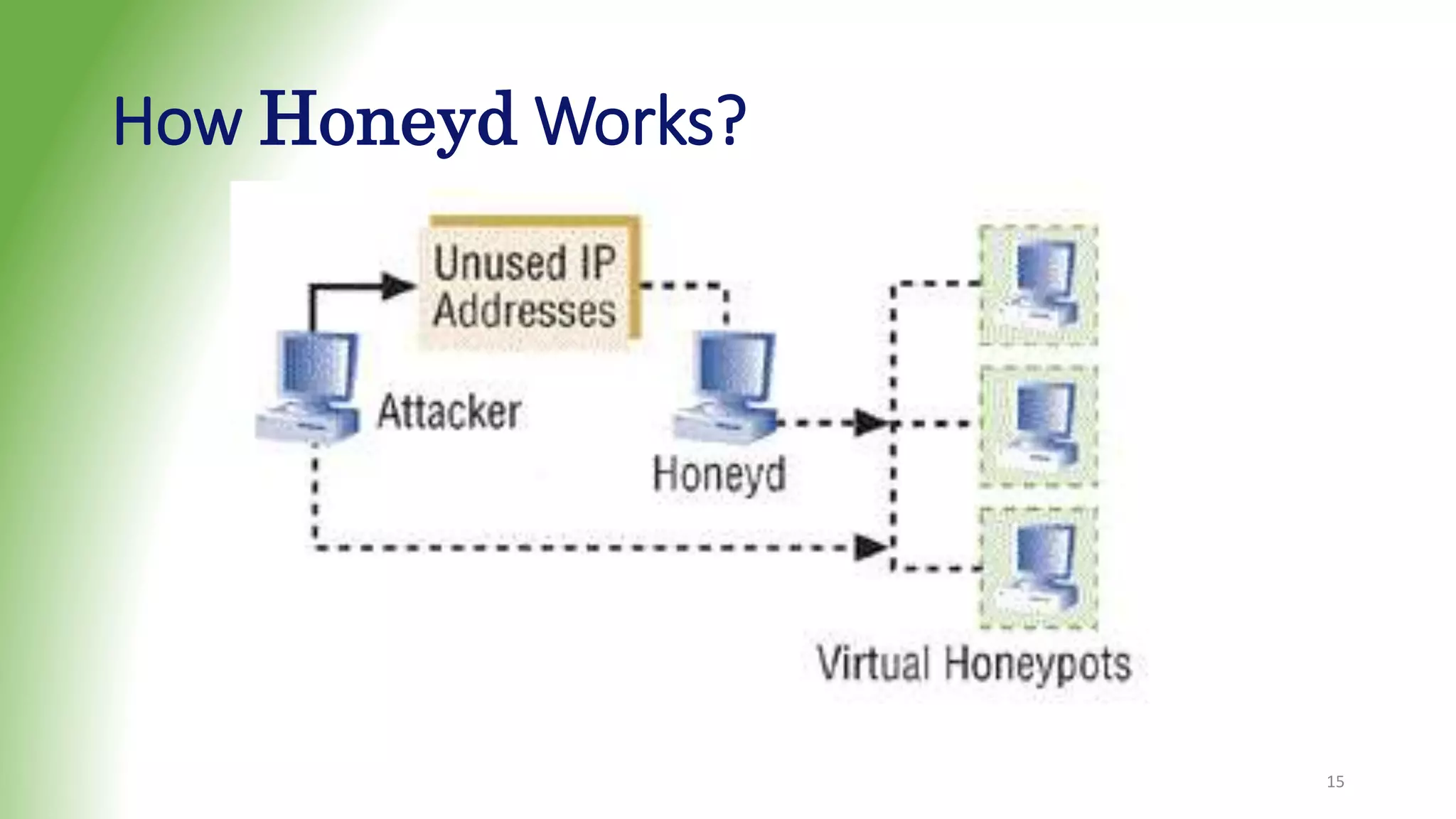
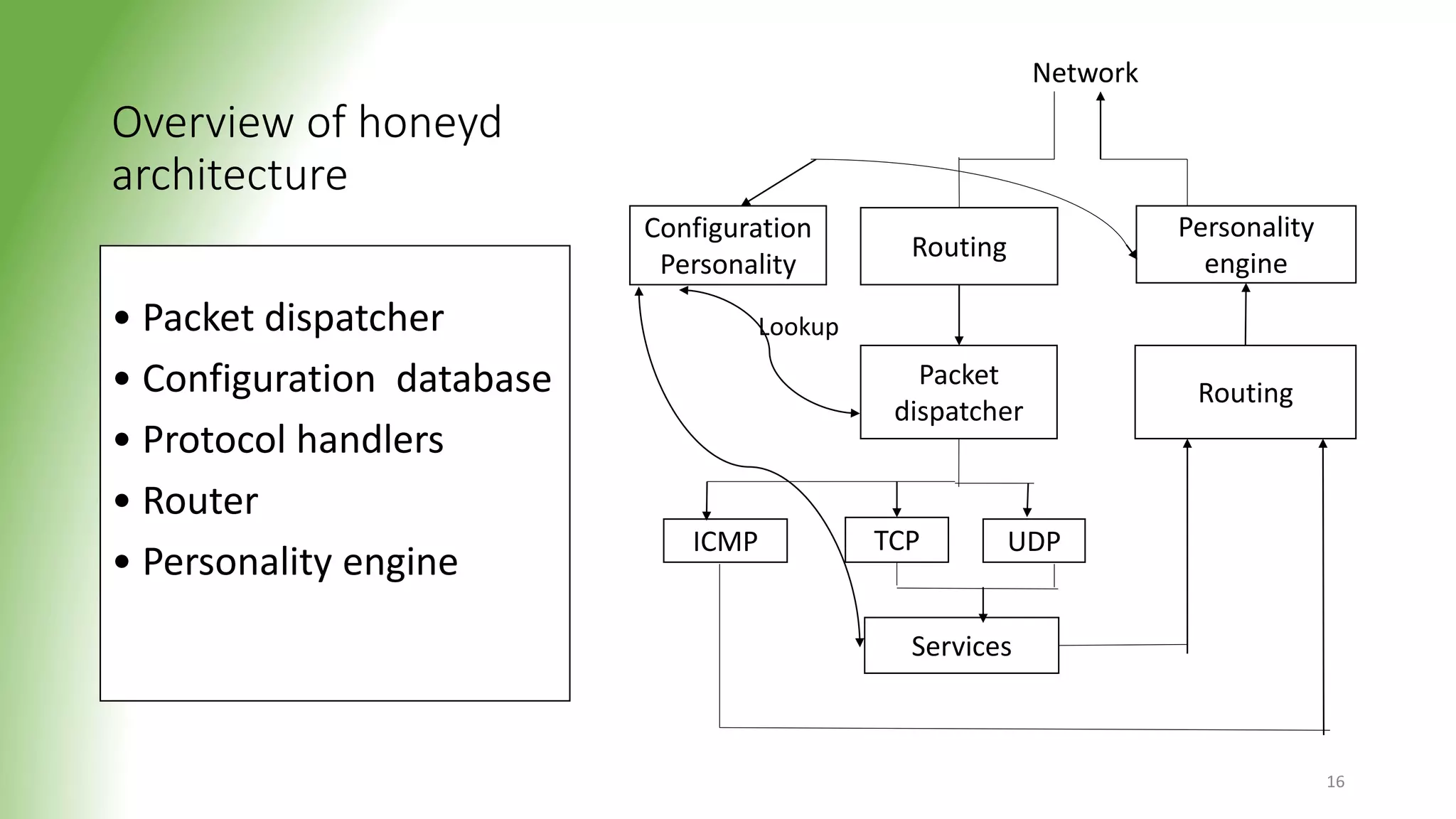
This document discusses honeypots, which are decoy computer systems used to gather intelligence about cyber attacks. Honeypots can be classified based on their level of interaction, implementation, and purpose. Low-interaction honeypots like Honeyd simulate some system aspects with minimal risk, while high-interaction honeypots like Honeynet aim to be fully compromised. Honeynets form a network of honeypots to capture extensive attack information for research. The document outlines the architecture and functionality of Honeyd and Honeynet honeypots. Honeypots provide benefits like reduced false alarms and insights into attacker techniques, but also pose risks if they are detected.