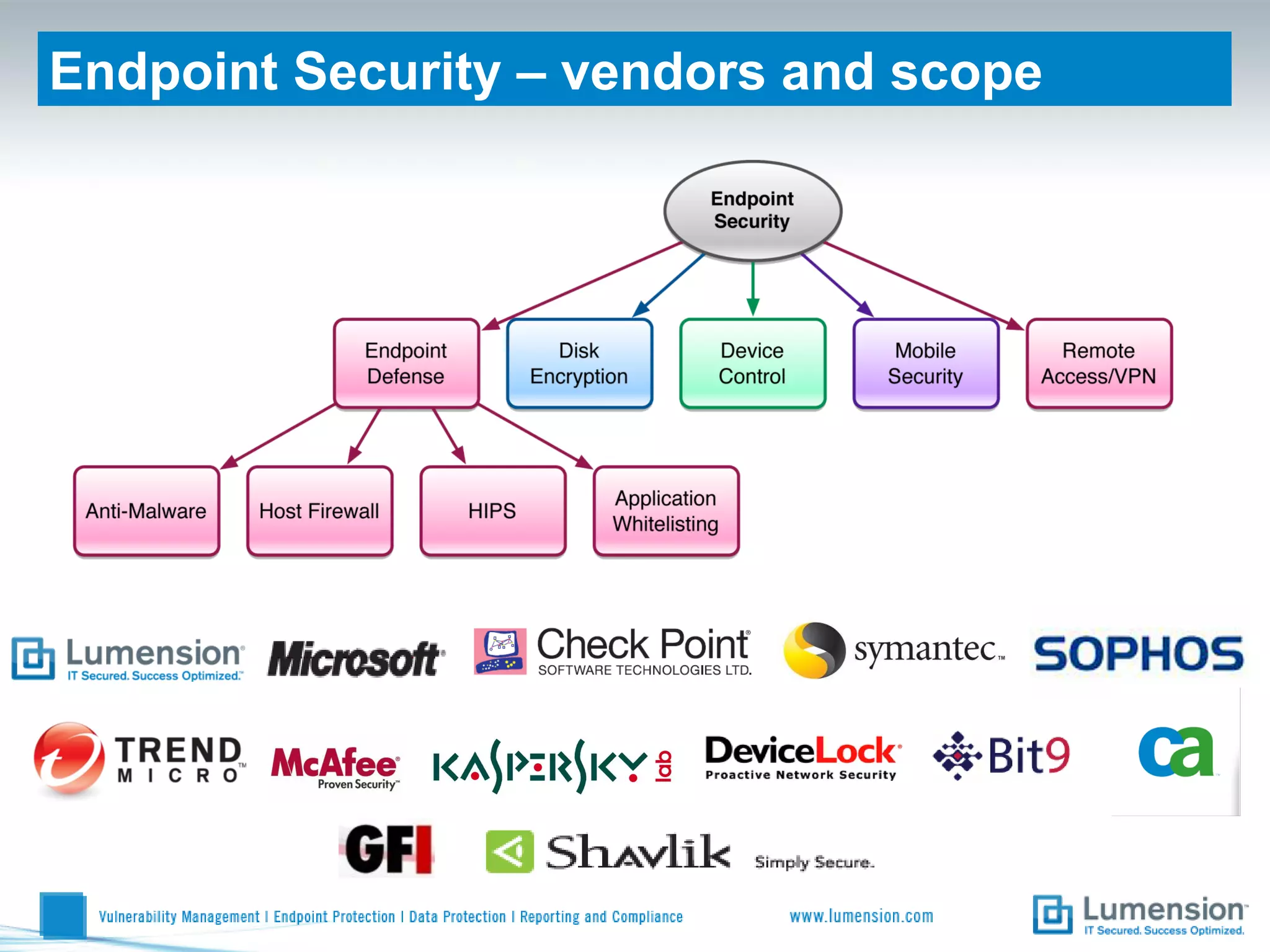
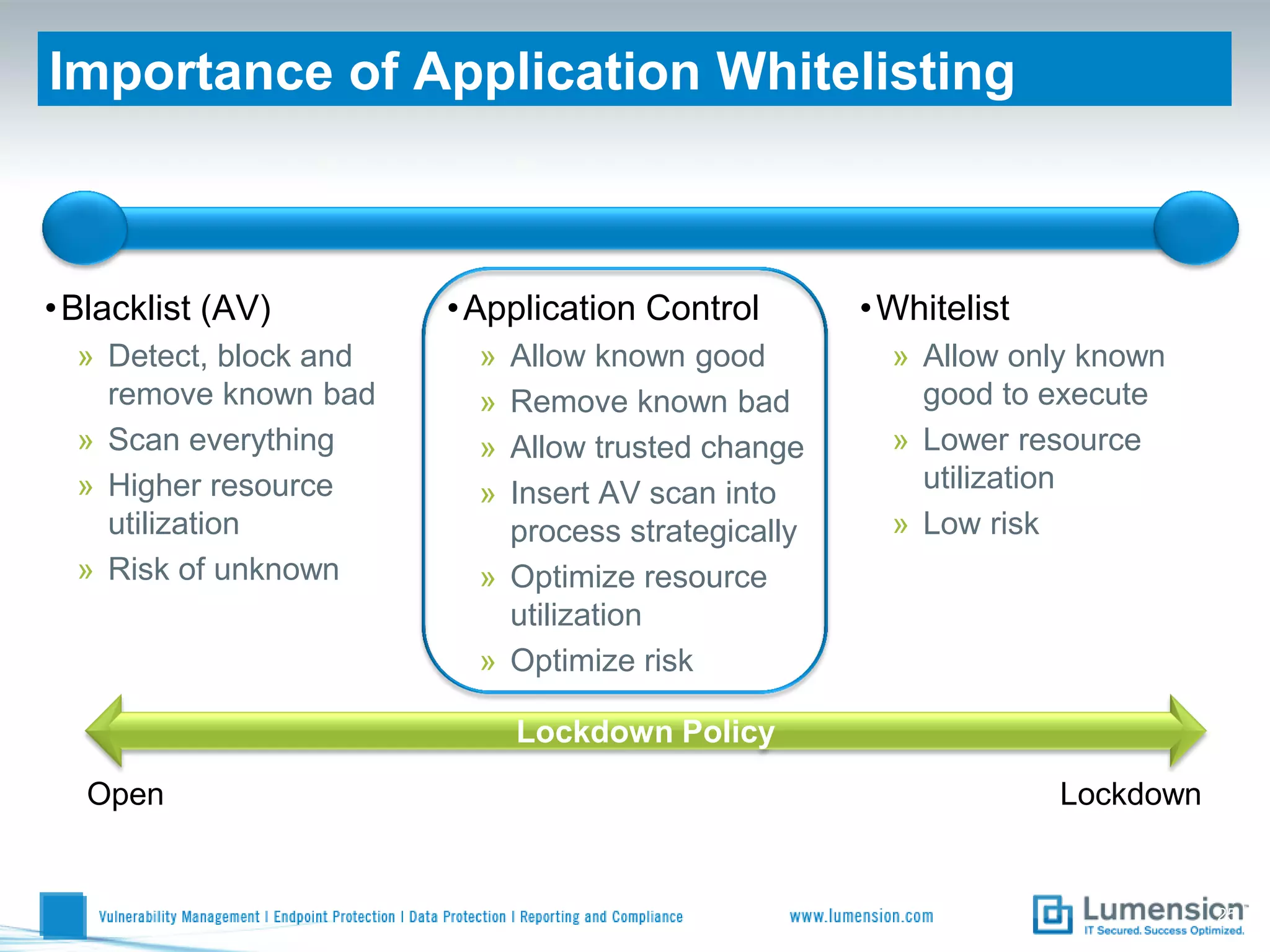
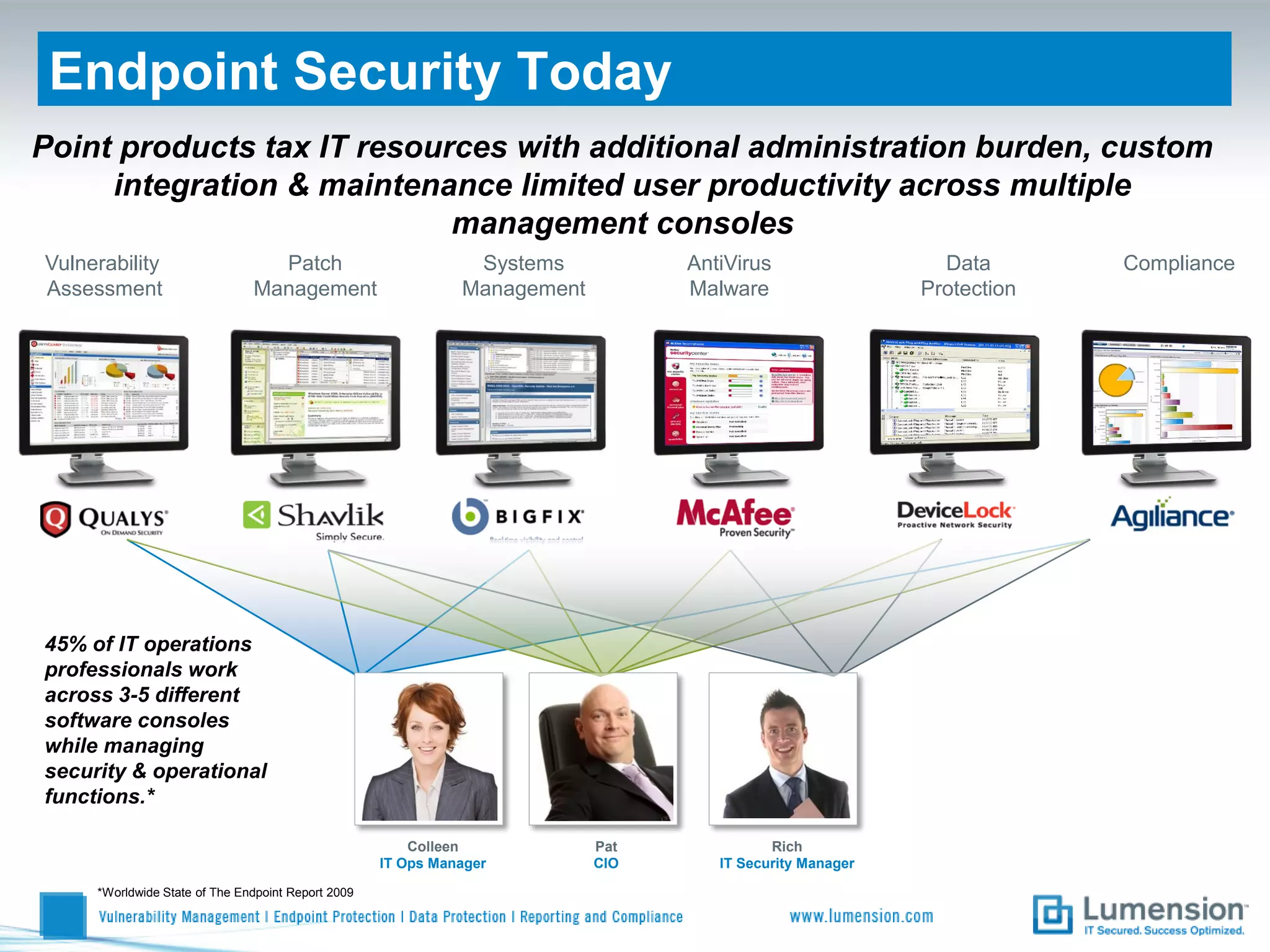
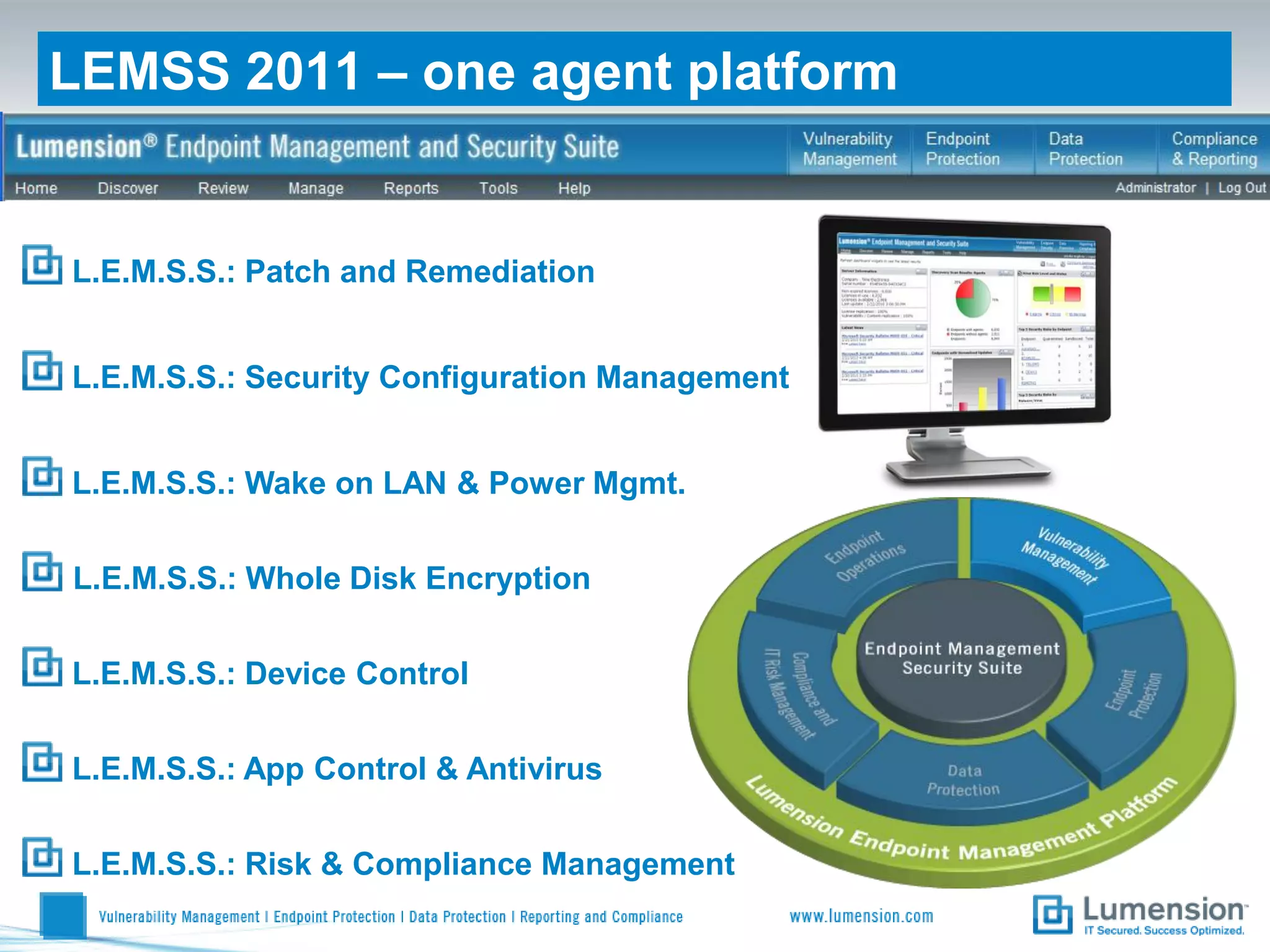
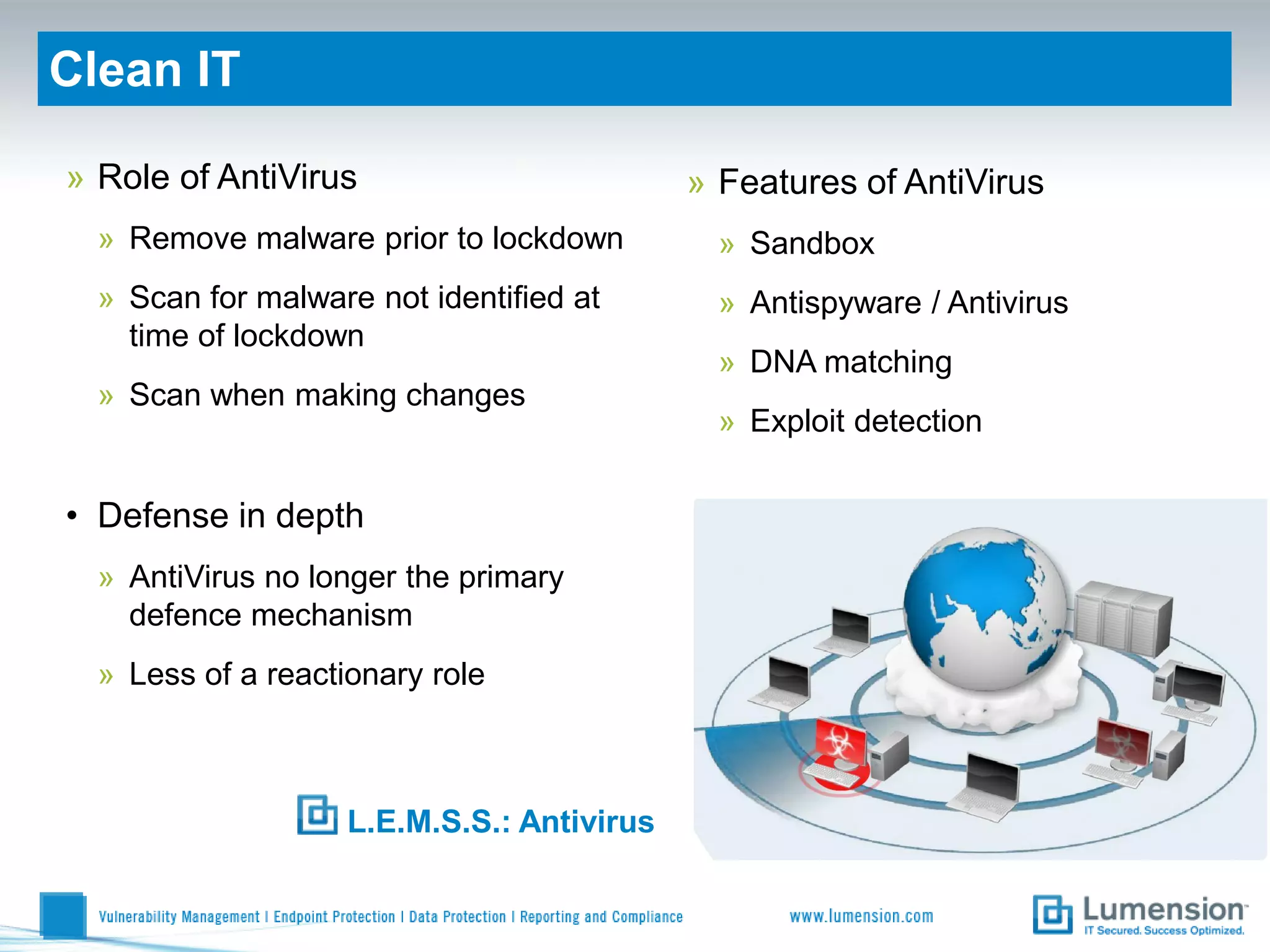
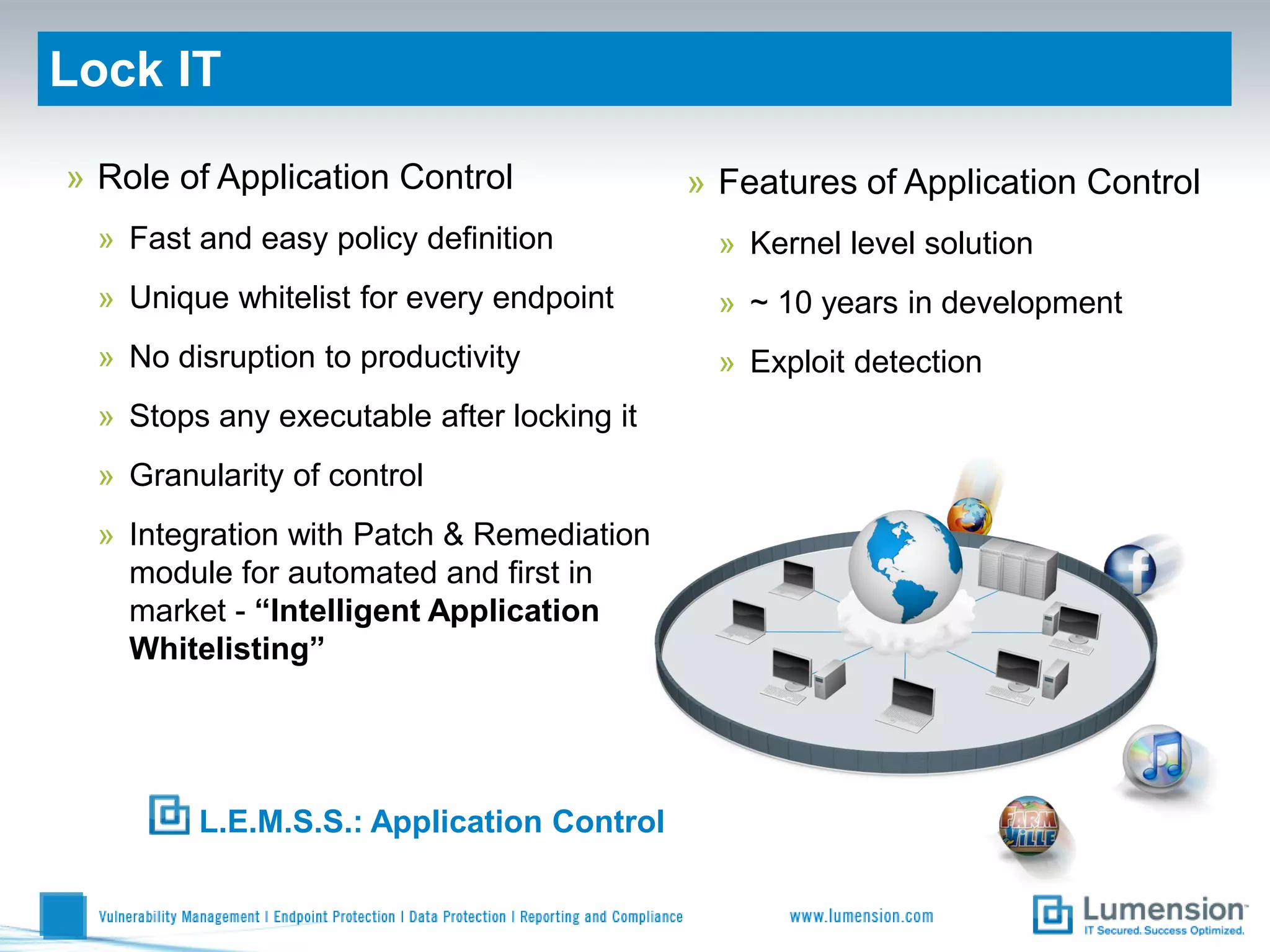
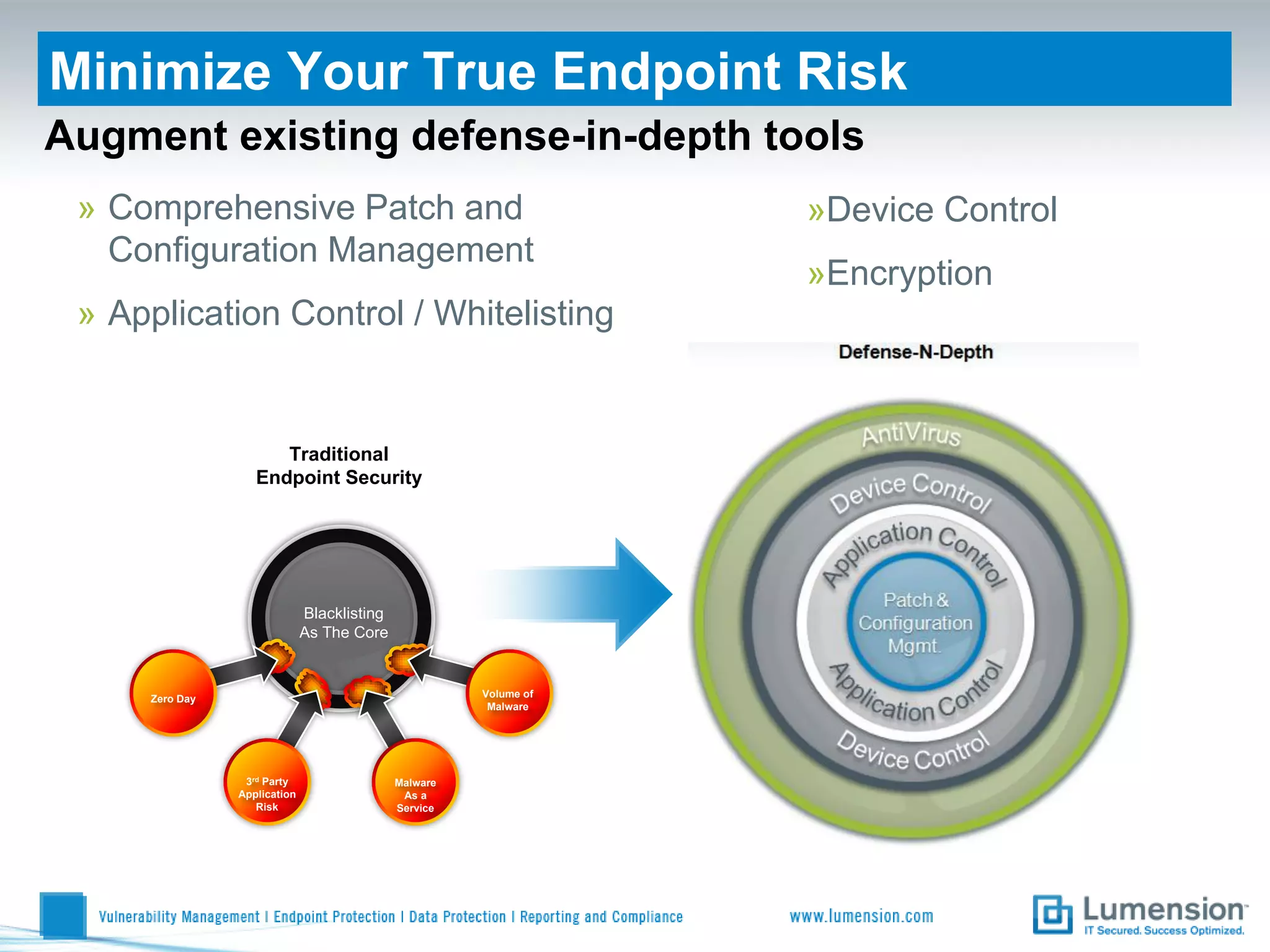
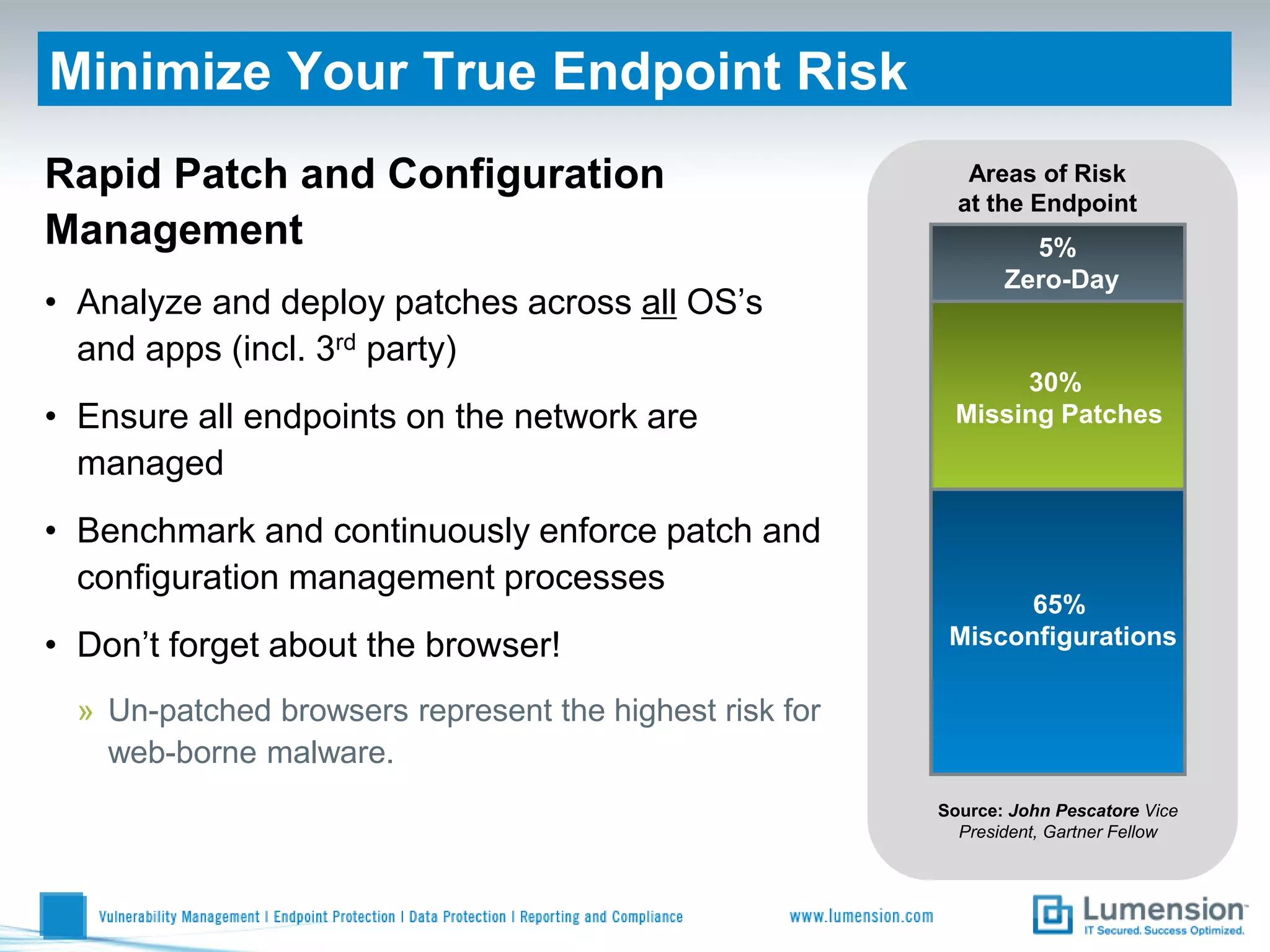
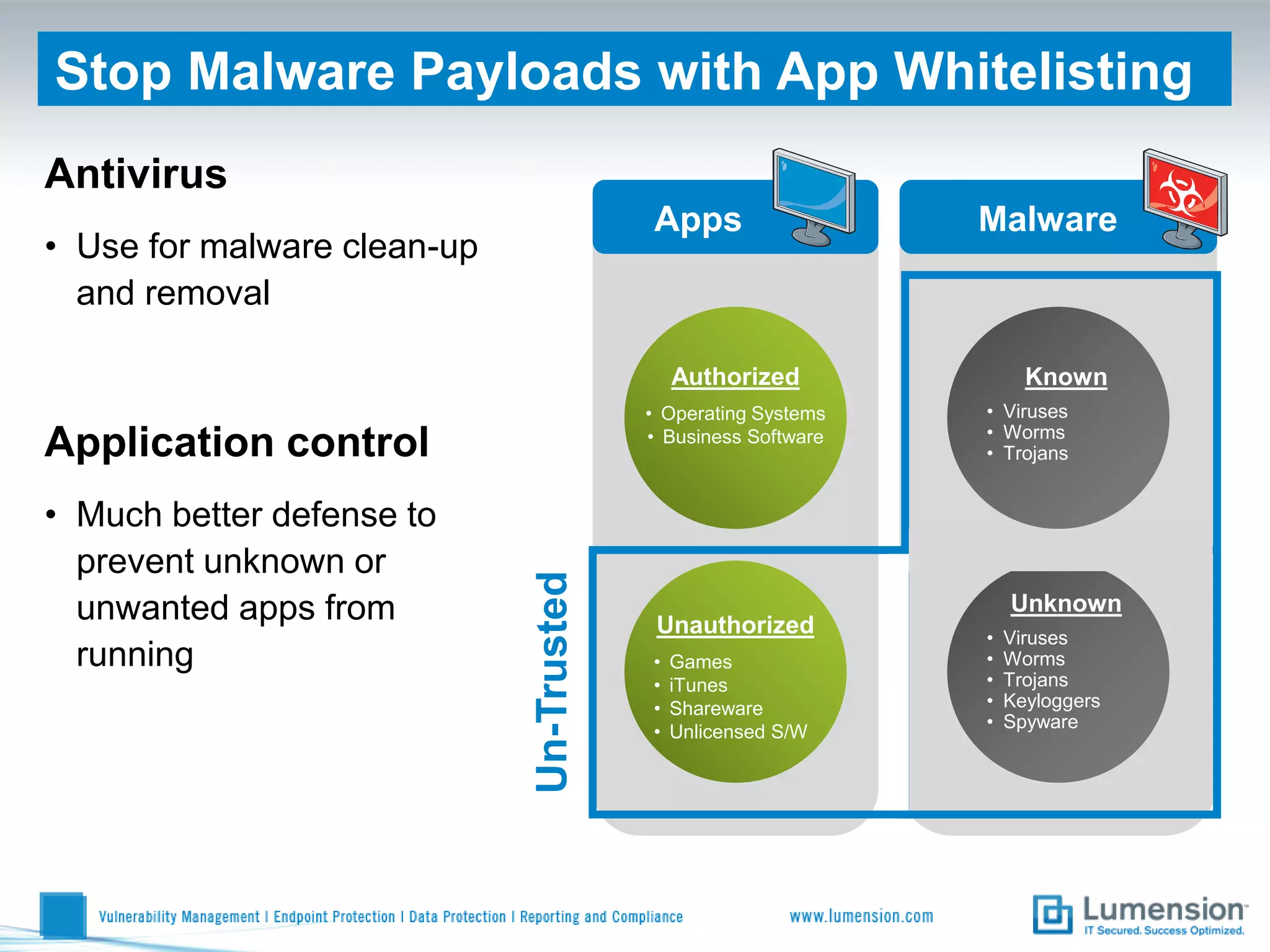
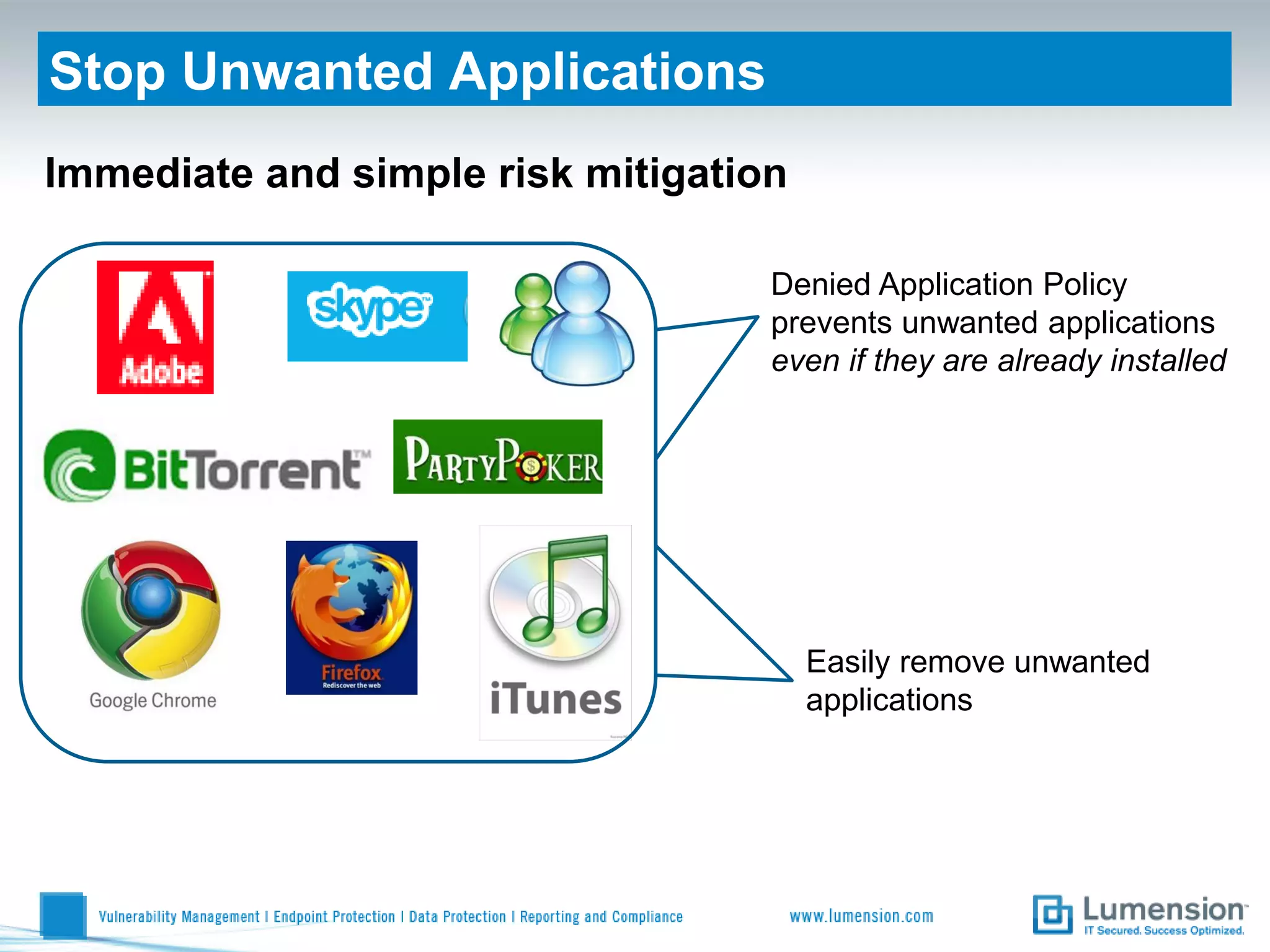
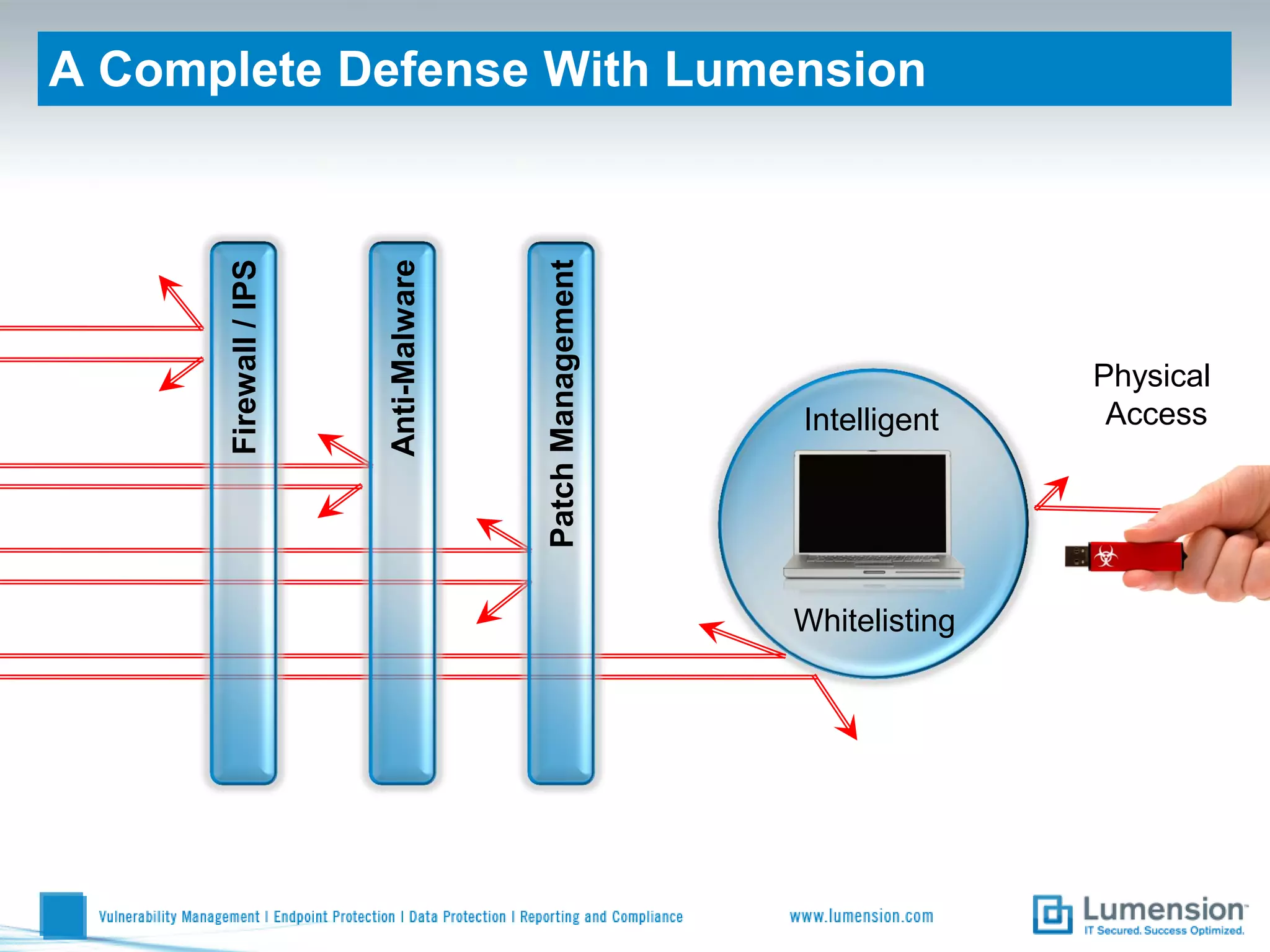
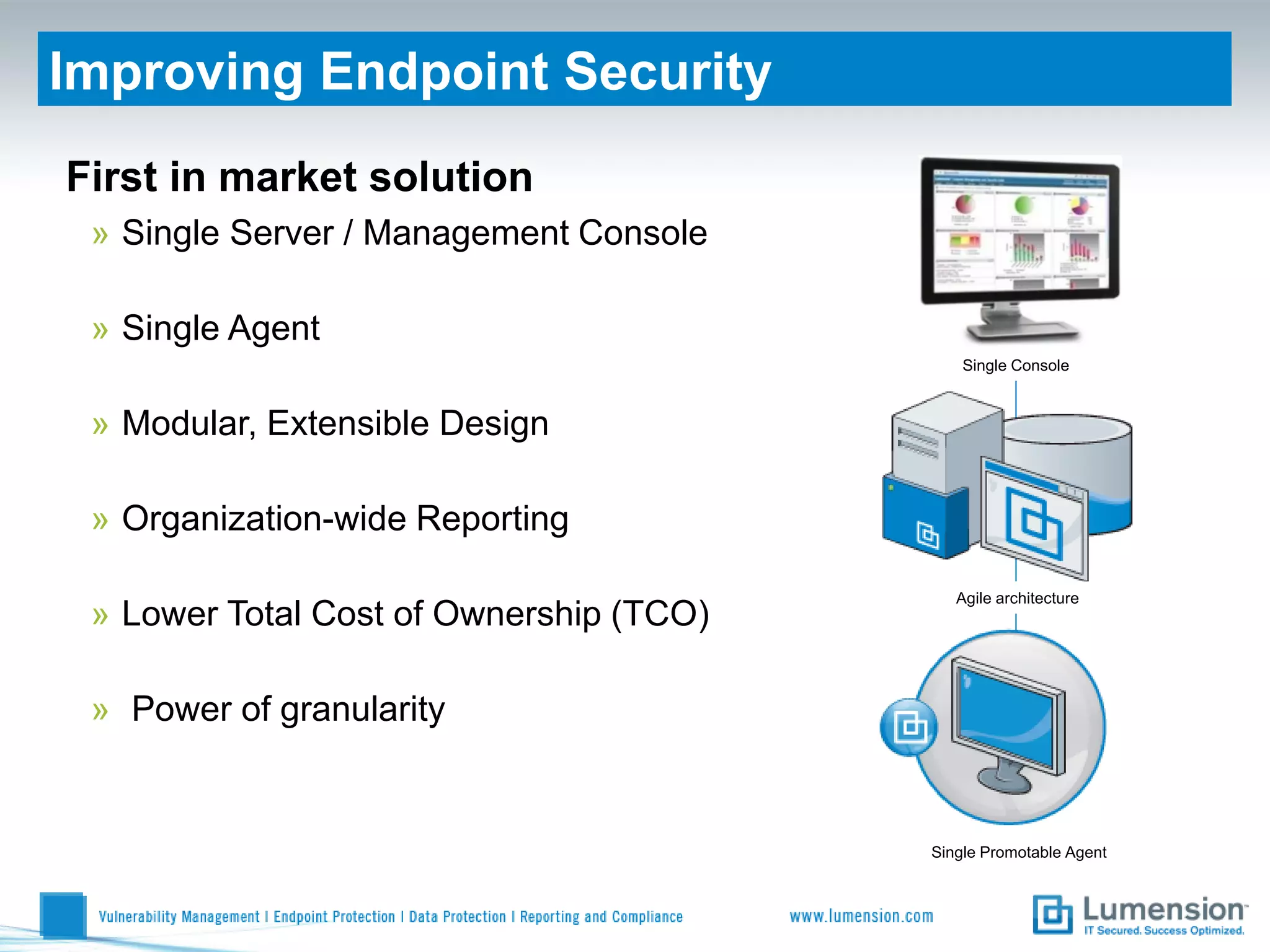
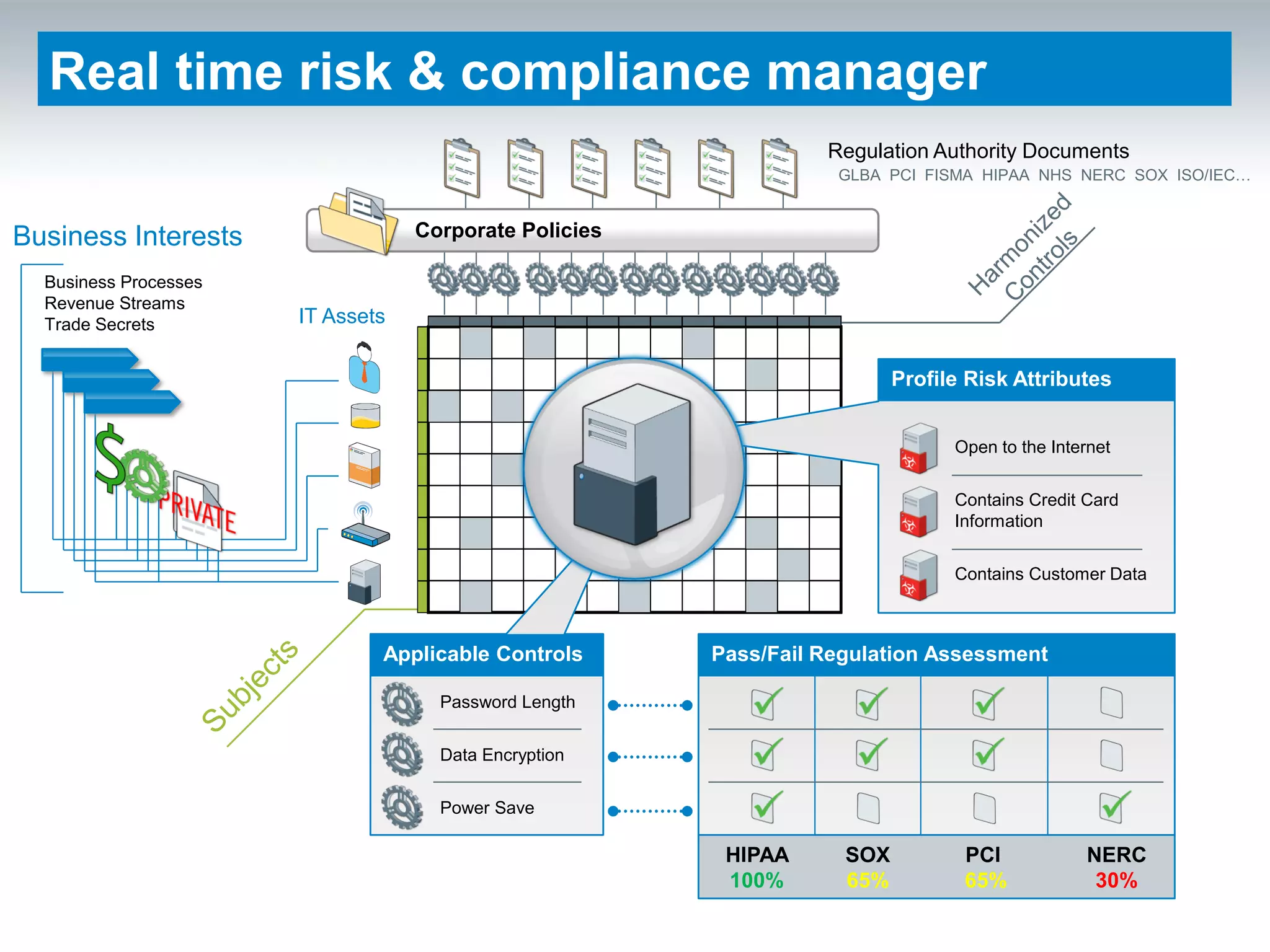
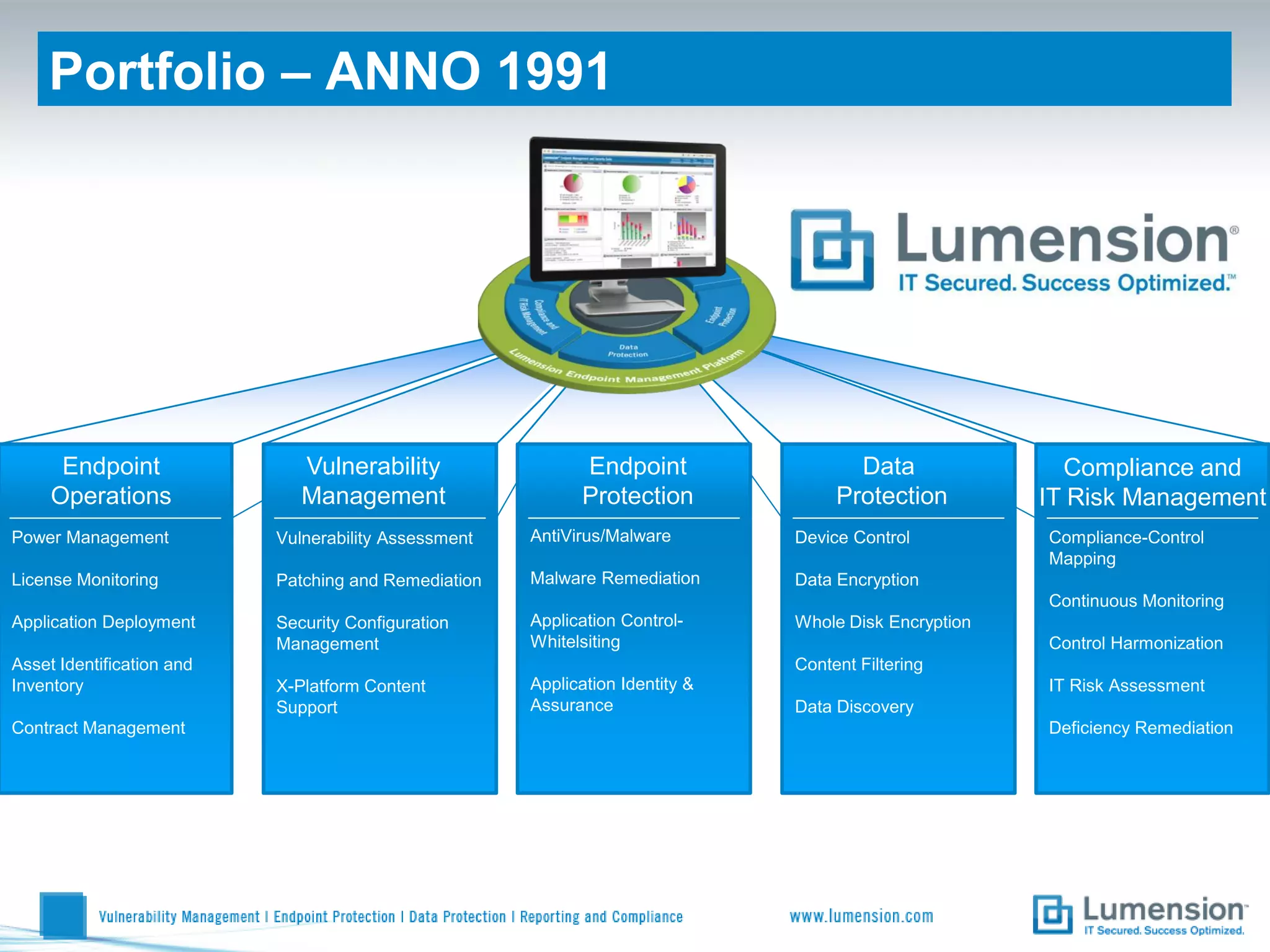
Shift to Intelligent Endpoint Security Management
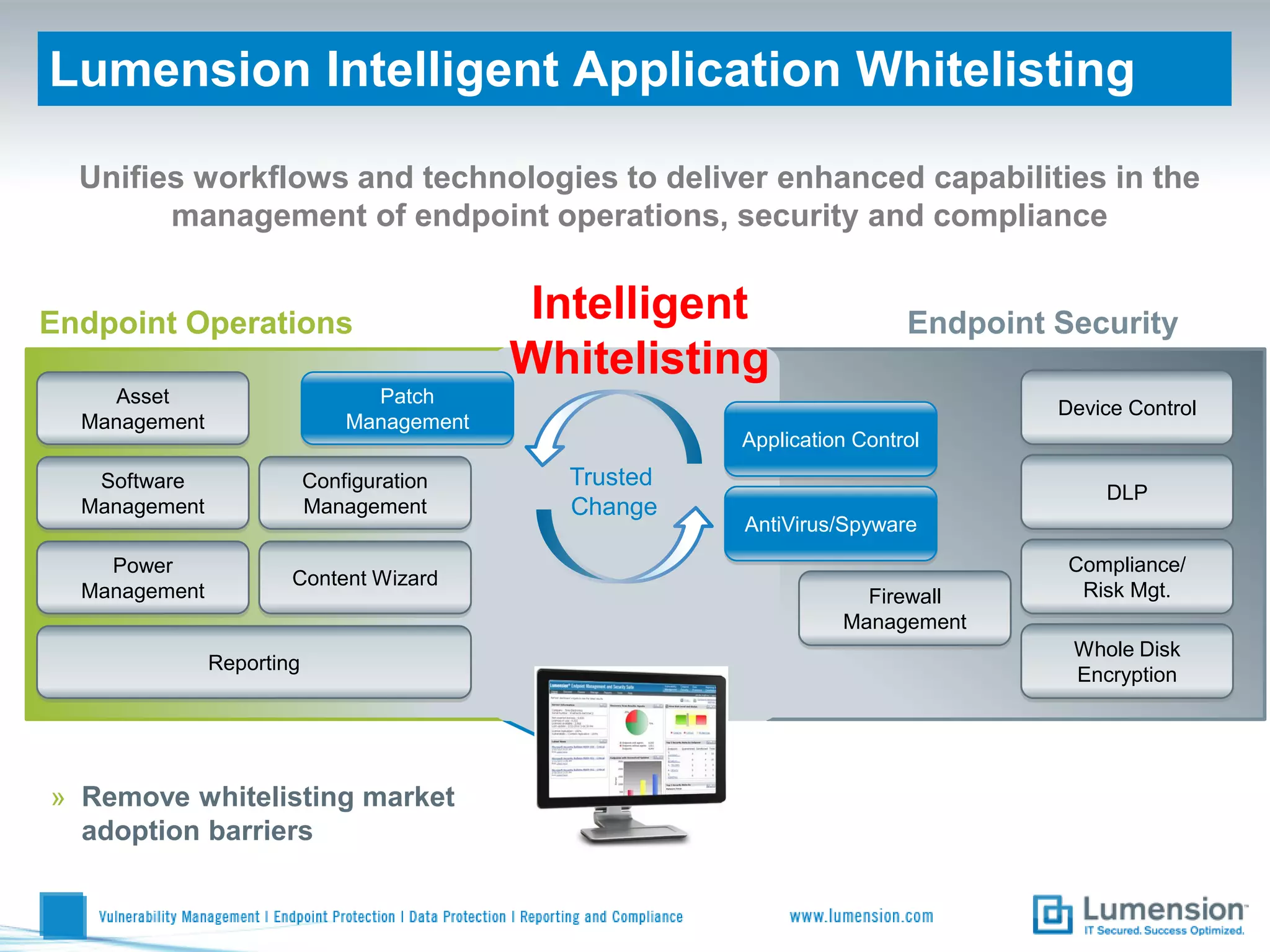
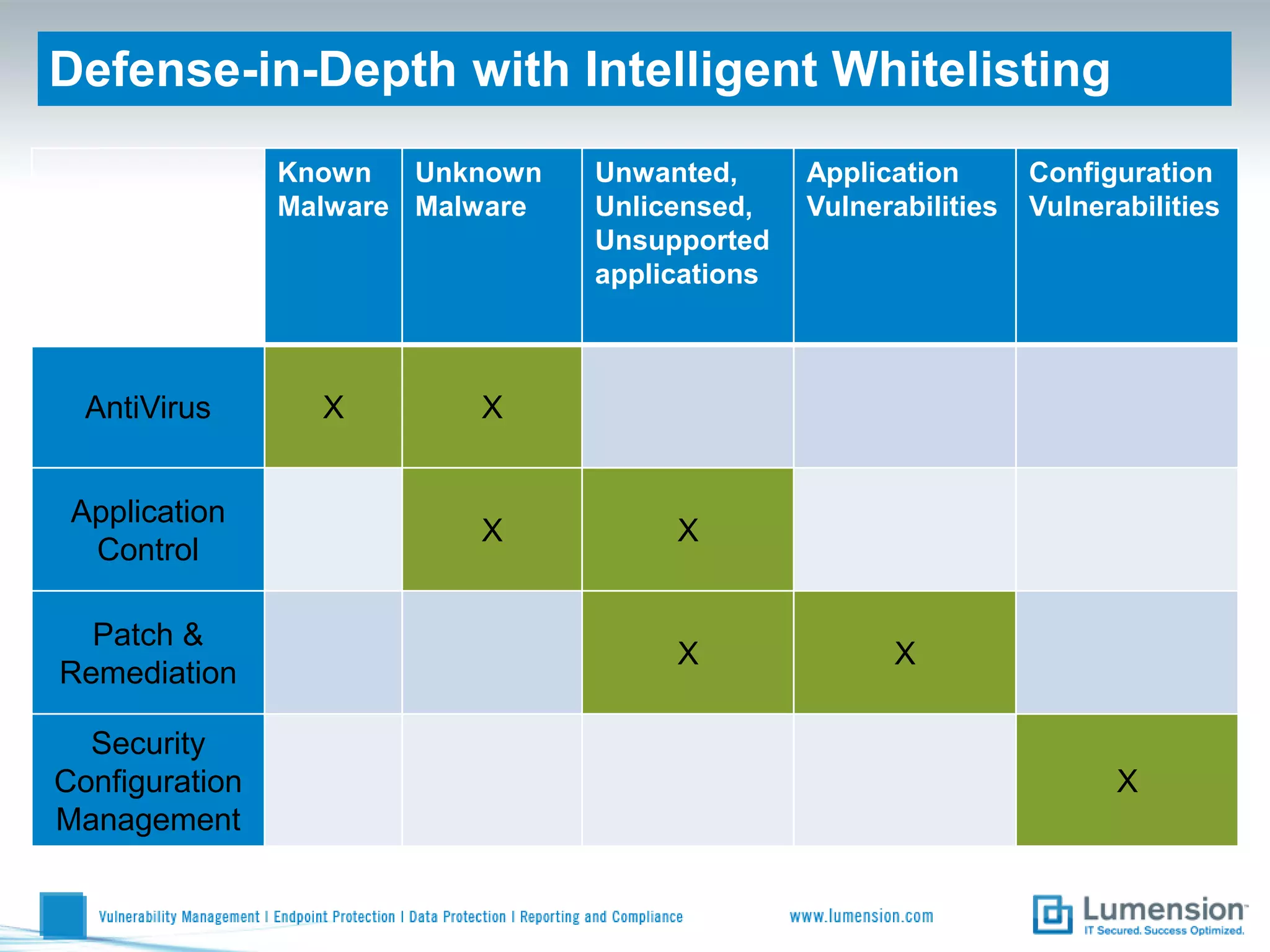
The document discusses the shift from traditional endpoint security methods to more intelligent approaches. Traditional defenses like antivirus software and patching are no longer effective against modern threats. New strategies are needed to control applications and local user privileges, prevent zero-day and targeted attacks, and provide better security reporting. Without improved technology solutions, organizations will continue to have sensitive data and systems compromised by cybercriminals. The future of endpoint security requires more intelligent methods like application whitelisting to lock down systems while optimizing security and resources.










![Quotes from AV vendors
Basic security protection “You can’t just rely on
is not good enough,” antivirus software – and
Rowan Trollope Senior we’re an antivirus
Vice President, Symantec company” George Kurtz,
Worldwide CTO, McAfee
[Standard] antivirus is not "[signatures are] completely
effective anymore... Raimund ineffective as the only layer [of
Genes, CTO Trend Micro Inc endpoint security]… Nikolay
Grebennikov, CTO, Kaspersky](https://image.slidesharecdn.com/dss-itsecconf-lumension-intelligentapplicationwhitelisting-riganov2011-111208171229-phpapp01/75/DSS-ITSEC-CONFERENCE-Lumension-Security-Intelligent-application-whitelisting-Riga-NOV-2011-21-2048.jpg)