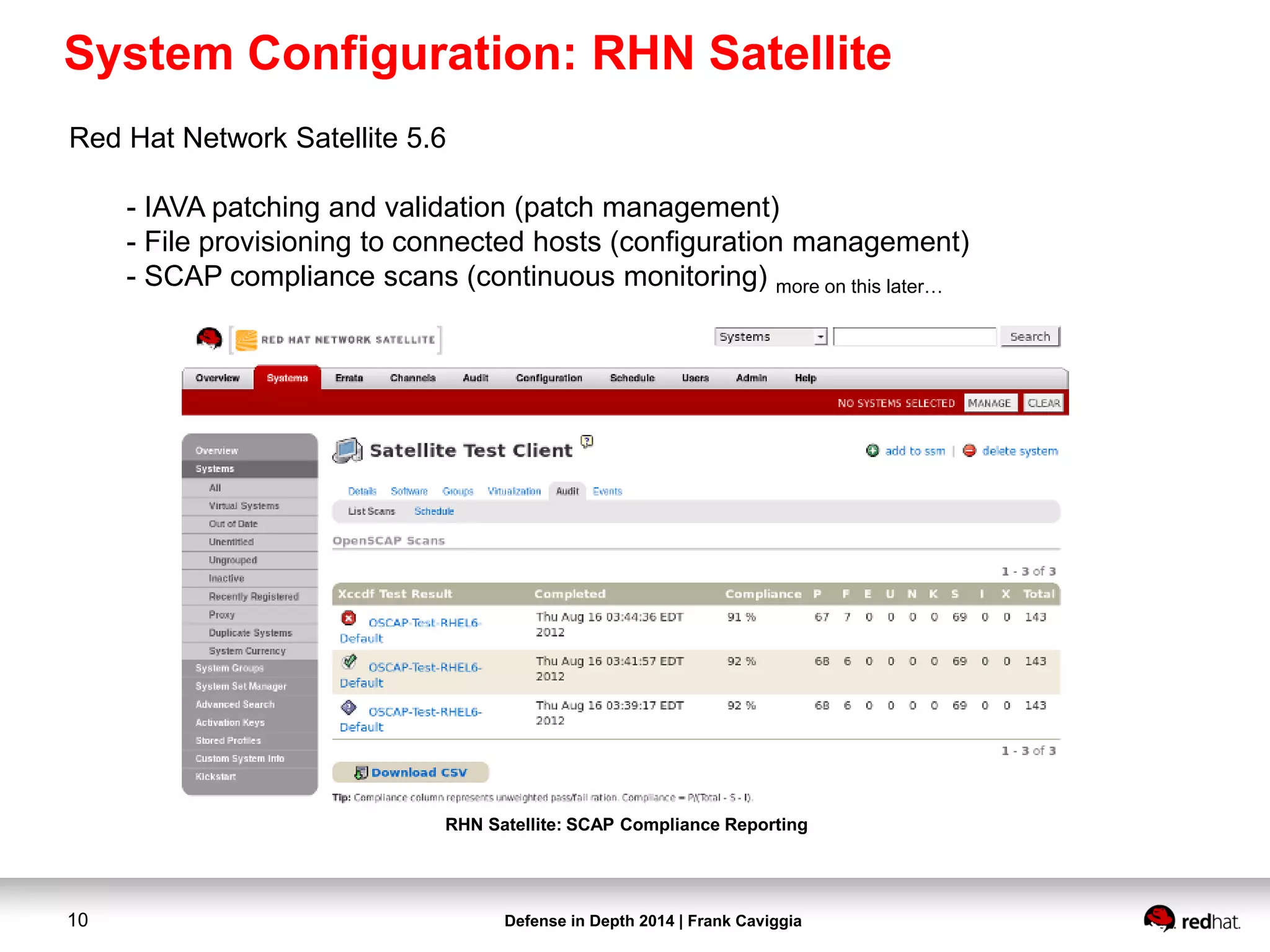
- Red Hat Network (RHN) Satellite 5.6
System Configuration: Software](https://image.slidesharecdn.com/715c6ddb-4894-406d-a4a2-aa0022c45ece-150224200208-conversion-gate02/75/KVM_security-5-2048.jpg)