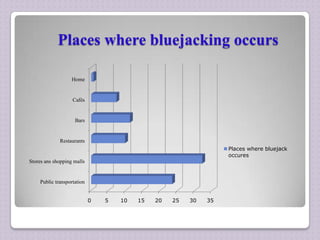
This document discusses bluejacking, which is sending unsolicited messages to Bluetooth devices. It provides an introduction to bluejacking and Bluetooth technology. The history of bluejacking is explained, originating from a comment on a mobile forum. Steps for bluejacking using mobile phones and computers are outlined. The document also lists software tools for bluejacking and common locations where it occurs. Potential harm from bluejacking and prevention methods are briefly mentioned before concluding.