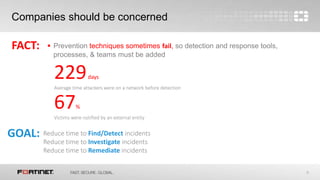
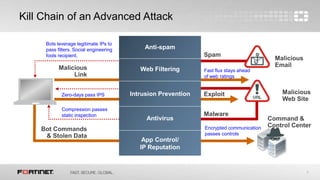
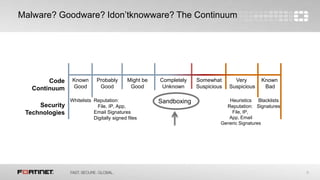
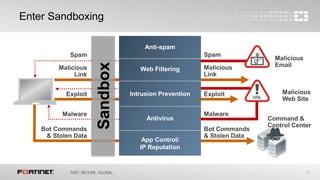
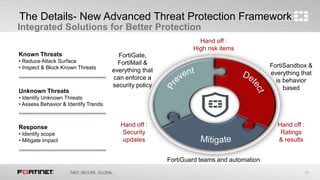
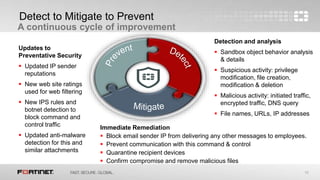
This document discusses advanced threat protection and sandboxing techniques. It summarizes that many breaches still come from older vulnerabilities even as new threats emerge. Sandboxing allows potentially malicious files and code to be executed and analyzed safely in an isolated virtual environment. This helps identify unknown threats that evade traditional defenses. The document advocates an integrated security approach using sandbox analysis to detect unknown threats, along with preventative defenses and updated intelligence to help mitigate risks and prevent future attacks.

![2
Old & New Threats
Despite all the publicity about zero-day exploits, a big
percentage of breaches (44 per cent) come from
vulnerabilities which are two to four years old.
[…] Most vulnerabilities stem from a relatively small
number of common software programming errors.
Every one of the top ten vulnerabilities exploited in 2014
took advantage of code written years or even decades
ago, according to HP, which recorded an increase in the
level of mobile malware detected.
“Many of the biggest security risks are issues we’ve known
about for decades, leaving organisations unnecessarily
exposed,” said Art Gilliland, senior vice president and
general manager, Enterprise Security Products, HP.](https://image.slidesharecdn.com/sandboxing-150910083117-lva1-app6891/85/Sandboxing-2-320.jpg)